Original Title: "Infiltrating 600 Electric Fraud Groups, He Aims to Intercept Black Market Money"
Original Author: Sleepy.txt, Dongcha Beating
In the history of commerce, wherever wealth surges, there will be a tug-of-war between law and order.
Looking back from the tail end of 2025, the global issuance of stablecoins has firmly crossed the $300 billion mark, nearly tripling from last year, with monthly trading volumes reaching an astonishing $4 to $5 trillion. Stablecoins, as a form of crypto asset, have shed the label of "geek toys" and have become the primary gateway for traditional finance to enter the digital world.
However, beneath the prosperity lies a shadow. According to the latest industry report, the scale of funds received by illegal addresses globally is expected to exceed $51.3 billion by 2025. With hundreds of billions of dollars capable of crossing borders in seconds, traditional regulatory measures often struggle to keep pace with this speed, making it difficult to discern which businesses are legitimate and which are criminal proceeds.
In this world where rules have yet to be fully established, Professor Zhou Yajin is a unique entrepreneur.
Zhou Yajin's career path is a typical reflection of the deep collision between elite scholarship and industry. In 2010, he went to the United States to pursue a PhD, delving into mobile security for five years, and then joined Qihoo 360 with his mentor, Professor Jiang Xuxian, completing the first leap from the laboratory to the front line of industry. In 2018, he chose to return to Zhejiang University to take up teaching. Three years later, he once again plunged into the industrial wave, founding the blockchain security company BlockSec.
In the past four years, Zhou Yajin has led BlockSec through a shift in business focus. Initially starting with smart contract code auditing, the company gradually extended into deeper areas such as security monitoring, fund tracing, and anti-money laundering compliance.
Zhou Yajin and his team have long been engaged in specialized research on on-chain data, even using technical means to "infiltrate" black market groups involved in electric fraud in Southeast Asia, gaining access to a wealth of little-known underlying survival scenarios. Through his perspective, we may gain insight into the most genuine interest games in this new digital world.
The following is Zhou Yajin's account, edited and organized by the Dongcha Beating editorial team after an interview.
This article is sponsored by Kite AI
Kite is the first Layer 1 blockchain designed for AI agents' payments, providing a foundational infrastructure that allows autonomous AI agents to operate in an environment with verifiable identities, programmable governance, and native stablecoin settlements.
Kite was founded by senior experts in AI and data infrastructure from Databricks, Uber, and UC Berkeley, and has completed $35 million in financing, with investors including PayPal, General Catalyst, Coinbase Ventures, 8VC, and several top investment foundations.
From Code Auditing to the Anti-Money Laundering Battlefield
I pursued my PhD in the United States from 2010 to 2015, under the guidance of Professor Jiang Xuxian. At that time, we focused on mobile security, particularly Android malware detection, which was among the earliest efforts globally. After graduating in 2015, I followed my mentor to Qihoo 360, aiming to industrialize our research findings.
In 2018, I joined Zhejiang University, returning to academia from the industry. At that time, China was experiencing a small boom in ICOs in 2017 and 2018, which brought blockchain into the view of a small number of people, prompting me to start looking into blockchain security. I observed that on-chain security incidents were frequent, and while the academic community had developed several good solutions, the industry was lagging behind, with very few people paying attention to these issues.
Thus, in 2021, I co-founded BlockSec with Professor Wu Lei.
Initially, people's understanding of a "blockchain security company" was extremely stereotypical: Aren't you just doing audits? Indeed, we started with smart contract auditing. Thanks to our academic research background and a relatively elite team, we quickly established a foothold in the auditing business. However, my vision for the company was not to be just a security service provider. Auditing addresses pre-launch security, but there were no particularly good solutions for post-launch protection at that time.
So in 2022, while continuing our auditing work, we also began developing an on-chain attack monitoring platform. Our product concept was to continuously monitor on-chain transactions and automatically block any attack transactions that occurred. During this process, we found that despite having auditing and monitoring, project parties could still be attacked. Coupled with numerous phishing and private key loss incidents affecting end users, this led to new demands.
