Background
Wallets play a crucial role in the Web3 world. They are not only storage tools for digital assets, but also necessary tools for users to conduct transactions and access DApps. In the previous Web3 security guide, we mainly introduced the classification of wallets and listed common risk points to help readers form a basic understanding of wallet security. With the popularity of cryptocurrencies and blockchain technology, cybercriminals have targeted the funds of Web3 users. According to the stolen forms received by the SlowMist security team, many users have been stolen due to downloading/purchasing fake wallets. Therefore, in this issue, we will explore why fake wallets are downloaded/purchased, the risk of leaking private keys/mnemonics, and provide a series of security recommendations to help users safeguard their funds.
Downloading Fake Wallets
Due to the lack of support for Google Play Store on many mobile phones or due to network issues, many people download wallets from other sources, such as:
Third-party download sites
Some users download wallets from third-party download sites such as apkcombo, apkpure, etc. These sites often claim that their apps are downloaded from a mirror of Google Play Store, but what is the actual security of these apps? The SlowMist security team has conducted investigations and analysis of third-party sources of Web3 fake wallets, and the results show that the wallet version provided by the third-party download site apkcombo does not actually exist. Once users create or import wallet mnemonics on the start page, the fake wallet will send the mnemonics and other information to the phishing website's server.

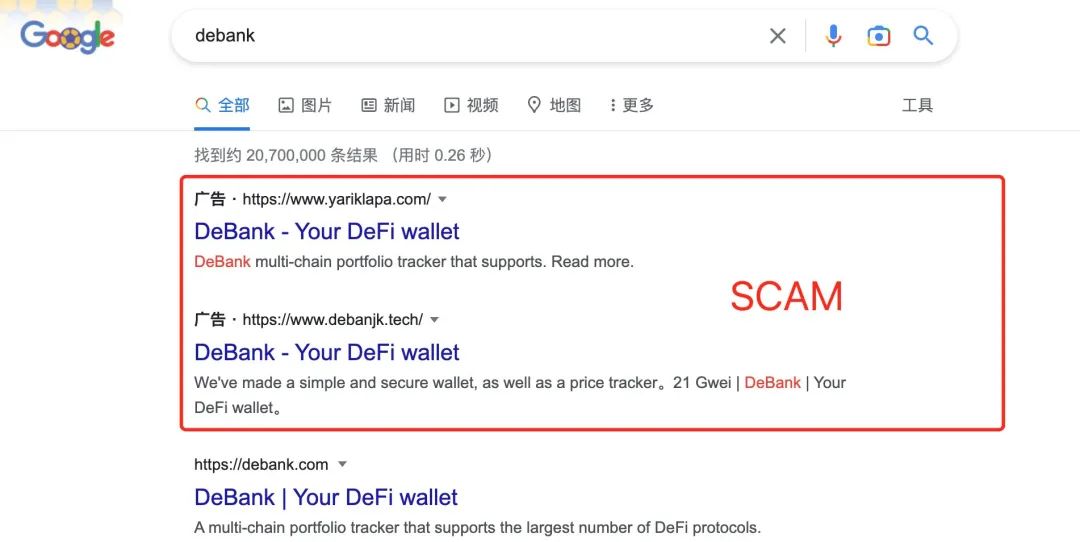
Search engines
Search engine result rankings can be manipulated, leading to cases where fake official websites rank higher than the real ones. Therefore, it is not recommended for users to directly search for wallets through search engines and then download wallets by clicking on the top-ranking links, as this may lead to downloading a fake wallet. In situations where users are not sure of the official website's URL, it is difficult to determine whether a website is fake based solely on its display page, as scammers create fake websites that are extremely similar to the real official websites, making it difficult to distinguish between the two. Therefore, it is also not recommended for users to click on links shared by other users on platforms such as Twitter, as these are often phishing links.
Friends/Family/Pyramid schemes
In the dark forest of blockchain, maintaining zero trust is crucial. Your friends and family may not have the intention to harm you, but the wallets they download may be fake and have not yet been stolen. Therefore, if you download a wallet through the QR code/link shared by them, you may also download a fake wallet.
