Original Title: I Studied Hundreds of Crypto Kidnappings and Robberies, Here's How to Stay Safe
Original Author: @beausecurity
Translated by: Peggy, BlockBeats
Editor’s Note: As the scale of crypto assets continues to expand, security risks are no longer limited to cyberattacks. Kidnappings, home invasions, extortion, and even violence against family members are real-world threats that are quietly approaching crypto investors. Recent cases show that criminals are targeting not only high-net-worth individuals and industry leaders but also ordinary holders.
This article systematically outlines the risk scenarios of wrench attacks based on numerous real cases and proposes protective strategies for digital and physical security. From social media privacy to home security, travel protection, and self-custody solutions, we hope to help readers build comprehensive security awareness to avoid paying a painful price due to momentary negligence.
Safety is not panic; it is preparation.
Here is the original text:
Kidnappings, home invasions, finger amputations, duct tape bindings, impersonating delivery personnel, online tracking, personal information leaks… These sound like plots from crime movies, yet they are frequently occurring in reality.
They have one thing in common: they are all methods of attack against cryptocurrency holders this year.
Just a few days ago, a thief impersonating a delivery person tricked a homeowner in San Francisco into opening the door, threatened them with a gun, and bound them, ultimately stealing $11 million worth of cryptocurrency.
This is not an isolated incident. In the past year, similar violent crimes have occurred globally, with criminals stealing hundreds of millions of dollars in digital assets from unsuspecting victims through physical attacks. It is reasonable to speculate that many cases remain unreported (to my knowledge, there have been at least three unreported incidents in the U.S. this year).
Before delving deeper, it is essential to mention @lopp's years of tracking "wrench attacks." He has compiled hundreds of known cases on GitHub, and I referenced many of these examples while writing this guide on how to avoid and respond to such attacks.

Many digital asset holders focus solely on digital security, but the risk of physical threats from the real world is on the rise.
What attacks could really happen to you?
Military strategists often focus on the "most likely course of action" and the "most dangerous course of action" of the enemy. We adopt the same approach, except here the "enemy" is anyone who might attempt to violently steal your crypto assets.
Most Likely Scenarios
"Wrench attacks" remain relatively rare in the entire cryptocurrency threat ecosystem. In contrast, you are more likely to encounter digital scams, phishing attacks, or even lose your private keys due to negligence, rather than being robbed in real life.
If you do encounter a wrench attack, it is usually because the criminals see you as an "opportunity target." In fact, many who carry out wrench attacks appear more like amateur criminals than professional thieves.
So, what might this look like?
A neighbor boasts about their crypto holdings at your barbecue, then breaks into your home looking for your seed phrase.
A stranger sees you browsing Coinbase at a café and casually steals your notebook or backpack.
In a random mugging, someone snatches your phone directly from your hand on the street.
On a night in a city hosting a crypto conference, someone threatens you with a knife or gun (you are wearing a conference lanyard and a Bitcoin T-shirt).
Most Dangerous Scenarios
An organized crime gang, equipped with skills in open-source information gathering, home invasion, crypto security, and criminal techniques, specifically targets digital asset holders, executives, and industry opinion leaders, forcing them to hand over cryptocurrency or holding them for ransom.
French police have arrested at least 24 individuals involved in violent kidnappings and extortion schemes related to cryptocurrency. Some members belong to a highly organized gang with logistics networks, enforcers, and planners.
The gang prepared vehicles, houses for holding victims, fake license plates, as well as various masks, fake guns, and geographic tracking devices (similar to Apple Airtags but more discreet), and other materials needed for kidnapping.
They disguised themselves as delivery personnel and kidnapped several well-known figures in the French crypto community, including Ledger co-founder David Balland. The gang extorted large amounts of cryptocurrency and even amputated the fingers of two victims before being arrested.
In a recent attack in San Francisco, the assailants impersonated delivery personnel, bound the victim with duct tape, and beat them while keeping the phone on speaker, repeatedly reciting the victim's personal information, which was clearly gathered in advance.
