Summary of Views
I. Frequent Security Vulnerabilities Break the Illusion of Industry Safety
Bybit was hacked for $1.4 billion, and Infini was hacked for $50 million, revealing the industry's security vulnerabilities through a series of large-scale cyberattacks.
Exchanges, wallet providers, and industry regulators all need to take responsibility for security, but currently, there is a lack of unified security standards in the industry.
Cold wallets are not absolutely secure; security vulnerabilities often stem from human error and negligence in system permission management.
II. Market Sentiment Fluctuates Dramatically, Industry Self-Rescue and Regulatory Response Lagging
Following the Bybit incident, market panic intensified, but institutional funds quickly flowed in with $4 billion, demonstrating the industry's resilience.
Regulatory agencies (such as the FBI) did not intervene immediately but have begun investigations and called for global exchanges to assist in freezing hacker funds.
Mature regulatory frameworks in regions like the EU and Singapore may prompt the industry to strengthen security standards, while the U.S. may accelerate anti-money laundering and KYC regulatory legislation.
III. Investors Should Adopt Anti-Fragile Strategies and Enhance Security Awareness
Choose compliant and transparent platforms, paying attention to team backgrounds, reserve proofs, past security records, and other factors.
Diversify investments and manage risks to reduce overall losses from single points of failure, combining centralized exchanges, DeFi protocols, and hardware wallets for varied storage methods.
Optimize personal security operations by employing multi-signature, cold-hot wallet isolation, and permission management measures to reduce human operational risks.
Seek opportunities in crises; during the accelerated process of industry security standardization and institutionalization, strategically allocate assets to avoid short-term losses and seize long-term gains.
IV. Industry Trend: The Crypto Market is Entering an Institutional Era
Although market sentiment is low in the short term, strengthened regulation, innovations in security technology, and accelerated compliance processes will drive the market towards maturity.
Investors with anti-fragile thinking will gain an advantage in turmoil, adjusting strategies to adapt to market changes by borrowing from the "anti-fragile" concept.
From Cold Wallets to Hot Crises: How Major Failures Trigger Turbulence and How Investors Can Be Anti-Fragile?
Less than two days after Bybit was hacked for over $1.4 billion, the Hong Kong-based financial payment platform Infini was hacked for nearly $50 million. In a market filled with anxiety, investor sentiment was once again overshadowed by pessimism. Although there have been many theft incidents in history, such consecutive large-scale hacks have cast a shadow over an already fragile market. This raises the question: how should investors view the series of theft incidents in the industry, and how should they actively adjust their strategies to remain optimistic in the face of industry pessimism?
I. From Bybit to Infini: The Security Illusion Behind Breached Defenses
Regarding the historically largest theft incident at Bybit, there have been many analyses from various angles in the market (4 Alpha has also followed up on the incident promptly). However, before the industry could fully quell the panic surrounding this event, Infini was hacked for nearly $50 million again.
Although, like Bybit, Infini quickly claimed full compensation, this did not alleviate market concerns. People cannot help but reflect: why do the security defenses of industry giants still get breached despite numerous historical theft incidents? A deeper analysis reveals that these theft incidents involve not only vulnerabilities in the project/exchange's own security systems but also a series of issues related to regulatory oversight and the establishment of unified security standards in the blockchain industry.
- Main Attack Process and Causes of the Bybit Incident
Multiple industry security organizations have confirmed that the hackers behind the Bybit theft primarily belong to the notorious North Korean hacking group Lazarus Group. According to the latest investigation results from February 26, this group infiltrated a machine belonging to Safe developers through social engineering or other means, gaining access to the front-end infrastructure, deploying malicious code, and deceiving three signers at Bybit to execute a precise attack, successfully stealing over $1.4 billion in Ethereum assets from Bybit's cold wallet (a product of the Safe team). The Infini theft incident has been clarified to have occurred due to the malicious exploitation of internal engineers' system permissions, with hacking methods nearly identical to those in the Bybit incident.