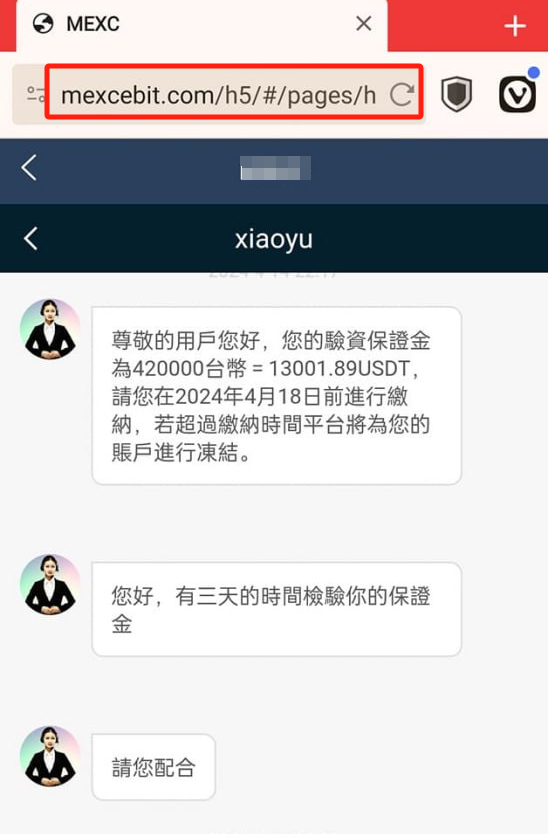
The SlowMist security team has received many stolen forms related to pyramid schemes, where scammers first gain the trust of the victim, then guide the victim to participate in cryptocurrency investments and share the download link of a fake wallet, resulting in the victim being emotionally deceived and losing funds. Therefore, users should remain vigilant towards online friends, especially when they are encouraged to invest or receive unclear links, and should not easily trust them.

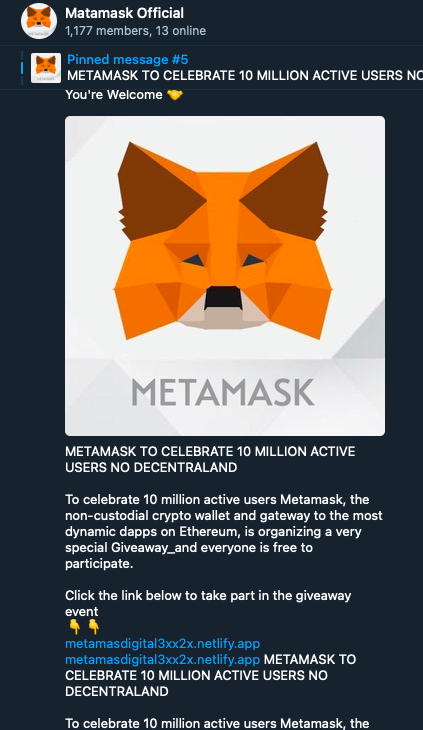
Telegram
On Telegram, when searching for well-known wallets, we found some fake official groups created by scammers, who claim that the group is the official channel of a certain wallet and even remind users in the group to recognize the unique official website link. However, these links are all fake.
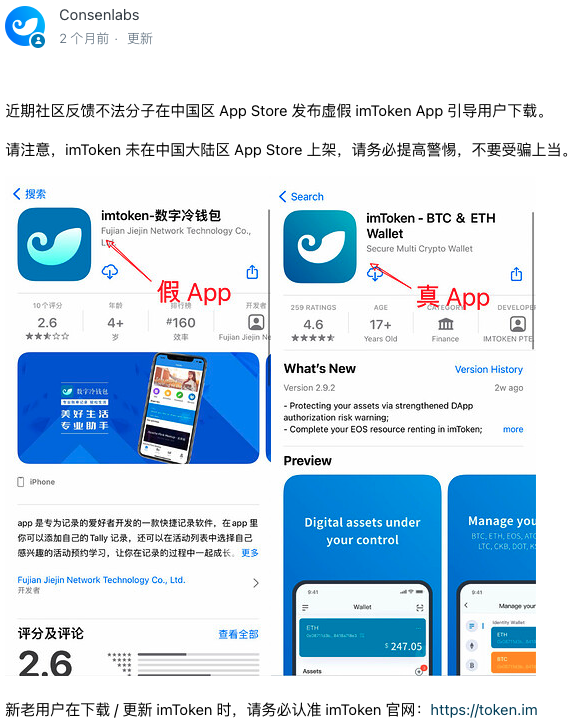
App Store
It is important to note that not all apps in the official app store are safe. Some criminals induce users to download fraudulent apps through methods such as purchasing keyword rankings. Readers should pay attention to discernment.
