作者:Lisa & 23pds
编辑:Sherry
背景
2025 年 6 月 18 日,链上侦探 ZachXBT 披露,伊朗最大的加密交易平台 Nobitex 疑似遭遇黑客攻击,涉及多条公链的大额资产异常转移。
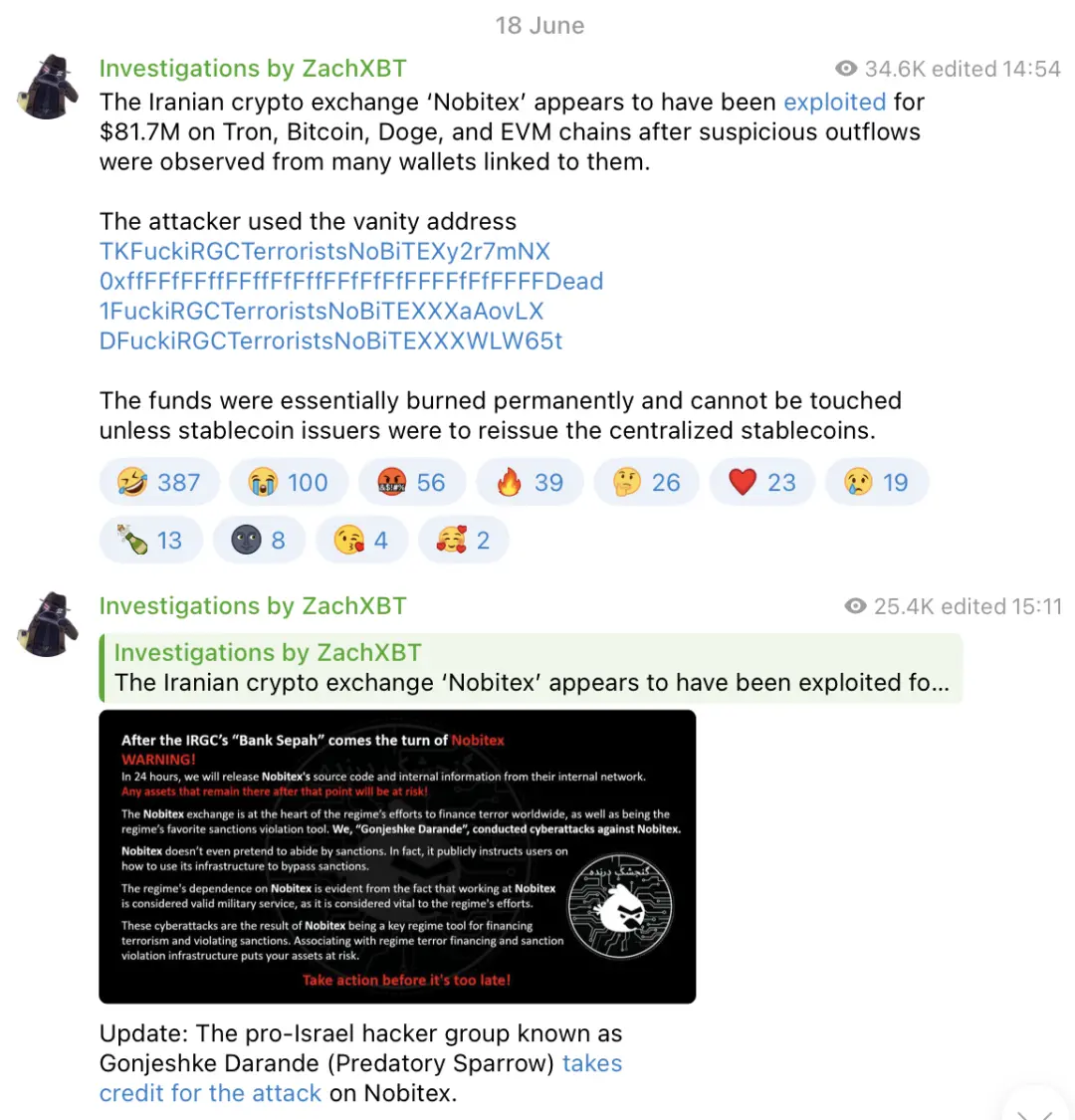
(https://t.me/investigations)
慢雾(SlowMist) 进一步确认,事件中受影响资产涵盖 TRON、EVM 及 BTC 网络,初步估算损失约为 8,170 万美元。
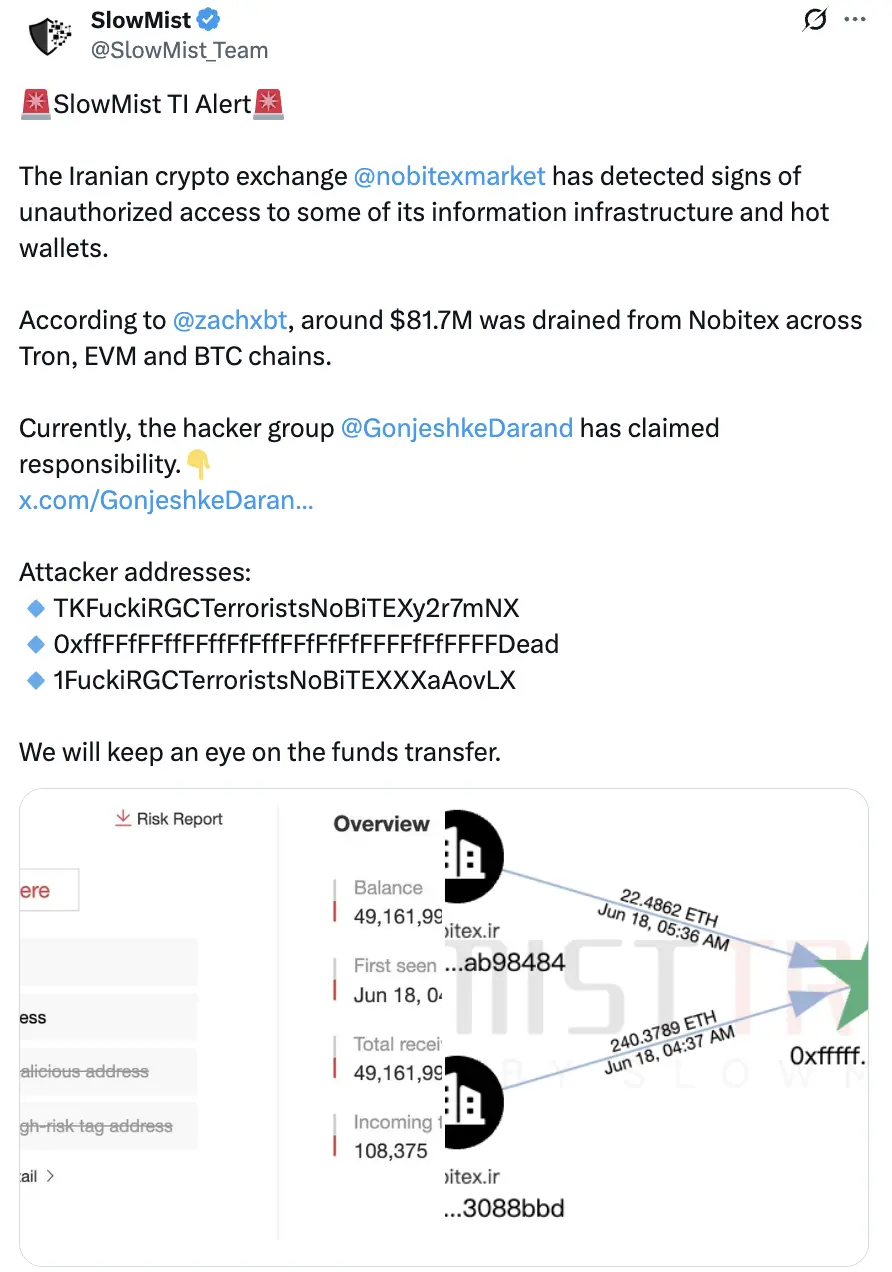
(https://x.com/slowmist_team/status/1935246606095593578)
Nobitex 也发布公告确认,部分基础设施和热钱包确实遭遇未授权访问,但强调用户资金安全无虞。
