原创|Odaily 星球日报(@OdailyChina)
作者|CryptoLeo(@LeoAndCrypto)

加密世界苦朝鲜黑客久矣!
近日,安全机构 Security Alliance(SEAL)发布了一篇主题为“帮助你识别真正的朝鲜开发者”的帖子,并配图了其推出的网址中的 6 张朝鲜黑客的照片。此外,Security Alliance 还公布了图片的来源网址:lazarus.group
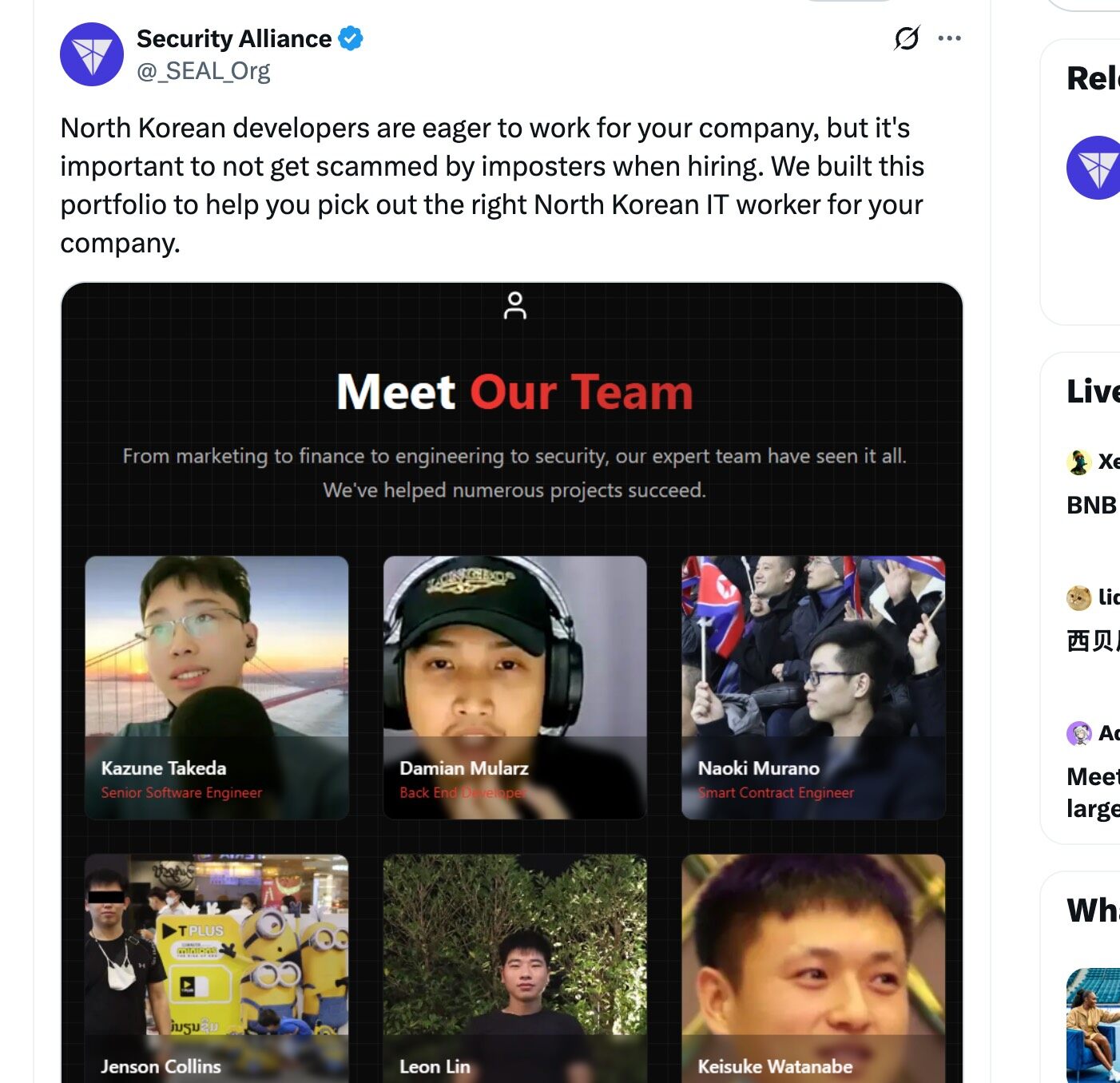
Lazarus Group 大家应该都很熟悉,臭名昭著的朝鲜黑客组织。该帖子在发布后迅速引起社交媒体热议,原因无他,朝鲜黑客正通过虚假身份伪装成互联网开发者、工程师等身份潜入项目/企业并对其进行各类攻击,从而盗取其资金,致使项目“英年早逝”。
战绩可查——朝鲜最大幕后黑手 Lazarus Group
作为朝鲜最大的黑客组织,近年来每次出现的大额黑客事件都有他们的身影,依靠各种黑客技术从各大机构/企业盗取巨量加密资产,甚至一举登上比特币持仓政府实体排行榜第三的席位,超越不丹、萨尔瓦多 2 大 BTC 钻石手,持仓数量仅次于美国和英国。
相关参考:《Lazarus Group 比特币持仓链上前三,朝鲜也来加密战略储备?》
而事实上,Lazarus Group 的盗窃活动远非加密行业,其“业务”广泛,也包括窃取银行资金、敏感数据、商业机密、军事情报和勒索赎金等。也有人表示,Lazarus Group 的操作有时并非为了钱,也会盗取的官方技术/数据等支持朝鲜科技发展,并试图制造混乱支持地缘政治目标。
