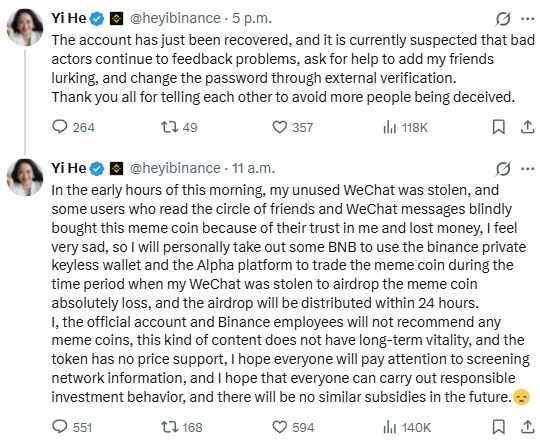
On December 10, 2025, multiple cryptocurrency media outlets reported that Binance co-CEO Yi He’s WeChat account was hacked for a short period, during which the hacker sent promotional information about a meme coin called MUBARA (Mubarakah) to her contacts. Subsequently, the token experienced an abnormal surge and significant volatility in a short time. The incident attracted widespread attention, not only because it involved a Binance executive but also as a prism reflecting multiple deep-seated issues in the current market regarding social account security, meme coin speculation mechanisms, and user risk awareness.
This article will rely on public media reports and on-chain traceable data to explore the facts, mechanisms, risks, and industry impacts, aiming to penetrate the surface and uncover the underlying logic. 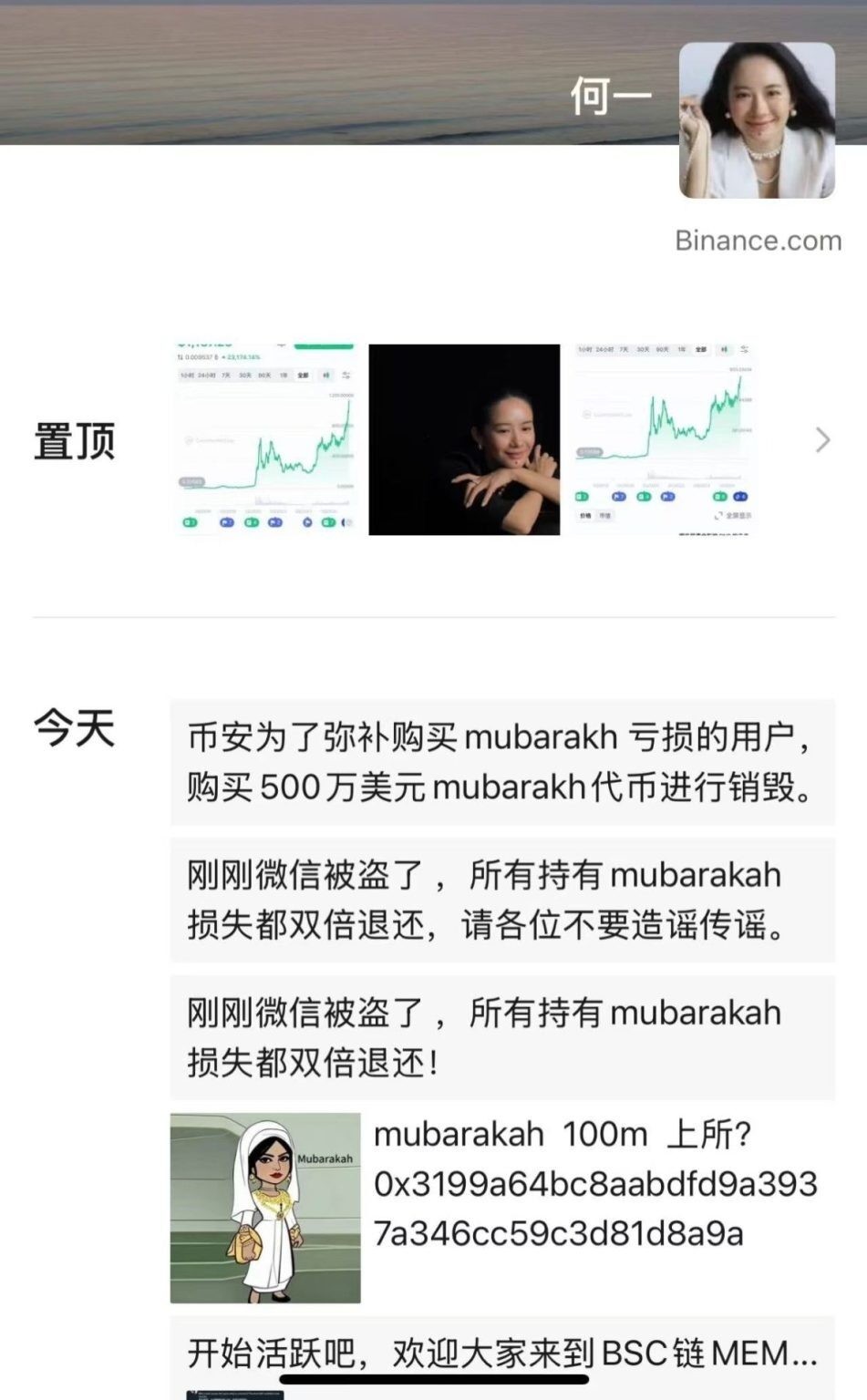
I. Incident Review: From Hacked Account to Token Volatility
According to disclosures from authoritative media such as CoinDesk, Cryptopolitan, and CryptoNews, as well as on-chain data tracking, the incident unfolded as follows:
(1) Social Account Hacked
Yi He’s WeChat account was briefly controlled. The hacker used her WeChat identity to send promotional information related to the meme coin MUBARA to her contacts. Notably, WeChat, as a mainstream social platform of the Web2 era, still holds significant credibility within the cryptocurrency industry, especially in private communication and industry information flow, which set the stage for subsequent market reactions.

(2) On-Chain Data Shows Signs of Pre-Positioning
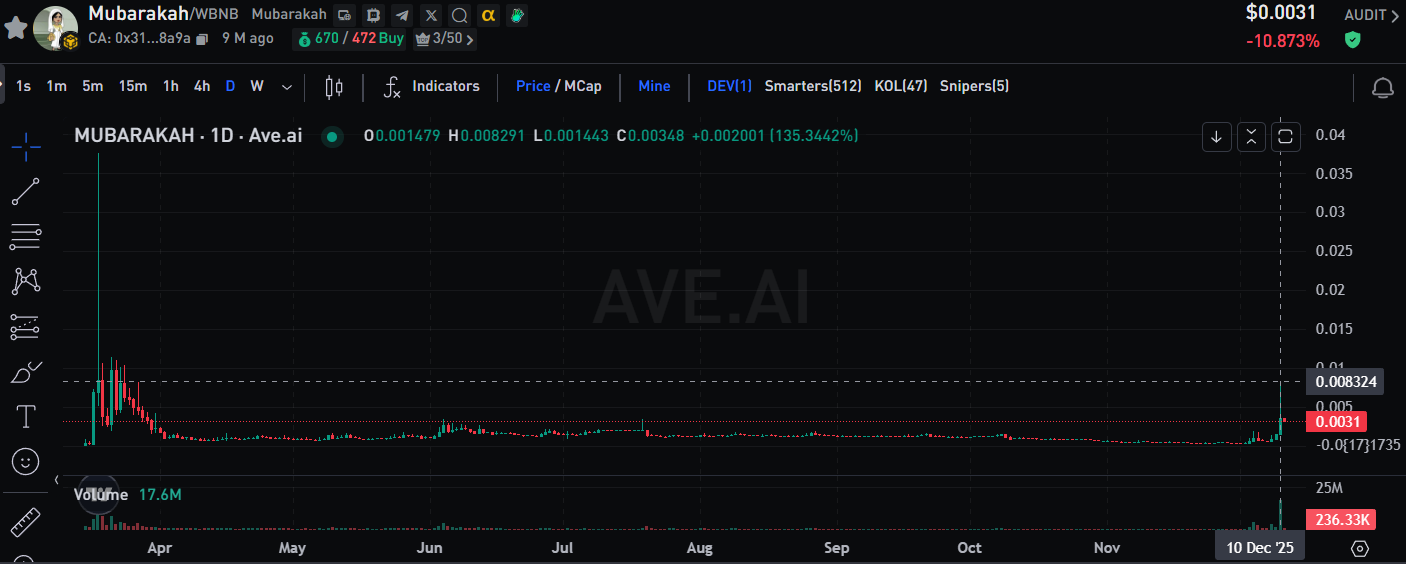
