Original Title: Exit Liquidity Machines
Original Author: Pine Analytics
Original Translation: GaryMa Wu Says Blockchain
Abstract
This report investigates a prevalent and highly coordinated meme token farming model on Solana: token deployers transfer SOL to "sniper wallets," enabling these wallets to purchase the token within the same block it goes live. By focusing on the clear, provable funding chain between deployers and snipers, we identify a set of high-confidence extraction behaviors.
Our analysis shows that this strategy is neither a coincidence nor marginal behavior — in just the past month, over 15,000 SOL in realized profits have been extracted from more than 15,000 token launches through this method, involving over 4,600 sniper wallets and more than 10,400 deployers. These wallets exhibit an unusually high success rate (87% sniper profitability), clean exit strategies, and structured operational patterns.
Key Findings:
· Deployer-funded sniping is systematic, profitable, and often automated, with sniper activity most concentrated during U.S. working hours.
· Multi-wallet farming structures are very common, often using temporary wallets and coordinated exits to simulate real demand.
· Obfuscation techniques are continuously evolving, such as multi-hop funding chains and multi-signature sniper transactions, to evade detection.
· Despite limitations, our one-hop funding filter can still capture the clearest, repeatable large-scale "insider" behavior cases.
· This report proposes a set of actionable heuristic methods to help protocol teams and front-end developers identify, label, and respond to such activities in real-time — including tracking early holding concentration, tagging deployer-associated wallets, and issuing front-end warnings to users during high-risk launches.
Although our analysis only covers a subset of same-block sniping behavior, its scale, structure, and profitability indicate that Solana token launches are actively manipulated by a coordinated network, and existing defenses are far from sufficient.
Methodology
This analysis starts with a clear objective: to identify behaviors on Solana that indicate coordinated meme token farming, particularly the situation where deployers provide funding to sniper wallets in the same block the token goes live. We break the problem down into the following stages:
1. Filtering Same-Block Snipes
We first filter wallets that are sniped in the same block immediately after deployment. Due to: Solana lacking a global mempool; needing to know the token address before it appears on public front-ends; and the extremely short time between deployment and the first DEX interaction. Such behavior is nearly impossible to occur naturally, making "same-block sniping" a high-confidence filter for identifying potential collusion or privileged activity.
2. Identifying Wallets Associated with Deployers
To distinguish technically skilled snipers from colluding "insiders," we track SOL transfers between deployers and snipers before the token goes live, only marking wallets that meet the following criteria: directly receiving SOL from the deployer; directly sending SOL to the deployer. Only wallets with direct transfers before the launch are included in the final dataset.
3. Associating Snipes with Token Profits
For each sniper wallet, we map its trading activity on the sniped token, specifically calculating: the total amount of SOL spent to buy the token; the total amount of SOL received from selling on DEX; and the realized net profit (rather than nominal gains). This allows us to accurately attribute the profits extracted from the deployer for each sniping event.
4. Measuring Scale and Wallet Behavior
We analyze the scale of such activities from multiple dimensions: the number of independent deployers and sniper wallets; confirmed coordinated same-block sniping occurrences; distribution of sniper profits; the number of tokens issued per deployer; and the cross-token reuse of sniper wallets.
5. Traces of Machine Activity
To understand how these operations are conducted, we group sniper activities by UTC hour. The results show: activities concentrate in specific time windows; a significant drop during UTC late-night hours; indicating that rather than being global and continuous automation, it aligns more with cron tasks or manual execution windows in the U.S.
6. Exit Behavior Analysis
Finally, we study the behavior of deployer-associated wallets when selling the sniped tokens: measuring the time from the first purchase to the final sale (holding duration); counting the number of independent sell transactions used by each wallet to exit. This distinguishes whether wallets choose to quickly liquidate or gradually sell off, and examines the relationship between exit speed and profitability.