对于加密世界,Lazarus Group 近四年的操作战绩如下:
2022 年:Axie Infinity 被盗超 6 亿美元加密资产
具体为:该黑客通过 LinkedIn 和 WhatsApp 联系了 Axie Infinity 开发商 Sky Mavis 的工程师,利用新工作机会引诱其参与面试。在经过多轮面试后,该工程师获得了一份薪酬极其丰厚的工作并收到了虚假 Offer,这份虚假 Offer 是以 PDF 文件的形式发送的,工程师下载了该 PDF 文件后,其内置木马渗透到 Ronin 的系统中,之后该黑客通过接管 Ronin 网络验证器而盗取资金。
2023 年:Poloniex 和 HTX 被盗超 2 亿美元
Poloniex 和 HTX 被盗原因为私钥泄露,黑客通过高级持久威胁(APT)手段长期渗透并监控 Poloniex,后获取热钱包访问权限。APT 攻击的特点包括高度隐蔽性、目标明确、持续性强和攻击手段先进。
两平台均与孙宇晨有关(可以判定当时孙哥被盯上了)。
2024 年:DMM Bitcoin(3 亿美元)和 WazirX(2.3 亿美元)被盗超 5 亿美元
2024 年 5 月份,日本加密交易所 DMM Bitcoin 检测到钱包中不当流出 4502.9 枚比特币。日本金融厅要求 DMM 调查被盗原因并给出客户赔偿方案。 后续发布官方声明称,该交易所被盗系 TraderTraitor 通过社交工程攻击,伪装成 LinkedIn 招聘人员,诱骗负责管理 DMM 交易的 Ginco Inc. 员工下载恶意程序代码,进而控制交易请求,将资金转移至黑客钱包。DMM 也承诺补偿客户,但因财务压力于 2024 年 12 月关闭,此后 DMM 将客户账户及资产将于 2025 年 3 月 8 日迁移至 SBI VC Trade。
