Recently, the Connext witch hunting program has caused dissatisfaction and heated discussions in the community. Some community members have threatened to poison Connext witch addresses, especially the top 10% of addresses in transaction volume on zkSync. Although most of it is just talk, some users have reported being poisoned in reality. Trusta Labs, through on-chain data analysis and security platform discussions, has analyzed two main strategies of witch poisoning attacks: forced clustering and label propagation, and has provided a detailed analysis of a real Connext witch poisoning case that occurred on Polygon.
This type of poisoning behavior may result in many innocent addresses being wrongly labeled as witches, which can harm users and the entire community, as well as affect the trust between the community and the project team. Therefore, Trusta Labs has initiated the "Proof of Innocence Program" (PoIP) to unite the community and project teams to combat poisoning and allow poisoned addresses to prove their innocence. In the PoIP plan, users submit relevant information for Trusta to verify through manual and AI analysis, and users receive feedback within 1 day. This data will be shared with project teams and anti-witch teams to prevent misidentification of witches and better protect users.
Connext Witch Hunting Program and Witch Poisoning
Connext is an L2 open protocol that allows developers to build applications that can use any token on any chain. Last week, Connext updated its airdrop rules and announced the witch hunter program, which has caused dissatisfaction and heated discussions in the community. Some community members have threatened to poison Connext witch addresses, especially the top 10% of addresses in transaction volume on zkSync. Let's first outline the schedule of the Connext airdrop:
- On August 18, Connext announced a cross-chain airdrop for its xERC20 $NEXT token.
- On August 24, Connext introduced the community reporting witch program similar to HOP and SAFE.
- From August 24 to September 1, community members identified and reported witch attackers, submitting reports on Github.
- As of September 1, the community reporting witch program collected about 600 reports from 62,070 candidate addresses, involving approximately 20,000 addresses (35%) (https://github.com/connext/community-sybil-reports/issues).
