Attack Dissection: The "Invisible" Evolution from SparkCat to SparkKitty
On June 23, 2025, Kaspersky's threat research team first disclosed SparkKitty, describing it as a "highly covert image-stealing malware." This virus shares a common origin with the SparkCat malware discovered in early 2024, sharing similar code structures and attack methods, but with more advanced techniques. Kaspersky analysts noted that SparkKitty's earliest activities can be traced back to February 2024, initially targeting Southeast Asia and China, infiltrating user devices by masquerading as cryptocurrency, gambling, and communication applications.
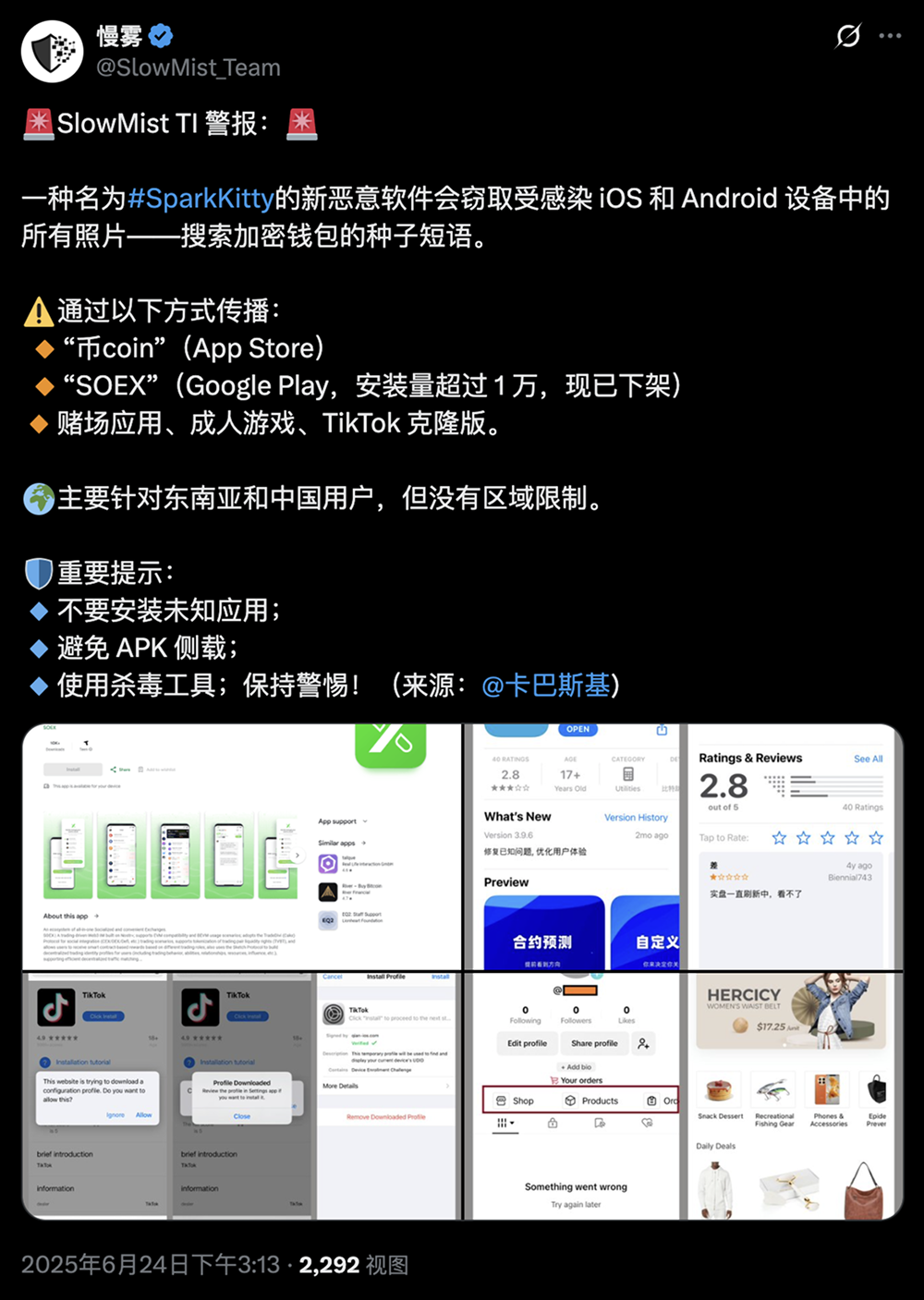
The core objective of SparkKitty is to steal all images from the photo album, with a focus on screenshots of cryptocurrency wallet seed phrases. Seed phrases are the only credentials for recovering a crypto wallet; once leaked, attackers can directly control the user's wallet and transfer all assets. Compared to SparkCat, SparkKitty's OCR (Optical Character Recognition) technology is more efficient, with some variants utilizing Google ML Kit OCR, only uploading images containing text, reducing server load and increasing theft efficiency. Additionally, the virus collects sensitive data such as device identifiers and browser cookies, increasing the risk of identity theft and account intrusion.

