Written by: Sanqing, Foresight News
Do you think you have escaped the zeroing of your assets and dodged the exchange's flash crash, making your assets safe? The answer may be far more brutal than you imagine.
Looking back from the end of 2025, if we only consider the candlestick charts, this year's story seems to be the familiar cycle of bull and bear markets, with fluctuations. However, behind the price curves lies another more thrilling trajectory. This year, hackers' hunting became more precise and deadly. According to incomplete statistics from SlowMist's blockchain hacking archive and other online sources, as of December 15, there were 189 on-chain and crypto-related security incidents throughout the year, with total losses reaching approximately $2.689 billion.
Data Overview
In terms of timing, most of this year's deadly "bombshells" were detonated in the first quarter, while the following three quarters faced continuous harassment from medium and small security incidents.
In Q1, there were 68 incidents, disclosing losses of approximately $1.658 billion, making it the quarter with the highest number and amount for the year, including billion-dollar incidents like Bybit, which made this period's record far exceed other quarters.
Q2 recorded 52 incidents with losses of about $465 million; Q3 had 38 incidents with losses of approximately $328 million; and Q4, as of December 15, recorded 31 incidents with losses of about $238 million.
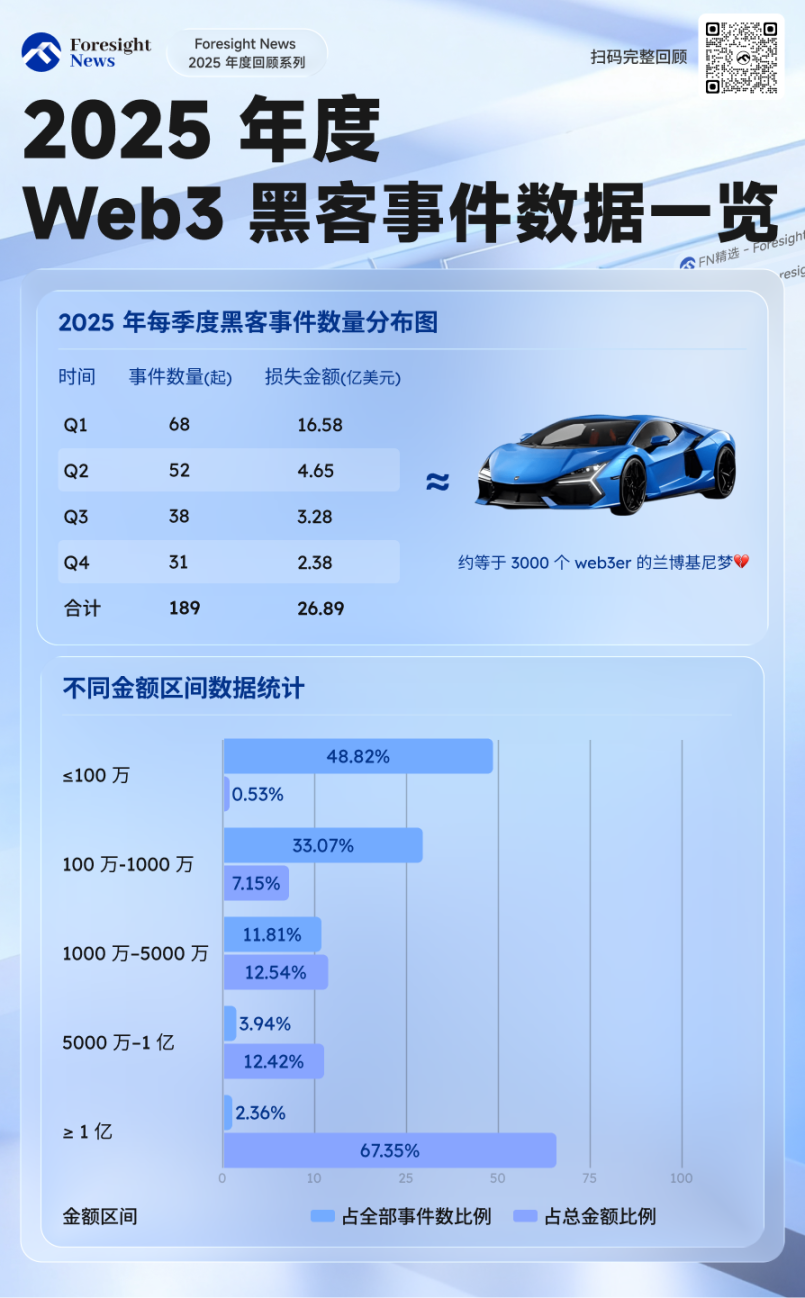
In terms of amounts, among the 127 disclosed loss incidents, about half (62 incidents) had a case value of less than $1 million. These "small cases," which occupy a significant portion, collectively resulted in losses of about $14.37 million, accounting for a negligible proportion (0.53%) of the total annual losses. The real crisis is highly compressed at the top of the pyramid.