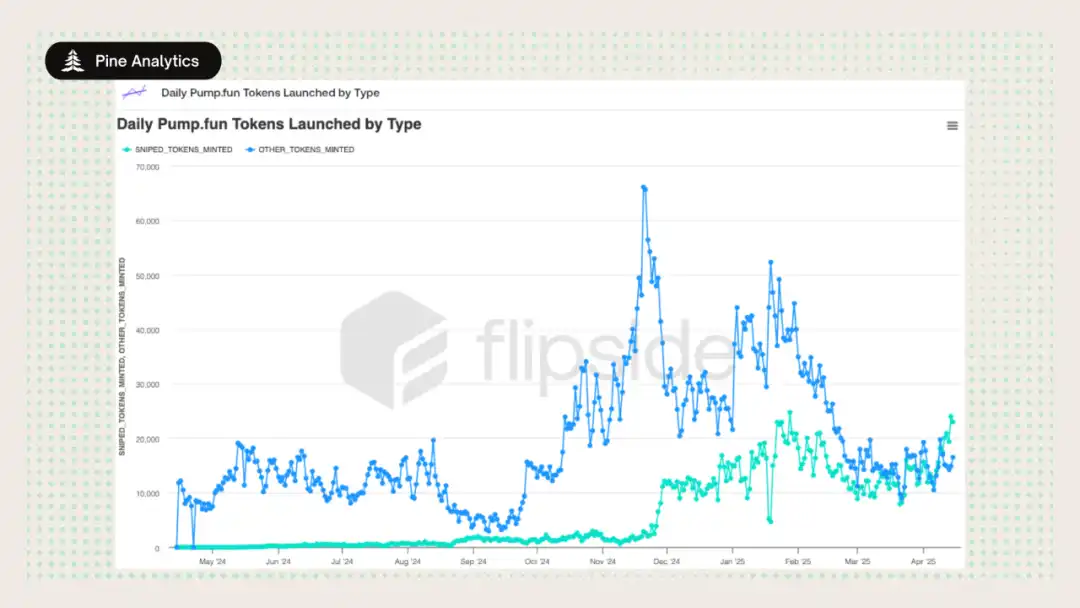
Focusing on the Clearest Threats
We first measured the scale of same-block sniping during the pump.fun launch, and the results were shocking: over 50% of tokens were sniped in the creation block — same-block sniping has shifted from a marginal case to a dominant issuance model.
On Solana, same-block participation typically requires: pre-signed transactions; off-chain coordination; or shared infrastructure between deployers and buyers. Not all same-block sniping is equally malicious; at least two types of roles exist: "casting a wide net" bots — testing heuristics or small-scale speculation; and colluding insiders — including deployers providing funding for their buyers.
To reduce false positives and highlight genuine collusive behavior, we incorporated strict filtering in the final metrics: only counting snipes where there was a direct SOL transfer between deployers and sniper wallets before the launch. This allows us to confidently identify: wallets directly controlled by deployers; wallets acting under the deployer's direction; and wallets with insider channels.
