Previous Review: Mixin is a decentralized asset management network that safeguards assets through sharded encryption of private keys. Due to the founder and technical details, Mixin has sparked a lot of discussion regarding security and compliance since its launch.
Mixin's official statement on September 25, 2023 at 10:50 am announced that the database of Mixin Network cloud service provider was attacked by hackers in the early hours of September 23, 2023, resulting in the loss of some assets on the main network. Preliminary investigations by Google and SlowMist estimated the involved funds to be around 200 million US dollars.
Amidst cheers and anticipation, BTC finally broke through $30,000 based on the news of spot ETF. However, for crypto enthusiasts to achieve financial freedom, besides following market trends, it is essential to protect their assets. Otherwise, even if BTC goes "to da moon," it will be in vain. Cregis has summarized the Mixin theft incident that shocked many half a month ago, hoping to help everyone better safeguard their digital assets in the next bull market!
(Mixin official X releases theft news)
Binance CEO Zhao Changpeng immediately commented on Mixin, stating that he couldn't understand the concept of "a decentralized peer-to-peer network" having a "database," and believed that "not everything claiming to be decentralized is truly decentralized."
(CZ questions the decentralization level of Mixin on X)
So, why would a network claiming to be decentralized be successfully attacked by hackers, and how were users' assets stolen?
To help everyone understand the ins and outs, Cregis Research has compiled three key pieces of information:
Mixin project's product form
Firstly, Mixin is not just an asset management product. The entire project consists of Mixin Network (the nominal ledger of BTC), Mixin Message (a social DAPP, claiming to be comparable to WeChat), and Xin Token (Mixin Network's POS staking tool, also used for trading).
Working principle of Mixin Network
Mixin Network has two core components: the Mixin full node and Mixin Domain.
Mixin Domain is the core of the theft incident! Mixin Domain is actually a component similar to a hot wallet system, providing each Mixin client with an independent Bitcoin deposit address and sharding the private key through Distributed Key Generation (DKG, one of the technical solutions of MPC), which is jointly managed by Mixin Domain and Mixin full node.
After users deposit to the Mixin DAPP address, the assets will eventually be aggregated and saved in a multi-signature address managed jointly by Mixin Domain and Mixin full node, and then the quantity will be mapped to Mixin Network and Mixin DAPP.
The crisis of Mixin also arises from this:
a) The sharding method of DKG is not the orthodox GG18 MPC scheme, and objectively carries the risk of internal and external asset theft due to the existence of the original private key.
b) The sharded keys are saved on Mixin Domain and Mixin full node, and the Mixin official white paper clearly states that there are backups of the shards, objectively carrying the risk of internal and external theft of shards for multi-signature transactions. (This is also the most probable reason for the loss of user BTC after the theft of cloud server data)
c) The assets displayed on Mixin DAPP are not truly BTC, nor are they xBTC executed through smart contracts for cross-chain transactions. They are just points generated by Mixin Network after receiving deposit communications, and are no different from the account balance of centralized exchanges.