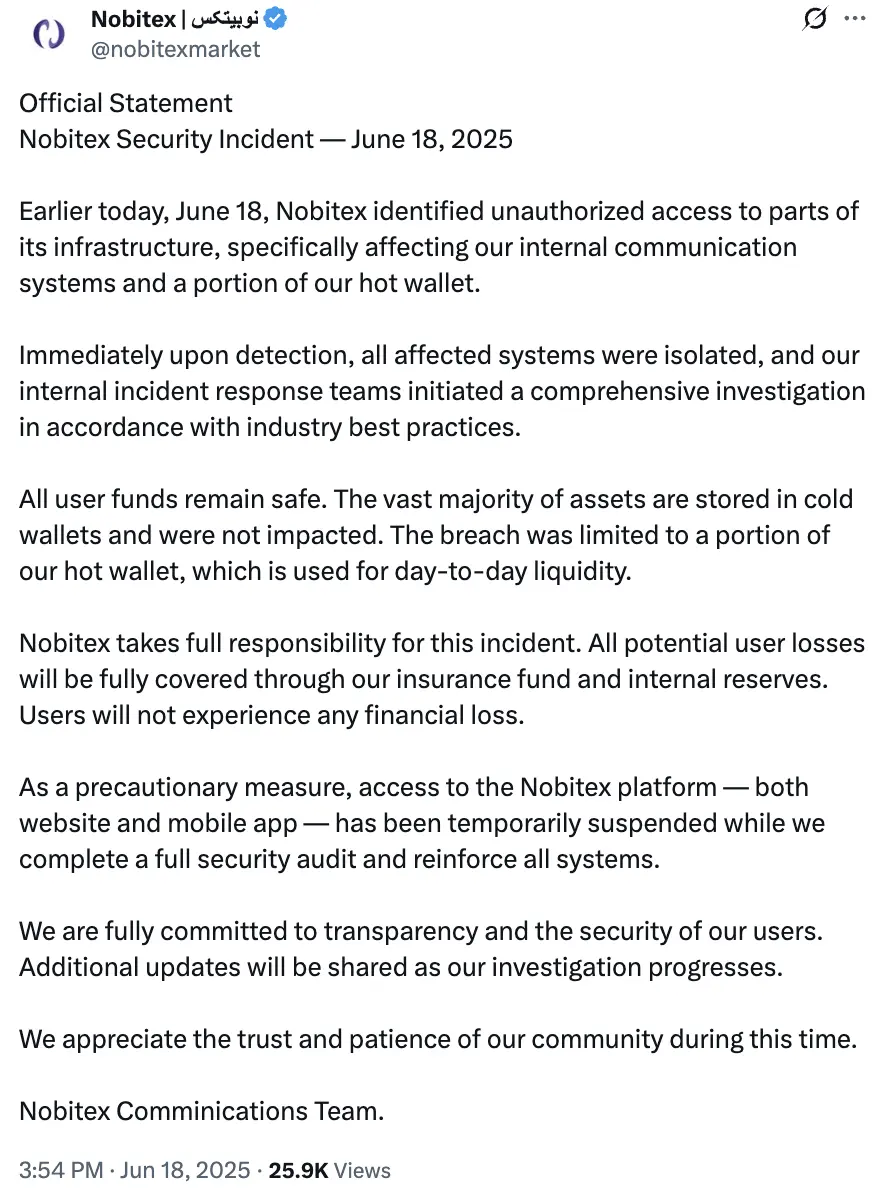
(https://x.com/nobitexmarket/status/1935244739575480472)
值得注意的是,攻击者不仅转移了资金,还主动将大量资产转入特制销毁地址,被“烧毁”的资产价值近 1 亿美元。
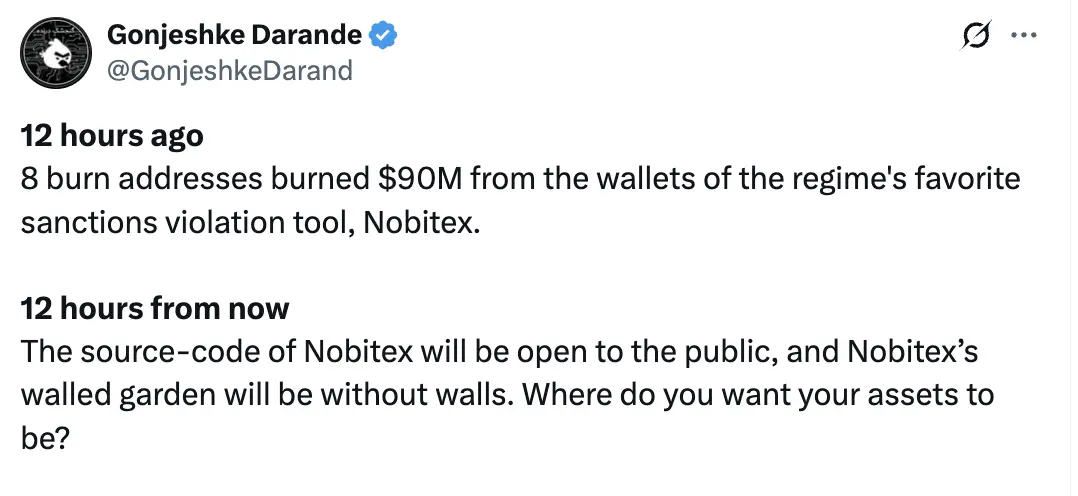
(https://x.com/GonjeshkeDarand/status/1935412212320891089)
时间线梳理
6 月 18 日
ZachXBT 披露伊朗加密交易所 Nobitex 疑似遭遇黑客攻击,在 TRON 链上发生大量可疑出金交易。慢雾(SlowMist) 进一步确认攻击涉及多条链,初步估算损失约为 8,170 万美元。