Chart: Bybit Exchange Attack Process
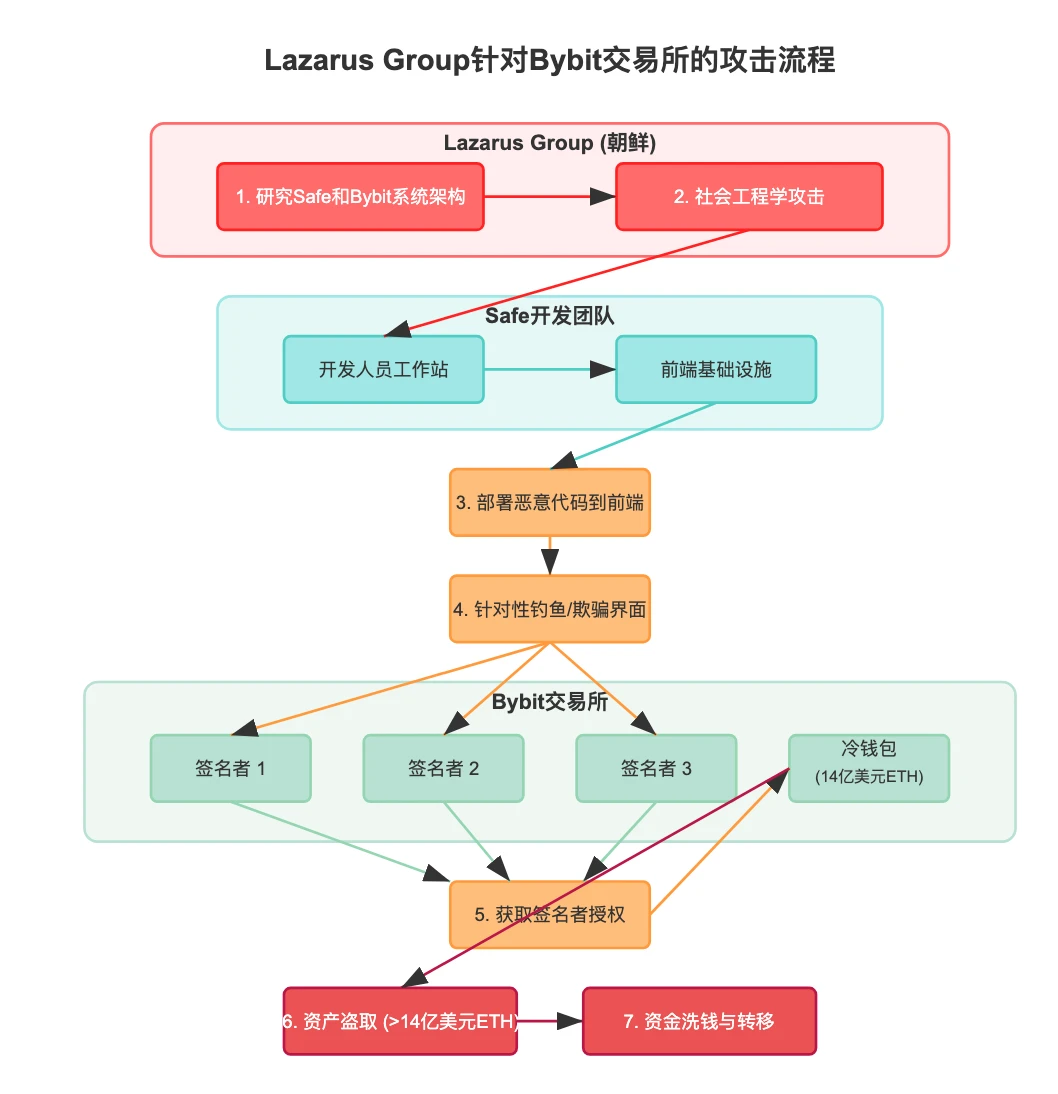
Chart created by: 4 Alpha Group
In the Bybit incident, although the Safe team promptly provided an investigation and explanation report, many industry figures, including former Binance CEO CZ, expressed dissatisfaction with the Safe security team's statement, particularly regarding the lack of a detailed report on the specific intrusion method. From the perspective of the attack entry, the Safe team, as the wallet provider, should bear primary responsibility, as there were deficiencies in both their development process and infrastructure security. However, whether such incidents are solely the responsibility of the wallet provider requires further exploration and reflection.