So, how can users avoid downloading fake wallets?
Official website download
The ability to find the real official website is not only useful when downloading wallets, but also when users participate in Web3 projects later on. Therefore, we will explain how to find the correct official website here.
Users may directly search for the project on Twitter, and then judge whether it is an official account based on the number of followers, registration time, and whether it has a blue or gold badge. However, all of these can be falsified. We have previously warned about the sale of high imitation accounts in the article "True and False Project Parties | Beware of High Imitation Accounts in the Comment Area." Therefore, we recommend that newcomers first follow some security companies, security practitioners, and well-known media outlets on Twitter to see if they have followed the official account you found.
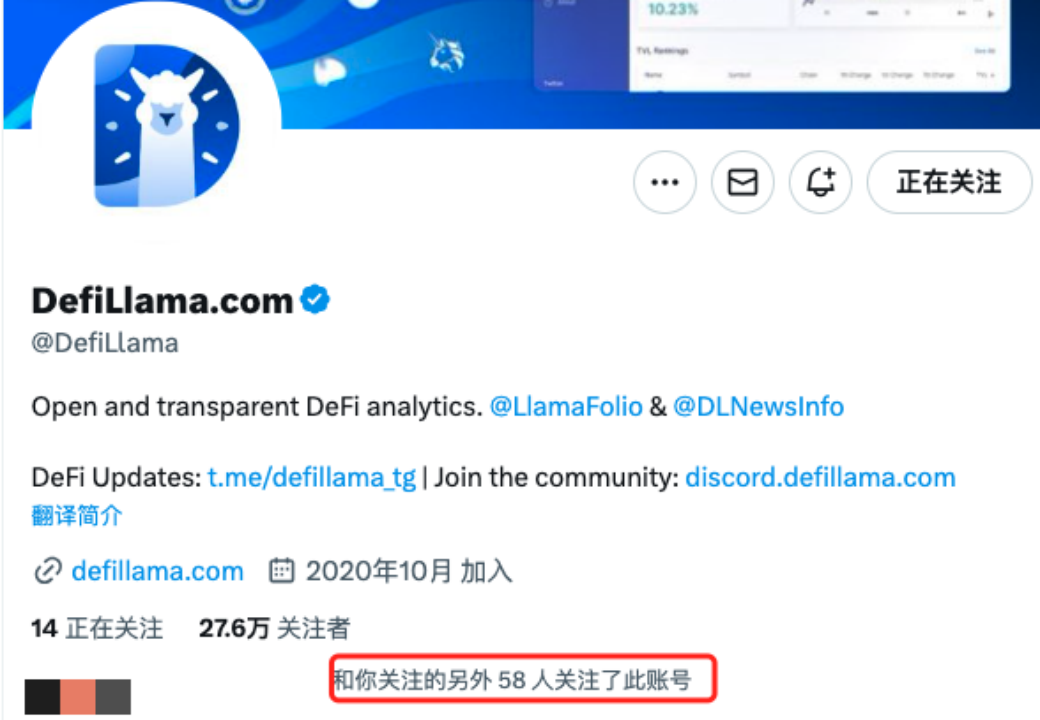
(https://twitter.com/DefiLlama)
Using the above method, users will most likely find the real official Twitter account. However, multiple verifications are still needed, as incidents of official Twitter accounts being hacked are not uncommon. Hackers may also replace the official website link on the official account with a fake official website link. Therefore, users need to compare the official website link they just found with the link found through other channels (such as DefiLlama, CoinGecko, CoinMarketCap, etc.):
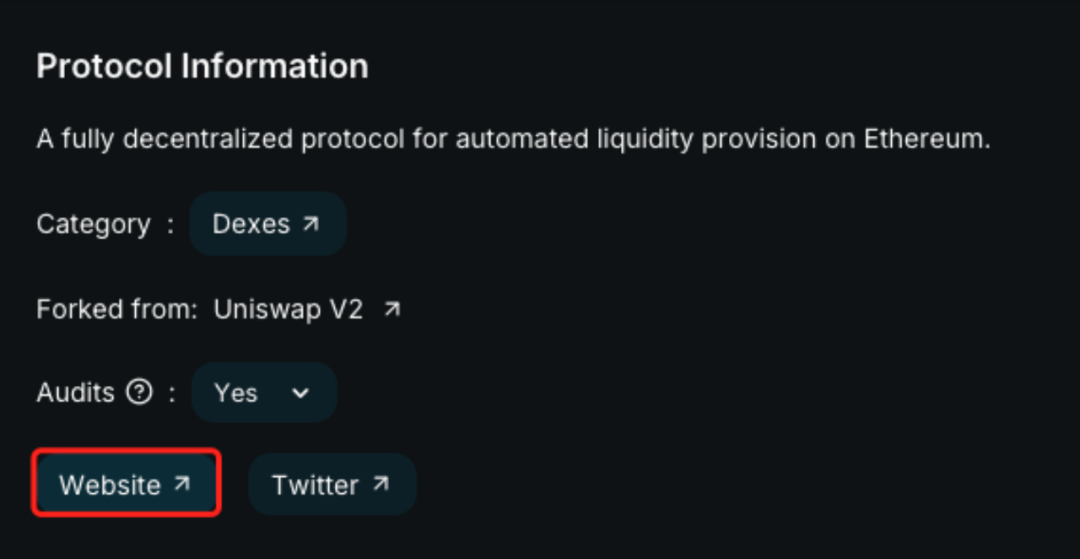
(https://defillama.com/)
(https://landing.coingecko.com/links/)