The physical harm and torture methods in these attacks raise serious concerns. While very few cases result in death, it is crucial to recognize the severity of the risks: these individuals want your money, not a murder charge.

David Balland, co-founder of Ledger, was kidnapped and extorted earlier this year.
Now that you understand the most likely and most dangerous scenarios, let’s look at how to respond.
How to Respond
Make Yourself a "Hard Target," Not a "Soft Target"
The terms "soft target" and "hard target" have become widely known due to public attention to terrorist attacks over the past few decades. Most people understand that terrorists are more likely to attack "soft targets," which are less protected and easier to hit, rather than well-guarded "hard targets."
Cryptocurrency thieves are also looking for soft targets. This is why they first target individual investors rather than robbing banks. They want to strike when you are unprepared, creating a high-pressure environment to force you or your family to hand over funds.
Your task is to make yourself a "hard target," making potential attackers feel that you are not worth the risk.
1. Social Media = Digital "Attack Intelligence Package"
A strong social media presence is a gift to attackers. Many users in the crypto community are completely open about their identities on Twitter (CT), with profiles resembling LinkedIn rather than anonymous forums. Even if you think you are not "doxxed," posts on social media are often enough for others to piece together your real identity.
Reusing old usernames on X, Discord, or Telegram can also help attackers pinpoint you. Is your Xbox gamer tag from high school really anonymous?
A backyard family selfie, a group photo from a crypto conference, or even a restaurant food photo can expose your residence or even track your movements in real-time.
Here’s an example: Bellingcat successfully located the position of an endangered animal trader through social media posts and Google Street View.
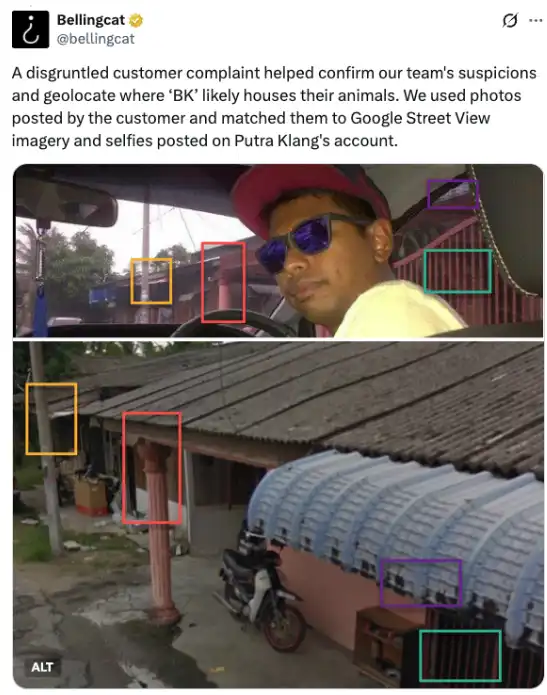
Even amateurs, as long as they can use Google Street View and popular AI tools like Grok, can likely achieve similar geographic pinpointing.
Your social media posts not only leak your location but can also make you a target for attacks. In the crypto community (CT), many people like to share profit screenshots or flaunt new watches and cars. While it is commonly believed that CEOs or influencers are wealthy (in fact, many are not), criminals will indeed look for potential victims on platforms like X.
This applies not only to physical threats in the real world but also to digital attacks. If you flaunt wealth online, you can be sure that scammers will focus their efforts on you.
I’m not saying don’t post crypto-related content or engage in the CT community, but please, don’t flaunt your wealth. There is almost no benefit to it, but it could cost you everything.
The same rules apply in real life. Some robberies and violent attacks come from people who know the victim in real life. You can introduce friends to cryptocurrency, but there’s no need to let everyone know you have money.
2. Clean Up Your "Digital Footprint"
Almost everyone with an internet or financial history has data that has been leaked, stolen, or inadvertently published online. In some countries, this data can be easily purchased; in countries with stricter data laws, leaked data can still be found on dark web markets.
