Most FHE projects are expected to launch their mainnet from this year to the first quarter of next year.
By Maggie @ Foresight Ventures
TLDR:
Fully Homomorphic Encryption (FHE) is the upcoming next-generation privacy protection technology, and it is worth our attention. FHE has ideal privacy protection capabilities, but its performance still has room for improvement. We believe that with the entry of crypto capital, the development and maturation of the technology will be greatly accelerated, just like the rapid development of ZK in recent years.
Fully Homomorphic Encryption can be used in Web3 for transaction privacy protection, AI privacy protection, and privacy protection coprocessors. I am particularly optimistic about the privacy protection EVM, which is more flexible and compatible with EVM than existing technologies such as ring signatures, coin mixing, and ZK.
We have researched several outstanding FHE projects, and most of them are expected to launch their mainnet from this year to the first quarter of next year. Among these projects, ZAMA has the strongest technology but has not yet announced plans to issue coins. In addition, we believe that Fhenix is the most outstanding FHE project among them.
I. FHE is an Ideal Privacy Protection Technology
1.1 Role of FHE
Fully Homomorphic Encryption is a form of encryption that allows people to perform arbitrary additions and multiplications on ciphertexts to obtain encrypted results, and decrypting the results will yield the same results as performing the same operations on plaintext. It achieves "computable invisibility" of data.
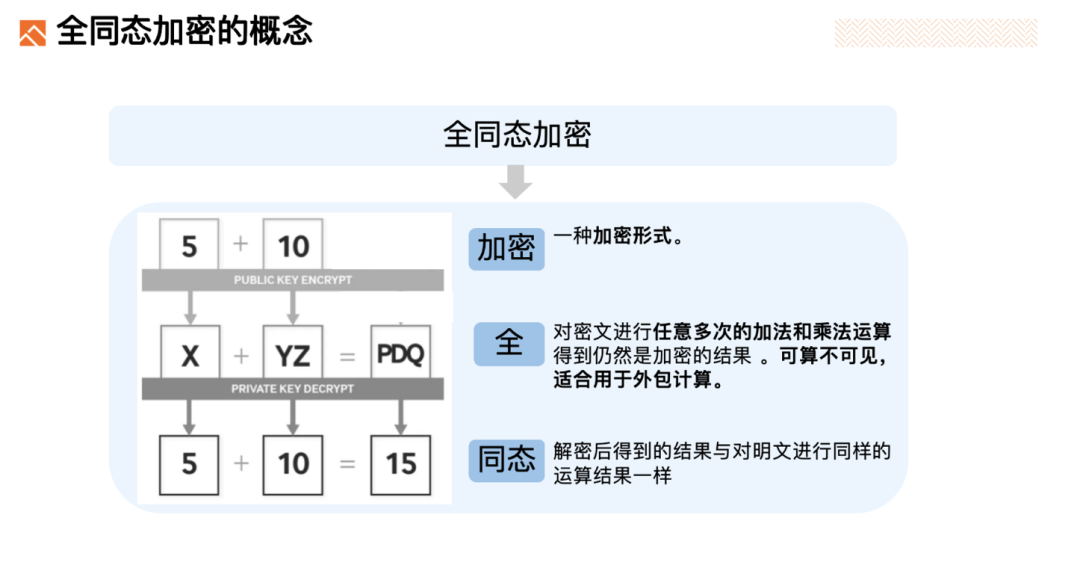
FHE is particularly suitable for outsourced computation, allowing data to be outsourced to external computing power for processing while avoiding data leakage.
In simple terms, for example, if you run a company and the data is very valuable, you may want to use efficient cloud services to process and compute this data, but you are concerned about data leakage in the cloud. In this case, you can:
Encrypt the data into ciphertext using fully homomorphic encryption before uploading it to the cloud server. For example, the numbers 5 and 10 in the image will be encrypted into ciphertext, represented as "X" and "YZ".
When you need to perform operations on the data, such as adding two numbers 5 and 10, you only need to perform the corresponding operation on the ciphertext "X" and "YZ" on the cloud server according to the algorithm's plaintext + operation, resulting in the ciphertext result "PDQ".
After downloading this ciphertext result from the cloud server and decrypting it, you will find that the plaintext result is the same as the result of the operation 5 + 10.
The plaintext only appears on your end, while the data stored and computed on the cloud server are all ciphertext data. This way, you don't have to worry about data leakage. This method of privacy protection is very ideal.
