This article Hash (SHA1): 9d28ef4e6e45c21121d4e6fc0ef7c011f48263d8
Number: Chain Source Technology PandaLY Security Knowledge No.025
Blockchain technology, as the core driving force of the digital economy, is revolutionizing the global financial and data security fields. However, the characteristics of decentralization and anonymity also attract the attention of cybercriminals, giving rise to a series of attacks on encrypted assets. Hackers never sleep, and places where funds are gathered are always their targets. According to data provided by various blockchain analysis and security companies, from 2020 to 2024, the losses caused by Web3-related hacker attacks have exceeded 3 billion US dollars. Our Chain Source security team will conduct in-depth analysis of several well-known blockchain hacker groups and their famous cases, revealing their modus operandi and providing practical strategies for individual defense against hacker attacks.
Modus Operandi and Theft Cases of Notorious Hacker Groups
North Korean Hacker Lazarus Group
Background:
According to information from Wikipedia, Lazarus Group was established in 2007 and is affiliated with the Reconnaissance General Bureau of the North Korean People's Army's General Staff Department, specializing in cyber warfare. The organization is divided into two departments: the first department is called BlueNorOff (also known as APT 38), with about 1700 members, mainly engaging in illegal transfers through forged SWIFT orders, focusing on exploiting network vulnerabilities for economic gain or controlling systems to commit financial cybercrimes, with a primary focus on financial institutions and cryptocurrency exchanges. The second department is AndAriel, with about 1600 members, primarily targeting South Korea.
Modus Operandi:

In the early days, Lazarus primarily conducted DDoS attacks through botnets, but now their attack methods have shifted to spear phishing, watering hole attacks, supply chain attacks, and targeted social engineering attacks against different targets. Lazarus uses spear phishing in emails and watering hole attacks on websites to achieve intrusion, and may use system disruption or ransomware applications to interfere with incident analysis. In addition, they may exploit SMB protocol vulnerabilities or related worm tools for lateral movement and payload delivery, and even carry out attacks on bank SWIFT systems to steal funds. Their technical features include the use of multiple encryption algorithms (such as RC4, AES, Spritz) and custom character transformation algorithms, disguising the TLS protocol to bypass IDS through white domain names in SNI records, and using IRC and HTTP protocols.
Furthermore, Lazarus damages systems by destroying MBR, partition tables, or writing garbage data to sectors, and uses self-deleting scripts to conceal attack traces. Their attack methods include using trojan programs as email attachments for spear phishing attacks, and intrusion through malicious documents and macros; in watering hole attacks, Lazarus analyzes the target's internet activities, attacks websites they frequently visit, and implants malicious code to steal funds on a large scale; in social engineering attacks, they obtain credentials by posing as recruiters for cryptocurrency or cybersecurity personnel, thereby carrying out attacks. Lazarus's arsenal includes a large number of custom tools, indicating the presence of a relatively large development team behind them. Their attack capabilities and toolkits include DDoS botnets, keyloggers, RATs, wiper malware, and malicious code such as Destover, Duuzer, and Hangman.
Cases:
- 2017 Bangladesh Bank Heist
Lazarus hackers stole $81 million by attacking the SWIFT system. Although this event mainly involved traditional banking systems, its impact also extended to the blockchain field, as funds obtained by hackers in this way are often used to purchase cryptocurrencies for money laundering.
- 2020 KuCoin Hack
In September 2020, KuCoin exchange suffered a large-scale hacker attack, resulting in losses of up to $200 million. Although direct responsibility was not fully confirmed, analysts believe it is related to Lazarus. The hackers exploited contract vulnerabilities and system weaknesses to steal a large amount of cryptocurrency and attempted to transfer and launder it through multiple channels.
- 2021 Ronin Network Attack
The Ronin network, which is part of the Axie Infinity game's blockchain, was attacked in March 2021, resulting in losses exceeding $600 million. Although direct responsibility has not been confirmed, many analysts have linked it to Lazarus or other state-sponsored hacker groups.
- 2022 Harmony Network Attack
The Harmony blockchain's cross-chain bridge was attacked in June 2022, resulting in approximately $100 million in losses. Although the identity of the attacker was not clear, some experts have linked it to the strategies of the North Korean hacker group, suggesting that they may have carried out this attack using similar methods.