2024 年 7 月份,印度交易平台 WazirX 遭遇黑客攻击,被盗金额约 2.3 亿美元。调查报告显示,被盗原因为 WazirX 的一个多重签名钱包遭受网络攻击,攻击者利用 Liminal 界面与实际交易数据之间的“显示不一致”(discrepancy),诱导 WazirX 的 3 名签名者和 Liminal 的 1 名签名者批准一个看似正常的交易(例如一次普通的 USDT 转账)。实际上,这个交易包含恶意负载,升级了钱包的智能合约,使其逻辑被篡改。篡改后攻击者获得完全控制权,无需 WazirX 的密钥即可转移所有资金。
2025 年:Bybit 被盗 15 亿美元
2025 年 2 月份,Bybit 被盗 15 亿美元,也是史上金额最大的加密盗窃案。具体为,具有系统发布权限的开发人员电脑设备被入侵,攻击者上传更改了 Safe 在 AWS S 3 bucket 中的一个 javascript 代码文件,该文件包含恶意逻辑,仅针对 Bybit 的以太坊 Safe 钱包以及一个未知钱包(推测是攻击者测试验证所用),从而完成对 Safe{wallet} 前端界面的入侵。随后 Bybit 在开展正常的冷热钱包代币转移过程中,所有 Safe{wallet} 用户所看到及使用的,都是被植入了恶意代码的 Safe{wallet} 前端,因此 Bybit 多签参与人看到 Safe{Wallet} 前端界面展示信息完全正常。最终黑客欺骗了多个(3 个)签名人,最终通过恶意交易获取多签钱包控制权,完成攻击。