Multiple analysis firms pointed out that two new wallets purchased approximately $19,000 worth of MUBARA just hours before the promotion. The token then rapidly surged, with an increase exceeding 200%, followed by significant sell-off behavior at the peak, with some profits exceeding $40,000. On-chain behavior clearly exhibited a typical structure of “pre-positioning → information trigger → price surge → sell-off.”
(3) Binance Official and CZ Respond
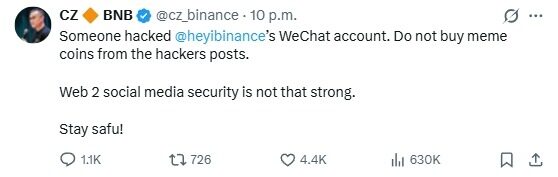
Zhao Changpeng (CZ) promptly warned users on social media not to trust token recommendations from the hacked account, emphasizing the significant security risks associated with social accounts on Web2 platforms. The Binance team later confirmed that the account had been recovered and issued security alerts to remind users to be cautious of fraudulent activities, preventing the situation from escalating further.

II. The Cross-Mechanism of On-Chain and Social Dimensions: A Typical “Trust Hijacking” Incident
Structurally, this is not merely a hacking incident but a result of multiple layered mechanisms.
(1) The Cost of Hijacking Social Identity is Lower than Asset Hijacking
Since social platform accounts are hosted by Web2 companies, their security relies on internal mechanisms. Trust within the cryptocurrency industry is highly concentrated on individuals (such as founders, CEOs, early investors, etc.), meaning that hackers only need to control a high-trust account for a short time to trigger real market behavior. This type of “information entry” risk is becoming a common security shortcoming in the industry.
(2) The Low Liquidity and High Volatility of Meme Coins Amplify Attack Effects