I once wrote in a post about an attacker who spent about $6,000 to purchase sensitive data on the daily movements of a CEO of a European crypto company. When the potential reward is significant enough, attackers will absolutely spend money to buy your black market data.
Services like DeleteMe or Optery are a good starting point for most people. These tools will search for where your data is published online or with data brokers based on the information you provide and help remove it. You’ll need to pay $5 to $30 per month, but it’s better than having your home address appear at the top of Google search results.
For public figures and high-net-worth individuals, I will discuss this in more detail later, but due to the unique risks that come with wealth or fame, this group should consider more robust threat monitoring and security services, such as Biscayne Strategic Solutions.
Your home is your castle, and you are the king
Whether or not you keep your private keys at home (I recommend against it, and will discuss this later), attackers will assume you do. They target residences because you are home, and can be forced to transfer funds, hand over private keys, or even be kidnapped for ransom against your family.
One of the key principles of home security: never let strangers into your home unless you have actively invited them. Don’t be soft-hearted just because someone says, "Can I borrow your phone?" or "Can I use your bathroom?" The fake delivery person in San Francisco tricked their way in by claiming they "forgot to bring a pen to sign for the package."
If a stranger shows up at your door, keep the "drawbridge up"!
1. Choose Your Residence Wisely
Whether buying a house, renting an apartment, or already living in a "forever home," assess the safety of the location.
For example, an apartment building with a doorman, mandatory visitor registration, and entrance cameras is more likely to deter potential attackers than a townhouse. A secluded standalone house may be more attractive than a community with "neighborhood watch."
There is no one-size-fits-all solution, so it is essential to evaluate the risks of each type of residence and take measures to mitigate those risks.
2. Conceal Your Residence
There are various ways to make your home a "hard target." Using the data cleanup tools mentioned earlier can help you erase residence-related information online. But be aware that public records may still expose property ownership, so relying solely on these tools is not enough.
For this reason, high-net-worth individuals, public figures, and privacy-conscious individuals can further conceal property ownership by establishing anonymous legal entities (such as LLCs or property trusts). This is simpler than you might think; you can learn how to do it through a Google search, with low risk and high reward.
Finally, you can request Google to blur your house in Street View, making online reconnaissance more difficult.
3. Protect Your Residence
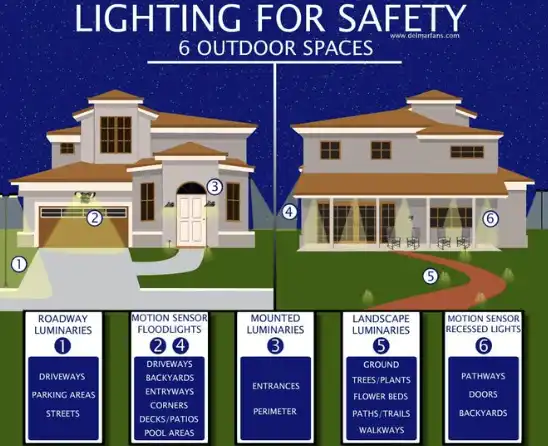
Example of security light arrangement for standalone houses
Almost anyone can make their home a less ideal target for attacks at a relatively low cost. Consider the following measures: install window privacy blackout curtains; equip with motion-sensor floodlights; install security cameras/doorbell cameras (like Ring Camera); set up an alarm system monitored by a security company on doors and windows; apply safety shatter-resistant film on windows to prevent glass from falling after breaking.
If the budget allows, consider converting a bedroom or walk-in closet into a "safe room"—treat it as the "main fortress" of your castle.
Many security companies also offer lower-cost "panic button" products that notify the company and alert the police when triggered. In some home invasions lasting several hours, such devices can be lifesaving (providing enough time for the police to arrive).
Self-Custody Solutions to Prevent Wrench Attacks
The increase in wrench attacks has led some to loudly proclaim, "Everyone should just hold Bitcoin through ETFs." This viewpoint is completely wrong. Self-custody is the best way to participate in cryptocurrency, while entrusting assets to third-party custody brings a different set of risks.
