The reasons and impacts of the recent attack on Cetus are still unclear. Let's first take a look at the code security audit situation of Cetus.
For those unfamiliar with the technical details, we can understand the audit summary.
➤ Certik's Audit
According to Certik's security audit of Cetus, only 2 minor risks were found, both of which have been resolved. There are also 9 informational risks, with 6 resolved.
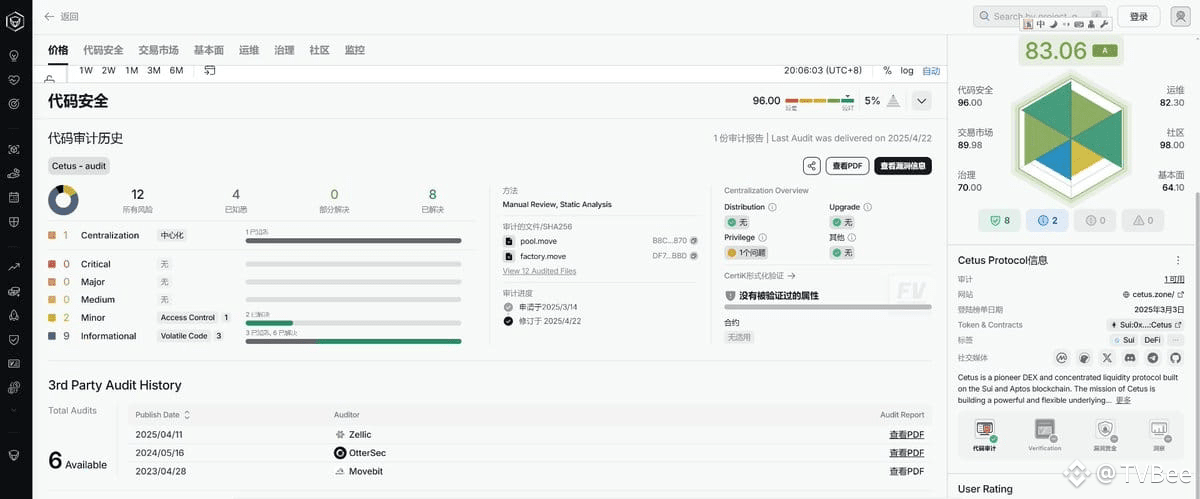
Certik provided an overall score of 83.06, with a code audit score of 96.
➤ Other Audit Reports of Cetus (SUI Chain)
A total of 5 code audit reports are listed on Cetus's GitHub, excluding Certik's audit. It is estimated that the project team is aware that Certik's audit is merely formal, so they did not include this report.
Cetus supports both Aptos and SUI chains, and these 5 audit reports come from MoveBit, OtterSec, and Zellic. MoveBit and OtterSec audited Cetus's code on the Aptos and SUI chains, respectively, while Zellic also audited the code on the SUI chain.
Since the attack occurred on Cetus on the SUI chain, we will only look at the audit reports for Cetus on the SUI chain.
❚ Audit Report from MoveBit
Report uploaded to GitHub on: 2023-04-28
If we do not understand the specific audit content, we can find a table like this to see the number of risk issues listed in the report at various levels and their resolution status.