Drainer Criminal Group
In the blockchain, "drainer" typically refers to a type of malicious smart contract or script designed to fraudulently steal funds from users' cryptocurrency wallets or accounts. These attacks often occur when users interact with counterfeit or compromised decentralized applications (dApps) or websites, and users may unknowingly authorize the malicious contract to control their funds. Some well-known drainer criminal groups include:
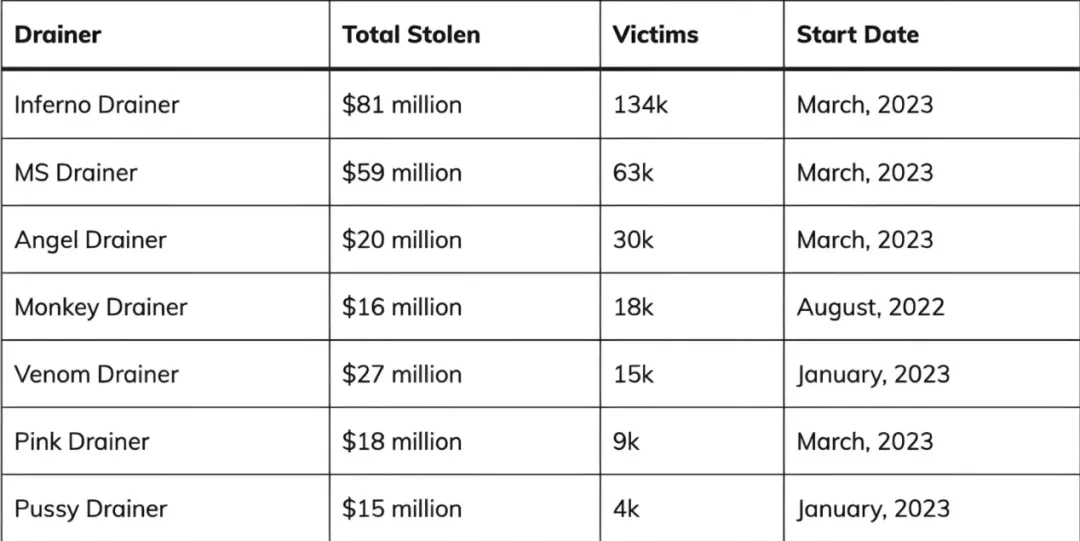
Background:
"Inferno Drainer" is one of the most popular cryptocurrency wallet scam tools, serving as a "Phishing-as-a-Service" (PaaS) platform that provides ready-made phishing tools for scammers. According to data from Web3 security company Blockaid, as of July 2024, the number of DApps using Inferno Drainer has increased to 40,000. The number of new malicious DApps using this tool has tripled, with a 300% increase in usage.
Modus Operandi:
The group promotes its services through Telegram channels, operating in a "fraud-as-a-service" model, where developers provide phishing websites to scammers to help them carry out fraudulent activities. When victims scan the QR codes on the phishing websites and connect their wallets, Inferno Drainer automatically checks and locates the most valuable and easily transferable assets in the wallets, and initiates malicious transactions. Once the victim confirms the transaction, the assets are transferred to the criminals' accounts. Of the stolen assets, 20% is given to Inferno Drainer's developers, and the remaining 80% goes to the scammers.
They primarily target users and platforms related to cryptocurrencies, such as decentralized finance (DeFi) applications, NFT markets, and cryptocurrency wallets. Using social engineering tactics, such as impersonating official announcements or airdrop activities, they induce users to authorize access to their wallets by disguising as legitimate applications or services, thereby stealing funds. The emergence of this tool has significantly lowered the threshold for carrying out online fraud, leading to an increase in related fraudulent activities.
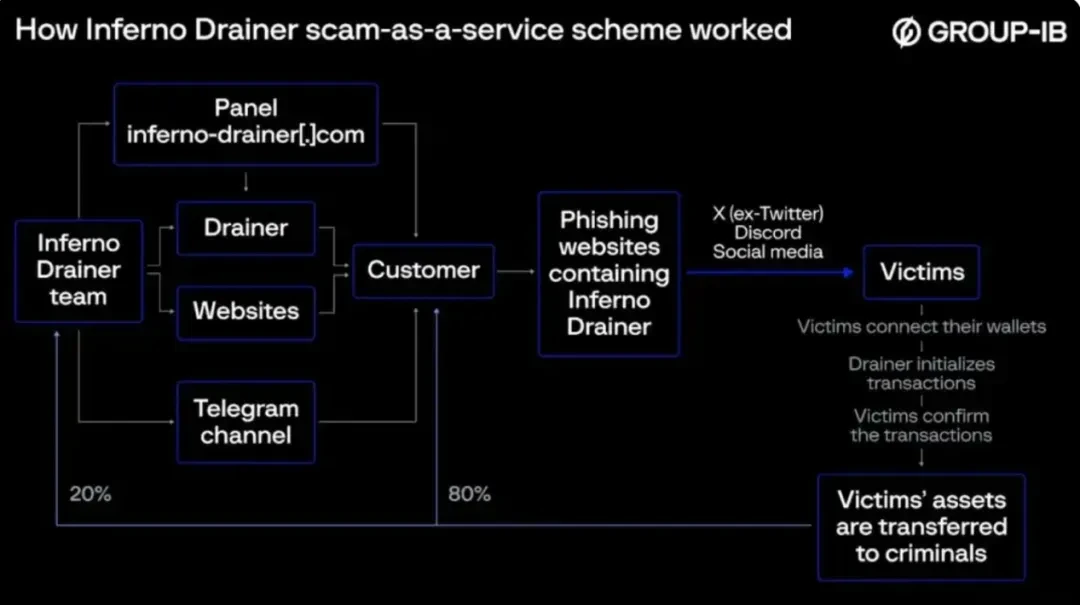
Cases:
- OpenSea Phishing Attack
Hackers used the Inferno Drainer platform to carry out phishing attacks against OpenSea users. OpenSea is a popular NFT marketplace, and many users' cryptocurrency wallets are associated with their accounts. The attackers created a phishing page disguised as the OpenSea website and attracted users to visit it through email and social media advertisements. When users connected their wallets and authorized transactions on the page, Inferno Drainer automatically initiated malicious transactions, transferring NFTs and cryptocurrencies from the users' wallets to addresses controlled by the hackers. This attack resulted in dozens of users losing their valuable NFTs and a large amount of Ethereum, with total losses amounting to millions of dollars.
