This article provides a deep analysis of the payment and receipt patterns of publicly disclosed addresses, the risks associated with the sources of funds for these addresses, and the activities of related addresses, and discloses the relevant analysis content.
Authors: SlowMist, CoinTrace Team
Background
On January 16, 2024, a blogger on a Chinese social media platform revealed that the Myanmar National Democratic Alliance Army was suspected of forcibly collecting large amounts of cryptocurrency from individuals involved in the telecommunications fraud industry in Myanmar, and displayed the cryptocurrency address claimed to be used for receiving payments. This disclosure has since been widely circulated on the internet.
Bitrace & MistTrack jointly conducted an analysis of the disclosed addresses for encrypted funds, including the patterns of fund receipts and payments, the risks associated with the sources of funds, and the activities of related addresses, with the aim of disclosing the relevant analysis content.
Address Behavior Analysis

(Source: https://mp.weixin.qq.com/s/WDWM22vw68-NsVr0_1jHfA)
The above image is from the disclosed article. Based on this, researchers conducted a USDT exchange rate analysis of the disclosed receiving address TKFsCN, attempting to infer the underlying settlement unit through the receipt of specific amounts of USDT.
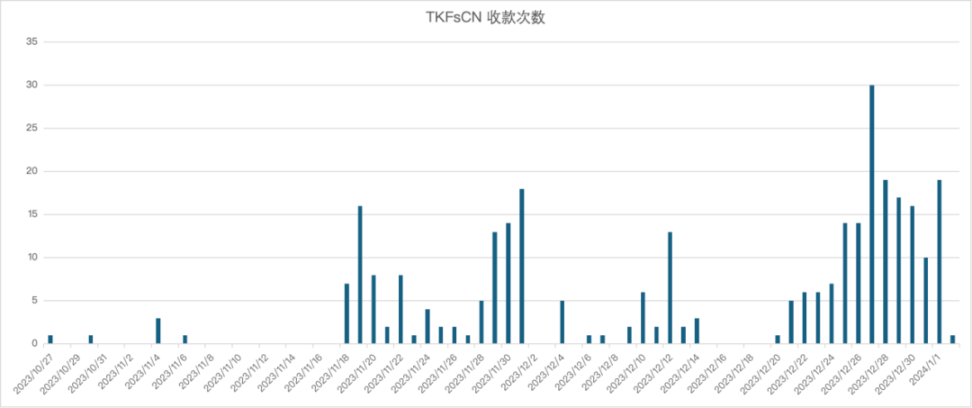
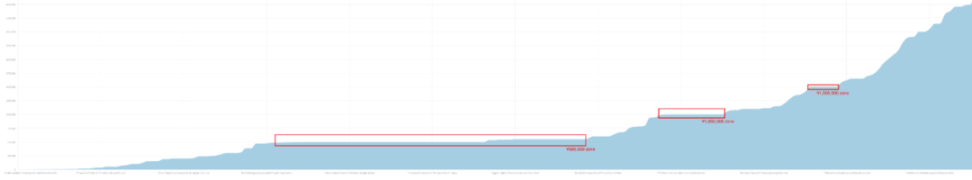
The historical transaction records of the receiving address show that a large number of individual USDT transactions received by this address are non-round numbers, such as 71417 and 42857, which are commonly seen in transactions settled in non-US dollar units. After attempting to calculate using the USDT exchange rate with various major fiat currencies, researchers found that these transactions are suspected to be settled at a rate of 1 USD: 7-7.2 RMB, and the single fund transfer amounts are clustered in the range of 500,000 to 600,000 RMB, 1 million RMB, and 1.5 million RMB.
After filtering out transactions of 100 USDT and below, it was statistically found that out of a total of 307 USDT transfers to TKFsCN, 193 transfers were in RMB to USD exchange rates, accounting for 62.86% of the total number of transactions and 45.29% of the total amount.
This indicates that over half of the transactions received by this address are settled in RMB, and the majority of the converted amounts are in the range of 500,000 RMB. The party paying USDT is likely Chinese.
