Written by: Beosin
GMX was attacked, with the attacker exploiting a reentrancy vulnerability in the project contract, profiting approximately $42 million. The Beosin security team conducted a vulnerability analysis and fund tracking of this incident, and the results are shared as follows:
Detailed Attack Steps
The attacker first utilized the refund mechanism in the executeDecreaseOrder function of the OrderBook contract to initiate a reentrancy attack, bypassing the leverage switch of the project Timelock contract:
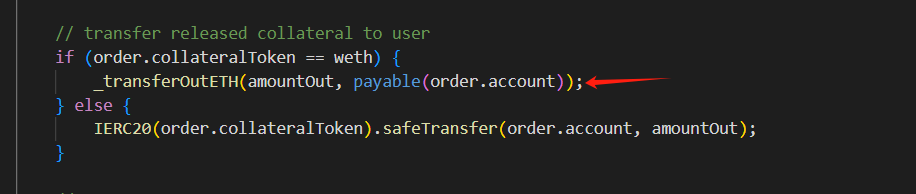
Then, the attacker borrowed USDC through a flash loan to stake and mint GLP, while increasing the short position of BTC with USDC as collateral, leading to an inflated AUM value in the GLPmanager contract, which affects the price of GLP.
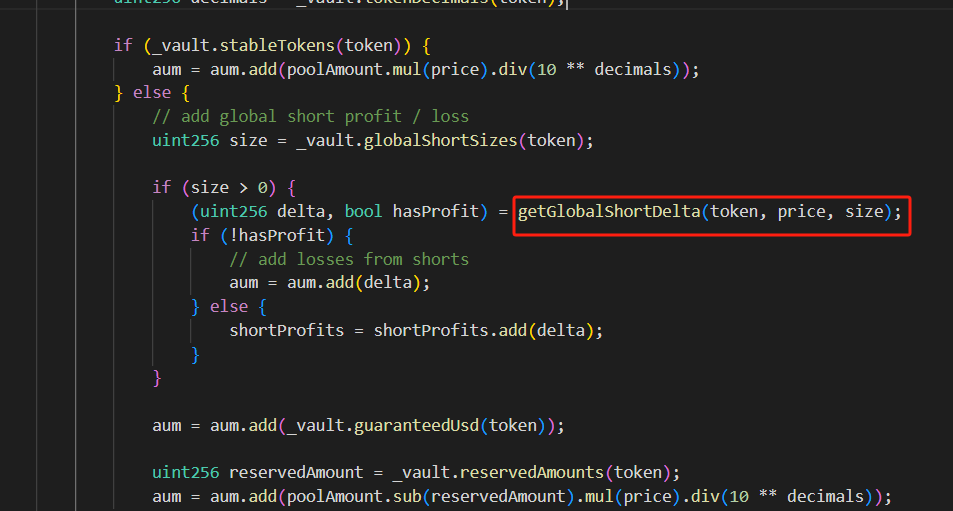
Finally, the attacker redeemed GLP at an abnormal price for profit and specified the exchange for other tokens.
Vulnerability Analysis
From the above attack process, we can see that the reasons for the exploitation of vulnerabilities in this incident are as follows:
Lack of reentrancy protection, leading to internal state modification during the redemption process.
The redemption logic is relatively complex, lacking sufficient security checks.
Although GMX has undergone multiple security audits, this reentrancy vulnerability was still overlooked. If stricter checks had been applied to the redemption logic, considering the potential for reentrancy vulnerabilities, such security incidents could have been avoided.
Tracking of Stolen Funds
Beosin Trace tracked the stolen funds and found that the attacker's address 0x7d3bd50336f64b7a473c51f54e7f0bd6771cc355 profited approximately $42 million. Subsequently, the DeFi protocol exchanged stablecoins and altcoins for ETH and USDC, transferring the stolen assets to the Ethereum network through multiple cross-chain protocols. Currently, approximately $32 million worth of ETH from the stolen assets is stored in the following four Ethereum network addresses:
0xe9ad5a0f2697a3cf75ffa7328bda93dbaef7f7e7
0x69c965e164fa60e37a851aa5cd82b13ae39c1d95
0xa33fcbe3b84fb8393690d1e994b6a6adc256d8a3
0x639cd2fc24ec06be64aaf94eb89392bea98a6605
Approximately $10 million worth of assets are stored at the address 0xdf3340a436c27655ba62f8281565c9925c3a5221 on the Arbitrum network. Beosin Trace has added the hacker-related addresses to the blacklist and will continue to track them.