Currently, there are several self-custody solutions that specifically consider the risk of physical attacks and increase the difficulty for attackers:
Casa Vaults: A secure self-custody solution that requires multiple keys to approve transactions. Combining hardware wallets with geographically dispersed key storage enhances security.
Safe Multisig: Transactions require multiple signatures to complete.
MPC Wallet ZenGo: Offers a time-lock feature that allows users to set a fund lock time, similar to the opening hours of a bank vault.
In any case, do not rely solely on a mobile app or browser extension to store all your crypto assets. A stolen device or street robbery could instantly wipe out your entire portfolio.
1. Key Storage

2. Bank Safe Deposit Box: Affordable and Almost Universally Available
Your seed phrase is the "key to your kingdom" for your crypto wallet. If stored at home, a single home invasion could completely destroy your asset portfolio. It is advisable to keep at least part of your wallet and seed phrases in a secure location away from your residence, such as using a bank's safe deposit box system. There is no reason to keep your entire crypto asset portfolio at home—limit home assets to what is needed for active trading to avoid "putting all your eggs in one basket."
Even storing keys in a second property you own may not prevent attacks. Earlier this year, a man in Minnesota was kidnapped and forced to drive three hours to retrieve a crypto wallet from his family cabin. Using a bank safe deposit box can protect your private keys with bank-level security systems.
3. Travel Safety
When traveling, you are almost always at a disadvantage in terms of physical security because you are away from familiar surroundings and in someone else's territory. The following measures can reduce risks:
Do not post travel plans online in advance. Wait until you return home to share photos or discuss your itinerary.
Research local crime statistics and consider this information when choosing hotels and making plans. Avoid staying in areas with poor security.
If traveling for crypto work or events, be mindful of your clothing and behavior signals. Around crypto conferences, thieves and professional criminals are active. Wearing event lanyards or crypto-branded clothing can make you a target.
Do not discuss crypto topics with strangers, including hotel staff, taxi or rideshare drivers, and restaurant servers. These individuals already have insight into your lifestyle and accommodation information, and do not need more clues.
Key Principle: Stay low-key and do not send opportunity signals to attackers through social media. If they know you are not home, they may take the chance to break in.
4. High-Net-Worth Individuals and Public Figures
High-net-worth individuals (HNWIs) and public figures (CEOs, influencers, streamers) face risks far greater than ordinary crypto investors, for obvious reasons: they are more public, and attackers assume or know they are wealthy.
The risks for crypto company CEOs may even be higher than those for CEOs of large publicly traded companies because the crypto industry itself has financial attributes. Unlike large companies, crypto company CEOs often do not have a complete security team for threat analysis, and may not even have physical security provisions.
I recommend that public figures and high-net-worth individuals in the crypto space incorporate at least some security functions into their business budgets, whether in-house or outsourced. Services like Biscayne Strategic Solutions mentioned earlier not only cover privacy monitoring and data deletion but can also identify online tracking, doxxing, threats against you, and help assess security needs.
Truly well-known public figures should also consider hiring personal security during high-risk travel periods (such as crypto conferences or in cities with poor security). There are many trained former police officers, Secret Service agents, CIA, and military personnel offering security services, and if you know the right channels, quality service does not have to be expensive.
Finally, high-net-worth individuals and public figures should communicate potential "wrench attack" threats with their families and develop protection plans with their security teams. Kidnapping for ransom can target not only the primary target but also capture "soft target" family members.
Self-Defense

Mossberg 590A1 Shotgun
I strongly support self-defense. Police response is often slow, and criminals carrying out "wrench attacks" specifically choose victims they perceive as "soft targets." Being prepared for defense can serve as a deterrent and can stop an attack at a critical moment, but it is not foolproof. You cannot be as efficient as a 24/7 security team, and we all have moments of lowered vigilance.
Unfortunately, the success rate of self-defense in reality is quite low. Earlier this year, @lopp mentioned in a talk that only about 6% of known attacks were thwarted by victim self-defense.