以上均为 Lazarus Group 参与和间接参与的黑客盗取事件,金额巨大,且手法专业,很多被盗事件并非安全漏洞或人为失误,但在 Lazarus Group 的长期监控下依旧丢了资金,Lazarus Group 可以说是无孔不入。
CZ 助力警示,Lazarus Group 常见的诈骗方式
帖子发布后,CZ 也很快转发了该帖子,并列出了一些常见的朝鲜黑客诈骗方式:
1、假扮成求职者,试图在企业谋得职位。这让黑客得以近距离接触攻击目标,这些黑客尤其青睐开发、安全和财务职位;
2、假扮成雇主,试图面试/聘用你的员工。在面试过程中,他们会称 Zoom 出现问题,并向面试者发送“更新后”链接,其中包含会控制员工设备的病毒。或者他们会向员工提出一个编程问题,然后发送一些“示例代码”;
3、伪装成用户。在客户支持请求中向你发送链接,该链接指向的页面会下载某种病毒;
4、通过贿赂企业员工和外包供应商来获取数据。数月前,印度一家主要的外包服务公司遭到黑客攻击,导致一家美国主要交易所的用户数据泄露,用户资产损失超过 4 亿美元(或为 Coinbase)。
最后,CZ 呼吁企业需要培训员工不要下载未知文件,且应仔细筛查应聘者。