After finding and confirming the official website link, it is recommended that users save the link to their bookmarks. This way, they can directly find the correct link from their bookmarks next time, without having to search and confirm it every time, reducing the probability of entering a fake official website.
App Store
Users can download wallets through official app stores such as Apple Store, Google Play Store, etc. However, before downloading, be sure to check the app developer information to ensure that it matches the developer identity announced by the official source. Users can also refer to app ratings, download counts, and other information.
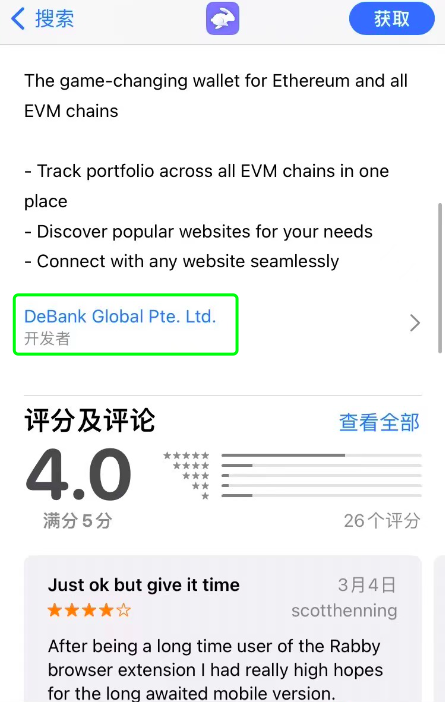
Official Version Verification
Some readers may wonder how to verify if the downloaded wallet is genuine. Users can perform file integrity verification, which compares the hash value of the file to determine if the file has been altered during transmission or storage. Users only need to drag the previously downloaded APK file into the file hash verification tool, which will use hash functions (such as MD5, SHA-256, etc.) to generate the file's hash value. If this value matches the official hash value, it is a genuine wallet; if it does not match, it is a fake wallet. If a user verifies that their wallet is fake, what should they do?
1. First, confirm the scope of the leak. If you only downloaded a fake wallet but did not enter the private key/mnemonic, simply delete the app and download the official version again.
2. If the private key/mnemonic has been imported into the fake wallet, it means that the private key/mnemonic has been leaked. Please download the genuine wallet from the official website and import the private key/mnemonic, then create a new address to quickly transfer the transferable assets.