2. Cold Wallet Theft Highlights the Lack of Unified Security Consensus in the Industry
Whether it is the theft of Bybit or Infini, the entire industry is warned: one should not overly rely on the illusion of security provided by technology; any technology can be breached; and neglecting human security defenses can lead to fatal consequences.
Cold wallets have long been viewed as the "ultimate safe" for crypto assets, but the Bybit incident shattered this illusion. The cold wallet itself was not directly breached; rather, it was bypassed through front-end manipulation, exposing the vulnerability of relying on a single technological solution. The deeper issue lies in the lack of unified security standards and consensus in the industry. Whether it is exchanges or project parties, they often build their protective systems based on their own understanding rather than following common best practices. For example, Bybit did not set up a secondary review mechanism for cold wallet operations, and Safe did not strictly isolate development permissions, providing hackers with opportunities due to these human oversights.
Moreover, asset custody, insurance mechanisms, and security audits have yet to form systematic norms within the industry. Historically, from Mt. Gox to multiple theft incidents at Binance, despite technological advancements, the ability to systematically counter hackers has seen limited improvement. The root cause is the fragmented regulatory environment, which makes it difficult to unify investor protection and security standards, leading to varying security levels across platforms. In this situation, the concentration of large assets in a few protocols or platforms becomes a primary target for hackers.
II. Industry Response to Thefts: From Panic to Self-Healing, Insights from the Collective Experience
After the significant theft at Bybit, the CEO quickly went live to disclose relevant information and did not suspend withdrawals. Within 12 hours after the peak of withdrawals, the entire system returned to normal. However, during this process, the industry experienced significant volatility, and both market participants and industry regulators reacted.
1. Industry Self-Rescue and Resilience
Following the Bybit incident, multiple industry institutions extended a helping hand to assist the exchange in overcoming difficulties, with net inflows exceeding $4 billion within 12 hours, reflecting the industry's maturity in crisis response, especially within four hours after the incident (e.g., Elliptic, Chainalysis) confirmed that the attack originated from the Lazarus Group and assisted in tracking the flow of funds.
It is noteworthy that user reactions were polarized. Despite Bybit's promise of full compensation, withdrawal volumes surged, and on-chain data showed a rapid increase in stablecoin transfers, with significant funds flowing into DeFi protocols. This indicates that even among the top three exchanges in the industry, users still tend to "vote with their feet" in the face of a massive hacking incident, prioritizing self-protection over trusting the platform's promises. The market's fear and greed index plummeted to extreme fear levels in a single day, highlighting the difficulty of restoring confidence.
The response to the Infini incident was similar. Although its scale was smaller, the consecutive attacks heightened market anxiety. Project parties and security companies began calling for enhanced permission management and third-party audits, with some institutions even proposing the establishment of an industry mutual aid fund to address similar crises. These real conditions in the industry indicate that user trust is relatively fragile, further underscoring the urgency of accelerating regulatory compliance.
2. Regulatory Agencies Did Not Intervene Immediately, but Their Attitude May Be Influenced
Behind both incidents, more actions from the industry were observed. Regulatory bodies worldwide did not speak out immediately, but this does not mean there was no impact on regulation. Just this Thursday, the FBI in the U.S. has intervened in the investigation of the Bybit theft case and called for global exchanges to assist in freezing assets related to the North Korean hacking organization.
In regions like the EU and Singapore, where relatively mature regulatory systems exist, these incidents may further strengthen the enforcement of compliance frameworks. For the U.S., we expect this incident may prompt regulatory agencies to reconsider anti-money laundering and related KYC requirements for crypto platforms. Although President Trump promised to create a "crypto capital," the SEC's previous regulatory stance indicates that "technological neutrality" and "investor protection" are important bases and principles for regulation. This may, to some extent, accelerate regulatory legislation and hasten the overall process of establishing security standards in the industry.