Although the intention of selecting and rewarding valuable real users is good, we have seen a lot of controversy within the community regarding the witch reporting program. "Poisoning" has become a hot topic, with some reported witch address users threatening to poison other wallet addresses. Their goal is to disrupt the entire witch reporting work and airdrop plan. Some KOLs have also demonstrated short videos of using bots to poison, but it was later proven to be just mockery. Although most of these poisonings are just talk, some users have reported being poisoned in reality.
Discussion of Witch Poisoning Strategies
Based on on-chain data analysis and security risk control experience, Trusta Labs has analyzed and discussed two main methods and strategies of witch poisoning attacks: forced clustering and label propagation, and has discovered a real poisoning case.
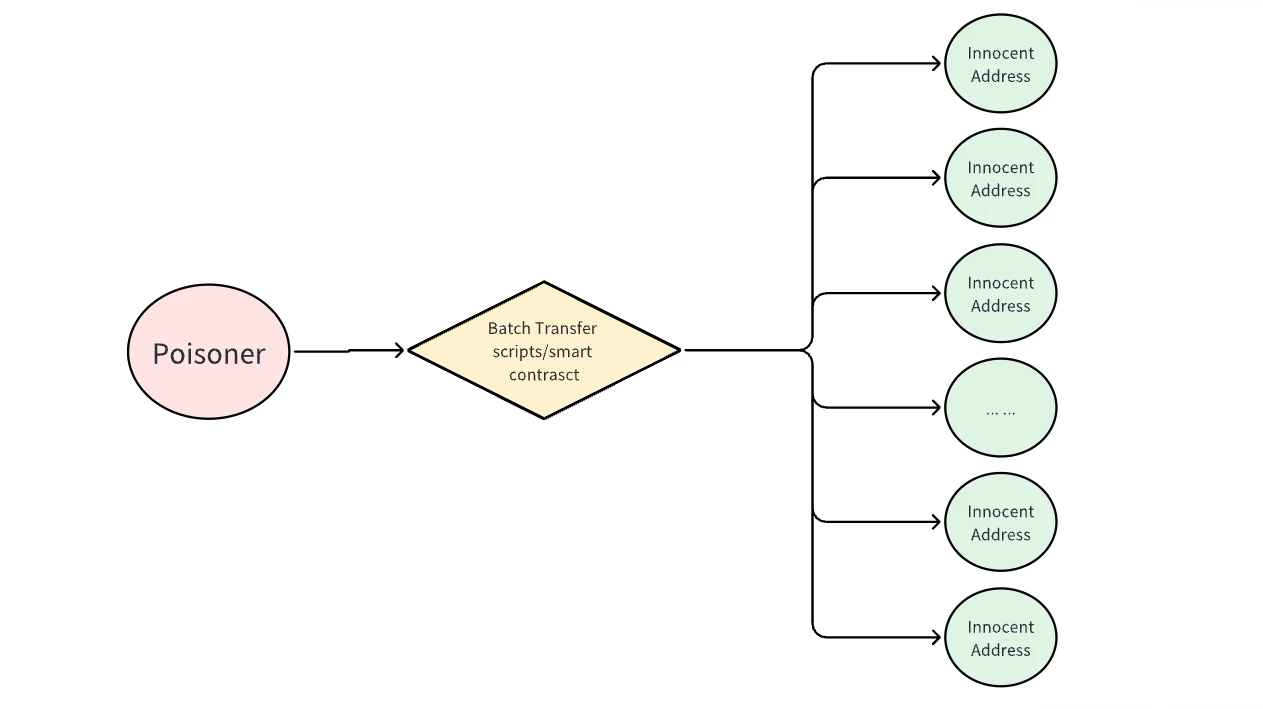
Poisoning Method I (Forced Association/Clustering): Poisoners use batch operation scripts or tools like disperse.app to perform batch token transfers. They make many small transfers to a group of innocent addresses in a very short period of time. All forged transfers send the same token in extremely small amounts.
Through the poisoner's large token transfers, all unrelated addresses are forcibly associated, forming a cluster. Due to the batch transfer relationship of the poisoning addresses and belonging to a cluster, some witch identification algorithms may label all addresses in the cluster as witch addresses. This forced clustering is entirely based on the batch transfer relationship with the poisoning addresses, even though these addresses are actually unrelated.
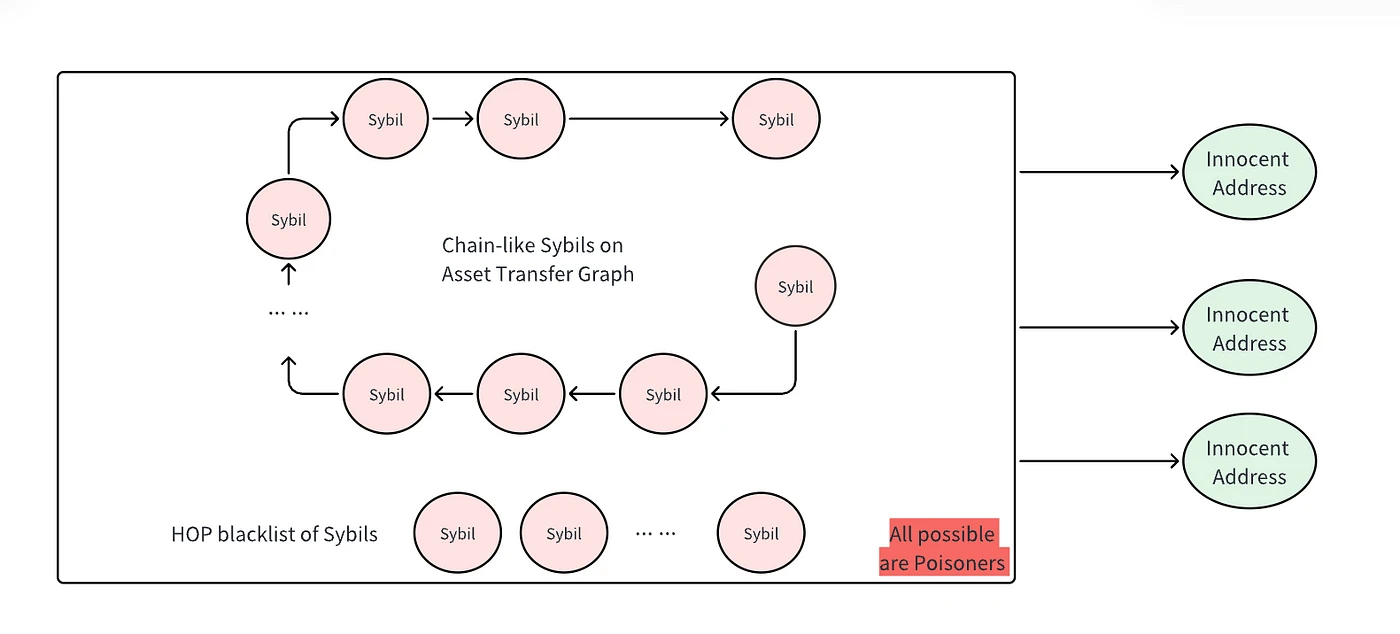
Poisoning Method II (Witch Label Propagation): Label propagation is a graph mining algorithm based on the rule that closely connected nodes in a graph often have the same label. In the graph, addresses in boxes have already been labeled as witch addresses due to their chain-like fund transfer relationships. Attackers can use these witch addresses as "poisoners" to intentionally transfer funds to innocent addresses, creating an extended chain-like structure, thereby propagating the witch label to other innocent addresses.