3. If your cryptocurrency is unfortunately stolen, we will provide free community assistance for case assessment. You only need to submit a form according to the classification guidelines (funds stolen/scammed/extorted). At the same time, the hacker addresses you submit will also be synchronized to the InMist threat intelligence cooperation network for risk control. (Note: Submit the Chinese form at https://aml.slowmist.com/cn/recovery-funds.html, and the English form at https://aml.slowmist.com/recovery-funds.html)
Purchasing Fake Hardware Wallets
The above explains why fake wallets are downloaded and the solutions. Now, let's talk about why fake hardware wallets are purchased.
Some users choose to purchase hardware wallets from online stores, but non-official authorized store hardware wallets have significant security risks. Before the wallet reaches the user, it may have passed through many hands, and it is uncertain whether the internal components have been tampered with. If the internal components have been tampered with, it is difficult to detect the problem from the appearance and functionality.
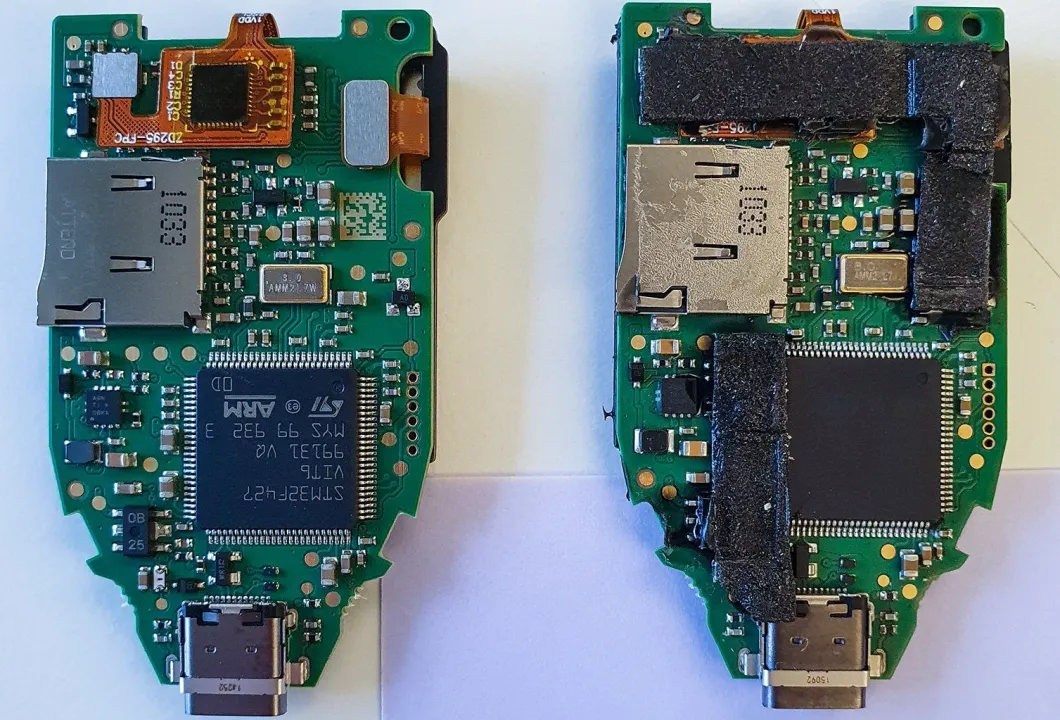
(https://www.kaspersky.com/blog/fake-trezor-hardware-crypto-wallet/48155/)
Here are some methods we provide to counter hardware wallet supply chain attacks:
Purchase from Official Channels: This is the most effective way to address supply chain attacks. Do not purchase hardware wallets from unofficial channels, such as online stores, purchasing agents, or friends.
Check the Appearance: Upon receiving the wallet, first check if the outer packaging shows any signs of tampering. This is the most basic step, although hackers are unlikely to be exposed at this stage.
Official Website Device Verification: Some hardware wallets provide an official website device verification service. When the user initializes the wallet, the device will prompt the user to perform an official website device verification. If the device has been tampered with during transportation, it will not pass the official website device verification.