From users "voting with their feet" on security to the delayed responses from regulators, it reveals that the entire crypto industry is still in a state of security normlessness. However, with the advancement of global regulatory legislation and the acceleration of compliance processes, the crypto industry is becoming increasingly mature and moving towards the mainstream, which is inevitable. This means that for investors, one should never overlook investment risks and asset security in the current industry.
III. How Investors Can Adjust: Rebuilding Anti-Fragility, Security and Compliance Remain Top Priorities
As a responsible asset management institution, in the face of the consecutive large-scale hacking incidents at Bybit and Infini, we firmly believe that security and compliance are not only the primary guarantees for institutional operations but also the highest priority for protecting client assets. These events not only sound the alarm for the industry but also provide investors with an opportunity to reassess their strategies.
In a turbulent market environment, we advise investors to shift from "passive panic" to "active anti-fragility," responding to uncertainty with a more resilient mindset. Here are specific recommendations based on our years of experience and professional insights:
1. Choose Compliant and Transparent Platforms, but Pay More Attention to Team Expertise and Industry Reputation
When selecting an investment platform, compliance and transparency are basic thresholds, but they are far from sufficient to cope with the increasingly complex risk environment. We recommend that investors thoroughly assess the team's expertise and industry reputation of the platform, as these are often key indicators of its long-term reliability. A team with rich financial backgrounds, technical expertise, and crisis response capabilities can demonstrate stronger adaptability and responsibility in critical moments. For example, as an asset management institution, we comprehensively evaluate potential strategy partners, including but not limited to reserve proofs, audit reports, and past crisis response situations, to ensure that every asset entrusted by clients can withstand the test of time. Investors can also adopt this standard, choosing platforms that demonstrate accountability in crises and maintain transparency in compliance.
2. Enhance Self-Security Awareness, Diversify Risks, and Reduce Overall Losses from Single Points of Failure
Technical vulnerabilities and human negligence are the core lessons from this hacking incident, reminding investors that they must actively enhance their security awareness rather than completely rely on platform promises. While cold wallets are not a panacea, they remain an effective tool for personal asset protection. Regularly checking permission settings and avoiding links from unknown sources can significantly reduce the risk of being attacked. At the same time, diversifying investments is an effective strategy to guard against single points of failure. We recommend that investors allocate their assets across various platforms (such as centralized exchanges, DeFi protocols, and hardware wallets) and diversify across regions and asset classes.
3. Strictly Adhere to Security Operation Requirements and Continuously Optimize Security Measures
Security is not only a technical issue but also a reflection of processes and discipline. As an asset management institution, we strictly implement multi-signature, cold-hot wallet isolation, and permission tier management in our daily operations, along with regular audits to ensure that protective measures are up to date. Investors should also regard security operations as a norm. In the face of continuously evolving hacking techniques, protective measures need to be continuously optimized. We advise investors to pay attention to industry trends, learn the latest security best practices, and introduce professional custody services or insurance mechanisms when asset scales are significant, further strengthening their defenses. This shift from passive defense to active optimization is a key step in achieving "anti-fragility."
4. The Industry is Rapidly Entering an Institutional Era, Finding Opportunities in Crisis
Although market sentiment is low in the short term due to hacking incidents and external macro factors, we believe that crises often serve as catalysts for industry self-repair and upgrades. Strengthened regulation, innovations in security technology, and the proliferation of decentralized solutions will bring long-term benefits to compliant platforms and projects. Investors can take advantage of market panic to prudently allocate assets, seeking investments that offer the greatest stability and yield match.
Our investment strategy always revolves around this principle, capturing excess returns for clients in turbulent times through multi-strategy asset management solutions, while ensuring that security and compliance are the bottom line, guaranteeing that every return can withstand the test of risk.
Drawing on Nassim Taleb's concept of "anti-fragility," we also encourage investors to view crises as opportunities to optimize strategies rather than mere threats. For example, building positions in quality assets during extreme market panic or choosing relatively stable quantitative arbitrage strategies. This proactive adaptability can not only help investors avoid losses in the short term but also position them advantageously when the industry recovers.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