I share this data not to discourage you but to remind you: preventive measures are more important than relying solely on self-defense in a crisis.
If You Can Legally Carry a Gun
If your area allows gun ownership and has self-defense protection laws, I encourage everyone to consider legally owning a gun and carrying it concealed. However, it must be stated: firearms (and when to use them) is a skill that needs to be learned. If you buy a gun but never train, store it improperly, or are unfamiliar with local laws, you are likely to harm others, harm yourself, or even end up in jail.
If you are willing to practice, store it properly, and learn the laws, I recommend the following types:
Shotguns (not banned in most areas): Mossberg 500, Remington 870, Mossberg 590A1
Handguns: Glock 17, Glock 19, Sig Sauer P365
If You Cannot Legally Carry a Gun
In many areas, firearms are difficult to obtain or are banned. But do not assume that attackers will not have guns (sometimes they even use fake guns to intimidate victims).
We previously mentioned that an attack in France failed due to the resistance of locals and the victim. Indicating to attackers that you will not easily yield may cause them to back off.
Some non-firearm self-defense options include:
Pepper spray/bear spray
Baseball bats/tire irons/crowbars
Knives: folding knives, hunting knives, kitchen knives
Your car (if you are carjacked, drive away directly)
What to Do If You Suspect You Are Experiencing a Wrench Attack?
Earlier this year, a video showed a group in France attempting to kidnap the daughter of a crypto executive on the street. She ultimately escaped, thanks to bystanders rushing to help.
In the video, the victim fought back desperately and made noise to attract the attention of passersby. Several men then rushed forward, grabbing anything they could use as a weapon, even including a fire extinguisher, despite the attackers appearing to be armed (possibly with a fake gun). The decisive actions of the bystanders caught the attackers off guard, forcing them to stop the assault and flee into a waiting van.

After failing to kidnap the daughter of a crypto executive in France, the kidnappers fled into a waiting van, thwarted by bystanders.
This case shows that not every attack necessarily ends in disaster, but the victim's response is often more of a "fight or flight" instinct rather than based on a well-developed response framework.
First, if you feel in danger, you should call for help immediately. Police response is indeed slow, but they do not always fail to arrive. Combining the previously mentioned home emergency button with new apps like @GlokApp can provide dual safety coverage for home and outings.
We have even seen attackers impersonate police officers, and sometimes they are real police. You can always call 911 or your local emergency hotline to verify the identity and location of the officers.
Once you confirm you are in danger, you can refer to the following response framework:
Run: Is it possible to escape the danger? In military and intelligence fields, this is referred to as "exiting X point," meaning the location of the threat. If you can get away from danger, act immediately.
Hide: Can you evade the attackers? Perhaps in a bedroom closet or safe room, or by ducking into a busy store or bar from the street. Choose a position with a higher defensive advantage—a bedroom closet with a weapon is better than a bathroom with no protection.
Fight: If there is no other choice, fight back with all your might. Use the self-defense tools discussed earlier. Remember, attackers prefer soft targets, not hard targets. Make noise and involve as many others as possible.
Ultimately, you need to decide whether to comply or fight back. Hopefully, you have adopted a robust self-custody solution to avoid the most severe losses from an attack, so that even if forced to comply, it will not be a devastating blow.
Conclusion
The threat of wrench attacks is on the rise, but they remain a minority. I believe everyone needs to be prepared to respond, but should start with digital security, then move to physical security.
When planning physical security, be sure to consider how your digital behavior intersects with the real world. Stop flaunting profits, vacations, and luxury items online; believe me, these behaviors can backfire on you.
There is no one-size-fits-all solution for crypto security, and the same goes for real-world crime. If this article has not answered your questions, please feel free to contact me. I have helped dozens of crypto executives, investors, and opinion leaders assess physical security risks.
If you found this article helpful, please share it with friends and family in the crypto community. Criminals use these methods because they are effective. The more prepared we are as a community, the lower their success rate will be, and the fewer attacks there will be.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