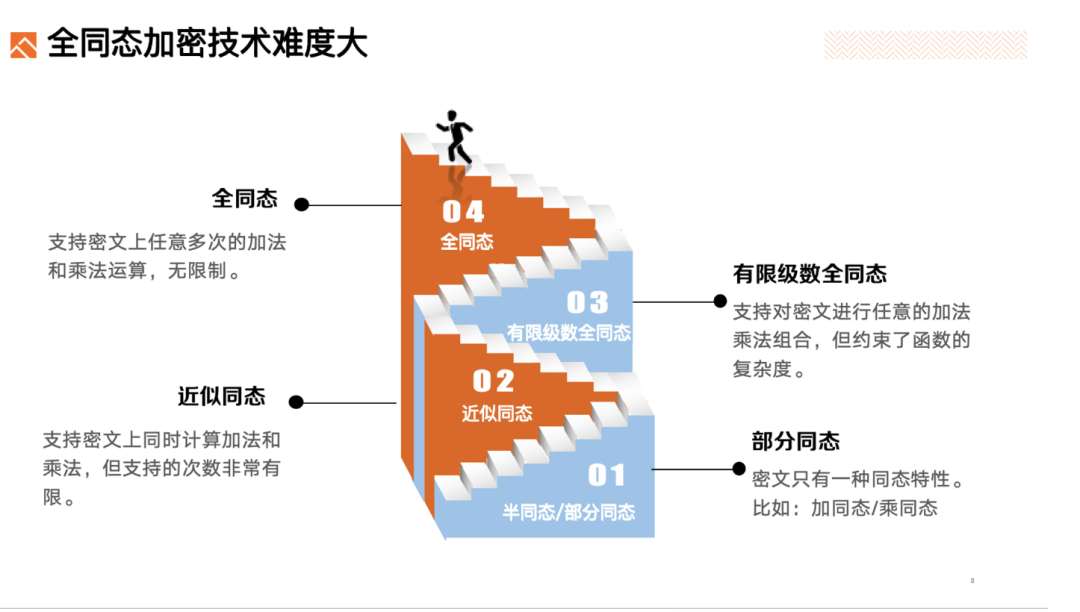
Partially Homomorphic Encryption: It is easier and more practical. Partially homomorphic refers to ciphertext having only one type of homomorphic property, such as: additive homomorphism / multiplicative homomorphism.
Somewhat Homomorphic: Allows us to perform addition and multiplication on ciphertexts, but the supported number of operations is very limited.
Limited Series Fully Homomorphic Encryption: Allows us to perform arbitrary combinations of addition and multiplication on ciphertexts, with no limit on the number of operations. However, there is a new complexity limit, which constrains the complexity of functions.
Fully Homomorphic Encryption: Requires support for arbitrary numbers of addition and multiplication operations, with no limits on complexity or number of operations.
Fully Homomorphic Encryption is the most difficult and ideal in this context, often referred to as the "Holy Grail of Cryptography".
1.2 History
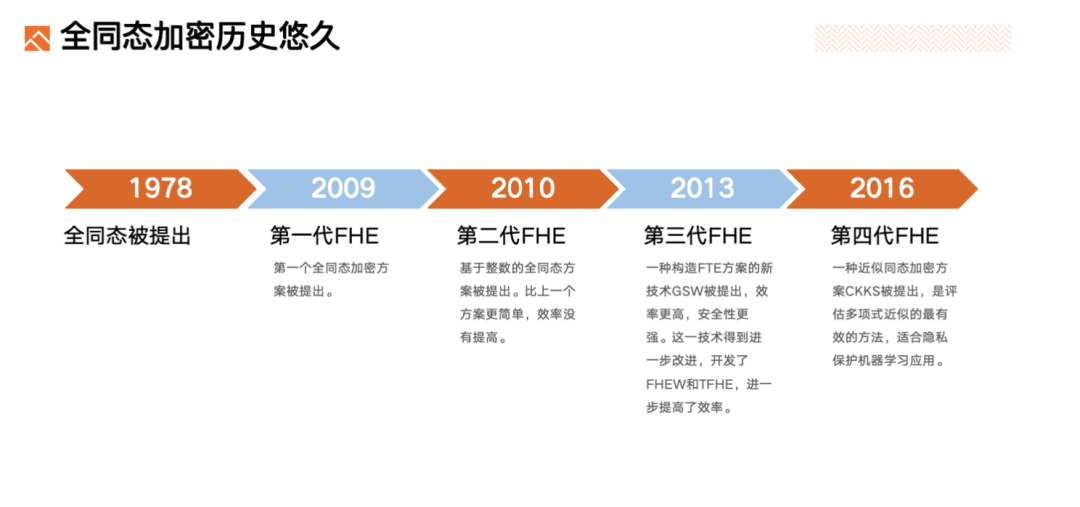
Long history of Fully Homomorphic Encryption
1978: Concept of Fully Homomorphic Encryption was proposed.
2009 (First Generation): The first fully homomorphic scheme was proposed.
2011 (Second Generation): An integer-based fully homomorphic scheme was proposed. It was simpler than the previous scheme, but did not improve efficiency.
2013 (Third Generation): A new technology, GSW, for constructing FTE schemes was proposed, with higher efficiency and stronger security. This technology was further improved, leading to the development of FHEW and TFHE, further improving efficiency.
2016 (Fourth Generation): An approximate fully homomorphic encryption scheme, CKKS, was proposed, which is the most effective method for evaluating polynomial approximations, especially suitable for privacy-protecting machine learning applications.