Meme coins typically have the following characteristics: low market capitalization, extremely low manipulation costs; prices driven by investor sentiment; extreme reliance on external narratives and guidance; lack of fundamental judgment basis. Once there is a stimulus with “similar endorsement,” even if it is just information released by a hacked account, it is enough to trigger rapid price fluctuations. The structure of the meme coin market provides a natural “amplifier” for such incidents.
(3) The Information Dissemination Path of the Incident Shows a Closed Trust Chain
The private environment of WeChat has a strong trust transmission effect: information source = industry executives, information channel = private communication, information form = direct forwarding, private exchanges, information verification threshold = extremely low. In this environment, some users can easily accept “insider news” hints, leading to rapid follow-up trading.
III. Structural Risk Exposure in the Cryptocurrency Industry
The incident itself has been controlled, but the systemic issues it exposes in the industry warrant further discussion.
(1) Social Account Security has Become a New Attack Surface in the Web3 Ecosystem
As the industry develops, the social accounts of project parties, exchange executives, and KOLs have become the main entry points for information dissemination in Web3. Compared to smart contracts or exchange security systems, these entry points are more vulnerable: Web2 platforms rely on traditional security mechanisms such as account passwords and SMS verification; they lack on-chain verifiable identities; and they do not possess immutability. Therefore, such “account hijacking → market volatility” incidents are almost inevitable in the future.
