🧐 Follow-up on the Venus user phishing attack incident | A must-read for everyone's wallet security!
Thanks to the authors below for their sharing and sincere advice, which can be considered a hard lesson! It is recommended that everyone read it carefully—
At the end, we will include insights and essential points to note that we gained from this theft incident!
The Venus @VenusProtocol theft incident has been a hot topic for the past few days;
Today, I saw this article and was first relieved that user @KuanSun1990 was safe and sound, which is the greatest luck among those who unfortunately became targets of hacker attacks!
The author also pointed out that Venus's timely and decisive measures helped him recover his assets, thus vindicating Venus!
Each of us could be attacked; this is not a trivial matter!
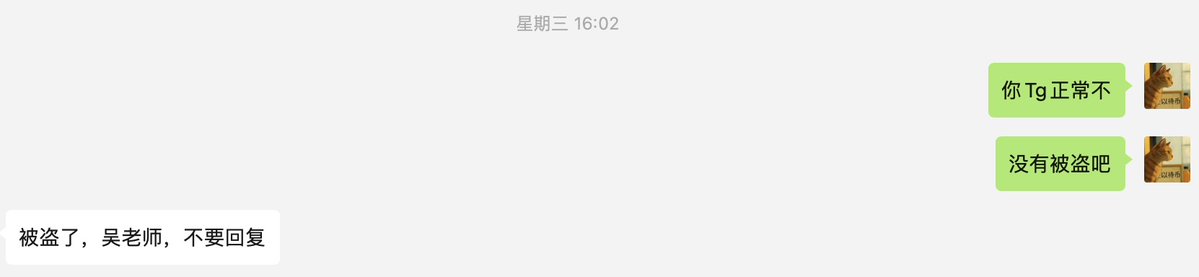
Just the day before yesterday, I personally encountered a similar incident:
A familiar person's TG sent me a meeting invitation, suggesting we study a project together. Since we had never discussed this project before, it wasn't even in my area of interest, and it wasn't a project he was responsible for, I was suspicious. I asked him on WeChat, and to my surprise, he immediately informed me that his TG account had been hacked and urged me not to believe it, which gave me a cold sweat!
The terrifying thing is that these types of scammers no longer have the fake Chinese feel in their language; their Chinese even includes modal particles, clearly indicating they have evolved!
Therefore, I believe that such scams will emerge in large numbers! Everyone must not let their guard down; losses may be small, but once stolen, it could mean losing everything!
1️⃣ Incident Overview:
On September 2, 2025, the victim's wallet, containing $13 million in assets, was nearly stolen. The attacking party has been confirmed as the Lazarus hacker group, which initiated the attack through Zoom phishing + deepfake + malicious plugins.
2️⃣ Attack Process:
1) Impersonating an acquaintance (Stack Asia BD, TG account had already been hacked).
2) After scheduling a meeting, a Zoom meeting link was sent → no sound → prompted "microphone upgrade needed" → clicked to upgrade.
3) Chrome crashed unexpectedly, and the plugin was replaced with a fake Rabby wallet plugin.
4) The victim attempted to withdraw in a "familiar operational scenario," blindly confirming, and nearly lost the funds.
Clearly, this was a transaction logic tailored to the victim's Venus positions and debt model.
Using "semi-acquaintance relationships" and guilt psychology to lower defenses, a deepfake video was used to forge a colleague's attendance, enhancing credibility, and finally, front-end hijacking (fake plugin), trojan, and blind-sign vulnerabilities.
3️⃣ Author's Review of the Incident:
Zoom is a common attack channel for Lazarus; be cautious of strange links from unfamiliar people or odd links from acquaintances.
If completely unfamiliar, I will be more vigilant. If particularly familiar, I can detect anomalies from behavioral habits and speaking styles. However, scammers pose as someone you might have met offline or a friend introduced, making you not familiar but having some intersection.
In recent years, North Korean hackers' methods have evolved into a "trinity of social engineering + deepfake + technical trojans." Even with video conferences and seemingly normal Twitter identities, it could all be a facade.
Hardware wallets are not a panacea for security; if plugins or front-ends are hijacked, users can still fall victim to blind-signing. Use hardware wallets as much as possible, but do not blindly trust their omnipotence; always combine them with front-end and other risk controls.
For wallets with assets, plugins should only be downloaded from official channels, whether upgrading or downloading; do not click any "upgrade" links in pop-ups.
Do not trust semi-acquaintance relationships: videos, voice calls, and meetings can all be deepfaked.
4️⃣ 🔒 Cryptocurrency Asset Security Self-Check List (Checklist)
- Communication and Meetings
Try to avoid using known high-risk platforms like Zoom for sensitive business.
Video/voice does not equal real identity → deepfake technology can easily forge.
Any meeting invitations, documents, links → verify the source (cross-platform or directly call to confirm).
- Plugin and Front-End Security
Only download plugins from official channels (Chrome/Firefox official stores).
Do not click any "upgrade" or "download" links in web/meeting pop-ups.
Regularly clean and check browser extensions to prevent replacements.
Before sensitive operations, consider using a dedicated clean device.
- Hardware Wallet Usage
Hardware wallets are not omnipotent; avoid over-reliance.
Minimize blind-signing operations.
Confirm transaction logic → use simulation/pre-execution tools to verify transaction results.
When encountering complex contract interactions, prioritize using official front-ends or trusted tools.
- Social and Interpersonal Relations
Semi-acquaintances are the most dangerous: be particularly cautious of people who are neither strangers nor familiar.
Acquaintance accounts can also be hacked → verify identity through multiple channels.
Do not lower your guard due to personal feelings, guilt, or being in a hurry.
- Mindset and Operational Habits
Maintain skepticism: any "unreasonable small requests" (like upgrading the microphone) should prompt you to stop and think.
If anomalies occur during operations (browser crashes, unusual prompts), stop immediately and check the environment.
Regularly review operational habits to avoid forming a "numb familiarity."
Stay skeptical: when encountering unreasonable requests, even if it's just "upgrading the microphone," take a moment to think.
5️⃣ Final Words:
This incident reminds us that hackers like Lazarus have integrated social engineering + deepfake + technical attacks into a complete weapon chain.
The core of security is no longer just "using hardware wallets," but rather to comprehensively enhance security awareness regarding identity verification, plugin control, and operational mindset.
Finally, I am very grateful that we have such a group of justice defenders in our circle, such as @peckshield @binance @SlowMist_Team @evilcos and others!
Of course, I know that writing so much like this cannot change anything; most people have to personally experience at least one hit to realize the kind of situation they are in before they truly value security, as I have gone through this myself!
I do not expect my article to change everyone's security awareness, but I hope that through my efforts to spread the word, I can truly help a few concerned individuals avoid hopeless losses, and that is enough!
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