The commonly used homomorphic encryption libraries mainly support third and fourth generation algorithms. Innovations in algorithms, engineering optimizations, blockchain friendliness, and hardware acceleration are likely to occur with the entry of capital.
1.3 Current Performance and Availability
Commonly used homomorphic encryption libraries:
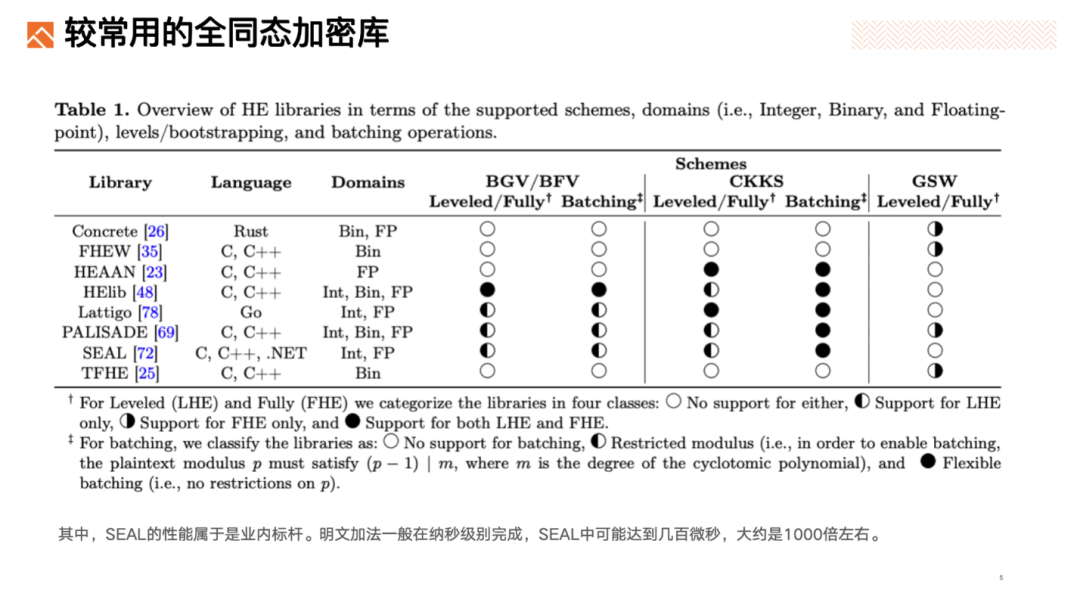
ZAMA TFHE Performance:
For example, the addition and subtraction of 256-bit numbers using ZAMA TFHE takes about 200ms, while plaintext computation takes approximately tens to hundreds of nanoseconds. FHE computation speed is roughly 10^6 times slower than plaintext computation. Some optimized operations are about 1000 times slower than plaintext. Of course, comparing the computation of ciphertext and plaintext is inherently unfair. Privacy comes at a cost, especially for fully homomorphic encryption, an ideal privacy protection technology.
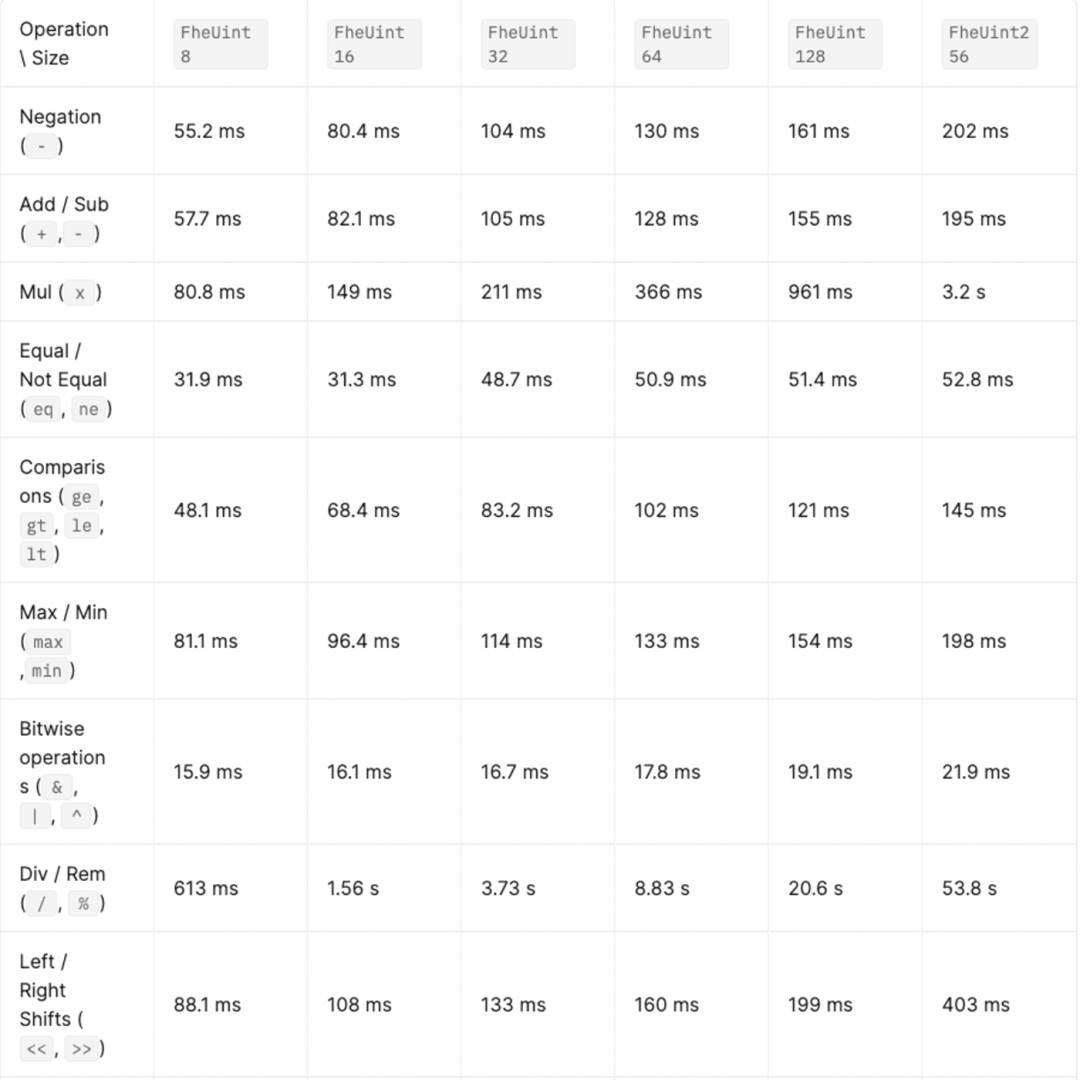
ZAMA plans to further improve performance by developing FHE hardware.
1.4 Several Research Directions for FHE + Web3 Technologies
Web3 is decentralized, and there are many technological directions for combining fully homomorphic encryption with Web3, such as the following.