When project parties were robbed or users were phished, they had to report to the police and clarify where the money had gone. Thus, starting in 2022, we developed a fund tracing product, which was entirely SaaS-based, allowing users to subscribe directly without a To B sales model.
The launch of this product surprised us with its user demographics. In addition to law enforcement agencies, media reporters were using it, financial institutions were using it, and even many private detectives taking on freelance work were using it. These users from different backgrounds helped us refine the product during their usage, attracting even more users. Additionally, we already had attack detection engines, phishing detection engines, etc., and these tags and data gradually became our deepest moat.
The turning point occurred from late 2024 to early 2025.
At that time, the issuance of stablecoins began to surge, and the market was no longer just participated in by Crypto Native individuals. Many traditional finance professionals started entering the space, and the first virtual currency they encountered was stablecoins. These individuals had a strong compliance awareness, and upon entering, they would ask: If I want to use stablecoins, how do I address AML (anti-money laundering) and CFT (counter-terrorism financing) issues?
There were no good compliance products on the market, and we happened to have accumulated foundational tag data over three years, so we quickly launched our anti-money laundering product. The entire process was quite natural; we transformed from a purely security service provider into a comprehensive supplier of "security + compliance" in response to market demand changes.
Infiltration
To engage in anti-money laundering, one must first deeply understand how the black and gray markets use money.
From our research perspective, cryptocurrency crimes are typically divided into two categories: one is "crypto-native," such as code vulnerability attacks on DeFi protocols, private key theft, or phishing. Without blockchain, these crimes would not exist at all.
The other category is "crypto-driven," such as electric fraud, extortion, and human trafficking. The emergence of cryptocurrency has greatly enhanced the efficiency and anonymity of their cross-border transactions. Among these scenarios, what shocked us the most was the human trafficking within the Southeast Asian electric fraud industry chain.
Many people think electric fraud is far from them, but if you look at their recruitment ads, the allure is extremely precise: starting monthly salary of 19,000 RMB, including airfare, meals, and accommodation, and even seriously promising "must purchase Shenzhen social security." This scam method specifically targets young people aged 18 to 37, luring a large number of victims to cross borders into scam parks located in Myanmar, Cambodia, or Laos.

The current electric fraud parks have organizational structures that are as tight as legitimate companies, with finance, technology, and call teams all in place. To maintain such a large operation, they need to continuously replenish "labor," and the parks (demand side) and human traffickers (supply side) do not know each other, communicating online without any trust.
Thus, an intermediary specifically providing credit endorsement for illegal transactions was born, known as "labor guarantee platforms."
The operational logic of this system is quite similar to Taobao. The park first deposits a certain amount of USDT as a guarantee on the guarantee platform; the trafficker is responsible for luring victims across the border and delivering them to a designated "inspection" location. Once both parties confirm in a private Telegram group, the platform releases the deposit to the trafficker. This transaction adheres to the principle of "money follows the person"; if either party tries to default, the platform will freeze or confiscate the deposit according to the rules to compensate the other party.
