As the airdrop season approaches, some Web3 users have ushered in a golden harvest moment. At the same time, they have also become major targets of criminal gangs in the dark forest of crypto. Bitrace has noticed that some criminals are using high-quality fake Twitter accounts to conduct phishing scams. They are posting a large number of false airdrop claim links in the official Twitter account's comment section, enticing users to click and try to claim tokens. Once users are careless, they may suffer financial losses.
In this context, the "high-quality fake Twitter account phishing scam" as a highly representative industrialized criminal behavior on social media platforms poses a serious threat to the financial security of users due to its highly organized and large-scale operation.
Twitter has become a new battleground for scams
In recent months, Bitrace has received help requests from several victims who had their coins stolen after clicking on "airdrop claim links" on Twitter. These links were actually phishing links posted by high-quality fake accounts of projects such as Etherfi, Tabi, Zeta, and Savm.
Taking the case of a victim of the Etherfi high-quality fake account as an example. On March 15th, ether.fi announced that its token would be listed on well-known exchanges such as Binance and OKX. However, it wasn't until March 18th that the project officially announced the airdrop query link. Criminals took advantage of the 3-day gap and spread false $ETHFI claim links on Twitter, causing victims to mistakenly believe they were real, click on the phishing link, and lose 136.2 ETH. The phishing webpage is now inaccessible, and the high-quality fake account has also disappeared without a trace. (The real account is @etherfi, and the fake account in the image below is @ethersfi)
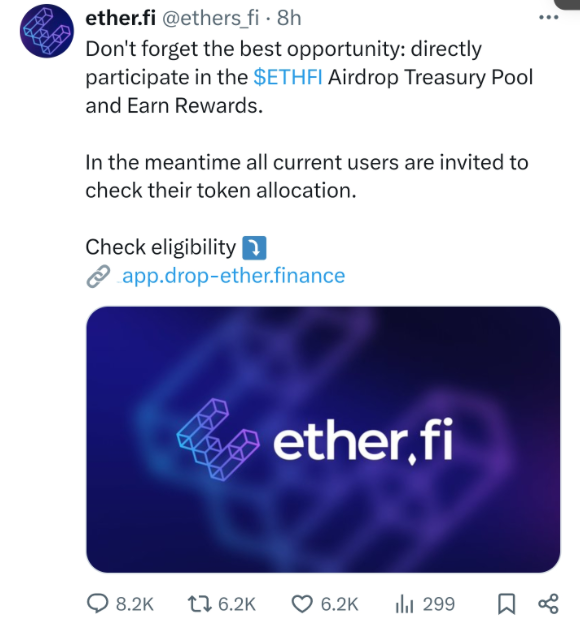
Fake link from a high-quality fake account appearing on the victim's page
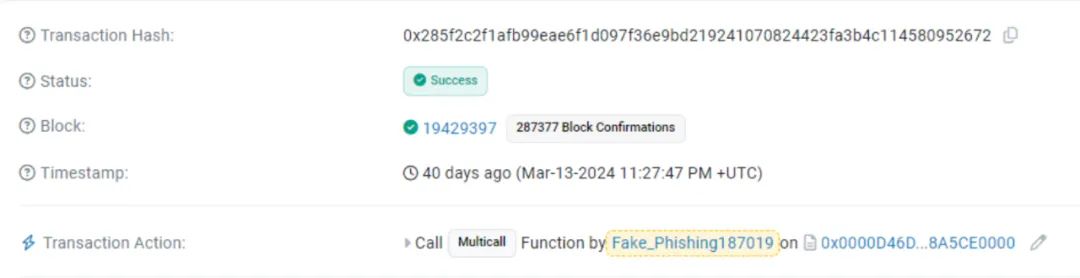
Bitrace's technical team traced the addresses of several victims of such cases and found that the attackers' (spender) addresses for phishing and stealing coins were all marked as Inferno Drainer, with the address 0x0000db5c8B030ae20308ac975898E09741e70000.