Innovative FHE schemes, compilers, and libraries to make FHE more user-friendly, faster, and more suitable for blockchain.
FHE hardware to improve computational performance.
FHE + ZKP to use FHE for privacy computation while using ZK to prove that the input and output satisfy certain conditions, or to prove that FHE is executed correctly.
Prevention of malicious operation nodes, which can be combined with EigenLayer restaking, etc.
MPC decryption schemes for sharing encrypted states, often using MPC sharding for keys, requiring a secure and high-performance threshold decryption protocol.
Data storage DA layer requiring higher throughput than the existing Celestia.
In summary, we believe that Fully Homomorphic Encryption is the upcoming next-generation privacy protection technology. FHE has ideal privacy protection capabilities, but its performance still has room for improvement. We believe that with the entry of crypto capital, the development and maturation of the technology will be greatly accelerated, just like the rapid development of ZK in recent years. This track of FHE is worth our attention.
II. Various Privacy Protection Scenarios for FHE in Web3, with a Particular Focus on Privacy EVM
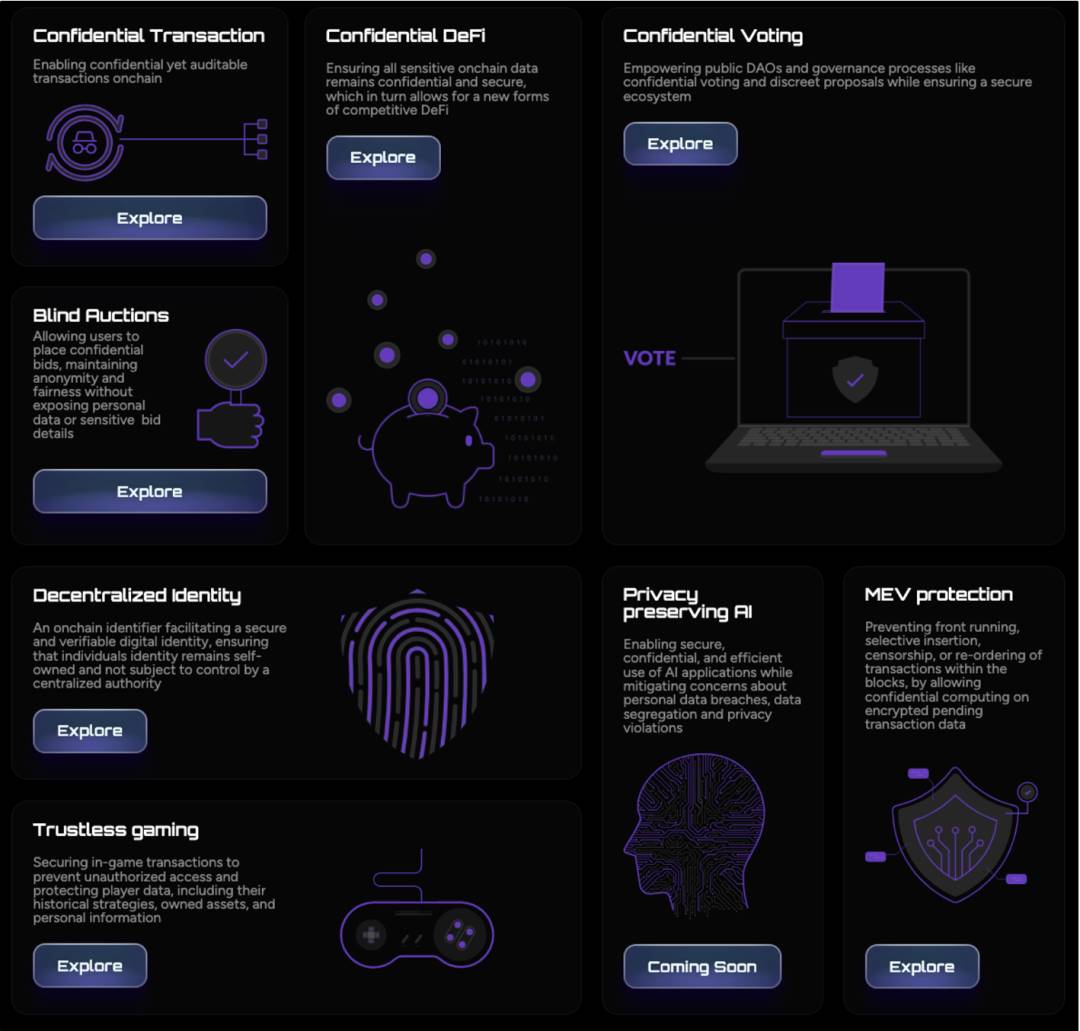