Analysis of Fund Sources
The original article mentioned, "After occupying the old street, they also caught (note: individuals in the telecommunications fraud industry) Chinese people everywhere. Those willing to pay for self-protection can be sent away, those who do not pay will be sent back to China." If true, there should be a large number of new transaction counterparties in the transactions of TKFsCN, and part of the funds should come from gray/black market, money laundering, fraud, and other related addresses.
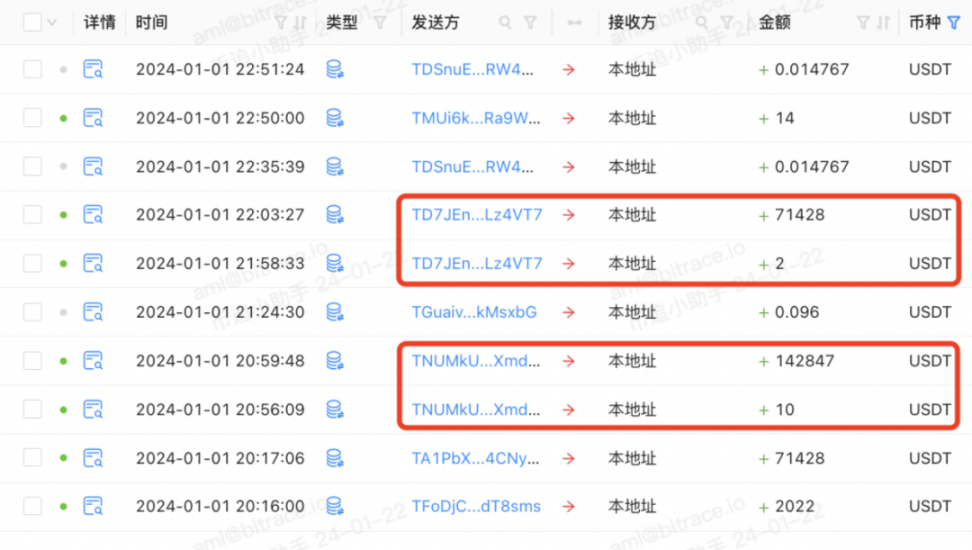
Data shows that between October 22, 2023, and January 2, 2024, TKFsCN received USDT transfers from 182 direct transaction counterparties, with 117 addresses showing the characteristic of small amount + large amount in consecutive two transactions. This is a typical behavior of transfer testing, where the payer does not choose to transfer the entire amount at once to confirm the correctness of the address, indicating that at least 62.29% of the transaction counterparties may be making their first transfer and are not fixed trading partners of TKFsCN.
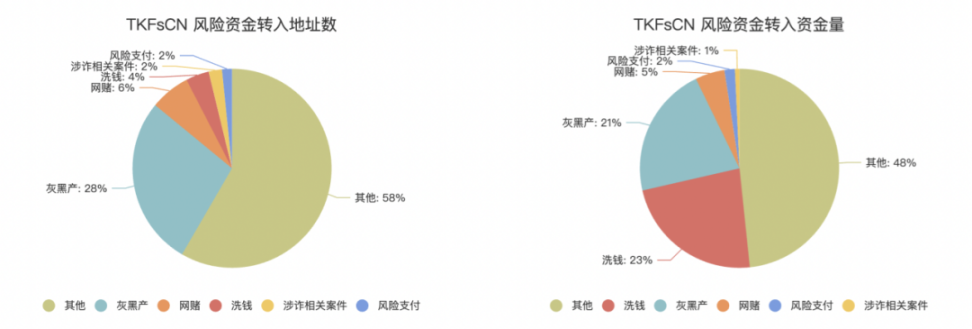
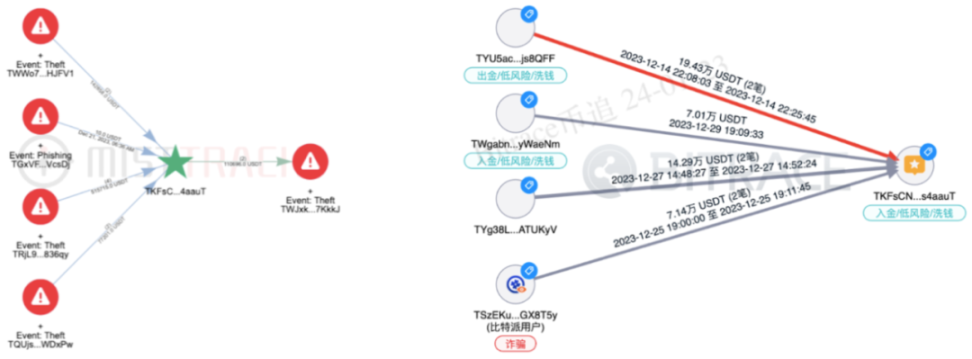
A deeper audit of the risk funds associated with TKFsCN's addresses indicates that among the 182 direct transfer counterparties, as much as 42% are associated with risky activities such as black market, online gambling, fraud, money laundering, and high-risk payments, transferring a total of 33,523,148 USDT to TKFsCN.
