Author: Beosin
In the early morning of January 9, the Truebit Protocol's non-open-sourced contract, deployed 5 years ago, was attacked, resulting in a loss of 8,535.36 ETH (approximately $26.4 million). The Beosin security team conducted a vulnerability and fund tracing analysis of this security incident and shares the results as follows:

Attack Method Analysis
For this incident, we analyze the most significant attack transaction, with the transaction hash: 0xcd4755645595094a8ab984d0db7e3b4aabde72a5c87c4f176a030629c47fb014
- The attacker calls getPurchasePrice() to obtain the price.
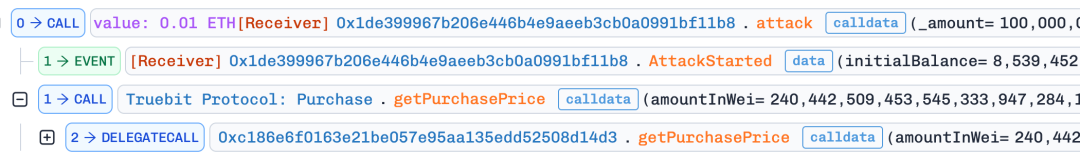
- Subsequently, the attacker calls the flawed function 0xa0296215() and sets the msg.value to a very small value.
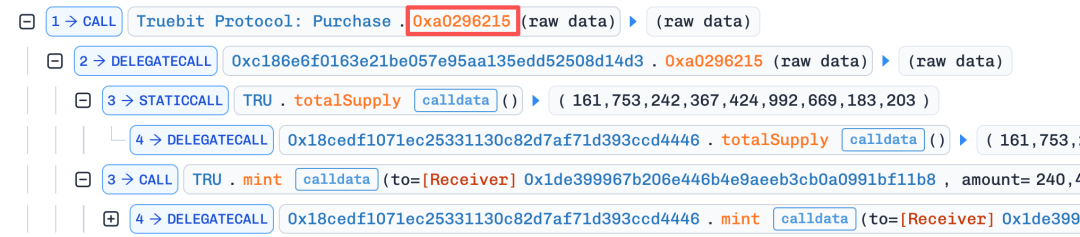
Since the contract is not open-sourced, it is inferred from the decompiled code that this function has an arithmetic logic flaw, such as integer truncation issues, allowing the attacker to successfully mint a large number of TRU tokens.
- The attacker uses the burn function to "sell back" the minted tokens to the contract, extracting a large amount of ETH from the contract's reserves.
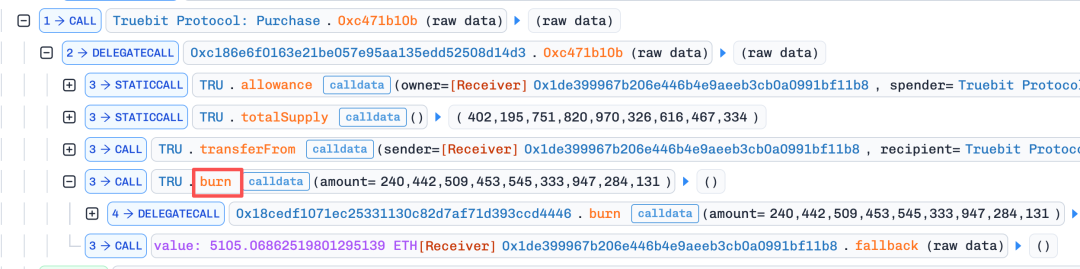
This process is repeated 4 times, with the msg.value increasing each time, until almost all ETH in the contract is extracted.
Tracing Stolen Funds
Based on on-chain transaction data, Beosin conducted a detailed fund tracing through its blockchain on-chain investigation and tracing platform, BeosinTrace, and shares the results as follows:
Currently, the stolen 8,535.36 ETH has been transferred, with the majority stored in 0xd12f6e0fa7fbf4e3a1c7996e3f0dd26ab9031a60 and 0x273589ca3713e7becf42069f9fb3f0c164ce850a.