(2) The Speed of Information Dissemination and Response Also Leads to Tail Risks
The cryptocurrency market remains in a high information asymmetry structure: hackers or manipulators occupy the upstream of the information chain, while general users are at the tail end, with market response mechanisms resembling “transmission” rather than “equilibrium.” Thus, a small time difference in information possession by a few individuals is enough to create a rapid profit window.
(3) Meme Coins Naturally Lack Risk Pricing Ability
There is almost no fundamental value analysis in the meme coin market, only based on: sentiment, social signals, information stimuli, celebrity effects. This means that as long as the narrative is briefly hijacked, prices will deviate from the norm. Such incidents are not rare but are an inevitable result of the structural flaws in the meme coin market.
IV. User-Level Risks: Why Are Investors Ultimately the Ones Being Harvested?
Although the incident was triggered by a hacker intrusion, the real risk is borne by the users.
(1) Users Often Make Decisions Based on “Familiar Identities”
Many people do not judge based on token structure, liquidity, or contract security, but rather based on: the information comes from Yi He, it is a “familiar person forwarding,” it seems like an internal opportunity, and there is time pressure. This judgment logic can easily be exploited by attackers.
(2) Lack of Information Verification Mechanisms
Many users fail to: double-check the source, verify with official channels, check on-chain liquidity, analyze fund pool size, or identify “pre-positioning” behavior. In an ecosystem where meme coin participants tend to be younger and more speculative, this risk is further amplified.
(3) Retail Investors are Always the Slowest Link
Manipulator buys → hacker promotes → token rises → retail investors enter → manipulator sells, this is the standard time difference chain. Retail investors find it difficult to avoid being in the last link of the chain, ultimately becoming the bearers of losses.
V. Industry Insights: How to Reduce Similar Incidents in the Future?
From an industry perspective, the incident provides at least three important insights:
(1) Project Parties and Exchanges Need to Establish On-Chain Verifiable Official Announcement Channels
For example: DID (Decentralized Identity) binding, on-chain signed announcements, decentralized identity verification, multi-platform synchronization update mechanisms. Through such mechanisms, reduce user reliance on a single Web2 platform, thereby enhancing the credibility of information from the source.
(2) Social Account Security Should Be Part of Industry-Level Risk Management
Including but not limited to: stronger verification for executive social accounts, establishing internal multi-level verification mechanisms for teams, and isolating management of social entry points for key personnel. The cost of such security measures is far lower than the losses caused by a single market fluctuation.
(3) User Education Must Be Upgraded
Educate users: not to rely on “familiar messages,” not to judge authenticity based on a single screenshot, not to chase prices in low liquidity tokens, and not to equate meme coins with “internal opportunities.” Only with an upgrade in user awareness can the attack surface for such scams be truly reduced.
Conclusion
The incident of Yi He’s WeChat account being hacked has largely subsided, and although it did not cause large-scale losses, the reality it reveals cannot be ignored: the trust structure in the cryptocurrency industry is being further amplified by “social entry points” and “meme coinization” risks. A piece of information from a hacked account can trigger price fluctuations, indicating that the industry still has a high dependency on information sources, while the characteristics of the meme coin market further amplify the fragility of this dependency.
In the long run, the industry needs to make systematic improvements in identity mechanisms, information verification mechanisms, user education, and social entry point security. Specifically, three upgrades need to be achieved: in identity mechanisms, transitioning from “personal trust” to “on-chain verifiable identity”; in information mechanisms, transitioning from “Web2 one-way dissemination” to “on-chain verifiable publication”; and in user awareness, transitioning from “blind following” to “rational decision-making.” Otherwise, similar incidents will continue to recur, and the ones who suffer will always be ordinary investors.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。