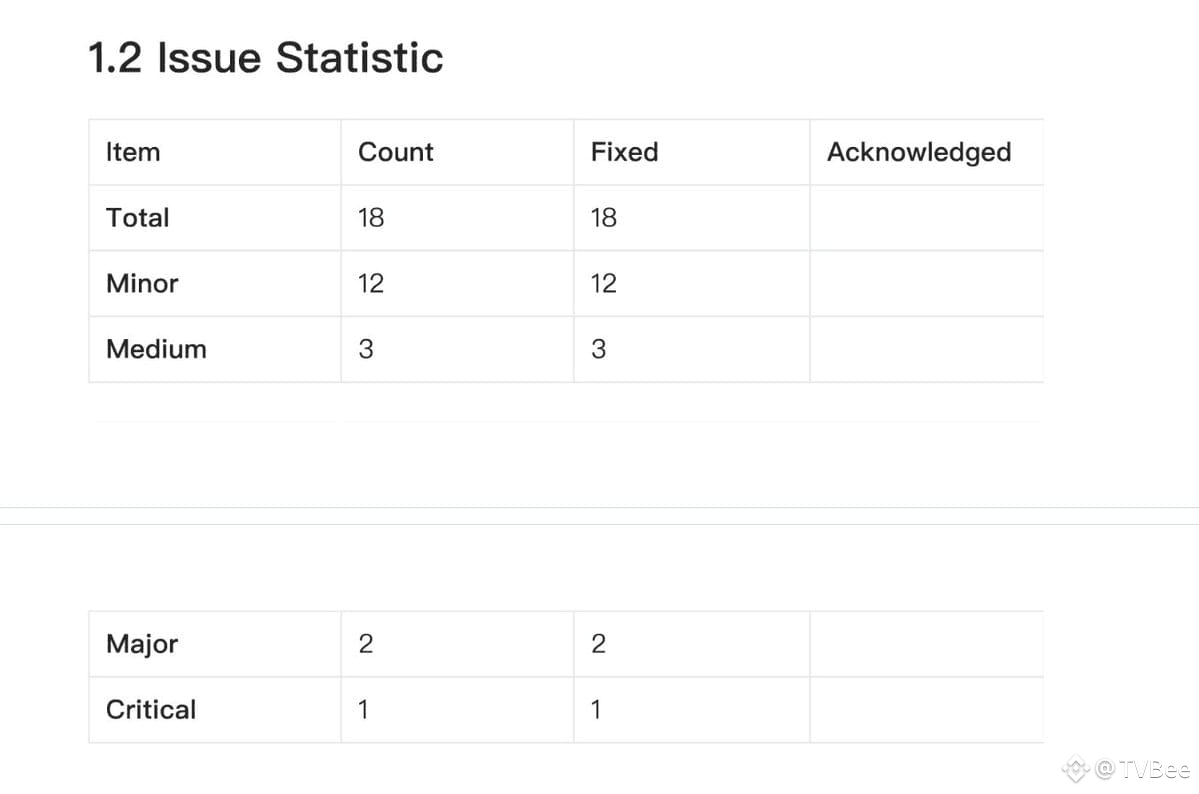
MoveBit's audit report for Cetus identified a total of 18 risk issues, including 1 critical risk issue, 2 major risk issues, 3 moderate risk issues, and 12 minor risk issues, all of which have been resolved.
This is more than the issues found by Certik, and Cetus has resolved all of these issues.
❚ Audit Report from OtterSec
Report uploaded to GitHub on: 2023-05-12
OtterSec's audit report for Cetus identified 1 high-risk issue, 1 moderate risk issue, and 7 informational risks. Since the report's table does not directly show the resolution status of the risk issues, I will not include a screenshot.
Both the high-risk and moderate-risk issues have been resolved. Of the informational risk issues, 2 have been resolved, 2 have submitted patches for fixes, and 3 remain. After some research, these 3 are:
• Inconsistency between Sui and Aptos version codes, which may affect the accuracy of liquidity pool price calculations. • Lack of pause state validation, meaning there is no verification of whether the liquidity pool is in a paused state during swaps. If the pool is paused, trading may still be possible. • Converting u256 type to u64 type, which can cause overflow if the value exceeds MAX_U64, potentially leading to calculation errors during large transactions.
It is currently uncertain whether the attack is related to these issues.
❚ Audit Report from Zellic
Report uploaded to GitHub on: April 2025
Zellic's audit report for Cetus identified 3 informational risks, none of which have been fixed:
• A function authorization issue that allows anyone to call and deposit fees into any partner account. This seems to pose no risk, as it involves depositing money rather than withdrawing it. Therefore, Cetus has not fixed this for now.
• There is a function that has been deprecated but is still referenced, resulting in code redundancy. It seems to pose no risk, but the code is not sufficiently standardized.
• A UI presentation issue in NFT display data, where a character type could have been used, but Cetus opted for the more complex TypeName data type in Move language. This is not a significant issue and may allow Cetus to develop additional features for NFTs in the future.
Overall, Zellic identified 3 minor issues that are primarily related to code standardization and pose minimal risk.
