This article Hash (SHA1): 221158eb736fa9ed3c6fb54451647bd73ca362c7
Number: Chain Source Technology PandaLY Anti-Fraud Guide No.003
With the Federal Reserve announcing a 50 basis point (50BP) rate cut in September, a massive trading frenzy erupted in the cryptocurrency market, leading to a sudden surge in on-chain trading data. Amidst the strong market volatility, investors rushed to adjust their asset portfolios, attempting to seize the opportunity for higher returns. However, this trading wave brought not only the chance for wealth growth but also lurking security threats. The PandaLY security team discovered that as trading volumes soared, hackers became increasingly active, exploiting investors' negligence during high-frequency trading, resulting in a dramatic increase in wallet address spoofing scams.
In recent security cases we have received, the proportion of scams involving forged wallet addresses has sharply risen. These scams create fake addresses that closely resemble the last few characters of users' real wallet addresses, tricking users into inadvertently transferring funds to wallets controlled by hackers during on-chain transactions. Many users rely on memory for the last few characters of wallet addresses or habitually copy addresses from historical transaction records, providing hackers with an opportunity to misappropriate significant amounts of funds without the victims realizing it.
Behind this phenomenon, in addition to the intense market fluctuations, there are several key factors. First, the operational habits of investors during on-chain transfers make these scams highly deceptive, especially when on-chain trading data surges, as users often lack the time and energy to verify details carefully. Second, hackers' technical methods are becoming increasingly sophisticated, allowing them to quickly generate forged addresses that even match the first or last few characters of users' wallet addresses, further increasing the scams' concealment.
Therefore, to help investors safely transfer funds and effectively avoid scams during this market surge, the PandaLY security team will provide a detailed analysis of the operational mechanisms of these scams and reveal the underlying technical principles. At the same time, we will offer a practical prevention guide to help you protect your digital assets from harm during high-frequency trading.
1. Technical Principles of Wallet Address Forgery Scams
Wallet Address Generation Mechanism
In blockchain transactions, wallet addresses serve as users' identity markers, with each address being unique, ensuring the security and immutability of transactions. However, generating wallet addresses with specific characters is not as complex as one might think. Taking the Ethereum network as an example, each wallet address consists of hexadecimal characters (0-9 and A-F), meaning that if a hacker wants to generate a wallet address with the last N characters being the same, the probability of success is one in 16 to the power of N.
Although this probability seems extremely low, hackers can easily generate these forged addresses using scripts and computational power through brute force methods. For example:
The probability of generating an address with 4 identical characters is 1/65536, which can be generated in seconds using ordinary computing devices and scripts.
The probability for 5 identical characters is 1/1048576; although the difficulty increases, it can still be generated in a short time with appropriate scripts and higher-performance devices.
The probability for 7 identical characters is only 1/268435456; hackers need more powerful computing capabilities and longer traversal times, but it is technically feasible.
Recent statistics from the PandaLY security team analyzing some forged address cases revealed that most of the forged addresses generated by hackers matched the last 5 to 7 characters of the target address. These forged addresses are often generated through simple brute force methods, allowing hackers to create a sufficient database of forged addresses within a few hours or days to select targets for scams.
Hackers' Forged Wallet Generation Strategy
Hackers' attack strategies are highly targeted, often selecting high-net-worth users as targets, especially those who frequently conduct large on-chain transfers and interact across multiple wallets. Once these users are identified, hackers begin deploying forged wallet addresses and continuously monitor the transaction behaviors of these target users.
The general steps of hackers' attacks are as follows:
Identify the target: Hackers use on-chain data analysis tools to filter out accounts that frequently conduct large transactions, particularly those with multiple interacting addresses.
Generate forged addresses: Hackers use brute force methods to create wallet addresses that match the last few characters of the target address. Typically, hackers generate multiple forged addresses to ensure coverage of the target user's commonly used wallets.
On-chain monitoring: Hackers monitor the transaction dynamics of the target account in real-time. When the target account initiates a fund transfer, hackers immediately use a forged address to conduct a transfer of the same amount, creating a similar transaction record.