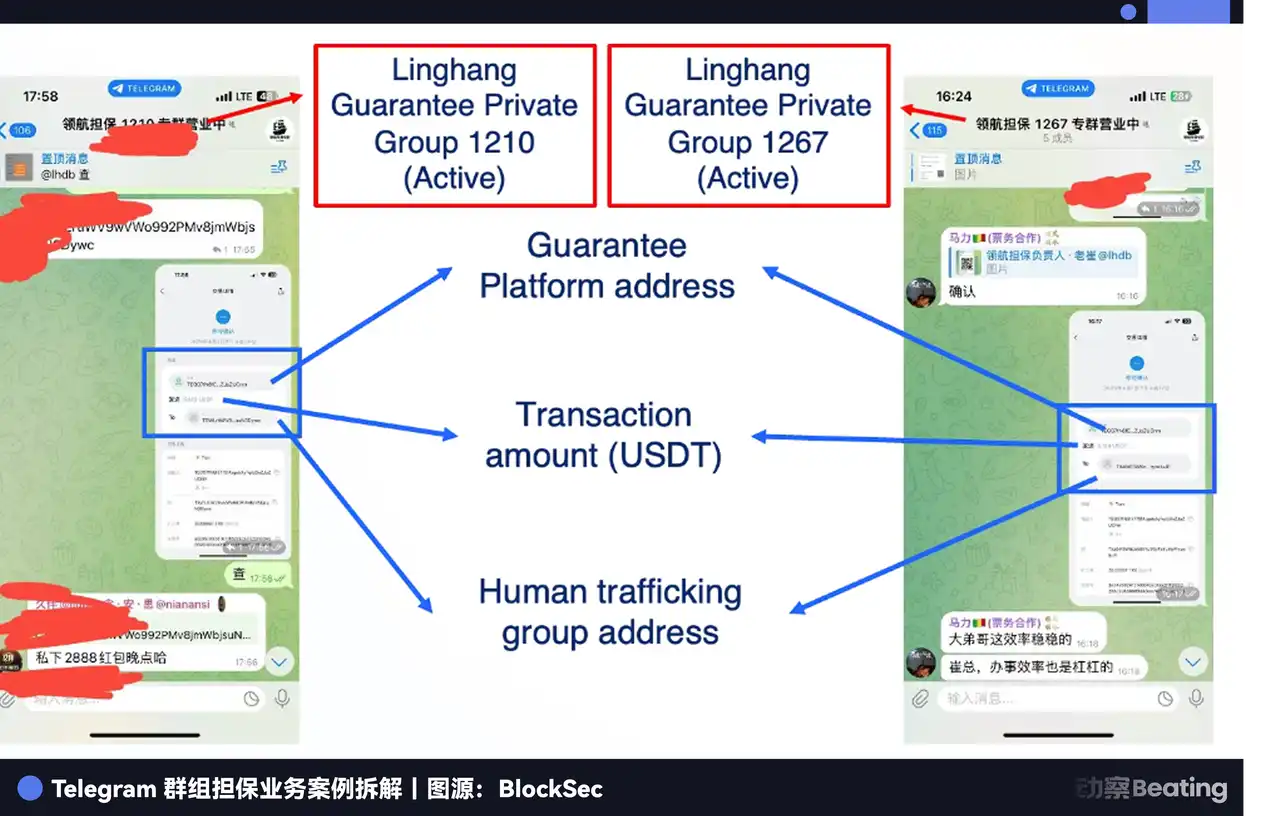
To attract business, these platforms open numerous public channels on Telegram to "show off." For example, in the channels of Linghang Guarantee or Haowang Guarantee, system bots will publish transaction screenshots and on-chain transfer records in real-time. They even run promotions like legitimate e-commerce, such as collecting commissions or offering "buy 10, get 2 free" deals.
This is also the most direct entry point for us to observe the black market.
From February to August 2025, we developed an automated system that continuously infiltrated these groups to gather intelligence. Because the chat in the groups was filled with jargon, we specifically trained a large language model for analysis.