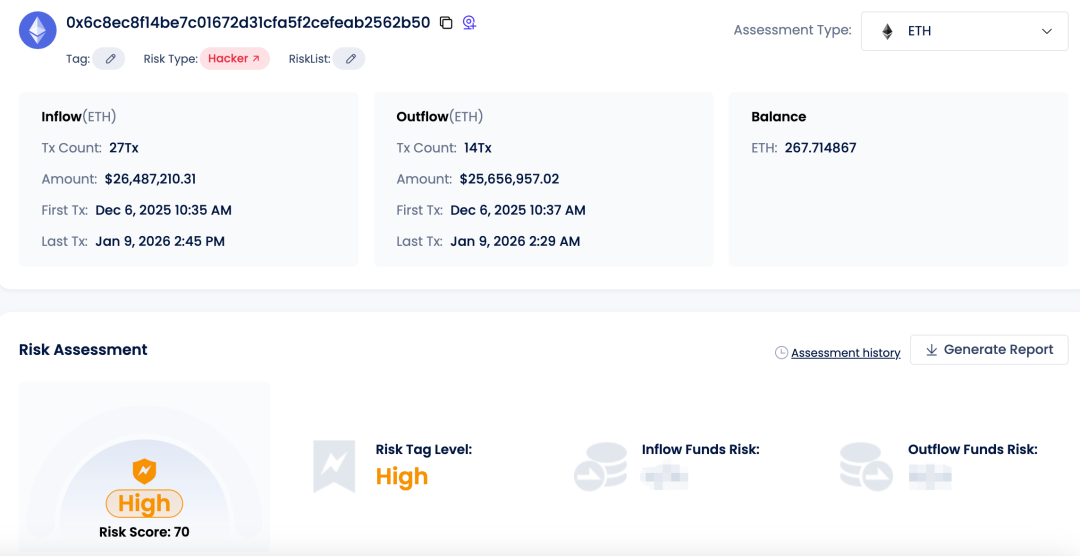
Among them, address 0xd12f holds 4,267.09 ETH, and address 0x2735 holds 4,001 ETH. The address from which the attacker initiated the attack (0x6c8ec8f14be7c01672d31cfa5f2cefeab2562b50) still holds 267.71 ETH, and there has been no further fund transfer from these three addresses.
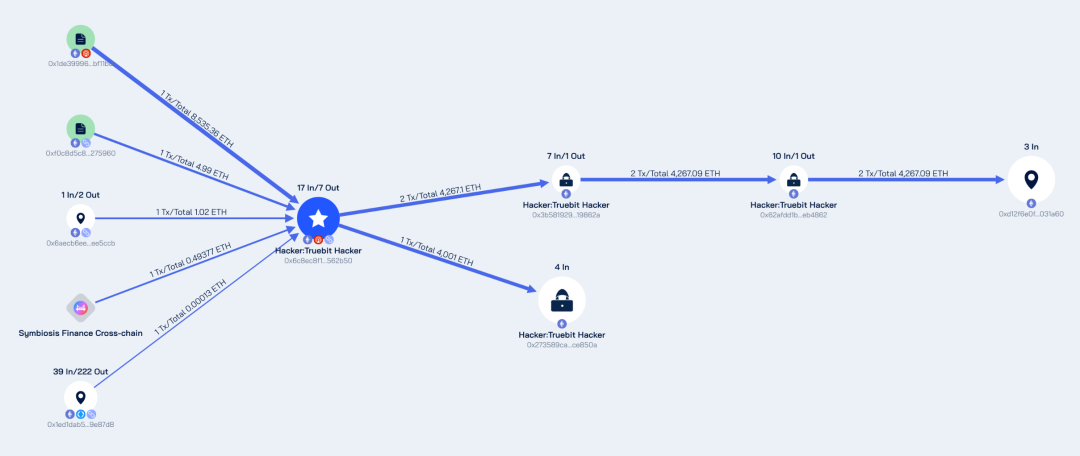
Stolen Fund Flow Analysis Chart by Beosin Trace
All the above addresses have been marked as high-risk addresses by Beosin KYT, taking the attacker's address as an example:
Beosin KYT
Conclusion
The stolen funds involve a smart contract that has not been open-sourced for 5 years. For such contracts, project teams should upgrade the contract, introducing emergency pause, parameter restrictions, and new Solidity security features. Additionally, security audits remain an essential part of the contract process. Through security audits, Web3 companies can comprehensively detect smart contract code, identify and fix potential vulnerabilities, and enhance contract security.
Beosin will provide a complete analysis report of all fund flows and address risks from this incident. Please feel free to request it via the official email support@beosin.com.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