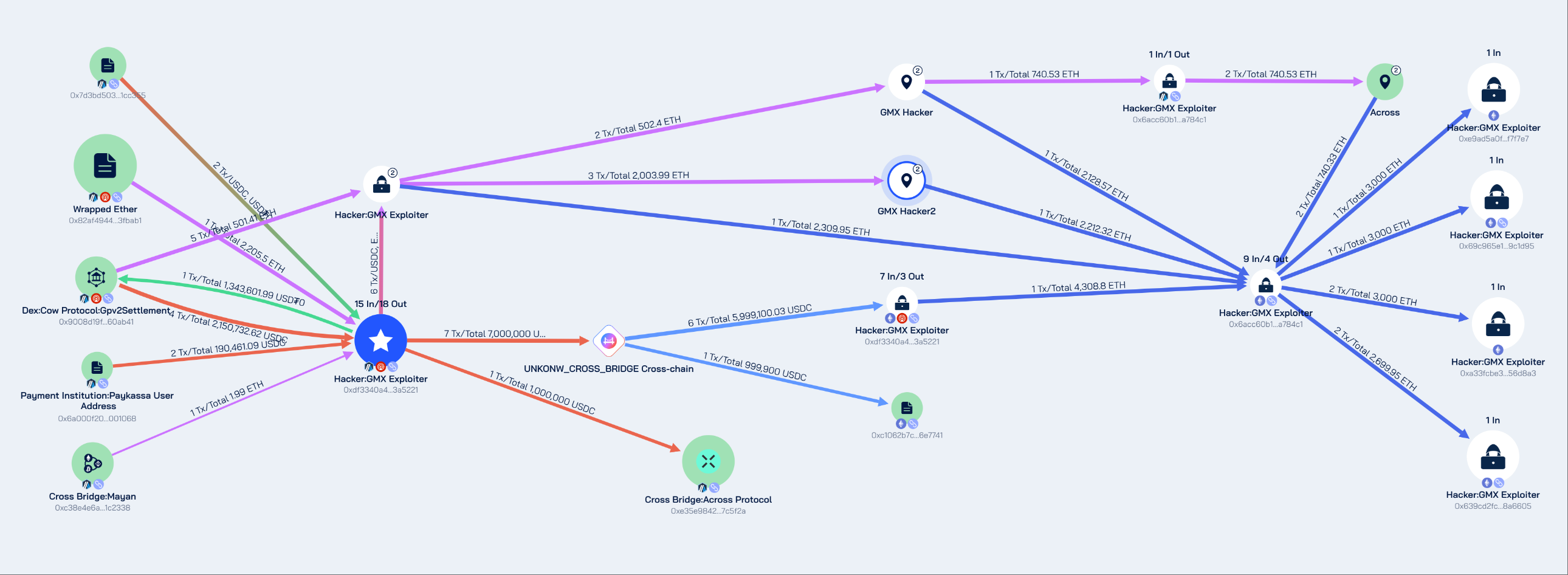
According to Beosin Trace analysis, all stolen funds are still stored in multiple addresses of the attacker.
Summary
The core of this attack lies in the reentrancy vulnerability present in the GMX contract, allowing the attacker to redeem a large amount of assets for profit through the falsely inflated AUM value. Complex DeFi protocols like GMX require comprehensive, multi-faceted security audits, with detailed testing and review of contract code. Previously, the Beosin security team has completed security audits for multiple DeFi protocols (such as Surf Protocol, SyncSwap, LeverFi, Owlto Finance), focusing on identifying logical flaws in contracts and extreme cases that may be overlooked, ensuring that DeFi protocols undergo thorough testing.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