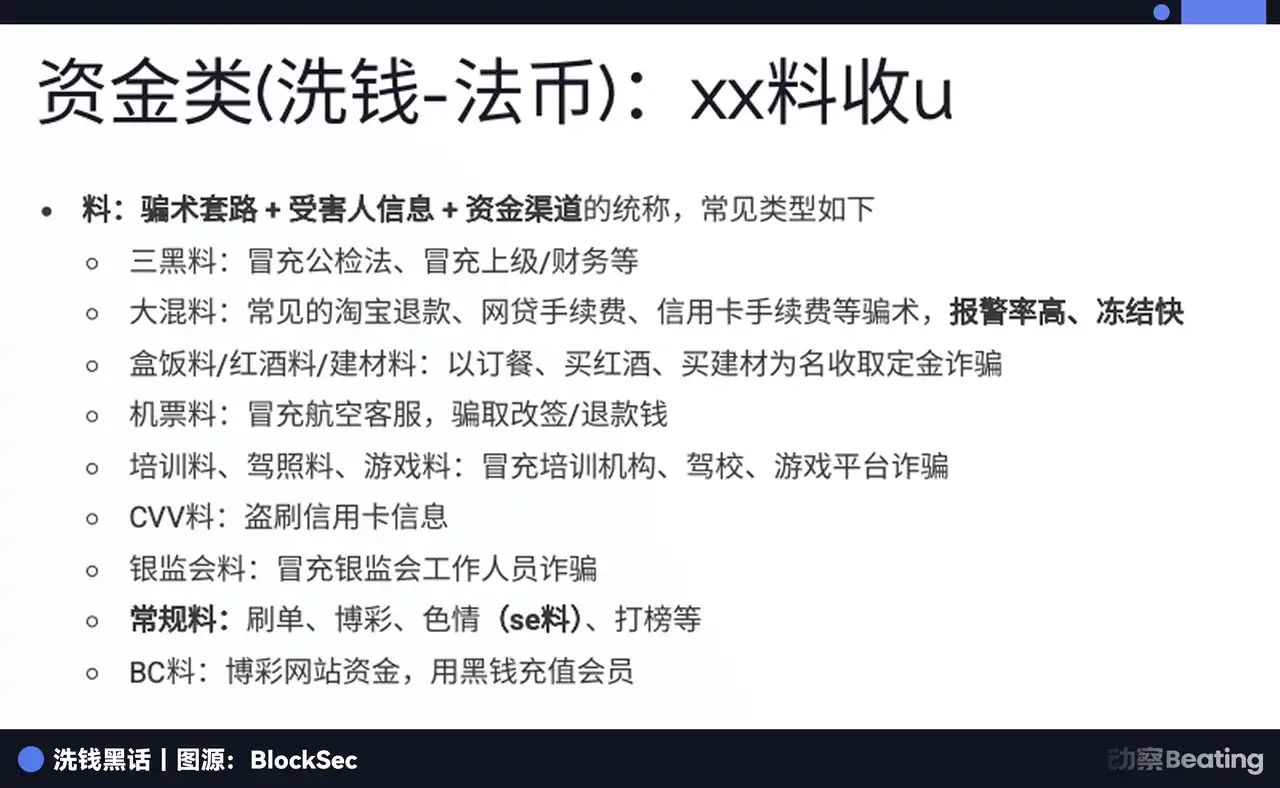
In the language of the black market, victims are referred to as "fish," and the scam tactics and victim information are called "materials." The materials are categorized in detail, including "three black materials," "mixed materials," "air ticket materials," etc. Based on the money laundering stages, they are further divided into "first-level materials," which involve directly receiving money from victims, and "second-level materials," which have undergone layered processing.
There is also a job called "mobile mouth," where accomplices in China use audio lines or specific apps to relay overseas scam calls to domestic phones, bypassing the operators' anti-fraud interception, earning about 200 USDT per hour. They have recruited many young people from small towns for this work.
In these black market groups, there are even openly circulated "Anti-Police Tutorials," meticulously teaching everyone how to calmly respond to investigations, such as insisting that the phone was lost and deleting scripts and encrypted communication apps in advance. The tutorial ends with a very ironic line—"Salute to every hardworking person."
Through six months of automated monitoring, we identified a total of 634 addresses associated with human trafficking gangs linked to one of the guarantee platforms, with the total tracked illegal transaction amount nearing $12 million. At the peak, 10 people were sold into parks through this one guarantee platform daily. The actual situation may be even more severe due to the existence of other guarantee platforms.
In tracing the flow of funds, we found that the vast majority of this money was on the Tron blockchain, primarily using the stablecoin USDT. The low operational threshold and cheap transaction fees of Tron make it very suitable for these technologically limited criminal groups. Although Tron’s transaction fees have increased now, they have already developed a habit of using it, making it difficult to switch to other methods.