Witch label propagation relies on existing witch addresses to propagate their labels to other addresses through fund transfer relationships. This requires the poisoner to already have been labeled as a witch. In contrast, forced association does not require pre-existing witch addresses. Any address can be used as a poisoner to artificially create a batch behavior pattern of false witch addresses. This makes it easier to execute and has lower costs.
During the process of analyzing on-chain data, Trusta Labs discovered a real Connext witch poisoning case on Polygon and explained the poisoning methods through a detailed analysis of this case.
Real Connext Witch Poisoning Case
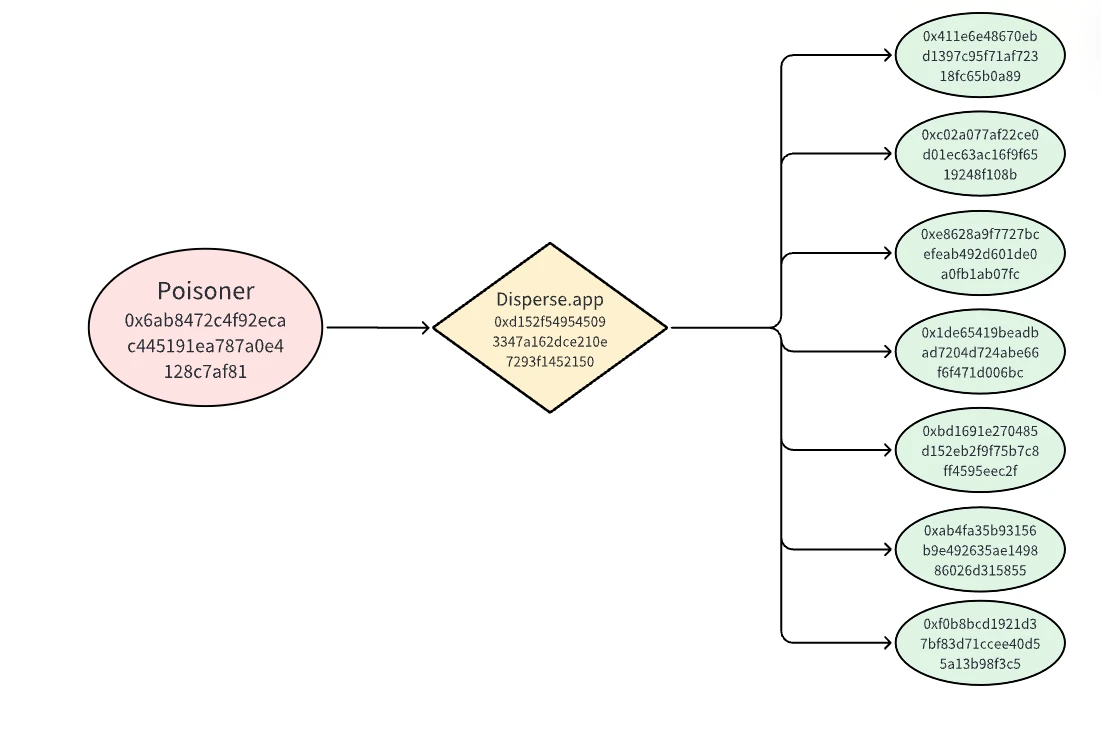
As shown in the image, the poisoning address 0x6ab used disperse.app to perform batch transfers to seven innocent addresses. We have analyzed this Connext witch poisoning case in detail based on the following evidence:
Polygon Scan shows the poisoning address's transaction records. After depositing 1 Matic from OKX, the poisoner's only action was to perform batch transfers to these 7 addresses (https://polygonscan.com/address/0x6ab8472c4f92ecac445191ea787a0e4128c7af81).