Confuse the user: When users make their next transfer, they often copy wallet addresses from historical transaction records. If users rely solely on memory or briefly check the last few characters of the address, they are likely to inadvertently transfer funds to the hacker's forged wallet.
This attack strategy is highly deceptive, especially in high-frequency trading situations where users' awareness of potential threats is typically low, making them more susceptible to confusion from forged addresses. Once funds are transferred to a forged wallet, tracking and recovering them becomes extremely difficult, often resulting in irreversible losses for users.
2. Scam Analysis
According to the latest data from the PandaLY security team, as on-chain trading volumes have surged, wallet address forgery scams have occurred frequently, particularly on high-volume networks like Ethereum and TRON. The number of wallet address forgery scam cases increased by 45% in the past quarter, with victims primarily being high-frequency trading users. The scam rate for these users is 35% higher than that of ordinary users, and these victims often mistakenly transfer funds to forged addresses while conducting multiple transactions in a short period.
In these cases, about 60% of the forged addresses matched the last 5 to 6 digits of the target address, and even 25% of the forged addresses matched the last 7 digits. This high degree of matching is highly misleading, making it easy for users to misjudge and inadvertently transfer funds to wallets controlled by hackers. Once funds are transferred to a forged address, recovery becomes extremely challenging, with the current recovery rate for such cases being only 15%, further highlighting the importance of preventive measures.
Through in-depth analysis of typical cases, the PandaLY team found that hackers often utilize on-chain monitoring tools to accurately capture the timing of target users' transactions and forge seemingly identical transaction records to confuse users' judgments. Particularly for those who frequently conduct large transactions, they often only check the last few characters of wallet addresses in urgent situations, falling into the trap of scams.
Scam Implementation Process
The core of the wallet address forgery scam lies in hackers generating forged addresses that share some characters with the target address, thereby confusing users' judgments. When users conduct on-chain transfers, they typically rely on the quick copy function for wallet addresses from historical transaction records, which gives hackers an opportunity.
The specific process is as follows:
Hackers lock onto target users: Target users are typically those who frequently conduct large on-chain transactions.
Generate forged addresses: Hackers generate wallet addresses that match the last few characters of the target address through scripting.
Monitor transaction behavior: Hackers monitor the target account's on-chain transactions in real-time. When the user initiates a transaction, hackers simultaneously initiate a transaction of the same amount to confuse the records.
User misoperation: When users make their next transfer, they may only check the last few characters of the wallet address, leading to the copying of the forged address and mistakenly transferring funds to the hacker's wallet.
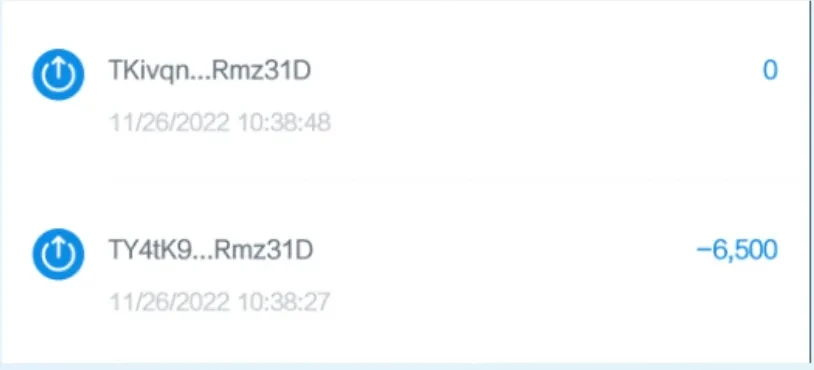
Address Poisoning Attack
Additionally, since the target of cryptocurrency asset transfers is a string of address hashes, users generally use the address copy function provided by wallets or browsers to paste the recipient's wallet address. Since blockchain explorers and web3 wallet pages typically do not display the full addresses of both parties in a transaction, but rather show the first part of the address with ellipses in between, if a phishing address matches the beginning and end of the real transaction partner's address, victims are likely to mistakenly treat the phishing address as the actual address they intend to interact with.