FHE belongs to the privacy protection track. In simple terms, it includes "transaction privacy protection" + "AI privacy protection" + "privacy protection coprocessors".
Transaction privacy protection also includes privacy protection for DeFi, voting, bidding, and preventing MEV, among others.
AI privacy protection also includes decentralized identity and privacy protection for other AI models and data.
Privacy protection coprocessors involve performing fully homomorphic ciphertext operations off-chain and returning the results to the chain, which can be used for Trustless games, among other applications.
Of course, there are various privacy protection technologies, and comparing them will help you understand the uniqueness of FHE.
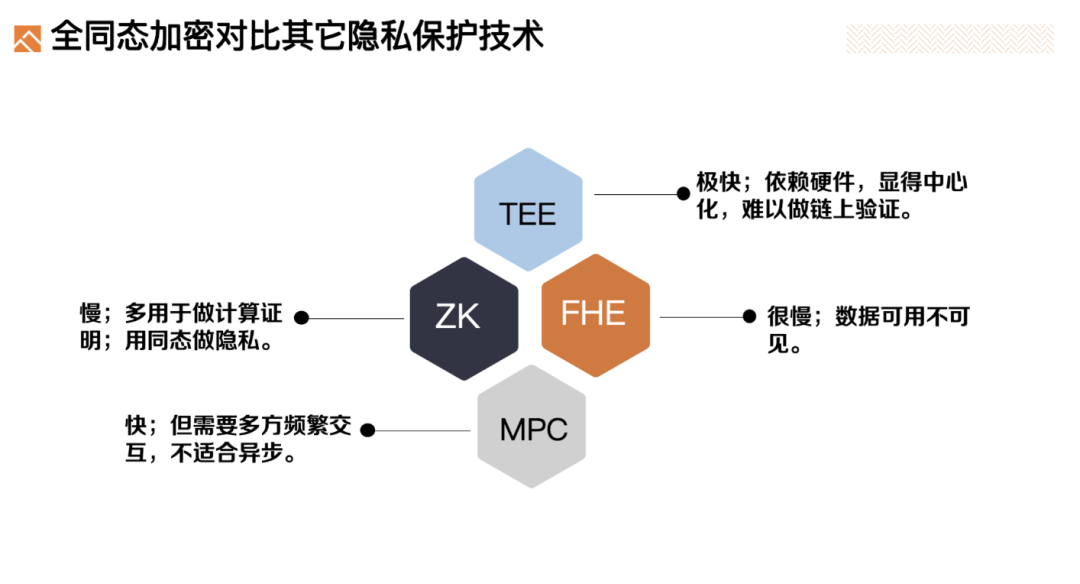
TEE is fast, as data is in plaintext form and computed in trusted hardware, resulting in very fast speeds. However, it relies on secure hardware, essentially trusting the hardware manufacturer rather than the algorithm, making this trust model centralized. Additionally, some TEE computations require remote verification by the TEE manufacturer, which is not suitable for integration into blockchain for on-chain verification. We require on-chain verification, which should only rely on historical data nodes of the blockchain and should not depend on external centralized institutions.