We should remember these three audit firms: MoveBit, OtterSec, and Zellic. Most audit firms in the market are skilled in EVM audits, while these three specialize in Move language code audits.
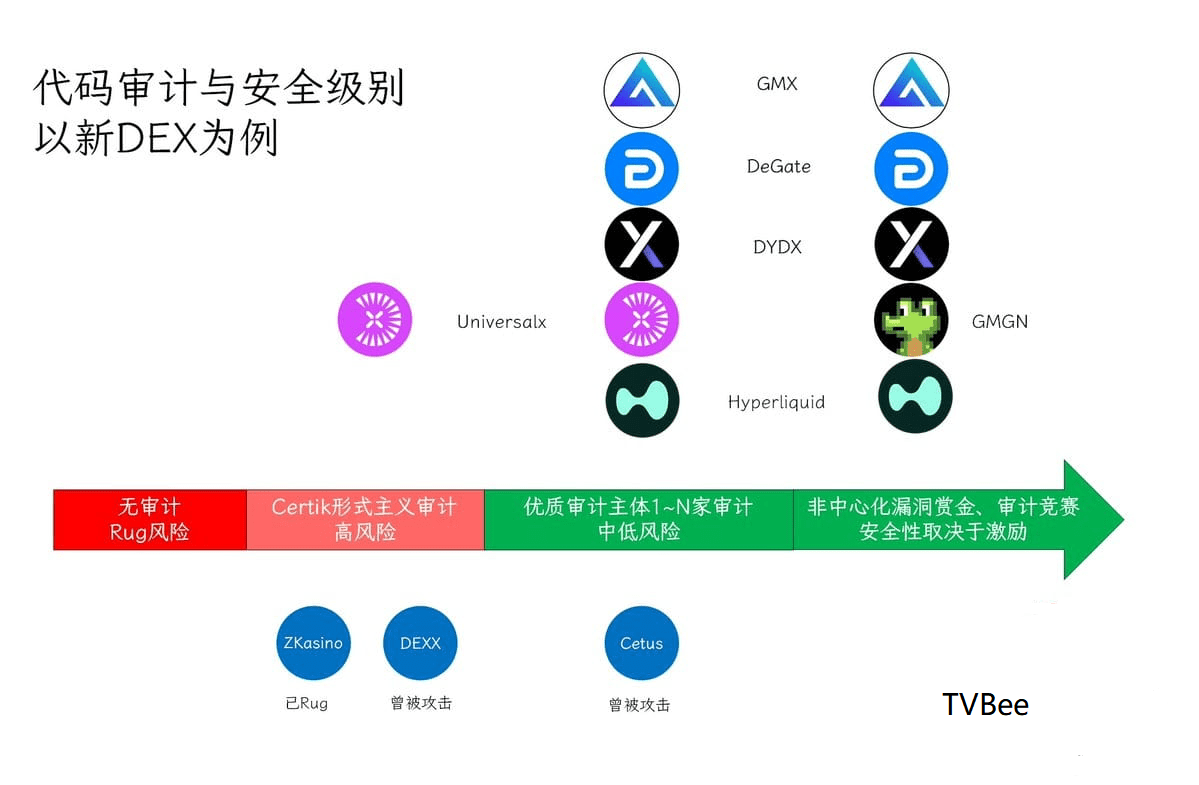
➤ Audit and Security Levels (Using New DEX as an Example)
First, projects that have not undergone code audits carry a certain risk of rug pulls. After all, if they are unwilling to spend money on audits, it is hard to believe they have long-term operational intentions.
Secondly, Certik audits are essentially a form of "favor-based auditing." Why is it called "favor-based auditing"? Certik has a very close partnership with CoinMarketCap. On the project page of CoinMarketCap, there is an audit icon that links to Certik's navigation platform, Skynet.