In conducting address poisoning attacks, attackers listen for transaction information of stablecoins (such as USDT, USDC) or other high-value tokens on-chain, using vanity address generators (like Profanity2) and other tools to quickly generate phishing addresses that match the first and last characters of the victim's address.
Depending on the principles of the attacking transactions, address poisoning phishing can be divided into the following three categories:
- Zero Transfer Phishing
Zero transfer attacks exploit the conditions for authorization limits in the transferFrom function. When the amount of tokens transferred is zero, the transaction can still proceed successfully and emit a token transfer event log, even without the sender's authorization. Blockchain explorers and wallets will detect this event and display the token transfer transaction in the user's transaction history.
The address of the transfer initiator is the victim's address, while the recipient's address is a phishing address that matches the beginning and end of the real recipient's address. If the victim is careless during their next transfer and directly copies the historical transaction address, they are likely to mistakenly copy the hacker's prepared phishing address, resulting in funds being transferred incorrectly.
To identify this most basic form of address poisoning attack, we only need to recognize transactions where the transferred token amount is zero.
To bypass wallet and blockchain explorer checks for zero-value transfers, small transfer phishing and fake token phishing have emerged.
- Small Transfer Phishing
Small transfer attacks are a variant of zero-value transfer phishing. Unlike fake token attacks, small transfer attacks use real value tokens to bypass fake token checks, but the amount of tokens transferred is often less than 1 dollar, representing a fraction of a real transaction, sometimes even less. To make phishing transactions appear more similar to real transaction history, phishing attackers may carefully design the transfer amount, replacing the thousand separators of the real transaction amount with decimal points.
Phishing attackers send fake tokens with the above characteristics to target victims using counterfeit addresses that match the beginning and end of the real addresses, leading users to mistakenly believe the phishing address is the actual transfer initiator's address and subsequently copy that address for their transactions.
- Fake Token Phishing
General blockchain explorers and wallets display token transfer history using the value of the Symbol variable in the token contract as the currency name. Fake token attacks exploit the fact that ERC-20 protocol tokens can have their Symbol defined arbitrarily, setting the Symbol string of fraudulent token contracts to match that of high-value tokens or stablecoins like USDT/WETH/USDC, and sending fake tokens to target victims using counterfeit addresses that match the beginning and end of the real addresses, making users mistakenly believe the phishing address is the actual transfer initiator's address and subsequently copy that address for their transactions.
Furthermore, to save on gas fees (especially on chains with high gas costs like Ethereum), fraudsters conducting address poisoning attacks typically deploy a phishing contract to transfer tokens to multiple victims in a single transaction.
Why Are Users Easily Tricked?
Users often rely on the last few characters of wallet addresses for quick confirmation when frequently using on-chain browsers to check transaction records, which has become a major vulnerability exploited by hackers. Due to the demands of transaction speed and frequency, users often neglect to verify the entire address, especially when conducting multiple similar transactions, making it easier to mistakenly transfer funds to hacker-generated forged addresses.
This type of scam takes advantage of the "simplification" habits in user operations, and what seems like an efficient way to operate is actually highly risky. To mitigate such risks, users should thoroughly verify wallet addresses for every transfer and not rely solely on the last few characters for quick confirmation.
3. Measures to Prevent Wallet Address Forgery Scams
1. Do Not Rely Solely on Memory to Match Wallet Addresses
In blockchain transactions, users' operational habits often create opportunities for hackers. Many people, when frequently using a particular wallet address, rely on memory to verify the last few digits of the address. On the surface, remembering the first few or last few characters of an address seems like a convenient way to simplify transactions, especially when users are accustomed to quick operations. However, this habit is extremely dangerous, as hackers exploit this "laziness" by generating forged addresses that partially resemble the target address, thereby deceiving users.
Moreover, hackers can even use technical means to generate forged addresses that match both the beginning and end of the target address, further increasing the confusion. Simply checking the first few or last few digits of an address is no longer sufficient to ensure safety. Hackers monitor on-chain activities, quickly deploying similar addresses and "striking" when the target user initiates a transfer.