MPC (Secure Multi-Party Computation) is also a privacy-protecting multi-party computation technology. However, this technology often requires multiple parties to be online simultaneously and involves frequent interactions, making it generally unsuitable for asynchronous scenarios such as blockchain. MPC is often used for decentralized key management, where private keys are not stored in complete form in any one place. Instead, private keys are divided into multiple fragments (or shares), which are stored on different devices or nodes. Only when signing a transaction, multiple fragments participate in a multi-party computation protocol to jointly generate the signature.
ZK (Zero-Knowledge Proofs) is mainly used for computation proofs, proving that a certain computation process is executed correctly, and is rarely used for privacy protection. ZK and homomorphic technologies are closely related, with the privacy protection part also using homomorphic technology.
FHE (Fully Homomorphic Encryption) does not require data exchange midway through ciphertext operations, and can be completely computed on servers/nodes. Therefore, it does not require the initiating party/multiple parties to be online, making it more suitable for use in blockchain. Additionally, compared to TEE, it is Trustless. The only drawback is its low performance.
Therefore, as long as FHE gradually improves its performance, its privacy protection capabilities will be more suitable for Web3.
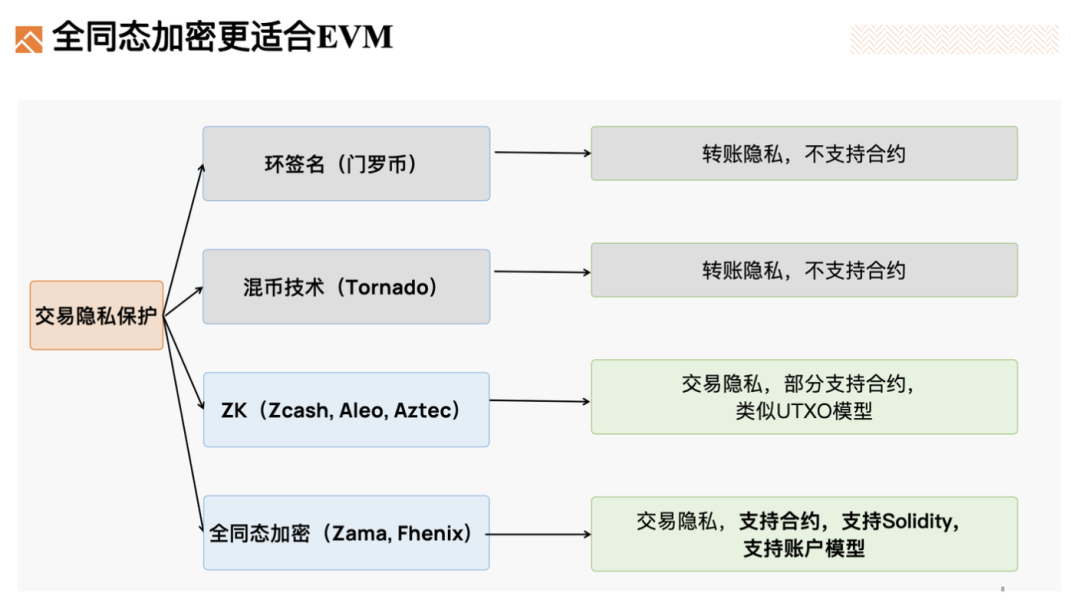
At the same time, in terms of transaction privacy protection, fully homomorphic encryption is also more suitable for EVM. This is because:
Ring signatures and coin mixing technologies do not support contracts.
Privacy data in ZK privacy protection projects like Aleo is similar to the UTXO model, rather than the EVM's account model.
Fully homomorphic encryption can support contracts and account models, making it easy to integrate into EVM.
In comparison, fully homomorphic EVM is indeed very appealing.