这些攻击不仅适用于企业,个人在遇到同类情况也需要提高警惕,比如看到陌生人的链接、共享屏幕等,尤其加密行业,很多人被攻击后的转帐时会遇到剪贴板劫持(Clipboard Hijacking)或地址替换病毒(Address Poisoning via Clipper Malware),也是我们可能遇到的最常用的攻击方式:当用户复制钱包地址(BTC、ETH、SOL 地址)时,软件会自动将其替换为攻击者控制的相似地址,这些替换地址往往开头和结尾几乎相同(例如,前 4-6 位和后 4-6 位字符一致),导致你转帐到黑客控制的地址。
此外,社交媒体上收到的陌生人链接也需要谨慎,该链接很可能包含病毒。
一份黑名单——朝鲜黑客的相关数据和应对方法
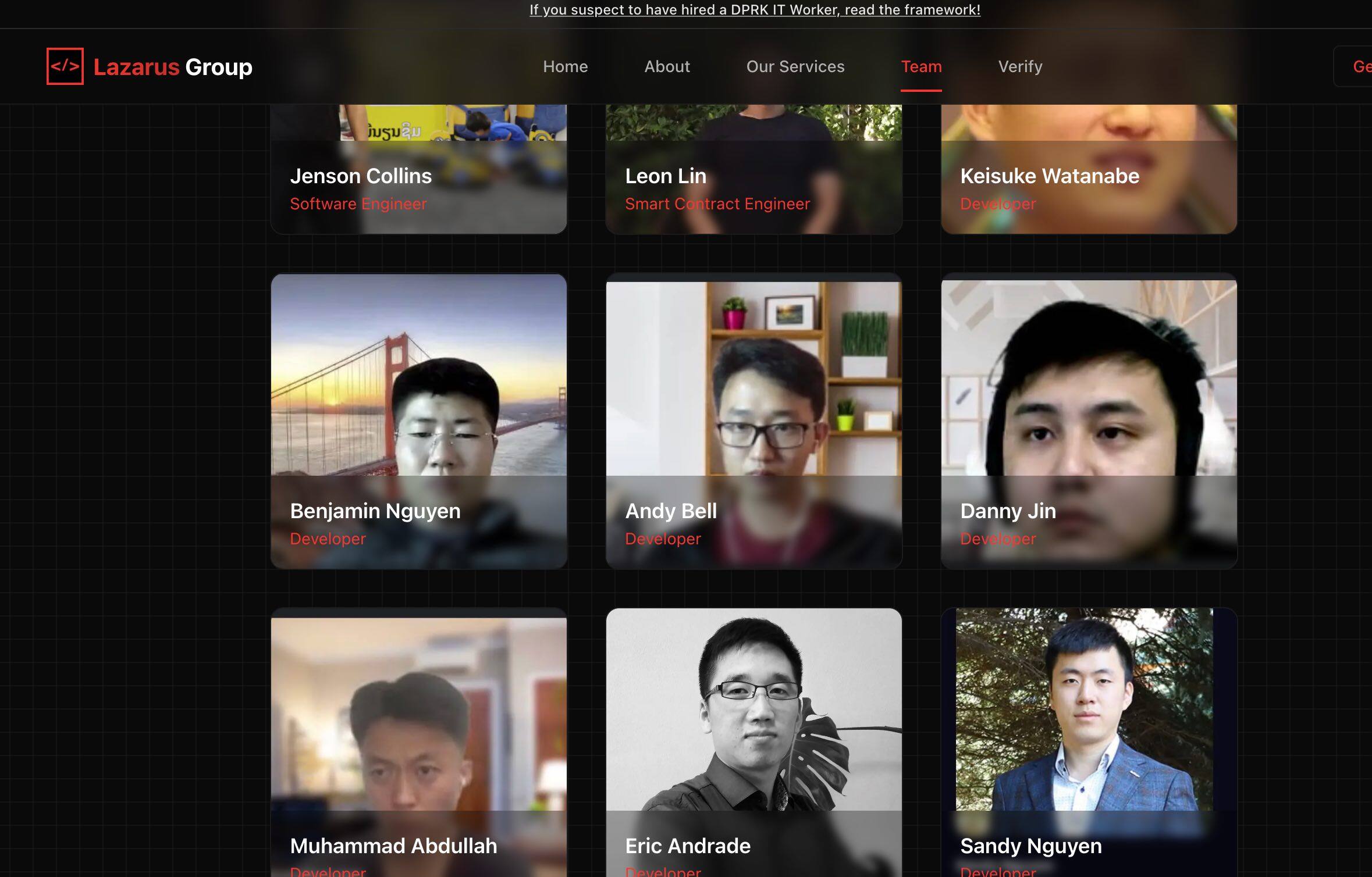
目前,lazarus.group 网站更新了 63 名黑客的名单,每个黑客的照片背景和状态都不同,这些黑客身份偏向开发者、智能合约工程师、软件工程师(针对 Web 3、区块链和后端开发),但名单上的信息并非自身真实信息,大概率是 Lazarus Group 团队黑客伪造的档案,或是 Lazarus Group 的成员或关联者,很多名单人员现仍在企业任职。
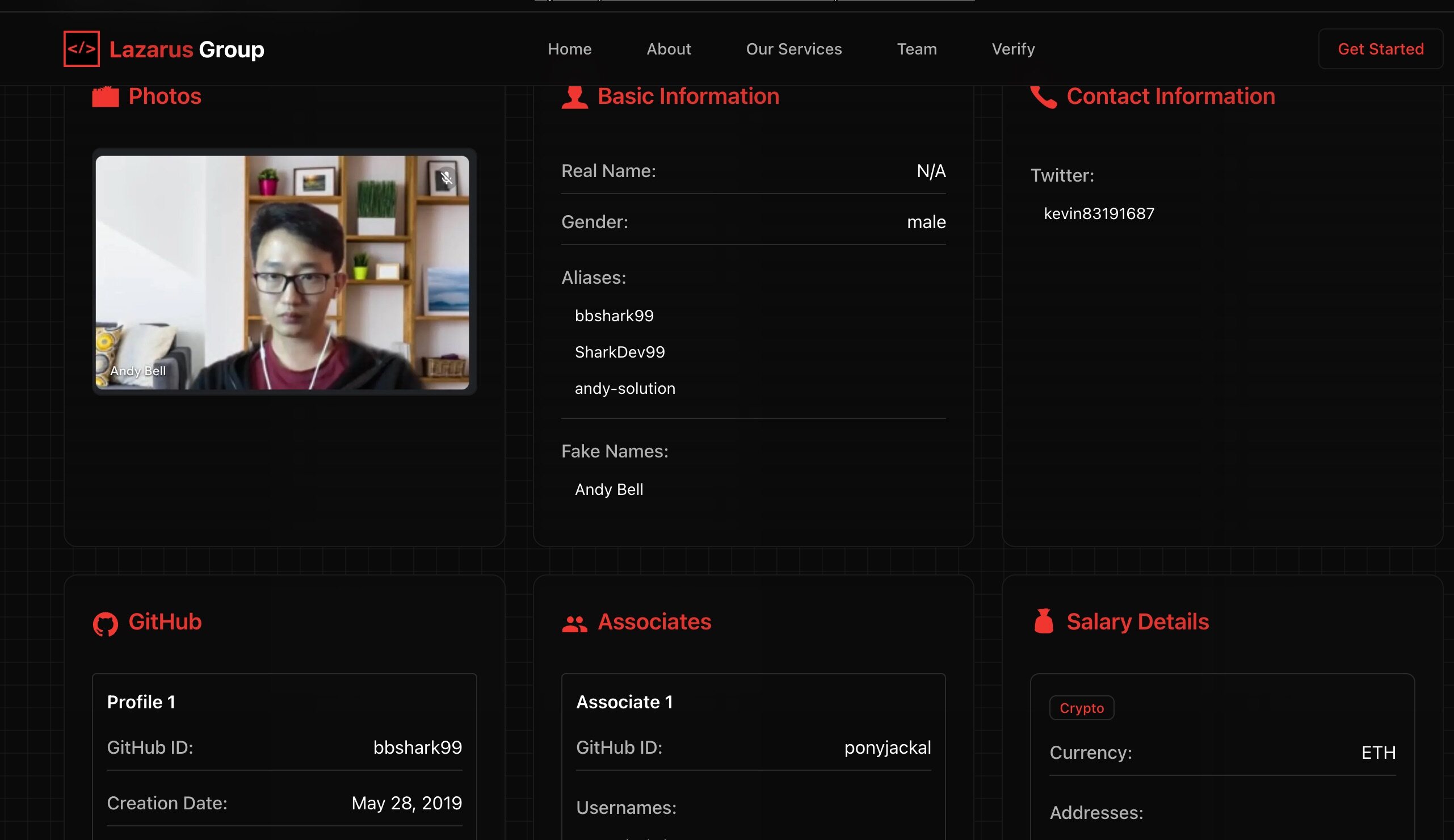
界面列出他们的曾用名、社交账号(邮件、推特、电话号等)、Github 账号、就职记录、捕捉到的图片甚至还包括加密钱包地址,还提供更详细的“简历”分析(如 LinkedIn 伪造痕迹、IP 异常等)。这些数据可以帮助 HR 和企业快速检测出面试者和员工是否存在风险。
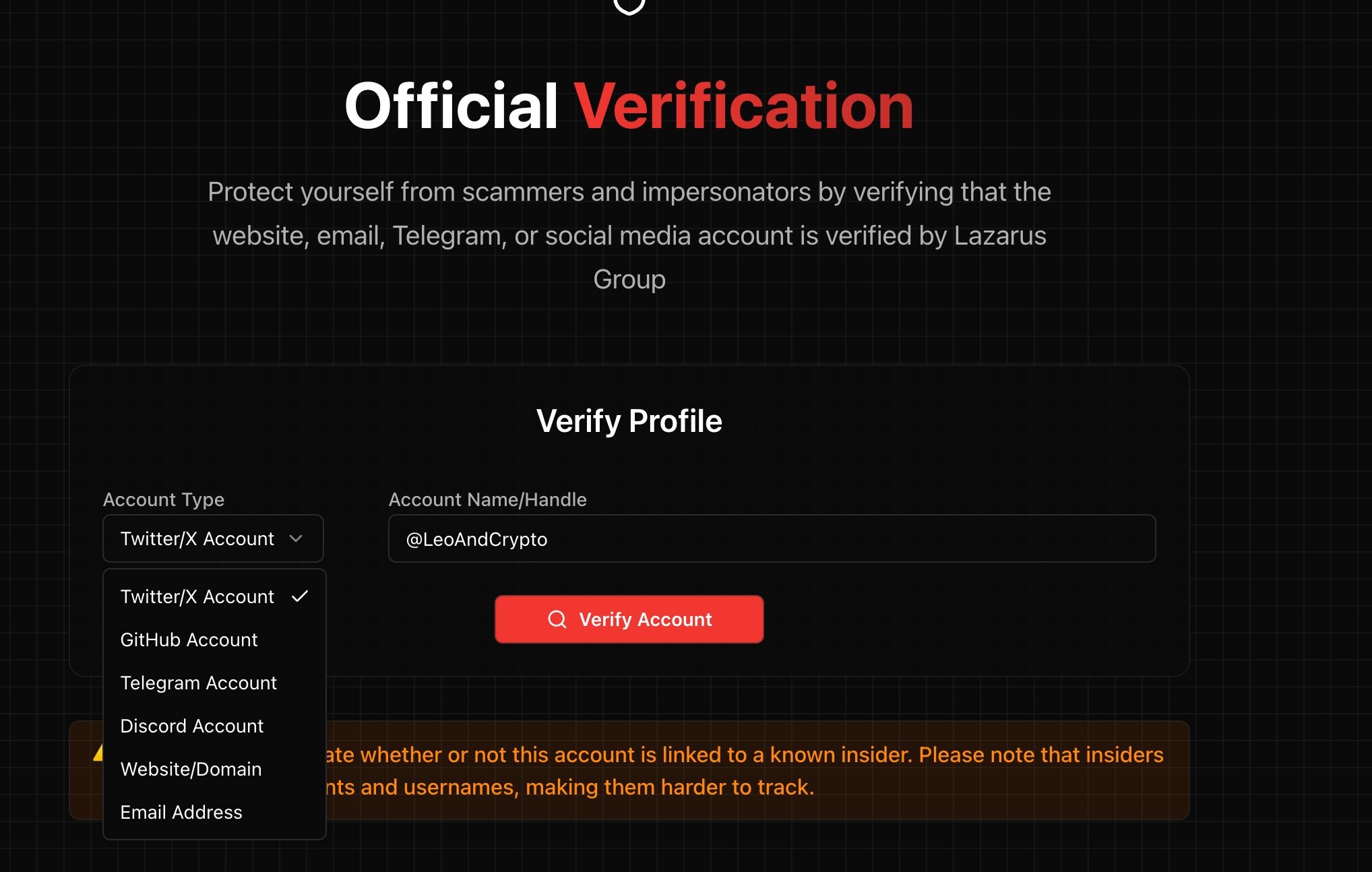
此外,该网址还推出了验证求职者账号的功能,包括 X、Github、TG、DC、网址和邮件验证(免费)。