- Uniswap Phishing Attack
Uniswap is one of the most popular decentralized exchanges in the decentralized finance (DeFi) space. Inferno Drainer was used in a phishing attack disguised as Uniswap. The attackers created a fake Uniswap website and directed users to visit it through Google ads, social media links, and other means. After authorizing the malicious contract on the website, Inferno Drainer quickly scanned their accounts and initiated a token transfer transaction to steal the users' assets. Multiple users lost a large amount of tokens and stablecoins in this attack, with total values ranging from hundreds of thousands to millions of dollars.
Similar Attack Methods Used by Hacker Groups
- Phishing Attacks
Hackers impersonate trusted organizations or individuals to deceive victims into clicking on malicious links or disclosing private keys, thereby gaining access to their cryptocurrency assets. For example, the Lazarus Group has previously launched precise phishing attacks by impersonating government officials, successfully stealing large amounts of funds from cryptocurrency exchanges.
- Malware
Hackers use malware to infect victims' devices, thereby stealing their cryptocurrency or gaining remote control of the devices. FIN6 often uses custom malware specifically targeting financial institutions and cryptocurrency exchanges.
- Exploitation of Smart Contract Vulnerabilities
Hackers identify and exploit vulnerabilities in smart contracts to illegally transfer or steal funds. Because smart contracts, once deployed on the blockchain, cannot be changed, the impact of vulnerabilities can be extremely severe.
- 51% Attacks
Hackers gain control of over 50% of the computing power in a blockchain network to carry out double-spending attacks or tamper with transaction records. Such attacks are particularly targeted at small or emerging blockchain networks, as their computing power is relatively concentrated and susceptible to malicious manipulation.
Preventive Measures for Individual Clients
- Strengthen Security Awareness
Always remain vigilant and avoid clicking on unfamiliar links or downloading software from unknown sources. Especially when it comes to cryptocurrency operations, extra caution is necessary to avoid falling into traps.
- Enable Two-Factor Authentication
Enable two-factor authentication (2FA) for all cryptocurrency accounts to add an additional layer of security and prevent unauthorized logins.
- Use Hardware Wallets
Store the majority of cryptocurrency in hardware wallets rather than online wallets or exchanges. This offline storage method effectively reduces the risk of remote hacking.
- Review Smart Contracts
Before interacting with smart contracts, try to understand the contract code or choose contracts that have been professionally audited to avoid interacting with unverified smart contracts and reduce the risk of fund theft.
- Regularly Update Devices and Software
Ensure that all devices and related software are up to date with the latest versions, and regularly perform security updates to prevent attacks due to old vulnerabilities.
Conclusion
In the blockchain field, security is always a crucial issue. Understanding and identifying well-known hacker groups, tools, and their modus operandi, combined with effective personal preventive measures, can greatly reduce the risk of becoming a target of attacks. As technology continues to evolve, hacker tactics are also advancing. The Chain Source security team recommends that users continuously enhance their security awareness and remain vigilant in order to stand undefeated in this rapidly changing digital era.
Chain Source Technology is a company specializing in blockchain security. Our core work includes blockchain security research, on-chain data analysis, and asset and contract vulnerability rescue. We have successfully recovered stolen digital assets for individuals and institutions. At the same time, we are committed to providing project security analysis reports, on-chain tracing, and technical consulting/support services for industry institutions.
Thank you for reading, and we will continue to focus on and share blockchain security content.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