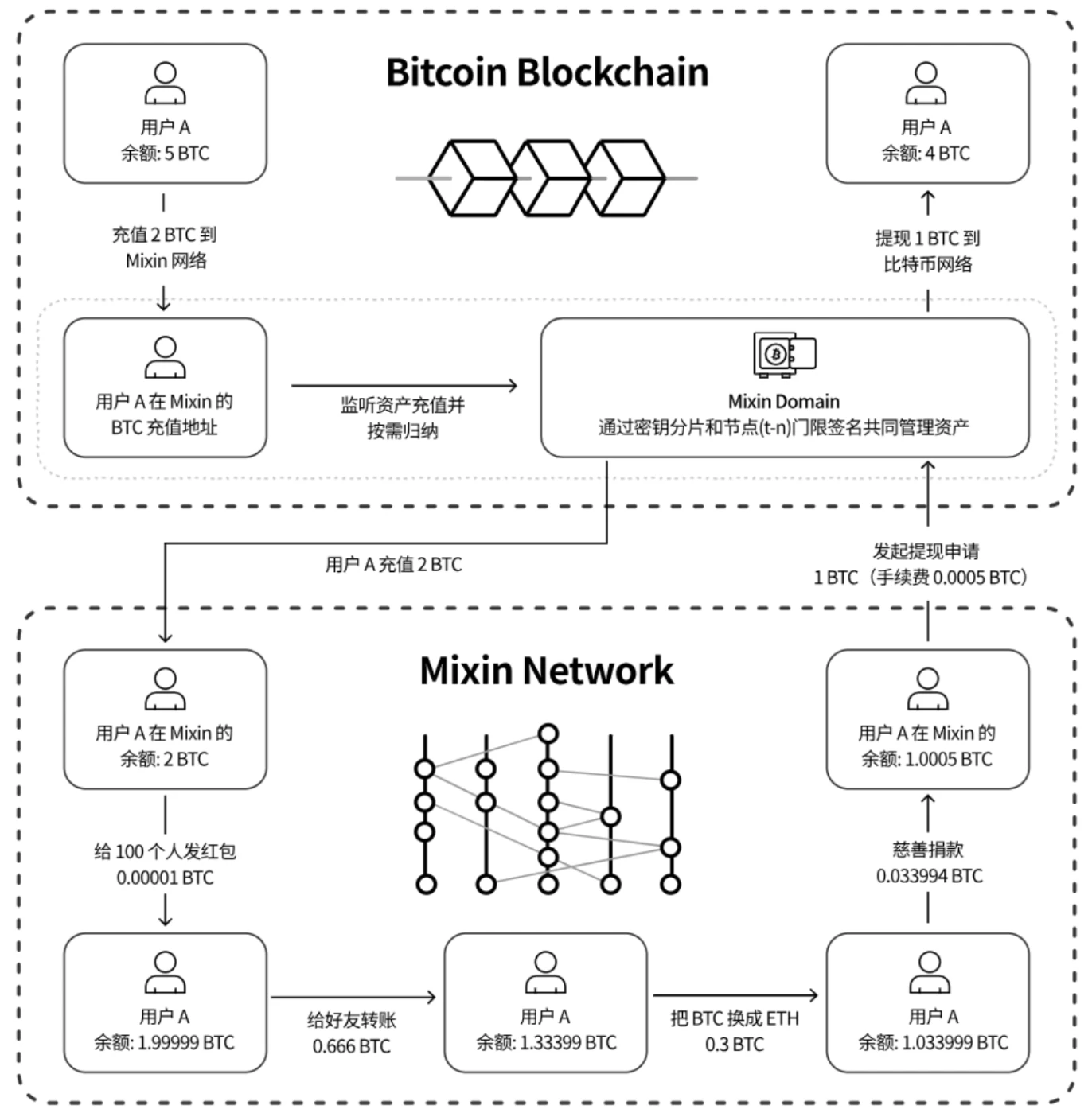
(Using the red envelope function of Mixin message as an example, simulating the working process of Mixin products)
N ways for hackers to steal Mixin clients' BTC
At this point, experienced friends should already know how big the pit of Mixin is, and Cregis Research still sorts out where Mixin clients' BTC are most likely to go from the perspectives of internal and external wrongdoing:
I. Internal wrongdoing (two directions)
If the workflow of Mixin Network is indeed consistent with the description in the white paper, there are two directions for internal wrongdoing:
a) The project party controls 2/3+1 of the full node servers and can initiate multi-signature transactions at any time. Currently, there are about 35 running nodes in Mixin, and based on the core code configuration file of Mixin, it is speculated that the Mixin team operates approximately 27 nodes. Additionally, since running a Mixin full node requires staking about 2 million US dollars' worth of Mixin Tokens, the number of external nodes is far from sufficient. Therefore, it can be ruled out that the multi-signature attack is carried out externally through node servers.