Including Bybit, there were 3 billion-dollar cases, which, although accounting for less than 3% of the total number, had a combined case value of approximately $1.811 billion, accounting for 67.35% of the annual total. Especially in the case of Bybit, the single incident loss reached $1.46 billion, accounting for more than half (54.29%) of the annual losses. For hackers, attacking 100 small to medium projects is far less profitable than executing a "single point explosion" on a top target.
The remaining losses from incidents in the $1 million to $10 million range totaled 42, accounting for 33.07%, with cumulative losses of about $192 million, accounting for 7.15%. There were 15 incidents in the $10 million to $50 million range, accounting for 11.81%, with losses of about $337 million, accounting for 12.54%. There were 5 incidents in the $50 million to $100 million range, accounting for 3.94%, with cumulative losses of about $334 million, accounting for 12.42%.
Top Ten Security Incidents of 2025
The author has selected the ten most devastating core cases of the year based on disclosed loss amounts. Although these ten incidents account for a very small proportion of the total number of cases, they contributed the vast majority of the stolen amounts for the year.
1. Bybit Supply Chain Attack: $1.46 Billion Phantom Signature
- Date: February 21, 2025
- Attack Method: Supply Chain Attack
This is the largest single hacker attack in Web3 history. According to on-chain detective ZachXBT and official forensic reports, this attack did not directly crack Bybit's private keys but was suspected to be a supply chain poisoning executed by the notorious North Korean hacker group Lazarus Group. The attackers infiltrated the computers of the multi-signature service provider Safe Wallet's developers through social engineering and implanted malicious code.
When the Bybit team executed routine hot and cold wallet aggregation operations, the tampered front-end UI implemented visual deception: the screen displayed a normal transfer address, but the underlying smart contract logic had been quietly replaced with a malicious backdoor. This led Bybit to unknowingly sign a transaction transferring 499,000 ETH to the hackers.
However, after the incident, Bybit quickly went live and issued a statement. To prevent the spread of the attack, Bybit immediately suspended interactions with the affected wallets while keeping the platform's withdrawal and deposit functions operational to avoid panic-induced runs, with only some withdrawals potentially delayed due to increased traffic. They confirmed that this only involved one ETH cold wallet, with other assets remaining secure, and emphasized that the platform had sufficient reserves to fully cover user losses, ensuring user funds were safe 1:1.
2. Cetus Contract Vulnerability: $260 Million DeFi Math Trap
- Date: May 22, 2025
- Attack Method: Contract Vulnerability
Cetus is an important liquidity provision protocol in the SUI public chain ecosystem. Post-incident analysis revealed that Cetus's smart contract had a mathematical library precision issue (overflow check defect) when handling specific parameters.
Hackers exploited this logical flaw by lowering the pool price, building positions in high-price areas, and then using the overflow vulnerability to inject inflated liquidity into the pool at a minimal token cost, ultimately emptying assets worth $260 million as if by magic. However, the climax of this incident was not just the attack itself but also the subsequent rescue operation. After the hackers succeeded and transferred some funds across chains, Sui verification nodes quickly identified and locked approximately $162 million in assets left on-chain by the attackers.
To reclaim this large sum, the Sui community passed a highly controversial upgrade proposal: Sui officially supported hard-coding two special transactions into the protocol upgrade to forcibly transfer assets from the hacker's address to a multi-signature wallet jointly managed by Cetus, the Sui Foundation, and a security company. The proposal was approved, and $162 million was successfully "confiscated" and used to compensate users. Coupled with the foundation's loans, Cetus ultimately achieved full compensation for the affected users. Although it was a just act to protect victims, it also broke the "immutability" of the blockchain.
3. Balancer Logic Flaw: $128 Million Rounding Error
- Date: November 3, 2025
- Attack Method: Logic Flaw
As an established DeFi protocol, Balancer was still severely impacted by a logic flaw in V2. Analysis indicated that the flaw stemmed from an extremely subtle rounding direction error when processing EXACT_OUT exchanges that included non-integer scaling factors, causing the protocol to incorrectly execute a floor rounding.
Attackers keenly captured this minute difference and repeatedly arbitraged using the batch exchange function, ultimately draining liquidity pools across multiple chains, including Ethereum, Arbitrum, and Avalanche, with total losses reaching $128 million. This attack quickly triggered a "domino effect": to prevent the flaw from affecting itself, BEX, Berachain, did not hesitate to suspend network operations through an emergency hard fork; protocols relying on Balancer liquidity, such as StakeWise and Beets, suffered severe blows.