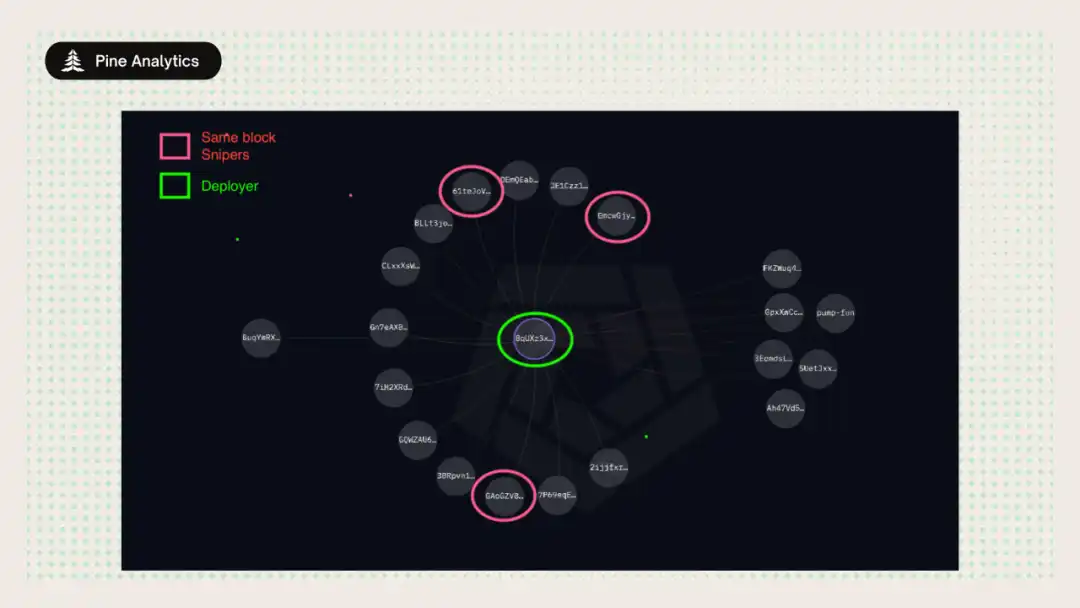
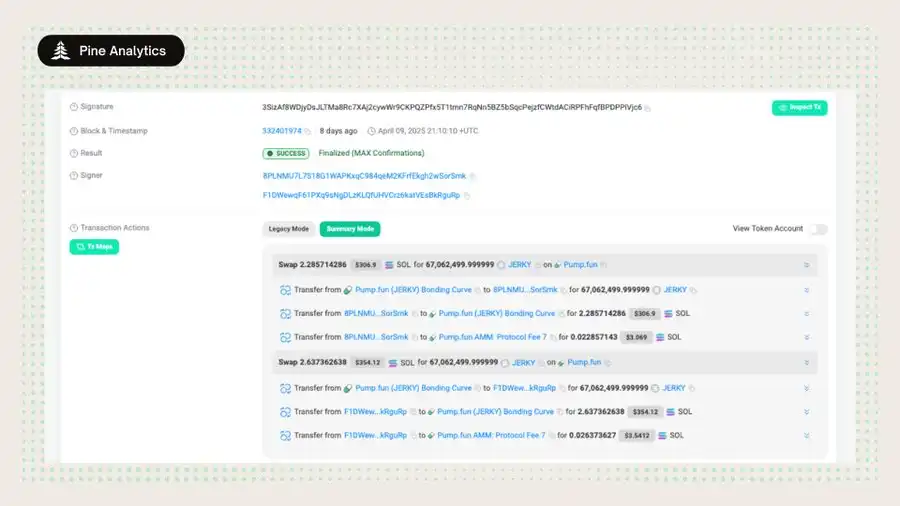
Case Study 1: Direct Funding
The deployer wallet 8qUXz3xyx7dtctmjQnXZDWKsWPWSfFnnfwhVtK2jsELE sent a total of 1.2 SOL to three different wallets, then deployed a token named SOL > BNB. The three funded wallets completed their purchases in the same block as the token creation, ahead of broader market visibility. They then quickly sold for profit, executing a coordinated flash exit. This is a textbook example of pre-funding sniper wallets to farm tokens, directly captured by our funding chain method. Despite the simplicity of the technique, it has been performed on a large scale across thousands of launches.