Therefore, the safest practice is to carefully verify the entire address for every transfer, especially during large transactions, ensuring that all characters match. Users can also utilize security plugins or automated tools to reduce potential errors in manual operations. Additionally, regularly updating transaction processes and reminding oneself to pay attention to details is an important step to avoid falling victim due to negligence.
2. Use Whitelist Functionality
To address the issue of address confusion during frequent transactions, many mainstream wallets and trading platforms have introduced a "whitelist" feature, which is an extremely effective security measure. Through the whitelist function, users can save commonly used receiving addresses to avoid manually entering addresses for every transaction, thereby reducing the risk of human input errors or being deceived by forged addresses.
On trading platforms like Binance or Coinbase, users can pre-set receiving addresses as fixed addresses, and once the whitelist function is enabled, unauthorized new addresses cannot be added. This way, even if hackers attempt to alter addresses through phishing attacks, funds will safely transfer to the pre-set addresses on the whitelist.
For decentralized wallets (like MetaMask), the whitelist function is equally important. Users can save commonly used addresses to avoid having to re-enter long strings of address characters for every transfer, reducing the likelihood of misoperation. Furthermore, during on-chain transactions, this whitelist mechanism allows users to quickly verify and use validated addresses in a shorter time, ensuring the security of each transaction.
The whitelist function not only effectively prevents manual errors by users but also provides a convenient and secure operating experience for high-frequency traders. Regularly maintaining and updating the whitelist, removing infrequently used or risky addresses, is also key to enhancing security.
3. Purchase ENS (Ethereum Name Service) Addresses
ENS (Ethereum Name Service) is an innovative technology that allows users to bind complex Ethereum wallet addresses to short, memorable domain names. This provides users with a highly convenient and secure solution, especially when frequently entering addresses. By mapping a wallet address to an easy-to-remember ENS domain (like "mywallet.eth"), users no longer need to manually input a lengthy 42-character Ethereum address, avoiding the risk of losing funds due to manual input errors.
However, ENS domains are not permanently valid. Each ENS address has an expiration date, and users need to renew it regularly to ensure long-term usage rights. If a domain expires without renewal, others can register that ENS address, potentially threatening the user's transaction security. Once an ENS address is registered by someone else, all transaction addresses bound to that ENS domain may point to a hacker's wallet, resulting in financial losses. Therefore, after purchasing an ENS domain, users should set renewal reminders to ensure timely renewals before expiration to avoid the address being registered by others.
At the same time, while ENS greatly simplifies address management, it also introduces new security risks. If hackers register well-known or commonly used ENS addresses, they may use them for phishing activities. Therefore, users should carefully choose which ENS domains to purchase and regularly verify their validity and the bound address information.
In summary, ENS is not only a tool to enhance user experience but can also serve as a security measure. However, users must remain vigilant about renewal and maintenance issues to mitigate potential security risks. By using ENS wisely, users can significantly reduce the likelihood of input errors during transfers and enhance transaction security.
Conclusion
In conclusion, as the volatility of the cryptocurrency market intensifies, investors face unprecedented security risks while pursuing high returns, particularly with the proliferation of wallet address forgery scams. Hackers generate forged addresses that closely resemble real addresses, exploiting investors' operational habits and negligence to transfer significant amounts of funds under their control. The PandaLY security team urges investors to avoid relying on memory matching or copying addresses from historical records, and to always carefully verify every character. At the same time, reasonably utilizing security tools such as whitelist functionality and ENS addresses can strengthen the protection of funds. Safe investment is not a blind pursuit of high returns but a meticulous prevention of every detail. By staying vigilant and refining operational habits, investors can achieve stable asset growth in the opportunity-laden yet risky cryptocurrency market.
Chain Source Technology is a company focused on blockchain security. Our core work includes blockchain security research, on-chain data analysis, and asset and contract vulnerability rescue, successfully recovering numerous stolen digital assets for individuals and institutions. We are also committed to providing project security analysis reports, on-chain traceability, and technical consulting/support services for industry organizations.
Thank you for reading. We will continue to focus on and share blockchain security content.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



