This article Hash (SHA1): b366289db9b21c3e9b6668c274e4a179be57a463
Number: Chain Source Security Knowledge No.008
In the past few years, the blockchain economy has experienced exponential growth, especially in 2022 when the locked value of the DeFi ecosystem reached a peak of $300 billion. Web3 has now seen a variety of attack methods and logical security vulnerabilities. Since 2017, Maximum Extractable Value (MEV) has consistently ranked at the forefront of attack methods causing losses on the Ethereum chain. The Chain Source Security team has conducted an analysis and summary of the basic principles and protection methods of MEV, hoping to help readers enhance their ability to protect their assets.
Basic Principles of MEV
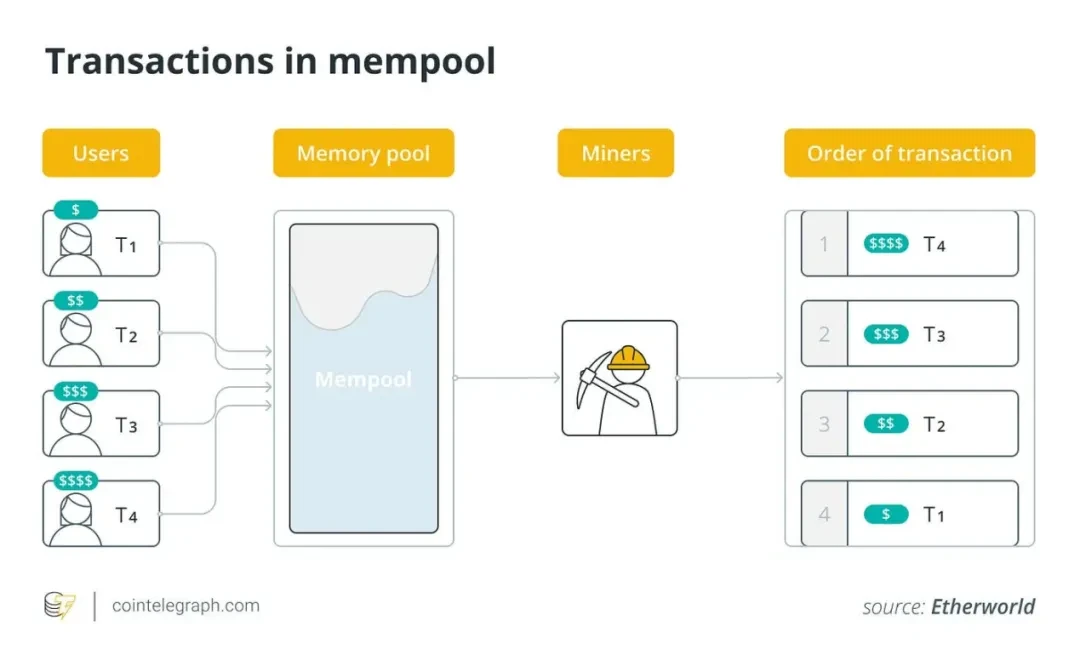
MEV, short for Maximum Extractable Value, was previously known as Miner Extractable Value during the POW era of Ethereum and was renamed to Maximum Extractable Value after many blockchains transitioned to POS, as block producers are no longer the sole decision-makers for transaction ordering (currently, miners and validators have these permissions, whereas previously only miners did).
MEV refers to the profit obtained by participants such as validators or sorters through selective operations on transactions within the blocks they produce (including including transactions, excluding transactions, and reordering transactions).
- Validators: Participants responsible for validating transactions and producing blocks;
- Sorters: Participants responsible for determining the order of transactions;
- Including transactions: Selecting which transactions will be included in the block;
- Excluding transactions: Selecting which transactions will not be included in the block;
- Reordering transactions: Deciding the order of transactions in the block;
The hackers currently using MEV mainly target wallet addresses that have qualified for airdrop snapshots and are about to unlock staked tokens. The premise for these attacks is to obtain the wallet's private key, then initiate dynamic Gas monitoring, and wait for the user's tokens or gas fees to arrive. Afterward, they send a transaction to extract funds in the same block or adjacent blocks, known as front-running transactions. These monitoring robots are referred to as Sweeper robots.