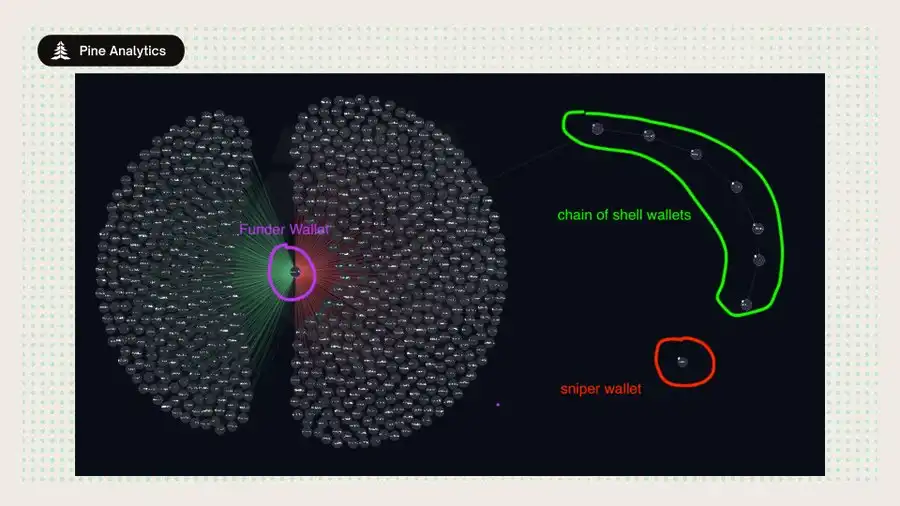
Case Study 2: Multi-Hop Funding
The wallet GQZLghNrW9NjmJf8gy8iQ4xTJFW4ugqNpH3rJTdqY5kA is associated with multiple token snipes. This entity did not directly fund the sniper wallets but instead routed SOL through 5–7 intermediary wallets to reach the final sniper wallet, completing the sniping in the same block.
Our existing method only detected some initial transfers from the deployer but failed to capture the entire chain leading to the final sniper wallet. These relay wallets are often "single-use," only used to pass SOL, making it difficult to associate them through simple queries. This gap is not a design flaw but a trade-off in computational resources — while tracking multi-hop funding paths in large-scale data is feasible, it is resource-intensive. Therefore, the current implementation prioritizes high-confidence, direct linkages to maintain clarity and reproducibility.
We utilized Arkham's visualization tools to illustrate this longer funding chain, graphically presenting how funds flowed from the initial wallet through shell wallets to the final deployer wallet. This highlights the complexity of funding source obfuscation and points to directions for future improvements in detection methods.
Why Focus on "Directly Funded and Same-Block Sniping Wallets"
In the remainder of this article, we will only study sniper wallets that directly received deployer funding before the launch and sniped in the same block. The reasons are as follows: they contribute significant profits; have minimal obfuscation techniques; represent the most actionable malicious subset; and studying them can provide the clearest heuristic framework for detecting and mitigating more advanced extraction strategies.
Findings
Focusing on the subset of "same-block sniping + direct funding chains," we reveal a widespread, structured, and highly profitable on-chain collusive behavior. The following data covers the period from March 15 to the present:
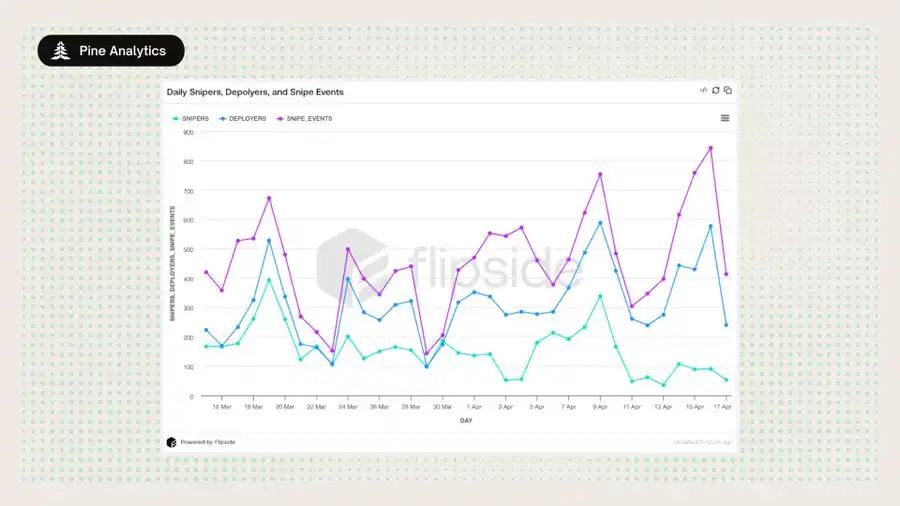
1. Same-Block and Deployer-Funded Sniping is Very Common and Systematic
a. Over the past month, more than 15,000 tokens have been confirmed to be sniped by directly funded wallets in the launch block;
b. Involving over 4,600 sniper wallets and more than 10,400 deployers;
c. Accounting for approximately 1.75% of pump.fun issuance.