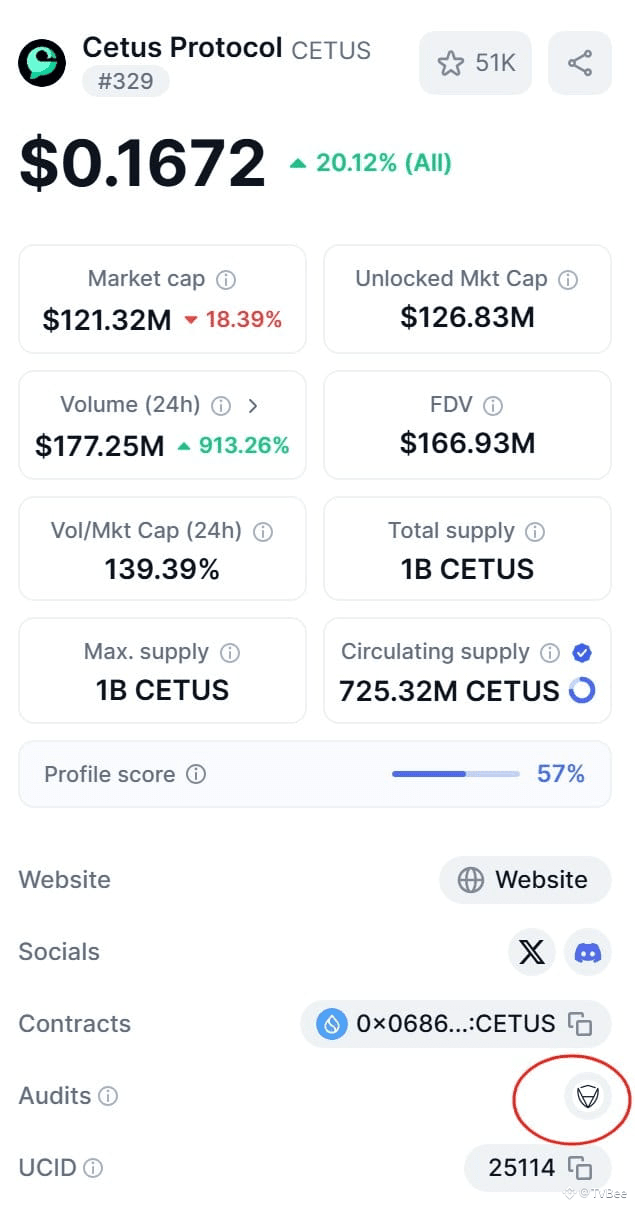
As CoinMarketCap is a platform under Binance, it indirectly establishes a partnership between Certik and Binance. In fact, Binance and Certik have always had a good relationship, so most projects wanting to list on Binance will seek Certik's audit.
Therefore, if a project seeks Certik's audit, it is highly likely that they want to list on Binance.
However, history has shown that projects audited solely by Certik have a high probability of being attacked, such as DEXX. Some projects have even already failed, such as ZKasino.
Of course, Certik also provides other security assistance; in addition to code audits, Certik scans websites, DNS, and offers some security information beyond code audits.
Thirdly, many projects will seek one or more other quality audit firms for code security audits.
Fourthly, in addition to professional code audits, some projects will also conduct bug bounty programs and audit competitions to gather ideas and eliminate vulnerabilities.
Since the attacked product is a DEX, here are some examples of newer DEXs:
---------------------------
✦✦✦ GMX V2, audited by 5 companies: abdk, certora, dedaub, guardian, and sherlock, and launched a bug bounty program with a maximum reward of $5 million.
✦✦✦ DeGate, audited by 35 companies including Secbit, Least Authority, and Trail of Bits, and launched a bug bounty program with a maximum reward of $1.11 million.
✦✦✦ DYDX V4, audited by Informal Systems, and launched a bug bounty program with a maximum reward of $5 million.
✦✦✦ hyperliquid, audited by hyperliquid, and launched a bug bounty program with a maximum reward of $1 million.
✦✦ UniversalX, audited by both Certik and Slow Mist.
✦ GMGN is somewhat special; no code audit report was found, only a bug bounty program with a maximum reward of $10,000.
➤ Final Thoughts
After reviewing the code security audit situations of these DEXs, we can see that even a DEX like Cetus, which has been audited by three firms, can still be attacked. Multi-party audits, combined with bug bounty programs or audit competitions, provide relatively better security.
However, for some new DeFi protocols, there are still unresolved issues in the code audits, which is why the community is particularly concerned about the code audit status of new DeFi protocols.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