Industrialization of high-quality fake account scams
In fact, high-quality fake account scams have become a well-organized black industry chain. From the buying and selling of "crypto-related" Twitter accounts, targeted tweet promotion, extensive deployment of matrix, to the generation of phishing websites, the scam not only has a clear operating process but also involves anonymous scenarios of third-party acceptance of cryptocurrency payments.
1. Purchase of CryptoRelated accounts
Well-known project parties have a large number of fans and accounts with blue checkmark verification, so high-quality fake accounts also need to be close to this. Scammers first buy high-quality Twitter accounts that meet the above conditions, replicate the official account's profile picture and bio, change to a nearly identical ID, and a highly confusing high-quality fake account is created.
Bitrace tried to search for "Twitter account" and other keywords in Telegram and found a large number of Twitter account buying and selling groups. After communicating with multiple parties, it was found that sellers all required cryptocurrency payments. The trading accounts provided by the other party were mostly related to the cryptocurrency industry, with a certain level of daily activity and fan base.
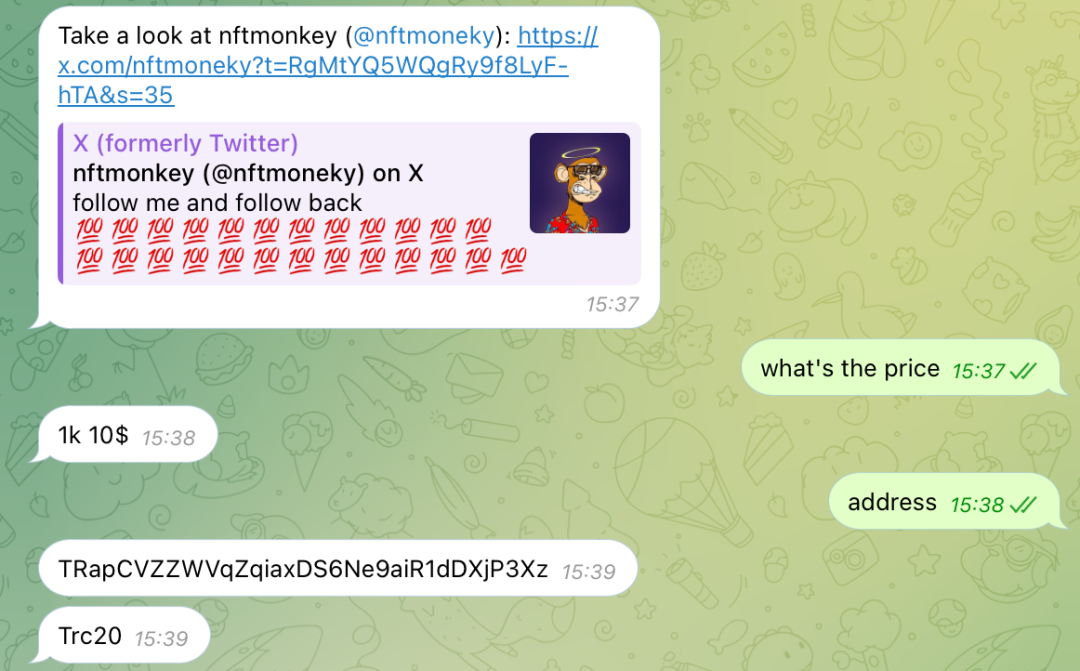
Above is the chat record between Bitrace and a seller
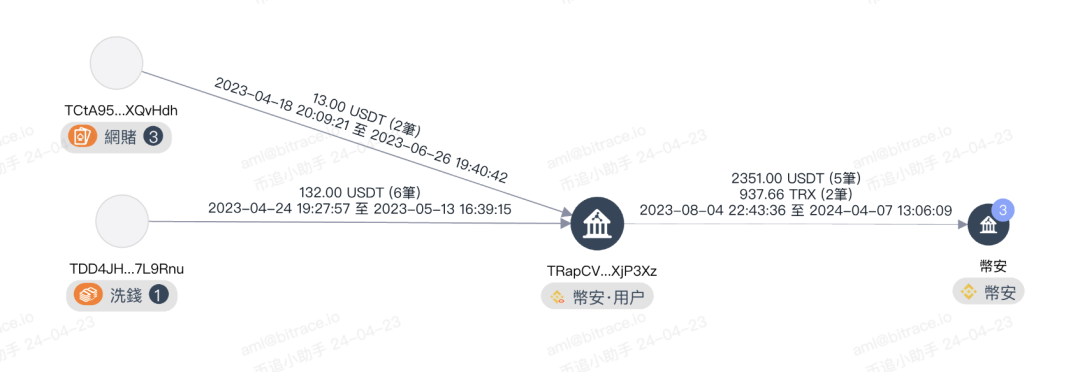
According to the seller's provided receiving address TRapCVZZWVqZqiaxDS6Ne9aiR1dDXjP3Xz, it was found that this address had multiple transactions with high-risk funds marked as "money laundering, online gambling," and this is just the tip of the iceberg. Buying and selling Twitter accounts may seem harmless, but it actually facilitates fraudulent actions by criminals. Why specifically cultivate Crypto Related Twitter accounts for sale, where are the sold accounts used, and did the seller really have no idea?