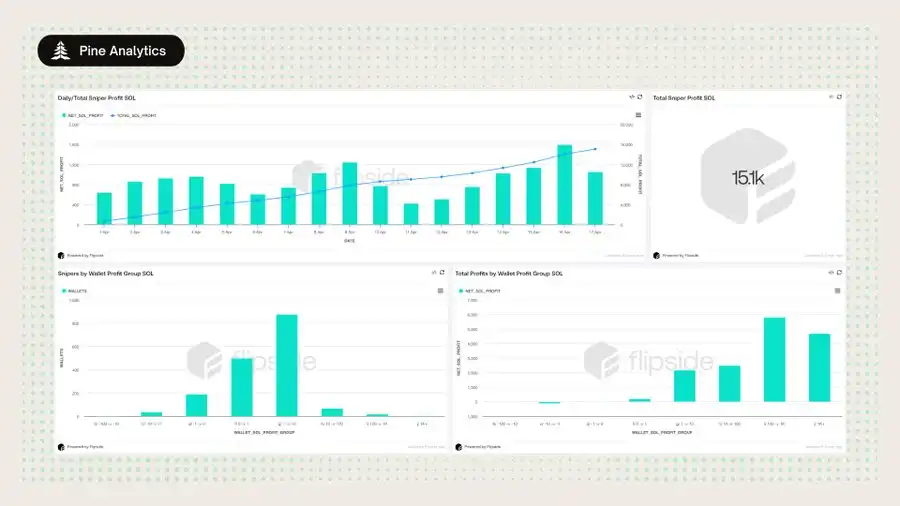
2. This Behavior is Highly Profitable
a. Directly funded sniper wallets have realized net profits of over 15,000 SOL;
b. Sniping success rate is 87%, with very few failed transactions;
c. Typical profits per wallet range from 1–100 SOL, with some exceeding 500 SOL.
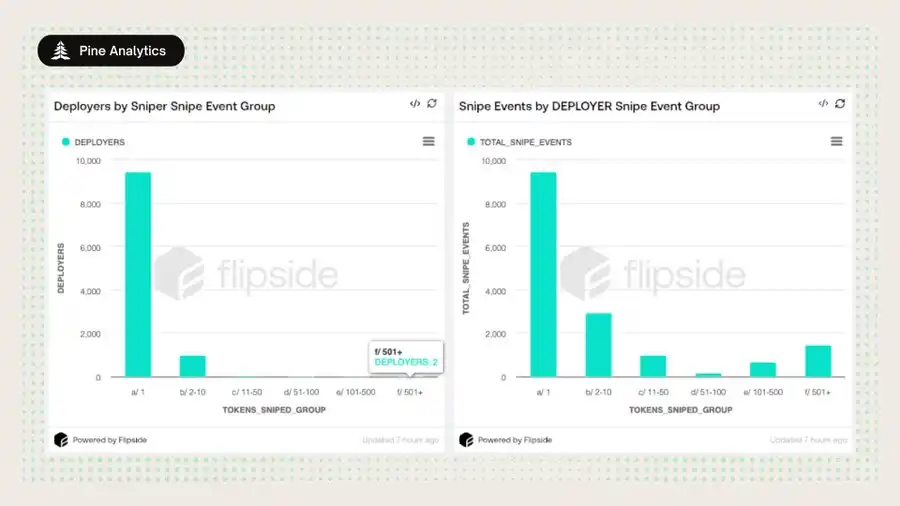
3. Repeated Deployments and Sniping Point to a Farming Network
a. Many deployers use new wallets to batch create dozens to hundreds of tokens;
b. Some sniper wallets execute hundreds of snipes in a single day;
c. A "hub-and-spoke" structure is observed: one wallet funds multiple sniper wallets, all sniping the same token.