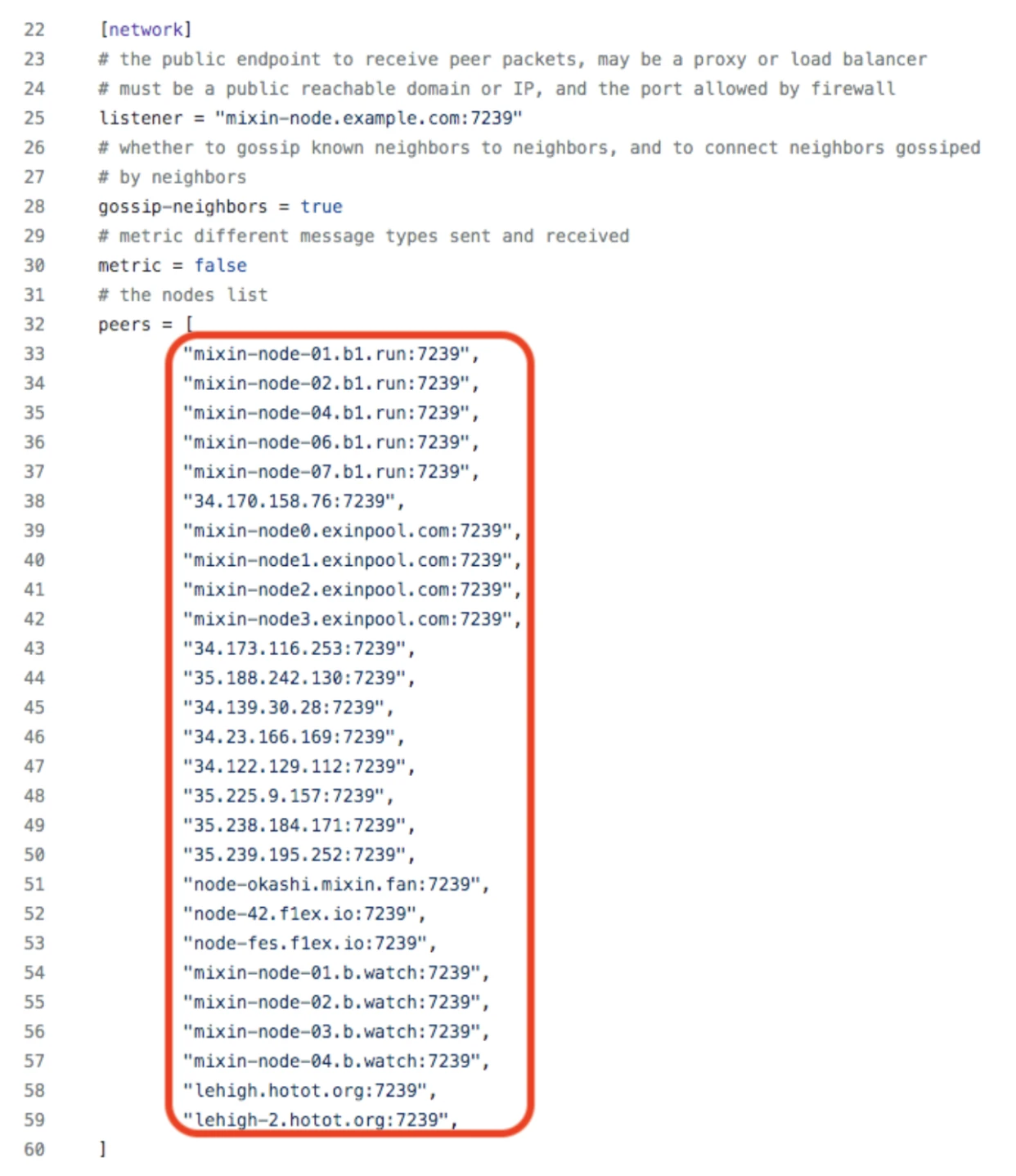
Official configuration document of Mixin network
b) According to Mixin's official white paper, to prevent the loss of key shards, Mixin will make multiple backups of the key shards on official servers. So even if they cannot control the full node servers to sign transactions, they can still use backup private key shards to initiate transactions.