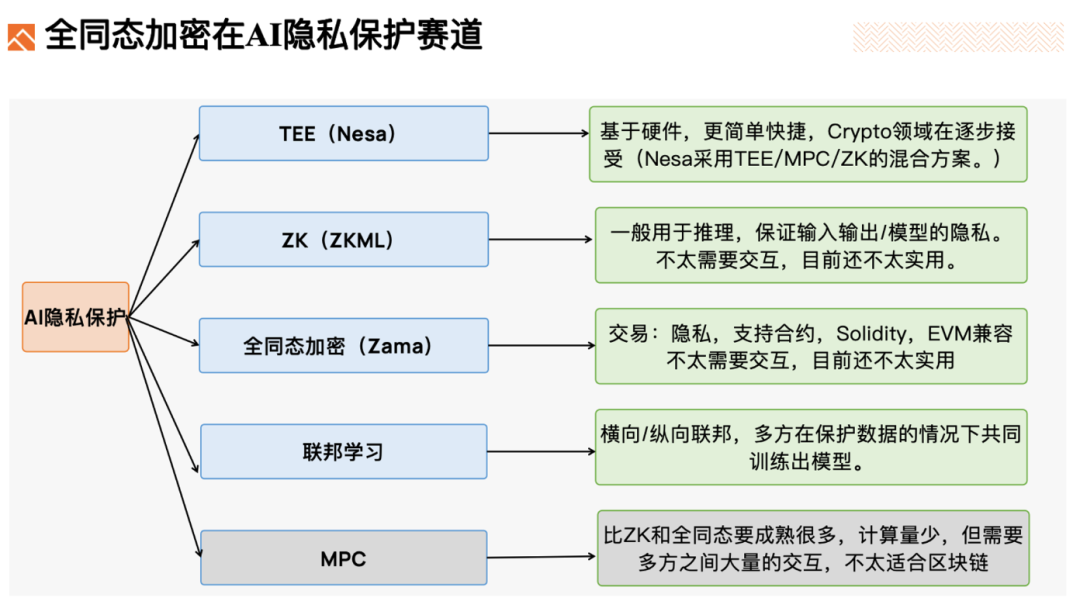
AI computations are already very computationally intensive, and adding such a complex encryption mode as fully homomorphic encryption may result in low performance and high costs at this stage. I believe that the ultimate privacy protection for AI will be a hybrid solution of TEE/MPC/ZK/semi-homomorphic encryption.
In summary, fully homomorphic encryption can be used in Web3 for transaction privacy protection, AI privacy protection, and privacy protection coprocessors. I am particularly optimistic about privacy protection EVM, which is more flexible and compatible with EVM than existing ring signatures, coin mixing technologies, and ZK.
III. Most FHE projects are expected to launch their mainnet from this year to the first quarter of next year, and we believe that Fhenix is the most outstanding FHE project apart from ZAMA
We have researched some of the outstanding fully homomorphic encryption projects currently available, and here is a brief overview of their information:
3.1 ZAMA (Tool)
Narrative: Provides fully homomorphic encryption for blockchain and AI
Tool: TFHE-rs, a Rust implementation of TFHE
Tool: Concrete, a compiler for TFHE
Product: Concrete ML, privacy-protecting machine learning
Product: fhEVM, privacy-protecting smart contracts
Team: CTO Pascal Paillier, a renowned cryptographer
CTO & co-founder: Pascal Paillier, a cryptographer. He obtained his PHD degree from Telecom ParisTech in 1999 and invented the Paillier cryptosystem in the same year. He started publishing papers related to homomorphic encryption in 2013 and is one of the top figures in the field of fully homomorphic encryption.
CEO & co-founder: Rand Hindi, graduated with a Bioinformatics PHD from UCL in 2011, has worked on data science projects, and has served as an advisor for multiple projects while working on ZAMA.
Funding: Over 4 years, a total of over $82 million in funding, with the latest Series A round raising $73 million, led by Multicoin Capital and Protocol Labs.
On September 26, 2023, a Seed Round of $7 million was led by Multicoin Capital, with participation from Node Capital, Bankless Ventures, Robot Ventures, Tane Labs, HackVC, and Metaplanet.
3.2 Fhenix (EVM + AI)
Narrative: FHE coprocessor / L2 FHE Rollup (EVM-compatible privacy L2)
Product: Supports FHE Rollup, a confidential smart contract compatible with EVM. Developers can use Solidity to develop Dapps while ensuring data privacy.
Product: FHE coprocessor, offloads encrypted computing tasks from the main chain (whether Ethereum, L2, or L3) to off-chain. They greatly improve the efficiency of FHE-based operations.
Collaboration: Collaboration with Zama, using ZAMA's fhEVM, forked from ZAMA's library on GitHub.
Collaboration: Collaboration with EigenLayer, Rollup nodes need to be re-qualified in EigenLayer.
Team: Guy Itzhaki has over 7 years of experience at Intel, serving as the Director of Homomorphic Encryption and Blockchain Business Development at Intel.
Founder: Guy Zyskind, MIT PHD Candidate, MSC from MIT in 2016. Involved in the development of the MIT Enigma privacy protocol, possessing strong research capabilities.
CEO: Guy Itzhaki has over 7 years of experience at Intel, with strong expertise in privacy protection, having served as the Director of Homomorphic Encryption and Blockchain Business Development at Intel.
Prof. Chris, Peikert, a cryptographer specializing in fully homomorphic encryption. Cryptography leader at Algorand.
Funding: 1 year, recent Series A funding of $15 million, led by Hack VC, with participation from Foresight Ventures and other institutions.
May 2024, Series A funding of $15 million, led by Hack VC, with participation from Foresight Ventures and other institutions.
September 26, 2023, Seed Round of $7 million, led by Multicoin Capital, with participation from Node Capital, Bankless Ventures, Robot Ventures, Tane Labs, HackVC, and Metaplanet.
Roadmap: Testnet launch in Q2 2024, mainnet launch in Q1 2025.
Q2 2024, launch of the threshold network.
Q3 2024, FHE Co-processor V0.