Nobitex 表示,技术团队检测到部分基础设施与热钱包遭到非法访问,已立即切断外部接口并启动调查。绝大多数资产存储在冷钱包中未受影响,此次入侵仅限于其用于日常流动性的部分热钱包。
黑客组织 Predatory Sparrow (Gonjeshke Darande) 宣称对此次攻击负责,并宣告将在 24 小时内公布 Nobitex 源代码和内部数据。

(https://x.com/GonjeshkeDarand/status/1935231018937536681)
6 月 19 日
Nobitex 发布第四号声明,表示平台已彻底封锁服务器外部访问路径,热钱包转账系“安全团队为保障资金所做的主动迁移”。同时,官方确认被盗资产被转移到一些由任意字符组成的非标准地址的钱包中,这些钱包被用来销毁用户资产,总计约 1 亿美元。
黑客组织 Predatory Sparrow (Gonjeshke Darande) 宣称已烧毁价值约 9,000 万美元的加密资产,并称其为“制裁规避工具”。
黑客组织 Predatory Sparrow (Gonjeshke Darande) 公开 Nobitex 源代码。
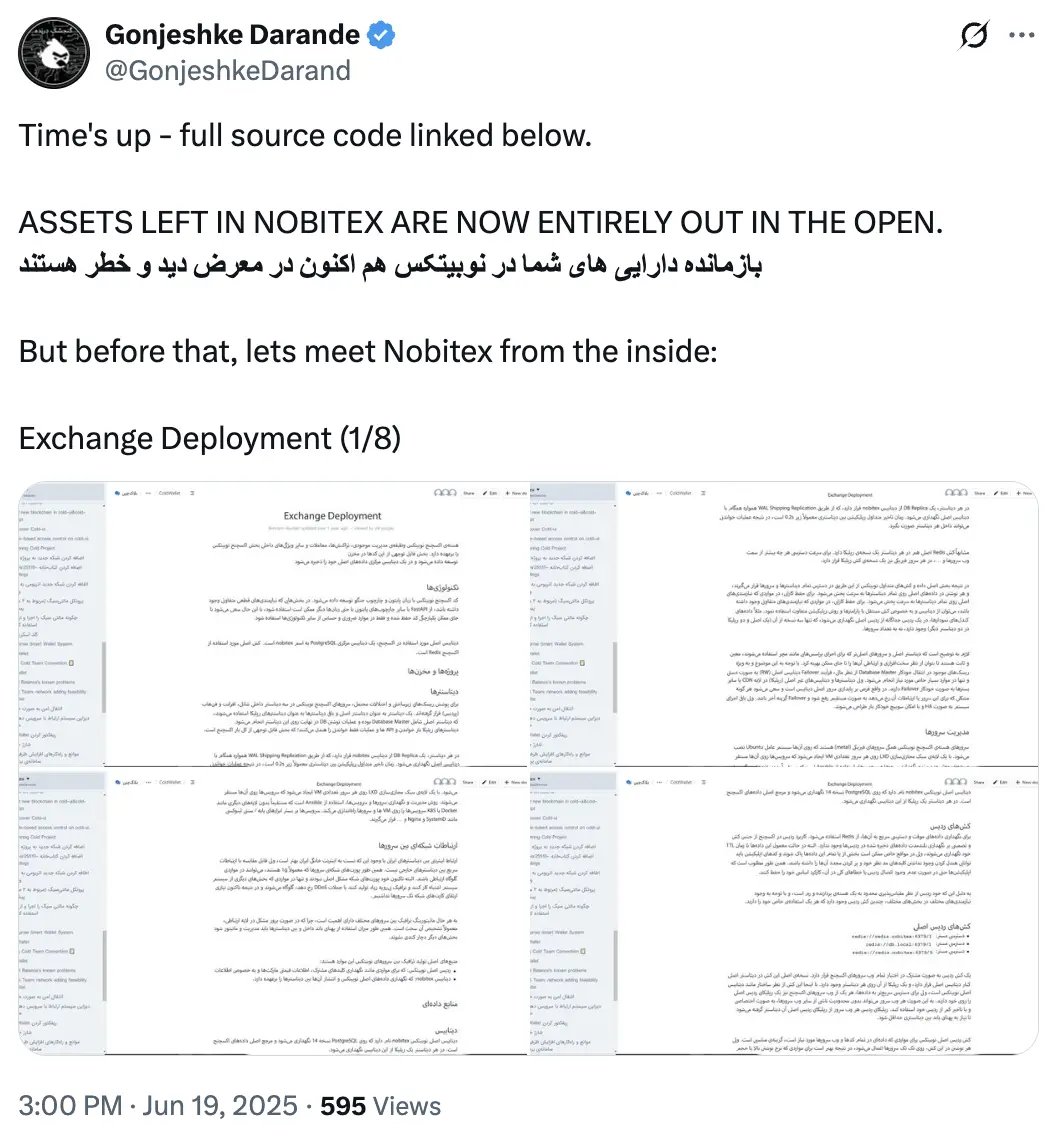
(https://x.com/GonjeshkeDarand/status/1935593397156270534)
源码信息
根据攻击者放出来的源码信息,得到文件夹信息如下:

具体来说,涉及下列内容:
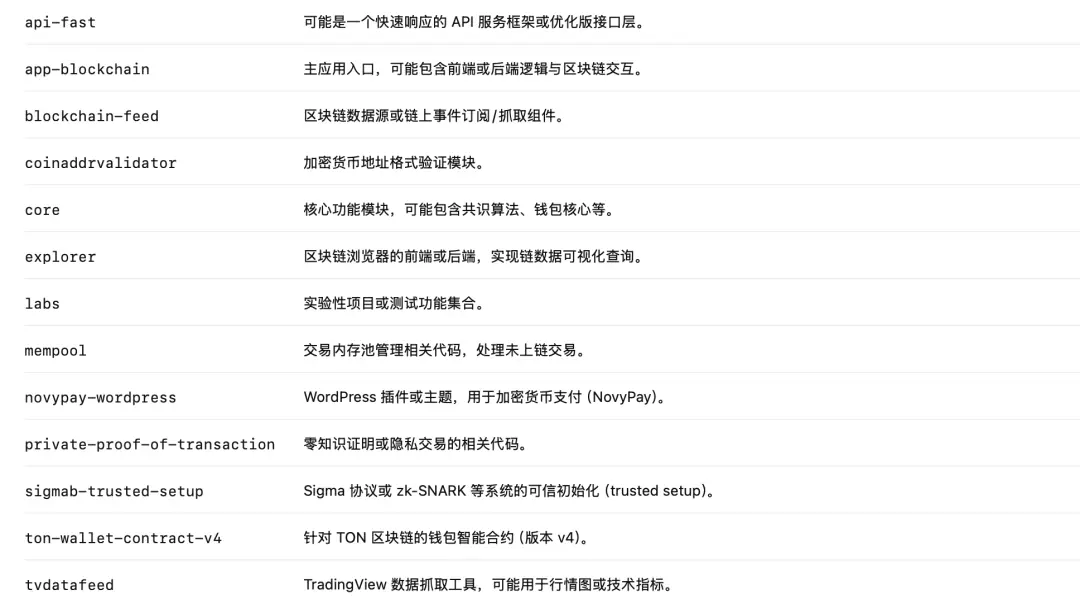