Breaking the Walled Garden: How Official Stores Became the Biggest Attack Vector?
What is most alarming about SparkKitty is its successful breach of what is considered the safest application distribution channels—Apple App Store and Google Play.
The review mechanisms of official app stores seem powerless in this battle. Attackers employed a "Trojan horse" strategy, disguising malicious code within seemingly harmless applications:
The Fall of the App Store: An application named "Coin" successfully launched with a simple cryptocurrency market tracking interface as a disguise. It exploited user trust in market tools to lure them into granting photo album access.
Google Play's Hotspot: A communication application named "SOEX," claiming to provide "encrypted chat and trading" features, has accumulated over 10,000 downloads. Additionally, gambling and adult gaming applications have been confirmed as significant dissemination mediums. Statistics show that since the SparkCat era, the cumulative downloads of related malicious applications on Google Play have exceeded 242,000.

In addition to official channels, attackers also supplemented their efforts with a multi-dimensional dissemination matrix:
Unofficial APK Distribution: Distributing APK installation packages disguised as cracked TikTok, popular blockchain games, or gambling applications through YouTube ads, Telegram groups, and third-party download sites.
Abuse of iOS Enterprise Certificates: Utilizing Apple's enterprise developer program to bypass the strict App Store review, directly installing applications on user devices via web links.
When these applications are installed and run, their permission requests (such as accessing the photo album) are often packaged as core functional requirements of the application, making it easy for users to inadvertently authorize, thus inviting trouble.
Thousands Victimized, Assets Reduced to Zero: A "Localized" Blitzkrieg Targeting the Asian Market
Southeast Asia and China have become the primary targets for SparkKitty. This is not a coincidence but a meticulously planned "localization" strategy:
Precise User Profiling: These regions are highly active markets for cryptocurrency and mobile gambling applications, with a large user base and relatively weak security awareness.
Cultural and Linguistic Bait: Application names (such as "Coin"), interface designs, and promotional copy all use localized languages, even embedding popular local gambling game elements, significantly lowering users' guard.

Although the attacks are concentrated in Asia, Kaspersky warns that SparkKitty is technically borderless, and its code can be easily modified to target users in any region globally. On X (formerly Twitter), security experts and crypto KOLs have launched large-scale alerts, urging users to self-check, and the panic surrounding the incident is spreading throughout the global crypto community. Its dangers are multi-layered:
Immediate Asset Evaporation: Seed phrases are the only key to recovering wallets. Once leaked, attackers can transfer all of a user's crypto assets within minutes, and recovery is nearly impossible.
Complete Privacy Exposure: The photo album may contain a vast amount of private information such as ID cards, passports, bank cards, and family photos. If exploited by malicious actors, the consequences could be dire.
Chain Account Compromise: Stolen cookies and credentials may lead to the takeover of users' social media, email, and even bank accounts.
Reflection: When Seed Phrase Screenshots Become the "Achilles' Heel"
Platforms are taking action. Google has removed related applications, and Apple has previously banned nearly a hundred developer accounts due to the SparkCat incident. However, this feels more like an endless game of "whack-a-mole." As long as attackers can continuously find loopholes in the review mechanisms, new "Trojans" will keep emerging.
The SparkKitty incident serves as a wake-up call for the entire industry, exposing several profound dilemmas:
The Trust Crisis of App Stores: Users' blind faith in the "absolute safety" of official stores has been shattered. Platforms need to introduce more proactive and intelligent dynamic behavior detection mechanisms, rather than relying solely on static code scanning.
The Eternal Conflict Between User Habits and Security: For convenience, users tend to back up their most important data—their seed phrases—using the simplest method: screenshots. This behavioral pattern is precisely the weakest link in the security system.
The "Last Mile" Dilemma of Crypto Security: No matter how secure hardware wallets are or how decentralized DeFi protocols are, as long as users make mistakes in managing seed phrases in this "last mile," all defenses will be rendered ineffective.

How to Protect Yourself? Better to Prepare Than to Regret
Eradicate Bad Habits, Physical Backup: Completely abandon the habit of storing seed phrases in photo albums, notes, or any online cloud services. Return to the most primitive and safest method: handwritten physical backups, stored in secure locations at different places.
Principle of Least Privilege: Guard your phone permissions like a miser. Any non-essential requests for photo album, contacts, or location access should be outright refused.
Establish a "Clean Room" Environment: Consider using a dedicated, network-isolated old phone to manage crypto assets, without installing any applications from unknown sources.
SparkKitty may be eradicated, but the next "Kitty" is already brewing. This attack reminds us that security in the Web3 world is not just a battle of code and protocols, but a continuous game concerning human nature, habits, and cognition. Staying vigilant in the face of absolute convenience is a necessary lesson for every digital citizen.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