Q1 2025, mainnet launch.
Q3 2025, FHE Co-processor V1.
3.3 Inco (EVM)
Narrative: Modular privacy computing layer / EVM chain support
Product: Supports FHE Rollup, a confidential smart contract compatible with EVM. Developers can use Solidity to develop Dapps while ensuring data privacy.
Collaboration: Collaboration with Zama, using ZAMA's fhEVM.
Team: Founder Remi Ga, former short-term software engineer at Microsoft and Google, worked on the DeFi project at Parallel Finance.
Founder: Remi Gai, had 6-9 months of software engineering experience at Microsoft and Google 22 years ago, later worked on Parallel Finance, a DeFi project.
Tech lead: Amaury A, core developer at Cosmos.
Funding: Recent Seed round funding of $4.5 million, led by 1kx.
February 2024, Inco Network completed a $4.5 million seed round funding, led by 1kx, with participation from Circle Ventures, Robot Ventures, Portal VC, Alliance DAO, Big Brain Holdings, Symbolic, GSR, Polygon Ventures, Daedalus, Matter Labs, and Fenbushi.
Progress: Testnet launch in March 2024, mainnet launch in Q4 2024.
March 2024, testnet launch including fhEVM. Currently includes examples of privacy-protected ERC-20, privacy voting, blind auctions, and privacy DID.
Q2-Q3 2024, testnet launch including fhEVM.
Q4 2024, mainnet launch.
Plans for 2025 include FPGA hardware acceleration, aiming for TPS of 100-1000.
3.4 Mind Network (AI&DePIN)
Narrative: Privacy protection and privacy computing for data. AI and DePIN data and models.
Product: Originally a privacy data lake in 2023, providing privacy-protected data storage and computing. This year, it has been adjusted to focus on privacy protection for AI and DePIN data and models.
Collaboration: Collaboration with ZAMA, using ZAMA's fully homomorphic library.
Collaboration: Collaboration with Fhenix, Inco, using fhEVM for Rollup.
Collaboration: Collaboration with Arweave for storing encrypted data.
Collaboration: Collaboration with EigenLayer, Babylon, and others for service node restaking: FHE Secured Restaking Layer: Scaling Security for AI DePIN Networks
Team: CTO George was a researcher at the University of Cambridge.
Co-founder & CTO: George was a researcher at the University of Cambridge, served as a technology executive at multinational banks, and has years of experience in internet finance technology.
Funding: 2 years, Seed funding of $2.5 million, incubated by Binance Labs.
June 20, 2023, Seed Round of $2.5 million, led by Binance Labs, with participation from HashKey, SevenX, and others.
RoadMap: Testnet is already live, currently featuring a restake function. The rest of the roadmap has not been disclosed.
3.5 Privasea (AI&DePIN)
Narrative: Privacy computing for AI and DePIN.
Product: Using FHE to train ML models. Optimizing Boolean gates of TFHE.
Product: FaceID, privacy-protected facial recognition. Used for anti-witch and KYC purposes.
Collaboration: Integration with BNB Greenfield for storing encrypted data.
Team: CTO Zhuan Cheng, PhD in Mathematics from the University of Chicago, with extensive experience in cryptography technology development.
CEO: David Jiao, previously raised $20 million for AI projects and $4 million for blockchain projects.
CTO Zhuan Cheng, PhD in Mathematics from the University of Chicago, with extensive experience in cryptography research and previously worked on NuLink's ZK privacy protection project.
Funding: 1 year, Seed funding of $5 million, incubated by Binance Labs.
March 2024, Seed Round of $5 million, incubated by Binance Labs, with participation from MH Ventures, K300, Gate Labs, 1NVST, and others.
Roadmap: Testnet V2 release in April 2024, mainnet launch in Q3 2024.
January 2024, Testnet V1.
April 2024, Testnet V2.
Q3 2024, TGE.
3.6 Optalysys (Tools)
Narrative: Homomorphic encryption hardware.
From the above information, it is evident that ZAMA provides the core open-source library for fully homomorphic encryption to these projects, making them the current undisputed technological leaders. However, ZAMA has not yet announced any plans for token issuance, so our focus is on Fhinex.
Fhinex will implement a privacy-protected EVM to enable privacy-protected smart contracts. They plan to build Fhenix L2, which is a fully homomorphic privacy EVM, providing privacy-protected transactions and DeFi. This L2 also includes a threshold network for some encryption and decryption operations. Additionally, Fhenix will establish an FHE co-processor, a fully homomorphic computing network that can serve EVM chains outside of Fhenix, providing fully homomorphic computing services.
The Fhinex team has strong technical expertise, with team members including experts responsible for privacy computing at Intel, a PHD involved in Enigma privacy protocol development at MIT, and the cryptography lead at Algorand.
In conclusion, we believe that fully homomorphic encryption projects such as ZAMA and Fhinex can bring ideal privacy protection tools to the blockchain.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