Nobitex 的核心系统主要采用 Python 编写,并使用 K8s 进行部署与管理。结合已知信息,我们猜测攻击者可能是突破了运维边界,从而进入内网,此处暂不展开分析。
MistTrack 分析
攻击者使用了多个看似合法、实则不可控的“销毁地址”接收资产,这些地址多数符合链上地址格式校验规则,能够成功接收资产,但一旦资金转入,即等于永久销毁,同时,这些地址还带有情绪性、挑衅性词汇,具有攻击意味。攻击者使用的部分“销毁地址”如下:
TKFuckiRGCTerroristsNoBiTEXy2r7mNX
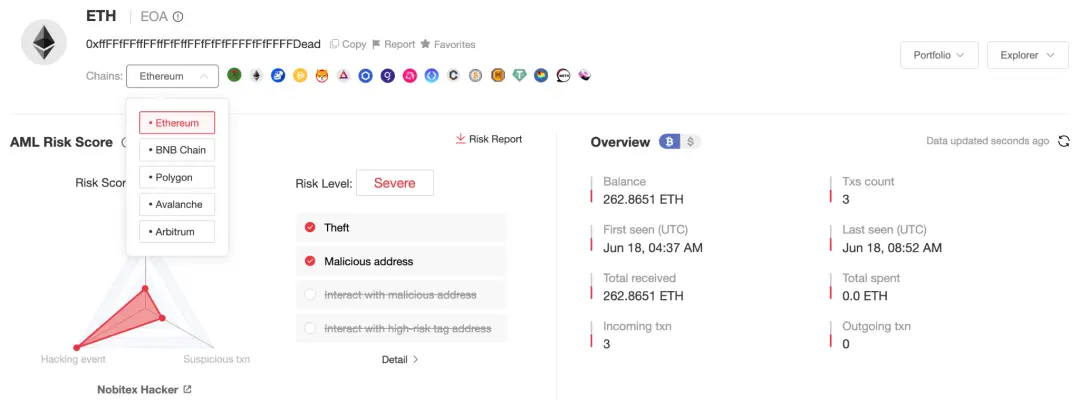
0xffFFfFFffFFffFfFffFFfFfFfFFFFfFfFFFFDead
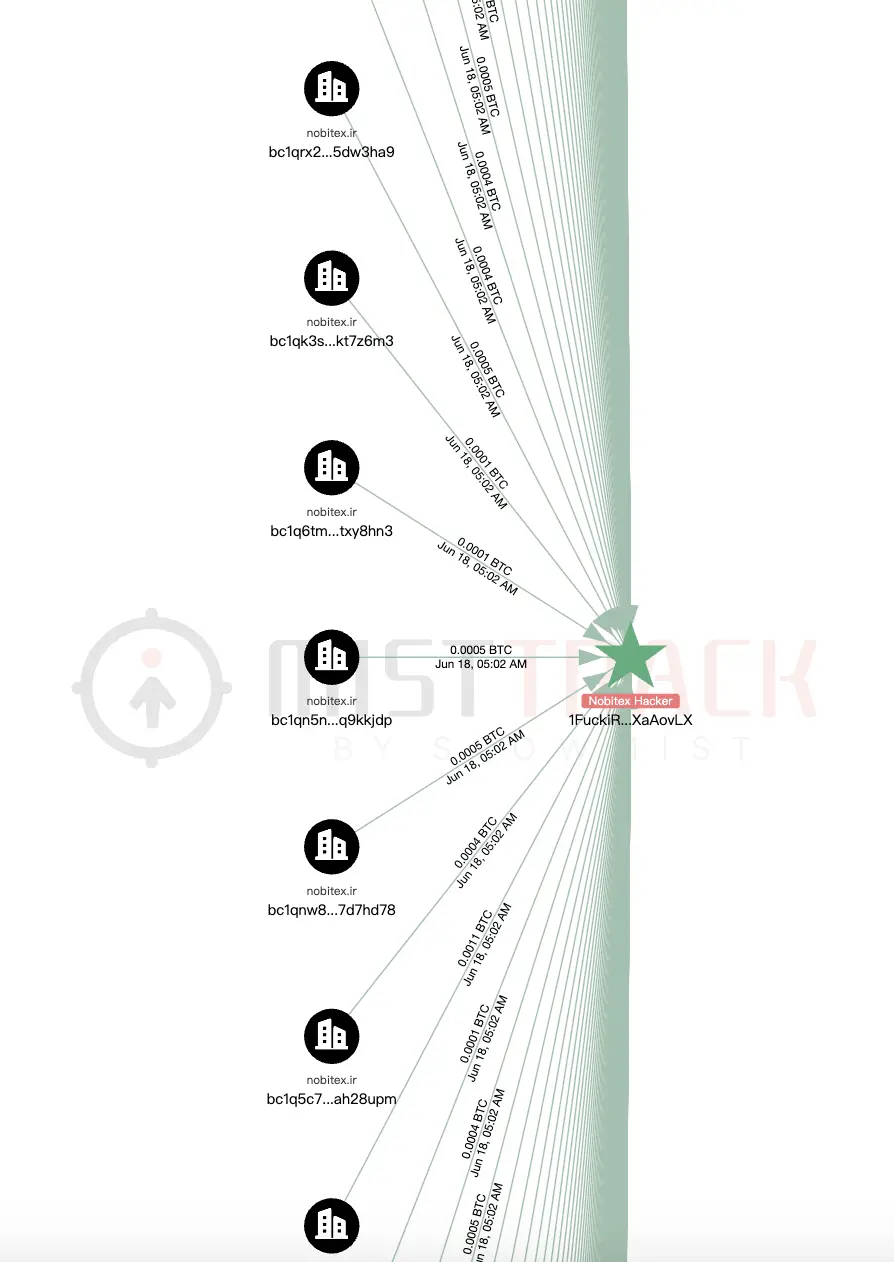
1FuckiRGCTerroristsNoBiTEXXXaAovLX