而 SEAL 推出的 SEAL Frameworks 也可以帮助你更好地了解安全相关的知识。文件提到:
朝鲜 IT 工作者通常使用虚假身份为外国公司从事远程信息技术工作,朝鲜 IT 工作者是该国政权的重要收入来源,尤其是对其武器计划而言。他们从事各种 IT 工作(但不限于 IT),经常伪装身份和地点,以获得自由职业合同并产生收入,这些收入会汇回朝鲜。这些工作者主要驻扎在中国和俄罗斯,部分分布在亚洲、非洲和拉丁美洲的一些地区。
文件内容显示,朝鲜还运营着一个“facilitators”网络,以帮助他们掩盖身份并促使达成远程线上办公,facilitators 出借其数字和物理身份赚钱,他们的客户大多都是朝鲜黑客。
自 2010 年至今,朝鲜 IT 工作者的数量增多,地域分布更广泛,活动也更多样化,其主要目标为:
-通过远程 IT 工作为朝鲜政权创造稳定收入;
-为朝鲜的 IT 相关业务(走私和洗钱)构建支持网络;
-获取西方公司的技术、基础设施以及身份信息(包括个人和公司、数字和物理身份信息);
-泄露公司机密(有意或无意);
-敲诈勒索(勒索软件和敲诈);
-避免制裁(朝鲜实体被禁止接受来自西方国家的任何形式的付款);
-黑客攻击(建立对基础设施的永久访问权限,以便立足或渗透);
-恶意软件(感染高价值目标以备日后盗窃)。
目前,活跃在不同公司和政府机构的朝鲜黑客估计总数在 2000 至 15000 之间。但这个数字包括同一行为者重复使用的多个身份或非活跃账户。SEAL 估算所有 Web 3 开发人员中,约有 3-5%是朝鲜人,任一时刻都至少有 200-300 个与朝鲜相关的账户在积极寻求 Web 3 公司的就业机会。