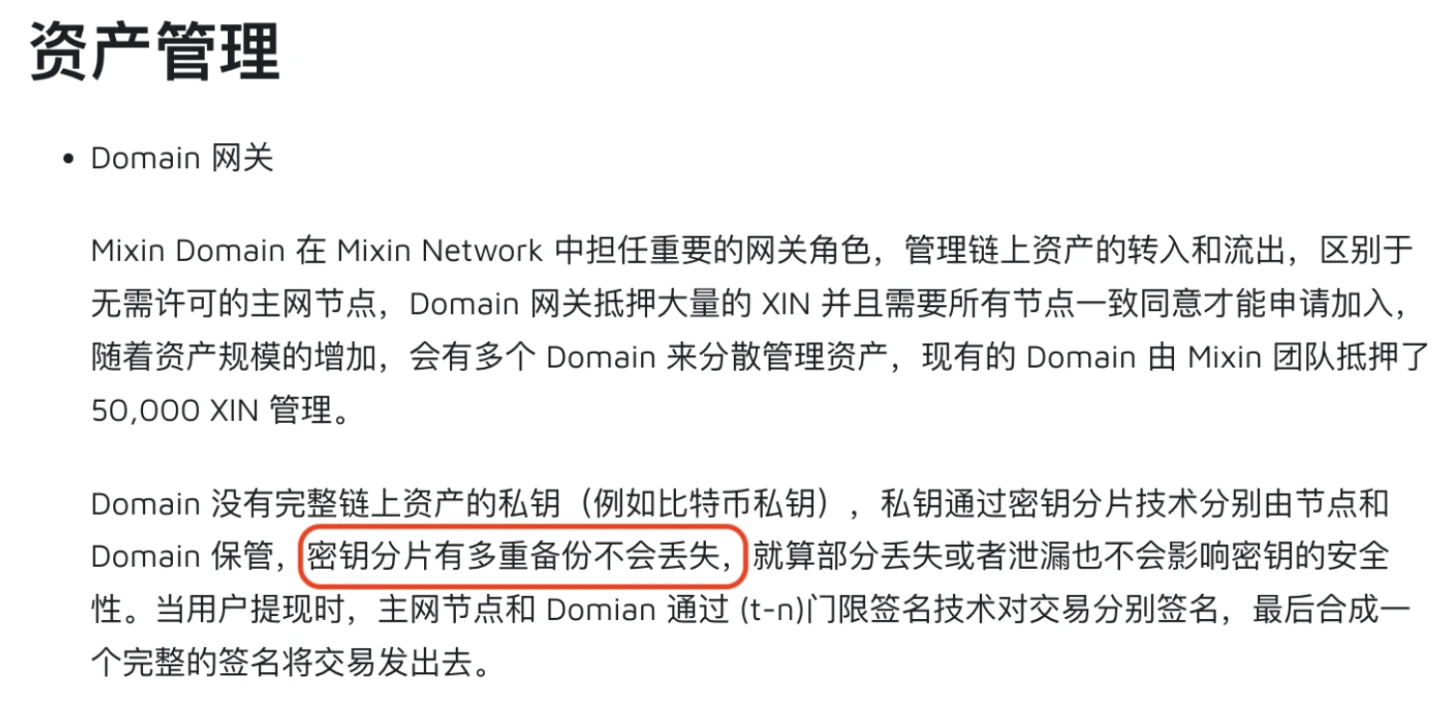
Description of key shard backup in Mixin's official white paper
II. External wrongdoing (4 directions)
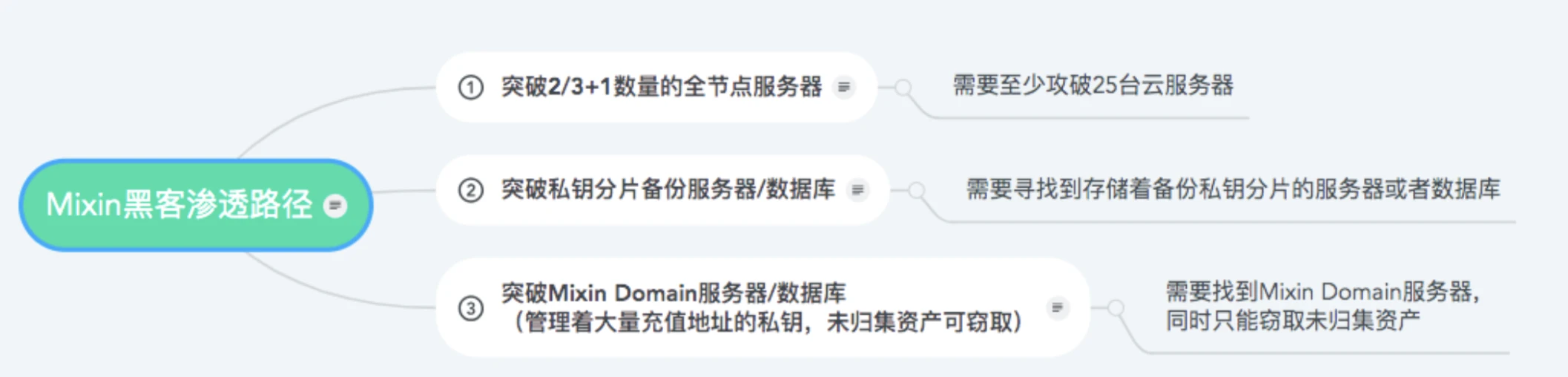
From the perspective of hackers, the ways to breach Mixin Network's defense are as follows:
a) Breach 2/3+1 of the full node cloud servers;
b) Breach the backup servers/database of private key shards;
c) Breach the Mixin Domain servers/database, obtain the private keys of a large number of deposit addresses, and steal uncollected hot wallet assets;
The purely technical paths above may seem simple, but they require a huge amount of work to succeed. In reality, hackers also have simpler (luck-based) methods, using phishing emails or websites to attack Mixin's core technology or operations personnel. Once a careless victim takes the bait, the hacker can enter the victim's host through a trojan horse to gather cloud server passwords and other information for precise attacks.