(Image source: MistTrack and BitracePro)
It is worth noting that among these risky activity-associated addresses, investigators also found 7 addresses explicitly related to known criminal cases, including two money laundering cases, one fraud case, one online gambling case, and one telephone fraud case, and the suspects' geographical locations are all in northern Myanmar or Cambodia.
This indicates that the counterparties initiating payments to TKFsCN are not only involved in a large number of risky cryptocurrency activities, but are also closely related to illicit individuals in the Southeast Asian region.
Another strange point is that investigators also found a money laundering address associated with a telecommunications fraud case in the outgoing addresses, indicating that there are certain doubts in the upstream analysis of the fund flow of some outgoing addresses. This doubt will be further explored in the "Related Address Analysis" section below.
Related Address Analysis
Based on the clustering analysis of the TKFsCN address mentioned above, it is suspected that this address has a clustering relationship with nearly a hundred other addresses, some of which not only exhibit similar fund receipt and payment activities to TKFsCN, but also reveal more information about the recipients. Taking the recipient address TKKj8G as an example:
- TKKj8G directly received over 4.6 million USDT in total from TKFsCN in 6 transactions, and is one of the collection addresses in the subsequent fund chain;
- TKKj8G is one of the core receiving addresses, and out of 60 transactions with amounts exceeding 100 USDT, as many as 50 transactions exhibit small amount testing behavior similar to TKFsCN;
- TKKj8G has been active since August 18, 2023, much earlier than other addresses, and during this period engaged in transactions with Huiwang Guarantee—receiving 160,000 USDT from Huiwang Guarantee, behaviorally analyzed as a merchant of Huiwang Guarantee retrieving a deposit from Huiwang Guarantee.
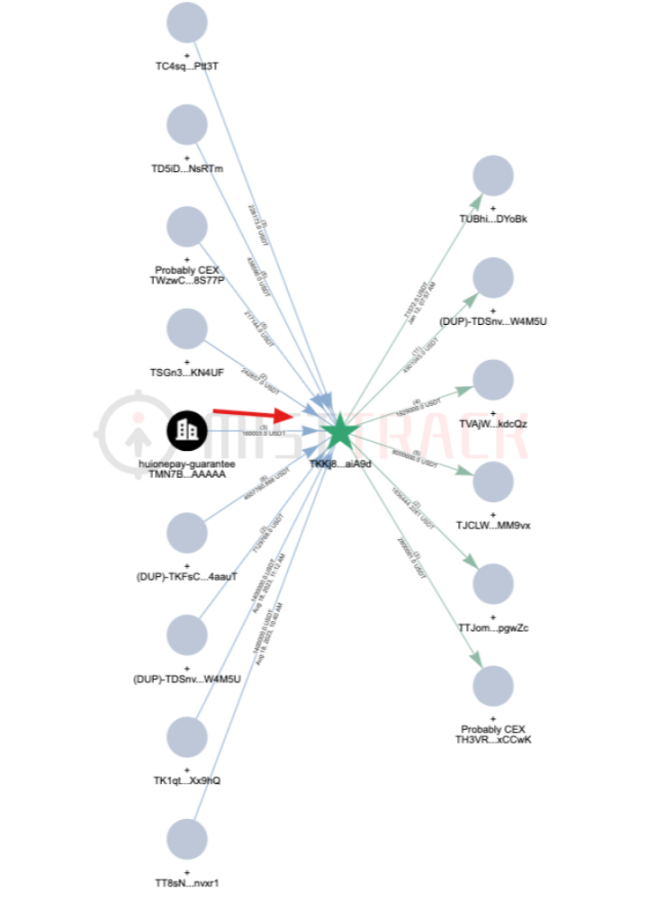
This indicates that the "Finance Department address" mentioned in the original article may not actually exist, and the addresses including TKFsCN and TKKj8G should belong to a digital currency exchange merchant located in northern Myanmar or Cambodia, who is collecting these funds on behalf of some entity for certain reasons.