SEAL Frameworks 也给出了一些建议,当企业发现员工与 Lazarus Group 有染时:
-不要立即解雇他们,在确保组织安全的同时,保持正常表现,以避免打草惊蛇。
-立即停止所有付款,如被怀疑,可以以“财务问题”等为由拖延时间。
-系统性地撤销对代码库、云基础设施和内部系统的所有访问权限。同时,收集所有可用数据(如客户身份验证文件、加密货币地址、电子邮件、简历)以供报告。
-对所有代码贡献进行全面的安全审计,密切关注依赖项、构建文件(持续集成/持续部署)以及潜在的后门。
-安全风险完全消失后,以商业相关的原因(如缩减规模、改变方向)终止他们的合同,并向执法部门报告此事。
持续更新的黑名单——短期有效还是长期利好
对于 lazarus.group 的公开名单行为:大部分人认为该名单能帮助企业更好地识别存在风险的员工或面试者,或许可以减少黑客事件发生的次数。
公开黑客相关数据在短期内或许可以起到一些作用,但长期来,由于该名单是公开可见的,黑客发现自己在上榜后很可能修改公开账号信息和个人信息,SEAL 对此的回复是很多人还是会习惯性使用某些惯用账号从而露出马脚。目前在 AI 深度伪造技术加持下,黑客或许可以更新所有的个人信息,甚至改头换面,所以名单的推出只会让黑客伪装地更加隐秘且不易察觉,毕竟加密行业很多人是线上办公的。
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