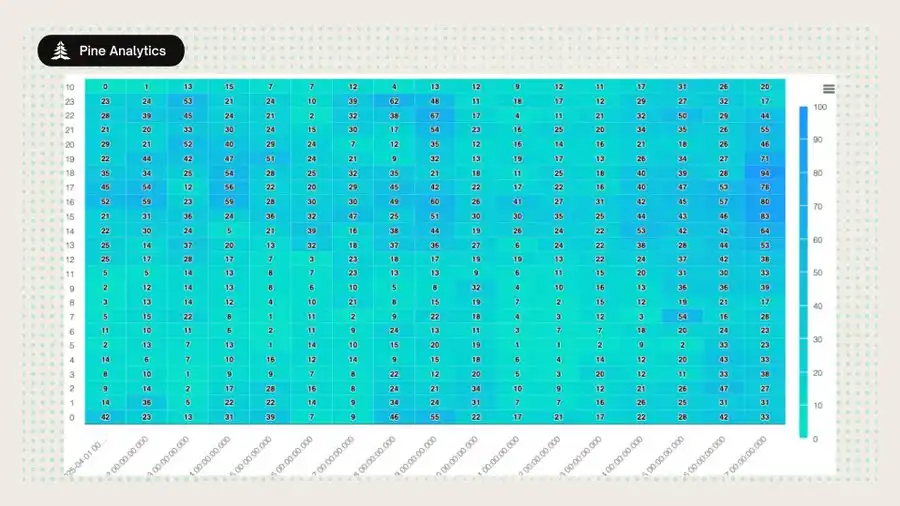
4. Sniping Exhibits a Human-Centric Time Pattern
a. Activity peaks during UTC 14:00–23:00; nearly ceases during UTC 00:00–08:00;
b. Aligning with U.S. working hours, indicating manual/cron timed triggers rather than global 24-hour automation.
5. Single-Use Wallets and Multi-Signature Transactions Obfuscate Ownership
a. Deployers fund several wallets simultaneously and sign snipes in the same transaction;
b. These burn wallets do not sign any transactions afterward;
c. Deployers split the initial purchase across 2–4 wallets to disguise real demand.
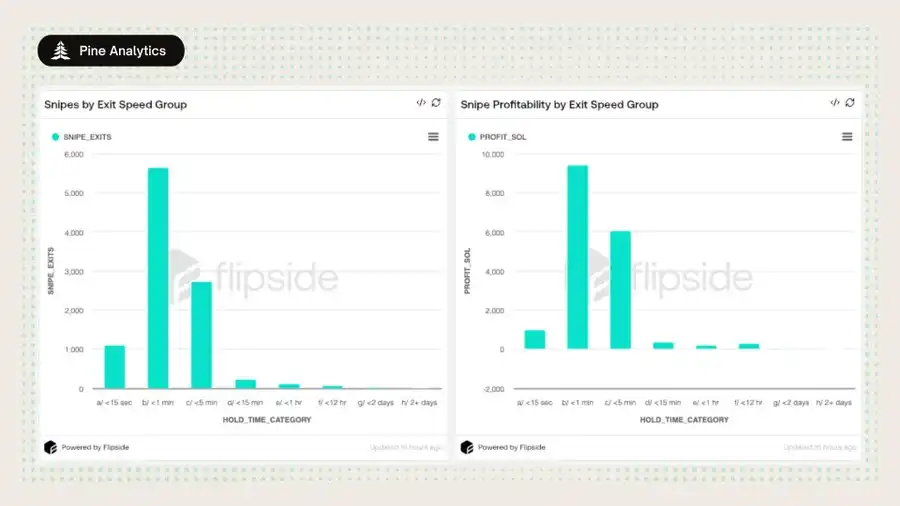
Exit Behavior
To gain deeper insights into how these wallets exit, we break down the data along two major behavioral dimensions:
1. Exit Speed — the time from the first purchase to the final sale;
2. Swap Count — the number of independent sell transactions used to exit.
Data Conclusions
1. Exit Speed
a. 55% of snipes are completely sold within 1 minute;
b. 85% are liquidated within 5 minutes;
c. 11% are completed within 15 seconds.
2. Swap Count
a. Over 90% of sniper wallets exit using only 1–2 sell orders;
b. Very few adopt gradual selling strategies.
3. Profit Trends
a. The most profitable wallets are those that exit within 1 minute, followed by those that exit within 5 minutes;
b. Longer holding periods or multiple sales, while having slightly higher average profits per transaction, contribute minimally to total profits due to their low frequency.
Explanation
These patterns indicate that deployer-funded sniping is not a trading behavior but rather an automated, low-risk extraction strategy:
· Early purchase → quick sale → complete exit.
· A single sell order reflects indifference to price fluctuations, merely taking advantage of the opportunity to dump.
· A few more complex exit strategies are exceptions, not mainstream patterns.
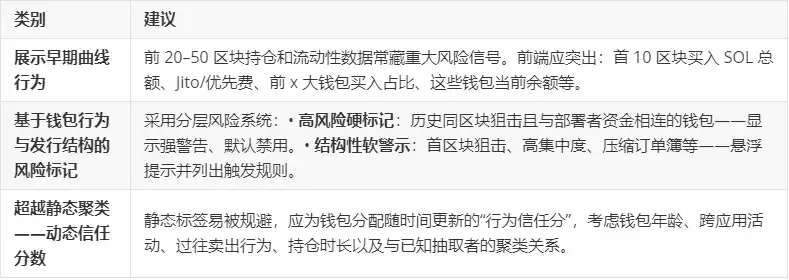
Actionable Insights
The following recommendations aim to help protocol teams, front-end developers, and researchers identify and respond to extraction or collusive token issuance models by transforming observed behaviors into heuristics, filters, and alerts, thereby increasing user transparency and reducing risk.
Conclusion
This report reveals a persistent, structured, and highly profitable extraction strategy for Solana token issuance: deployer-funded same-block sniping. By tracking direct SOL transfers from deployers to sniper wallets, we identify a set of insider-style behaviors that leverage Solana's high throughput architecture for coordinated extraction. Although this method only captures a portion of same-block sniping, its scale and pattern indicate that this is not sporadic speculation but rather operators with privileged positions, repeatable systems, and clear intentions. The significance of this strategy lies in:
1. Distorting early market signals, making tokens appear more attractive or competitive;
2. Endangering retail investors — who unknowingly become exit liquidity;
3. Undermining trust in open token issuance, especially on platforms like pump.fun that prioritize speed and ease of use.
To mitigate this issue, passive defenses are not enough; better heuristics, front-end alerts, protocol-level safeguards, and ongoing mapping and monitoring of collusive behaviors are needed. Detection tools already exist — the question is whether the ecosystem is willing to truly apply them.
This report takes the first step: providing a reliable, reproducible filter to identify the most obvious collusive behaviors. But this is just the beginning. The real challenge lies in detecting highly obfuscated, constantly evolving strategies and building an on-chain culture that rewards transparency rather than extraction.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