DFuckiRGCTerroristsNoBiTEXXXWLW65t
FuckiRGCTerroristsNoBiTEXXXXXXXXXXXXXXXXXXX
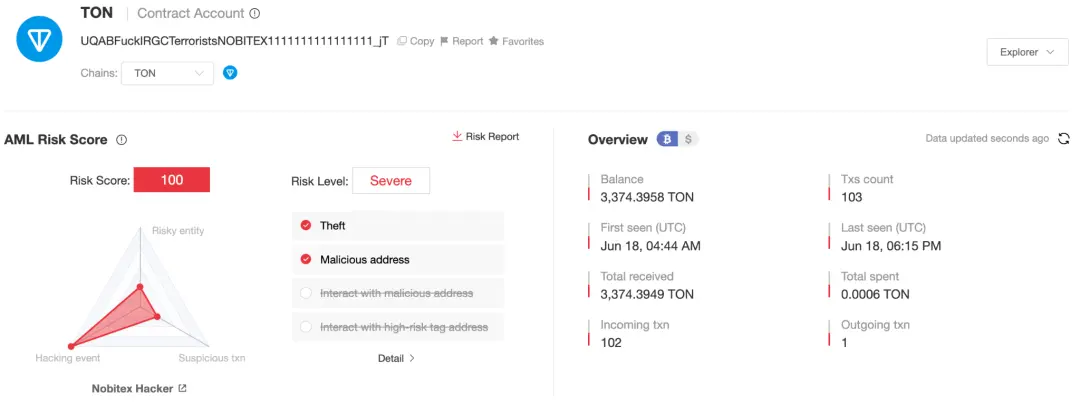
UQABFuckIRGCTerroristsNOBITEX1111111111111111_jT
one19fuckterr0rfuckterr0rfuckterr0rxn7kj7u
rFuckiRGCTerroristsNoBiTEXypBrmUM
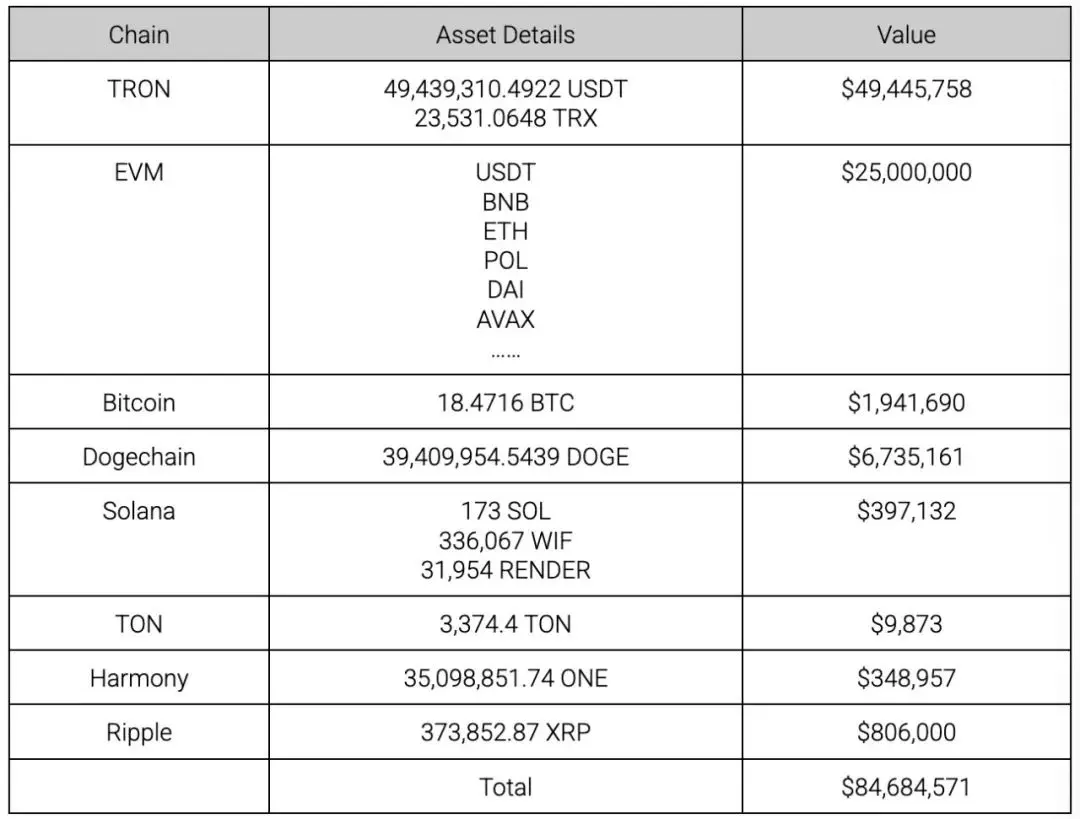
我们使用链上反洗钱与追踪工具 MistTrack 进行分析,Nobitex 的损失不完全统计如下:
根据 MistTrack 分析,攻击者在 TRON 上完成了 110,641 笔 USDT 交易和 2,889 笔 TRX 交易 :
攻击者盗取的 EVM 链主要包括 BSC、Ethereum、Arbitrum、Polygon 以及 Avalanche,除了每个生态的主流币种,还包含 UNI、LINK、SHIB 等多种代币。
在 Bitcoin 上,攻击者总共盗取 18.4716 BTC,约 2,086 笔交易。
在 Dogechain 上,攻击者总共盗取 39,409,954.5439 DOGE,约 34,081 笔交易。

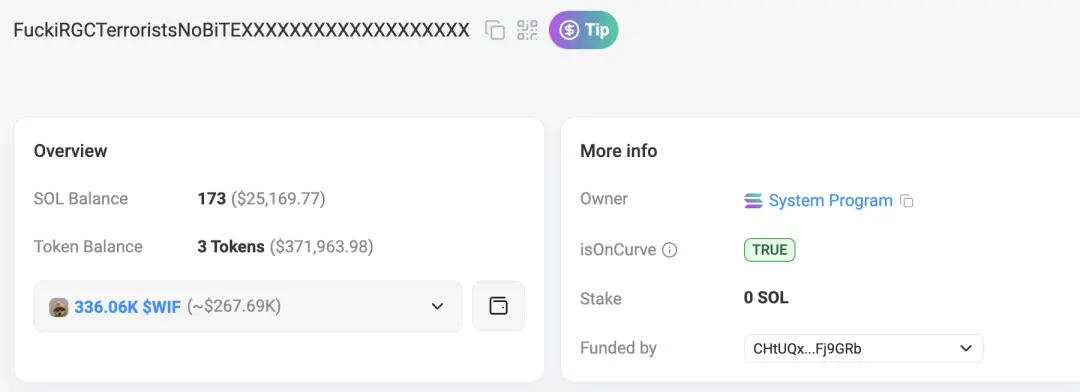
在 Solana 上,攻击者盗取 SOL、WIF 和 RENDER:
在 TON、Harmony、Ripple 上,攻击者分别盗取 3,374.4 TON、35,098,851.74 ONE 和 373,852.87 XRP:
MistTrack 已将相关地址加入恶意地址库,并将持续关注相关链上动向。
结语
Nobitex 事件再次提醒行业:安全是一个整体,平台需进一步强化安全防护,采用更先进的防御机制,特别是对于使用热钱包进行日常运营的平台而言,慢雾(SlowMist) 建议:
严格隔离冷热钱包权限与访问路径,定期审计热钱包调用权限;
采用链上实时监控系统(如 MistEye),及时获取全面的威胁情报和动态安全监控;
配合链上反洗钱系统(如 MistTrack),及时发现资金异常流向;
加强应急响应机制,确保攻击发生后能在黄金窗口内有效应对。
事件后续仍在调查中,慢雾安全团队将持续跟进并及时更新进展。
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