In summary, although there is currently no direct evidence to indicate that the theft of Mixin is an inside job, the logic of its technical implementation does indeed have vulnerabilities.
The impact of the Mixin theft event is not just the loss of assets for customers. Bitcoin was born out of people's disappointment and resistance to centralized financial institutions. Idealists hope to create an economic model that does not require trust and cannot be manipulated. However, after more than a decade of development, digital assets still seem unable to escape the centralized management model. The core reason for most asset losses is still placing trust in the wrong entities.
Where will the balance of security and convenience in encrypted custody ultimately lie?
Through the Mixin incident, we have found that anyone or any institution that chooses to store their digital assets in a mixed custody manner is essentially using a centralized asset management method.
While enjoying features such as convenient social login, private key recovery, and account retrieval, any asset transfer on the chain must be coordinated by a third party, inevitably carrying inherent or external risks.
Cregis's product has always adhered to the security strategy of customer self-custody. Although it may sacrifice some convenience, it can ensure that customers do not have to worry about losing their assets due to Cregis. This product feature aligns with the needs of enterprise-level fund management that places extreme emphasis on security.
As a Web3.0 enterprise grows in scale, it may no longer be willing to rely on the functionality provided by asset custody service providers' servers. At this point, you need Cregis's private deployment feature. Cregis can authorize the deployment of all source code from the client to the algorithm library to financial collaboration management on the customer's server. This code has been audited and proven to be free of security vulnerabilities over 6 years. Customers not only have the security of a hardware wallet but also can experience the rich functionality of Cregis. Moreover, without the need for software upgrades and maintenance, customers do not need to contact Cregis again and can fully protect their business secrets.
Security
Cregis's private deployment restricts all data and transaction activities within the project party's private servers to ensure the security and controllability of user assets and data. This security model effectively blocks various external threats, including but not limited to hacker attacks, data theft, or the instability of third-party services. Even Cregis cannot directly access the user's private key shards.
This unique security design stands in stark contrast to most solutions on the market that rely on centralized or mixed custody.
Exclusive Server Resources
As digital assets and Web3.0 applications become increasingly complex and extensive, the optimization and management of server resources become particularly critical. In Cregis's private deployment mode, customers can exclusively access server resources without sharing them with other clients or projects.
Support for Customization in Private Deployment
In the increasingly complex Web3.0 environment, standardized solutions often struggle to meet the specific needs of all institutions or projects. Therefore, Cregis not only meets standardized requirements but also supports personalized needs. Cregis's private deployment supports highly customizable financial collaboration management functions and flexible customization for specific business needs.
One-on-One Technical Consultation Services
Digital asset management and Web3 project operations involve multiple complex aspects, from transaction execution and data processing to security protection and compliance. Cregis's private deployment not only provides a powerful technical infrastructure but also offers one-on-one technical consultation services. The professional technical team can provide solutions in a timely manner for system configuration, transaction confirmation, and security protection issues.
Unlimited Wallet Numbers, Addresses, and Currencies
Cregis's private deployment allows users to add new wallets and addresses without restrictions, meaning they can freely manage various types of digital assets.
Contact Us
Official Website|Twitter|Discord
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