2. Deployment of multiple accounts with phishing links
Social media platforms such as Twitter have a very mature and clear content recommendation mechanism. By utilizing these rules, fraud gangs can effectively push fraudulent information to the timelines of target audiences:
A common method is to flood the comment section, where high-quality fake accounts post false airdrop claim links under official Twitter account tweets and use rhetoric to imitate and use bots to increase likes, retweets, and replies, gaining the trust of victims and ultimately illegally obtaining token authorization.
Paid third-party promotion service interface
Many victims may be confused by the interaction volume of fraudulent comments. In fact, such volume boosting services are already very widespread and are one of the tools commonly used by the black and gray industries.
Another common method is the pollution of keywords by KOC small accounts. Fraudsters use enticing promotional rhetoric such as "check eligibility, claim airdrop, free NFT minting," and combine them with fraudulent links of specific blockchain protocols to publish tweets. When potential victims search for the protocol name + specific keywords, Twitter is more likely to display fraudulent account tweets, posing a threat to ordinary investors.
3. Purchase of tweet promotion services
In addition to phishing methods that utilize platform recommendation mechanisms, social media platforms such as Twitter and Google are essentially involved in wrongdoing—failing to filter out fraudulent information in paid promotion, leading to paid promotion of phishing links.
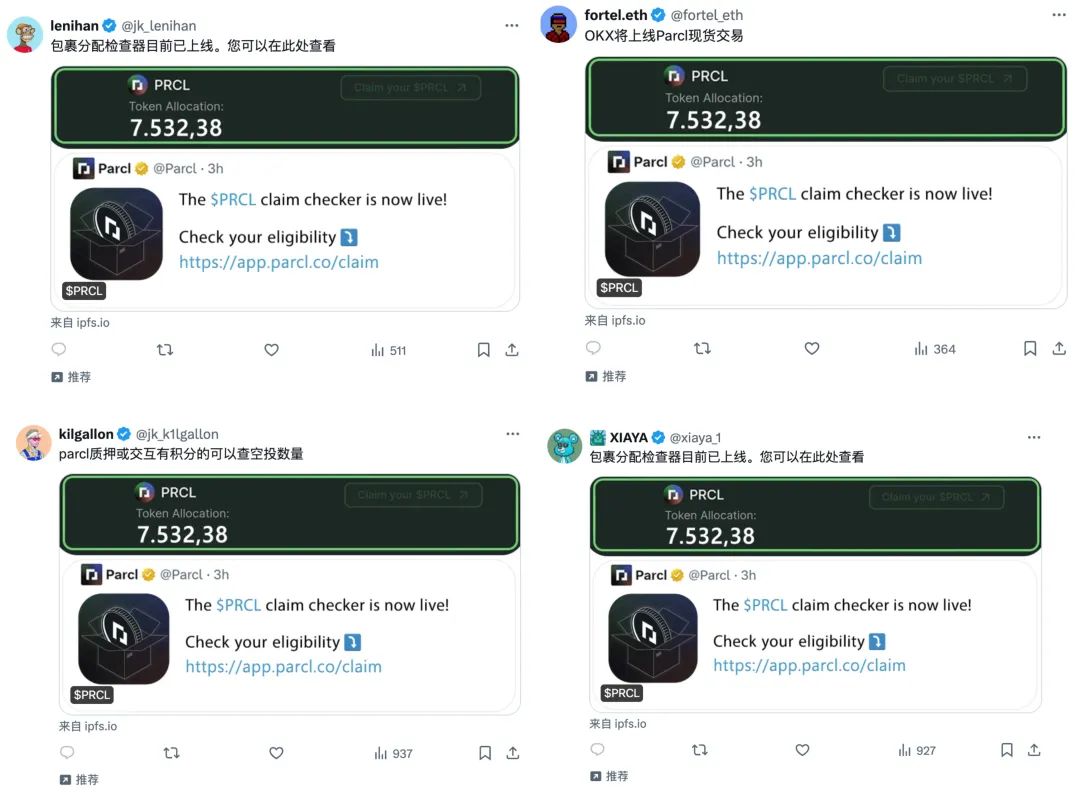
For example, Bitrace found that as soon as the news of the upcoming airdrop of the well-known Solana options project $PRCL was announced, a large number of blue checkmark Twitter accounts began to post phishing links and purchase Twitter promotion services to carry out extensive deployment of multiple accounts, with a large number of identical text and image phishing tweets being densely pushed to the timelines of specific groups.
4. Technical support from the well-known fraud group InfernoDrainer
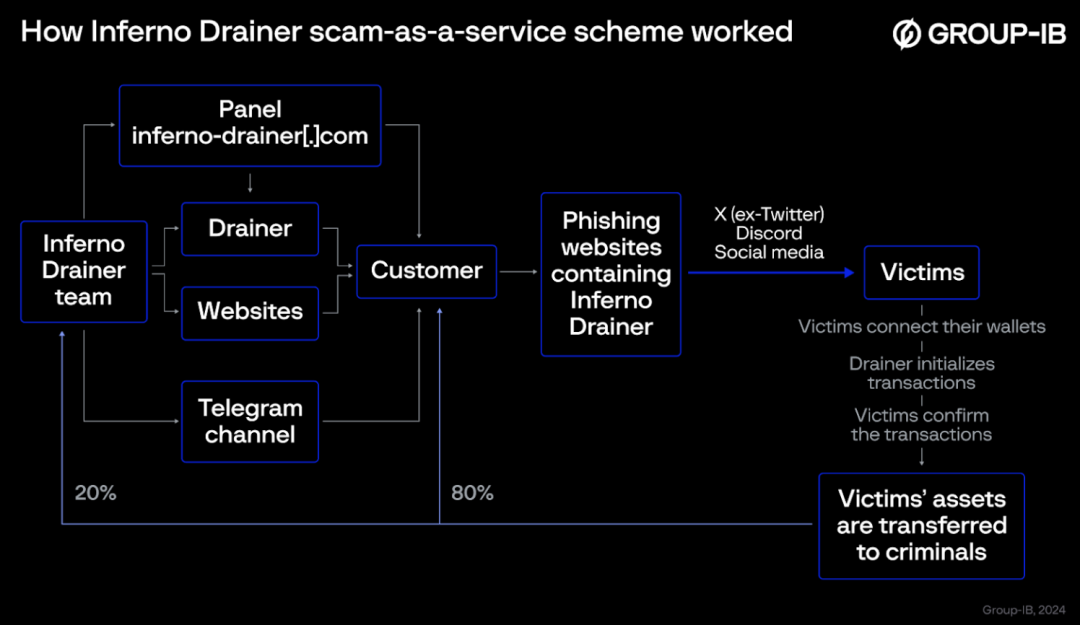
In the cases mentioned above, most of the stolen funds ultimately flowed to the address marked as Inferno Drainer. Inferno Drainer is a type of malicious software designed specifically to illegally empty or "drain" cryptocurrency wallets. This software is provided for rent by its developers, meaning that anyone can pay to use this malicious tool.