Protection Methods (Using ETH as an Example)
Firstly, there are two approaches to protection. Since it involves competing with hackers in front-running speed, the first approach is to increase Gas price and transaction ordering Nonce.
Because the transaction fee on Ethereum = Gas (quantity) * Gas Price (unit price), and the Gas Limit capacity of each Ethereum block is fixed, the higher the Gas Price, the higher the priority for the transaction to be included in the block confirmation. Additionally, the nonce in Ethereum represents the number of transactions. This concept, combined with Ethereum's account-based nature, means that each different account maintains its own nonce, and each transaction from each account in Ethereum has a unique nonce. This prevents replay attacks (the same transaction being processed multiple times) and allows the EVM virtual machine to clearly determine the order of transactions (e.g., if a transaction's nonce is 5, transactions with a nonce of 4 in the account must have been processed before this transaction).
The second approach is to connect to nodes with faster confirmation speeds and higher transaction obfuscation.
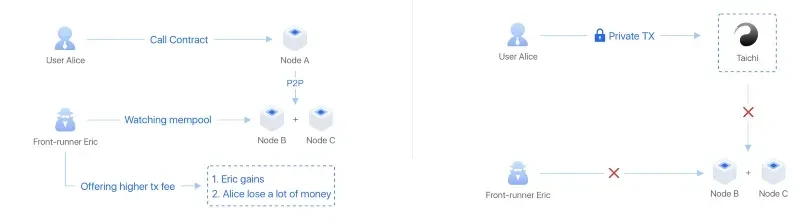
When it comes to changing connection nodes, the first recommendation is the TAICHI network, which is a privacy and security solution based on blockchains such as ETH and Solana. It achieves transaction obfuscation and privacy protection by introducing a series of relay nodes. These nodes receive user transaction requests, mix them with other transactions, and hide the source and destination of the transactions.
- Relay nodes: These nodes are the core of the TAICHI network, responsible for receiving, mixing, and forwarding transactions;
- Transaction obfuscation: By mixing multiple transactions together, relay nodes can effectively hide the source and destination of individual transactions;
- Privacy protection: This method effectively prevents on-chain data analysis and tracking, protecting user privacy;
The way Sweeper works is by monitoring the public memory pool of transaction records to achieve front-running transactions. However, TAICHI nodes allow us to submit signed transactions directly to miners without the need to broadcast them through the public memory pool, which means that Sweeper is highly likely to be unmonitored, allowing for the possibility of front-running Sweeper (the public memory pool refers to the collection of transactions that have been broadcast but have not yet been included in a block).
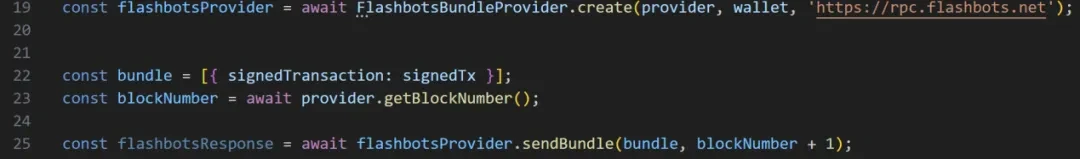
The second recommended node is FlashProtect, which is a solution to the MEV problem in the Ethereum system provided by FlashBots. Its working principle is to package user transactions and send them directly to miners through Flashbots, rather than through the public memory pool, to prevent malicious miners and robots from discovering and exploiting these transactions in the public memory pool to extract funds using MEV. Its drawback is that the transaction speed is very slow because it uses the Flashbots memory pool, which has far fewer validators than the public memory pool.
Conclusion
In general, various protection methods are also aimed at maintaining the decentralized transaction ordering process and ensuring that smart contracts process transactions fairly. However, the fundamental solution must come from adjustments made from the perspective of miners and validators.
Chain Source Technology is a company focused on blockchain security. Our core work includes blockchain security research, on-chain data analysis, and asset and contract vulnerability rescue. We have successfully recovered multiple cases of stolen digital assets for individuals and institutions. At the same time, we are committed to providing project security analysis reports, on-chain tracing, and technical consulting/support services for industry institutions.
Thank you for reading, and we will continue to focus on and share blockchain security content.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