4. Nobitex National-Level Strike: $90 Million Digital Geopolitical Conflict
- Date: June 18, 2025
- Attack Method: Unknown
When the Nobitex incident was disclosed by officials, only a rough description of the financial losses and business impact was provided. The incident occurred during a sensitive period of military conflict between Iran and Israel that lasted 12 days. The attacker, Predatory Sparrow, did not attempt to cover their tracks or launder the funds but instead transferred the money to humiliating addresses generated through brute force (the address suffix included slogans against the Iranian Revolutionary Guard Corps, IRGC).
This approach directly rendered these funds unusable and unrecoverable, effectively creating a "digital scorched earth" on-chain. The purpose was very clear: not for money, but to paralyze Iran's financial lifeline and humiliate the opponent. This attack also led to the leak of Nobitex's source code, revealing the "duality" of Iran's crypto economy: the code showed that Nobitex had a "backdoor" built in for law enforcement use, allowing monitoring of ordinary users without a search warrant; at the same time, it had designed special privacy protection logic for VIPs (usually sanctioned high-ranking officials or entities) to help them evade international sanctions and anti-money laundering scrutiny.
5. UPCX Permission Theft: $70 Million Liquidity Deadlock
- Date: April 1, 2025
- Attack Method: Private Key Leak / Malicious Contract Upgrade
This was a seemingly earth-shattering yet practically deadlocked hacker operation. On April 1, Cyvers detected anomalies in the management account of the payment public chain UPCX.
The attacker allegedly gained administrative privileges by upgrading the ProxyAdmin contract and calling the withdrawByAdmin function, withdrawing 18.4 million UPC from three management accounts, with a book value of up to $70 million. However, according to CoinGecko data, UPCX's market circulation at that time was only about 4 million tokens. This meant that the number of tokens in the hacker's hands was 4.6 times the total market circulation.
6. Phemex Hot Wallet Breach: $70 Million Multi-Chain Sweep
- Date: January 23, 2025
- Attack Method: Unknown Path Hot Wallet Private Key Leak
On January 23, the Singapore exchange Phemex suffered a large-scale cyberattack, with losses reaching $70 million. According to security agencies, the mastermind was likely the North Korean-related hacker group TraderTraitor. The attackers demonstrated high professionalism and execution: not only did they simultaneously transfer assets across multiple public chains such as ETH, Solana, and Polkadot through at least 8 addresses, but they also executed their operations with great precision.
The attackers prioritized converting freezeable assets like USDC and USDT into ETH, then bundled even small tokens worth only a few hundred dollars. After the incident, Phemex relied on its approximately $1.8 billion reserve to initiate compensation and restore services, temporarily stabilizing platform operations.
7. BtcTurk Hot Wallet Breach: $54 Million Second Setback
- Date: August 14, 2025
- Attack Method: Hot Wallet Private Key Leak
For Turkey's largest crypto exchange BtcTurk, this incident was a déjà vu nightmare. Fourteen months prior, the exchange had suffered a $55 million loss due to a hot wallet theft, leading to a complete management overhaul. However, the tragedy repeated itself as their hot wallet was breached again, allowing hackers to easily gain access to the private key permissions of seven blockchains, making off with approximately $54 million.
The most lamentable aspect of this case is not the amount, but the repetition of mistakes. The two thefts were both due to poor management of hot wallet private keys, which is the worst news for users because you never know if the platform has truly learned its lesson or is merely waiting for the next theft.
8. Infini Permission Theft: $50 Million Gambler's Heist
- Date: February 24, 2025
- Attack Method: Insider Job
Initially, the team attempted to negotiate with the hacker by making an on-chain announcement and offering a 20% bounty, but as the investigation deepened, a shocking truth emerged: this was not an external intrusion, but rather a case of "insider theft" by a core engineer.
According to court disclosure documents circulating online, the first defendant, Chen Shanxuan (Infini's core contract engineer), abused his position by retaining Super Admin privileges when deploying the contract, while falsely claiming to have transferred them to a multi-signature wallet. The defendant had accumulated massive debts due to a long-term addiction to high-leverage contract trading and online gambling. Before the incident, he had borrowed money from colleagues multiple times and even contacted underground money lenders.
Under the pressure of debt, he exploited his privileges to empty the treasury of $50 million. He converted USDC to DAI and then to ETH, attempting to launder the funds through mixing. This trust-based "makeshift" management once again confirms one of the values of crypto: Don't Trust, Verify!
9. CoinDCX Management Vulnerability: $44.2 Million from Side Jobs
- Date: July 19, 2025
- Attack Method: Internal Threat
India's leading exchange CoinDCX faced an absurd "insider" crisis. The hacker first conducted a tiny test transaction of 1 USDT in the early morning, then swept away assets worth $44.2 million as if a dam had burst. The police quickly identified and arrested company employee Rahul Agarwal.