Disassembly Self-Destruction Mechanism: Users can choose to purchase hardware wallets with a disassembly self-destruction mechanism. When someone attempts to open the hardware wallet and tamper with the internal components, it will trigger the self-destruction mechanism, and all sensitive information in the secure chip will be automatically erased, rendering the device unusable.
Risk of Leaked Private Keys/Mnemonics
Through the above content, everyone should have learned how to download or purchase genuine wallets. Now, the question is how to safeguard private keys/mnemonics. Private keys/mnemonics are the unique credentials for wallet recovery and asset control. The private key is a 64-character hexadecimal string composed of letters and numbers, while the mnemonic generally consists of 12 words. The SlowMist security team reminds that if the private key/mnemonic is leaked, the wallet assets are highly likely to be stolen. Let's look at some common reasons for the leakage of private keys/mnemonics:
Improper Confidentiality: Users may tell their private keys/mnemonics to friends and family to help them store them, only to have their funds stolen by those friends and family.
Network Storage or Transmission of Private Keys/Mnemonics: Some users, despite knowing that private keys/mnemonics should not be shared, save them through methods such as WeChat favorites, taking photos, screenshots, cloud storage, or memos. Once these platform accounts are collected and successfully hacked, the private keys/mnemonics can be easily stolen.
Copy-Pasting Private Keys/Mnemonics: Many clipboard tools and input methods upload the user's clipboard records to the cloud, exposing the private keys/mnemonics to an insecure environment. Additionally, trojan software can steal information from the clipboard when the user copies private keys/mnemonics. Therefore, it is not recommended for users to copy-paste private keys/mnemonics, as this seemingly harmless behavior actually carries a high risk of leakage.
So, how can private keys/mnemonics be safeguarded from leakage?
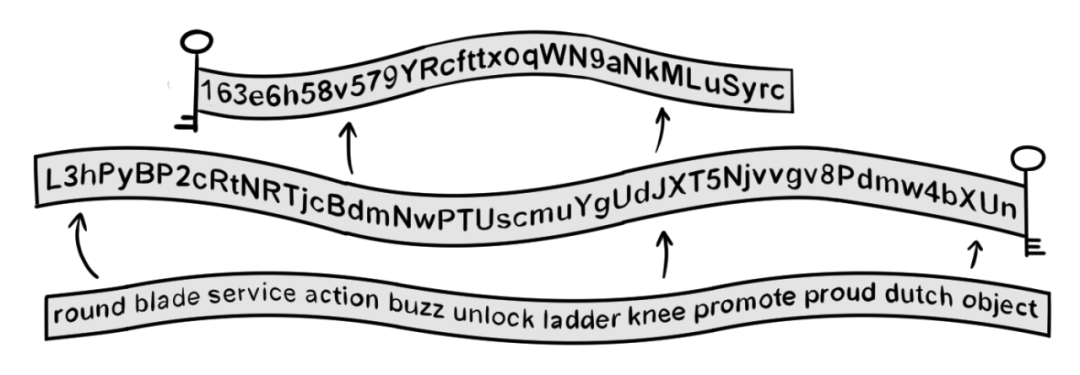
First, do not tell anyone, including friends and family, your private keys/mnemonics. Second, try to save private keys/mnemonics on physical media to avoid hackers obtaining them through network attacks. For example, write the private keys/mnemonics on high-quality paper (which can also be laminated) or use a mnemonic box for storage. Additionally, setting up multi-signature and dispersing the storage of private keys/mnemonics can also enhance their security. For information on how to back up private keys/mnemonics, you can read the SlowMist-produced "Blockchain Dark Forest Self-Guard Handbook" at: https://github.com/slowmist/Blockchain-dark-forest-selfguard-handbook/blob/main/README_CN.md.
Conclusion
This article mainly explains the risks of downloading/purchasing wallets, methods to find genuine official websites and verify wallet authenticity, and the risk of leaked private keys/mnemonics. We hope this content can help everyone take the first step into the dark forest with confidence. In the next issue, we will discuss the risks of using wallets, such as phishing, signing, and authorization risks. Stay tuned. (Ps. The brands and images mentioned in this article are for illustrative purposes only and do not constitute recommendations or guarantees.)
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