We analyzed the cash flow of over 120 gangs and found that more than 34.9% of these illegal proceeds ultimately flowed into the hot wallets of OKX, 6.9% into Binance, and 14.4% into wallets related to Huibang.
When you can clearly see where this money comes from and how it flows, anti-money laundering is no longer just a hollow phrase. The real data captured from the grassroots groups is currently the core barrier to security compliance.
12 Seconds: "Intercepting" Hackers in the Mempool
In the security industry, there has always been a concern: audits can only ensure that the code is secure at the moment of launch. However, once a project is running, it faces global hackers monitoring it 24/7. If auditing is "static defense," can we find a way to implement "dynamic interception"?
In 2022, while conducting audits, we launched an on-chain attack monitoring platform. The underlying logic of this product is to monitor Ethereum's Mempool. You can think of the Mempool as a waiting room where all transactions queue up before being officially packaged into blocks and recorded in the ledger.
In this waiting room, we not only monitor ordinary users' transactions but also focus on those with attack characteristics. Once we detect a suspicious attack transaction, our system immediately initiates automatic analysis in a private chain environment: What is it trying to do? Is the logic sound? How much money will it steal?
The most thrilling game usually occurs within a mere 12 seconds.
After Ethereum's merge, the block time was fixed at 12 seconds. This means there is an extremely short window from when a hacker issues an attack command to when the transaction is actually packaged and confirmed. These few seconds are the golden rescue time for white hats.
Once our system confirms an attack, it automatically generates a "front-running" transaction. The content of this transaction is almost identical to the hacker's, but the key difference is that we modify the receiving address of the funds from the hacker's wallet to our pre-set secure address.
To outpace the hacker, we must gain priority for packaging from the miners.
Hackers typically set a standard Gas Fee to maximize profits. We, however, adjust the Gas Fee algorithmically to be very high, even directly sharing a portion of this money with the miners. Driven by profit, miners will prioritize packaging our transaction. When our transaction is successfully executed, the hacker's transaction will automatically become invalid.
This capability has saved many projects in real combat.
The most typical instance was when we successfully intercepted an attack targeting a certain protocol in the Mempool, rescuing 2,909 Ethereum in one go for the project party. At that time, the hacker had already triggered a vulnerability, and it seemed that tens of millions of dollars were about to be stolen. Our monitoring system instantly alerted us, and within seconds, we completed the attack simulation, transaction generation, and Gas bidding. Ultimately, that large sum was transferred to our secure address ahead of the hacker.
Previously, project parties could only turn to Twitter for help or negotiate with hackers to see if they could offer a bounty to get their money back. But now, through technical means, we forcibly intercepted the money just one second before the hacker succeeded.
Only if you understand the code better than the hacker and can run faster than the hacker can you hold the last line of defense in this "Code is law" dark forest.
Epilogue
If the past decade in the crypto world was a "gold rush," then standing at this point in 2025, we see a return to "certainty." As the scale of stablecoins surges toward $300 billion, and as a new digital financial system transitions from "wilderness" to "city-state," technology is no longer merely a lever for wealth; it must first become a shield against the dark side of human nature.
The transformation experienced by Zhou Yajin and his team is essentially a reflection of this business logic. From code auditing to dynamic interception, and then to deep diving and dismantling the black market chain, this is not the solitary bravery of an individual but a defensive mechanism that inevitably arises when technology evolves to a certain scale. In this world where code is law, if we do not address the persistent issues of illegal fund flows and security defense failures, the so-called "financial revolution" will forever remain a game for a select few.
In the history of commerce, any industry that has moved toward the mainstream has undergone the painful transition from chaos to rule of law. This may be a long and tedious process, but as Zhou Yajin said, the ultimate form of security is "unperceived."
Only when security becomes as ubiquitous as air, yet ignored by everyone, can this once unpredictable digital wilderness truly complete its civilizational pioneering.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