SourceGroup-B
Developers provide phishing websites to support the activities of scammers. Once the victim scans the QR code on the phishing website and connects their wallet, Inferno Drainer will check and locate the most valuable and easily transferable assets in the wallet, initiating a malicious transaction. After the victim confirms these transactions, the assets are transferred to the criminals' accounts. 20% of the stolen assets go to the developers of Inferno Drainer, while 80% goes to the scammers.
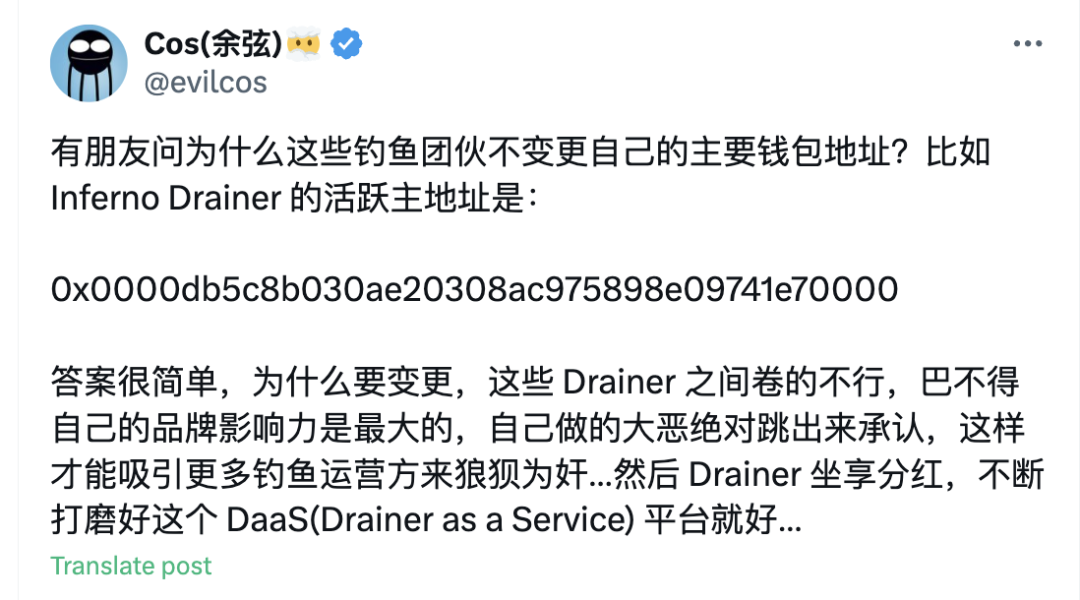
Renowned security practitioner Cosine has previously introduced Inferno Drainer, stating, "Admitting to doing big evil on your own is definitely a way to attract more phishing operators to collaborate." Criminals not only feel no shame in their scams but also use it as a strategy to attract more "operators" to join their ranks, expanding the criminal network and increasing the quantity and scale of criminal activities, which is shocking.
Countermeasures
As the primary channel for Web3 users to obtain firsthand information, Twitter has been contaminated by criminals. Online surfing requires caution, and clicking on links should be carefully considered. Bitrace reminds you:
- Understand the basic mechanisms of social media. Remember the unique ID of the official account, which cannot be replicated by high-quality fake accounts. The number of common followers is an important basis for distinguishing between real and fake accounts. Official accounts often have a large number of followers.
- Verify the authenticity of links through multiple channels. Once a project releases important information such as "airdrop eligibility check" or "airdrop claim," it will not only be announced on Twitter but also on other channels such as Discord, Telegram, and third-party media. Therefore, users can lock in the real airdrop link through multiple channels.
- Identify the pop-up content of wallet plugins. If you are unsure about the details behind a transaction, do not sign it easily.
- Be cautious when clicking on the comment section of long threads. The comment section of official tweets has traffic and is the target audience of scammers, often the most rampant place for phishing links. Project parties have also realized this issue and have added seals after the end of tweets to remind users to beware of scams.
Cryptocurrency network crimes have become more organized and orderly in the wave of industrialization, not only harming the interests of users but also damaging the healthy development of the entire cryptocurrency industry. If you unfortunately suffer losses, you can contact us for assistance at any time.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