Unusual Transactions
In summary, investigators can easily outline a typical payer profile—a person engaging in illegal activities in the Southeast Asian region, who, for some reason, has to pay 500,000 RMB worth of USDT to a collection address. To prevent address errors, small amount testing was conducted before a large amount was transferred. The cryptocurrency used for payment either comes from their own illegal gains or is purchased from other illicit entities.
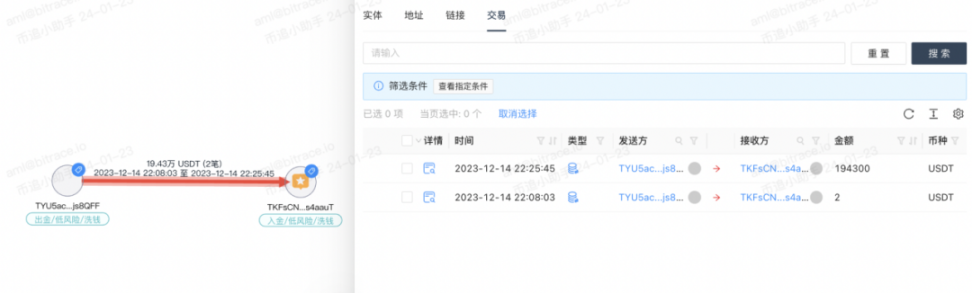
However, not all payers are like this. Investigators also found some addresses that do not fully conform to these characteristics, such as TYU5acSGRwsYJfBhdpQc3broSpfsjs8QFF. This address is one of the 7 directly involved addresses mentioned earlier. The other 6 addresses transferred encrypted currencies worth 500,000, 500,000, 1 million, 1 million, 2.7 million (1.5 million + 1.2 million), and 550,000 RMB to TKFsCN, but the transfer amount for TYU5ac, when converted at the same exchange rate, amounts to 1.36 million RMB, although it is an integer, this particular amount still differs significantly from the other addresses.
Investigators are unable to determine the reason for this. Considering the presence of small amount testing behavior at this address, a reasonable guess is that the transactions behind this address represent the consolidation of 3 transfers worth 500,000 RMB, with a 10% discount applied.
Conclusion
This article provides a deep analysis of the payment and receipt patterns of publicly disclosed addresses, the risks associated with the sources of funds for these addresses, and the activities of related addresses, and discloses the relevant analysis content. The main conclusions are as follows:
- Over half of the transactions received by the target address in this analysis are settled in RMB, and the majority of the converted amounts are in the range of 500,000, 1 million, and 1.5 million RMB.
- The addresses transferring funds to the target address in this analysis are closely associated with black market, online gambling, fraud, money laundering, and high-risk payments.
- Before the target address and its related addresses densely collected these funds, there were already traces of risky business activities. After conducting clustering analysis of the target address, this cluster is suspected to represent a merchant of Huiwang Guarantee.
- The addresses initiating payments to the target address are closely related to illicit individuals in northern Myanmar or Cambodia.
In summary, the content revealed in the article "Alliance virtual currency accounts exposed, extorting billions of virtual currency from people in the northern country" is consistent with on-chain facts. Indeed, there is a large collective of Chinese telecommunications fraud industry practitioners in northern Myanmar or Cambodia transferring integer amounts of RMB-denominated USDT assets to a certain address set. However, this group of addresses may not be the so-called "Finance Department address" as mentioned in the original article, but rather the address of a local digital currency exchange merchant, which is different from what was described in the original article.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