The investigation revealed that Agarwal had long been violating company policy by using the company-issued laptop for "side jobs," earning about $18,000 in extra income over the past year. However, this publicly owned computer ultimately became a Trojan horse for external hackers to infiltrate the internal network. Employee endpoint security and behavioral norms are invisible defenses that exchanges must never overlook.
10. GMX Management Vulnerability: $42 Million Boomerang of Leaks
- Date: July 15, 2025
- Attack Method: Reentrancy Attack / Patch-Induced Vulnerability
The decentralized derivatives trading protocol GMX V1 encountered the classic "reentrancy attack" vulnerability in smart contracts. A reentrancy attack exploits the time difference in contract logic, forcing a "queue jump" to initiate a call again before the system completes the final accounting. In this case, the hacker attacked while the system was updating the position quantity and average price, forcing the system to incorrectly use old prices to calculate asset values.
Ironically, this fatal flaw was introduced by the GMX team themselves when they urgently patched a bug in 2022. After three years of being buried, this time bomb was finally detonated. Fortunately, the hacker ultimately agreed to negotiate a white hat agreement and returned most of the funds.
Attack Methods
If we break down the attack methods, we find that hackers' invasions of Web3 resemble a layered "three-dimensional war." Different attack techniques reflect completely different levels of technical depth and destructive boundaries.
Supply chain attacks demonstrate a terrifying upper limit of destructive power. Although this category recorded only 4 incidents throughout the year, and 3 of them had unremarkable loss scales, the Bybit case ($1.46 billion) reveals the horror of this attack method: it bypassed on-chain smart contract defenses and poisoned directly from the infrastructure or code source. Such attacks are often difficult to execute, but once successfully infiltrated into the supply chain of centralized giants, the consequences can be devastating "dimensionality reduction strikes." It may not be the most frequent threat, but it hangs over the industry like the sword of Damocles.
Contract and protocol vulnerabilities are the main battleground for hackers and project teams to confront each other directly. This is the most common cause of security incidents, with 63 incidents causing approximately $675 million in losses. This is a typical "technical game": hackers need to be proficient in code logic to find mathematical or logical flaws. Although the destructive power of a single case may not be as shocking as Bybit, due to the large amounts of funds locked in DeFi protocols, breaching even a small point can often yield millions to tens of millions of dollars in illicit gains.
In contrast, account/frontend attacks are more like low-cost peripheral harassment. This category has as many as 57 recorded incidents (including Twitter hacks, frontend injections, etc.), but recorded losses are only $17.74 million. These attacks typically use traffic hijacking, phishing links, and other means, with relatively low technical barriers. Although they create the most panic noise on social media, their actual losses often stop at "superficial injuries" since they cannot directly touch on-chain treasuries.
Additionally, the human factor cannot be overlooked. Runaways, insider malfeasance, and private key leaks have also caused significant losses. Management should always be prioritized; no matter how perfect the system is, the person holding the keys will always be the unfillable gap.
Crypto Survival Checklist
Don't be the one helping hackers achieve their KPIs; the following is a survival checklist to help you live longer in Web3.
1. Assume the official can also lie
When you see links for "official airdrops" or "emergency compensation," don't click them right away! Twitter can be hacked, Discord can be breached, and even the president can issue fake coins.
Go to the official website and cross-verify in the community. Spending an extra minute to confirm is better than spending ten years to break even.
2. For unfamiliar projects, only use a secondary account
For unknown tokens or unheard-of DApps, don't connect with your main wallet that holds large amounts! Prepare a wallet with only a few hundred USDT to test the waters.
Develop a habit of isolation; if it blows up, it will only be a secondary account, leaving your main base unharmed.
3. Avoid unlimited authorizations as much as possible; revoke permissions regularly
No protocol is worth entrusting your life savings to. Fill in the authorization limit with what you actually need, and don’t set it to unlimited just to save on gas fees.
Regularly check with Revoke.cash to cancel any authorizations that you haven’t used in a long time or that look unfamiliar.
4. Slow signing, double-check
When facing the signature box that pops up from MetaMask, don’t just click confirm. Ask yourself three questions: What is this transaction actually doing? Is the contract address correct? If I get hacked, can I bear the loss of this transaction?
If you can’t answer any of these, refuse to sign.
5. Separate your funds; trading funds are for trading, savings are for saving
Keep some funds on exchanges, some in on-chain wallets, and further diversify across different chains. Trading accounts = money for flexible use (on exchanges/hot wallets), savings accounts = money that is hardly touched (in cold wallets/multi-signatures).
Never click random links or authorize in your savings account. Diversification is not about making more money; it’s about ensuring that if one place gets hit, you still have chips to recover.
Remember, Web3 is not short of opportunities, but it lacks those who can stay at the table forever.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