The poisoning transfers occurred during the period from 2023-08-25 05:49:40 to 2023-08-25 05:52:12, which was during the Connext community witch reporting program.
The poisoner performed 7 rounds of transfers, sending 0.0001 MATIC to each address in each round. Since the poisoner could perform multiple transfers to the same address in a round, a total of 180 transfers were made in all 7 rounds. The complete list of the 180 poisoning transfers can be found at the following Google Docs link (https://docs.google.com/spreadsheets/d/1dR9wVZN1o0_vBixKrxg6JSycHj7ADQlo/edit?usp=sharing&ouid=117000940990722879540&rtpof=true&sd=true).
All 7 addresses are candidate addresses for the Connext airdrop. Witch report #589 (https://github.com/connext/community-sybil-reports/issues/589) used these transfers as evidence to accuse these seven addresses of being a witch clustering group.
No direct transfers were detected between these 7 addresses. Apart from direct transfers from the poisoning address, there were no other transactions between them.
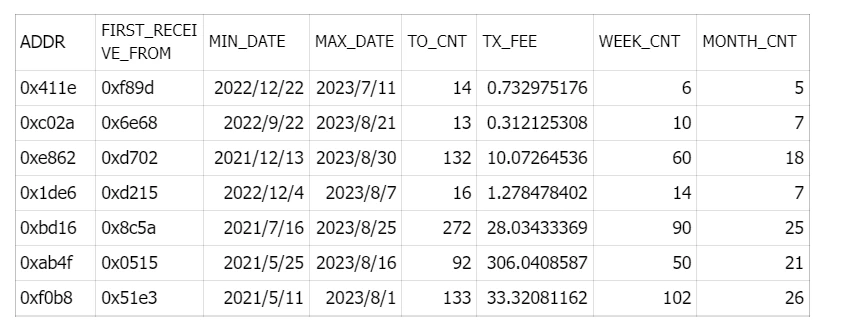
We analyzed the Polygon activity statistics of these addresses. As shown in the table, these 7 addresses are completely different in terms of initial fund sources, first and last transaction dates, number of interacting contracts, transaction fees, and active weeks/months. This extreme difference indicates that they cannot belong to a witch group controlled by a single person.
Through analysis, we have concluded that this is a real poisoning case related to the Connext airdrop, using the forced association/clustering poisoning strategy.
Trusta Launches "Proof of Innocence" Program (PoIP)
Through on-chain analysis, Trusta has found that due to witch poisoning attacks, many unrelated addresses have been wrongly labeled as witches. This has not only occurred in the Connext airdrop, but also in various indiscriminate attacks on innocent wallets. These poisoning attacks have harmed users and the entire community, as well as affected the trust between the community and project teams.
Trusta has been committed to building more trust in the Web3 and crypto world. In order to better protect innocent addresses from witch poisoning and unite to combat poisoning attacks, Trusta has launched the "Proof of Innocence" program (PoIP). This program allows poisoned innocent addresses to prove their innocence. If your address has been poisoned, you can choose:
Visit the PoIP entrance (link below) and provide details of the poisoning, such as your wallet address, the poisoned address, transaction hash, and the blockchain it belongs to. (https://docs.google.com/forms/d/e/1FAIpQLSe1dl6ocyhnDWUtm9BBvmWDGLrDjhc9NNpfHXff2XhXL5eg/viewform)
Trusta will use a combination of manual and AI analysis algorithms to determine whether it was a poisoning attack.
You will receive the determination results via email within one day.
This data will collectively form a database to prove that your address is unrelated to the poisoned address!
Trusta has launched the real user identification service TrustScan, used by several leading communities such as Gitcoin Passport, and the on-chain value rating product TrustGo (https://www.trustalabs.ai/). These services will continuously improve the accuracy of user identification results by combining this data. Trusta will also provide this data to all project teams and anti-witch teams to prevent innocent addresses from being mistakenly identified as witch addresses due to poisoning attacks.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



