这次共 13 个项目最终入围决赛,涵盖链游基础设施、Telegram 机器人、AI、跨链互操作性等多个领域。
撰文:ETHGlobal
编译:Frank,Foresight News
9 月 22 日至 24 日,ETHGlobal 在纽约举办 ETHGlobal New York 黑客松,共 13 个项目最终入围决赛,涵盖链游基础设施、Telegram 机器人、AI、跨链互操作性等多个领域。
其中不乏有一些有意思的创新项目,包括支持拍照识别的 Telegram 转账机器人 F.A.S.T.、为 NFT 智能创作背景故事的 ConsciousNFT、允许用户在丢失签名私钥后恢复其智能合约所有权的 A.S.R. 等等,本文将对入围项目进行简要介绍。
FRAMED!
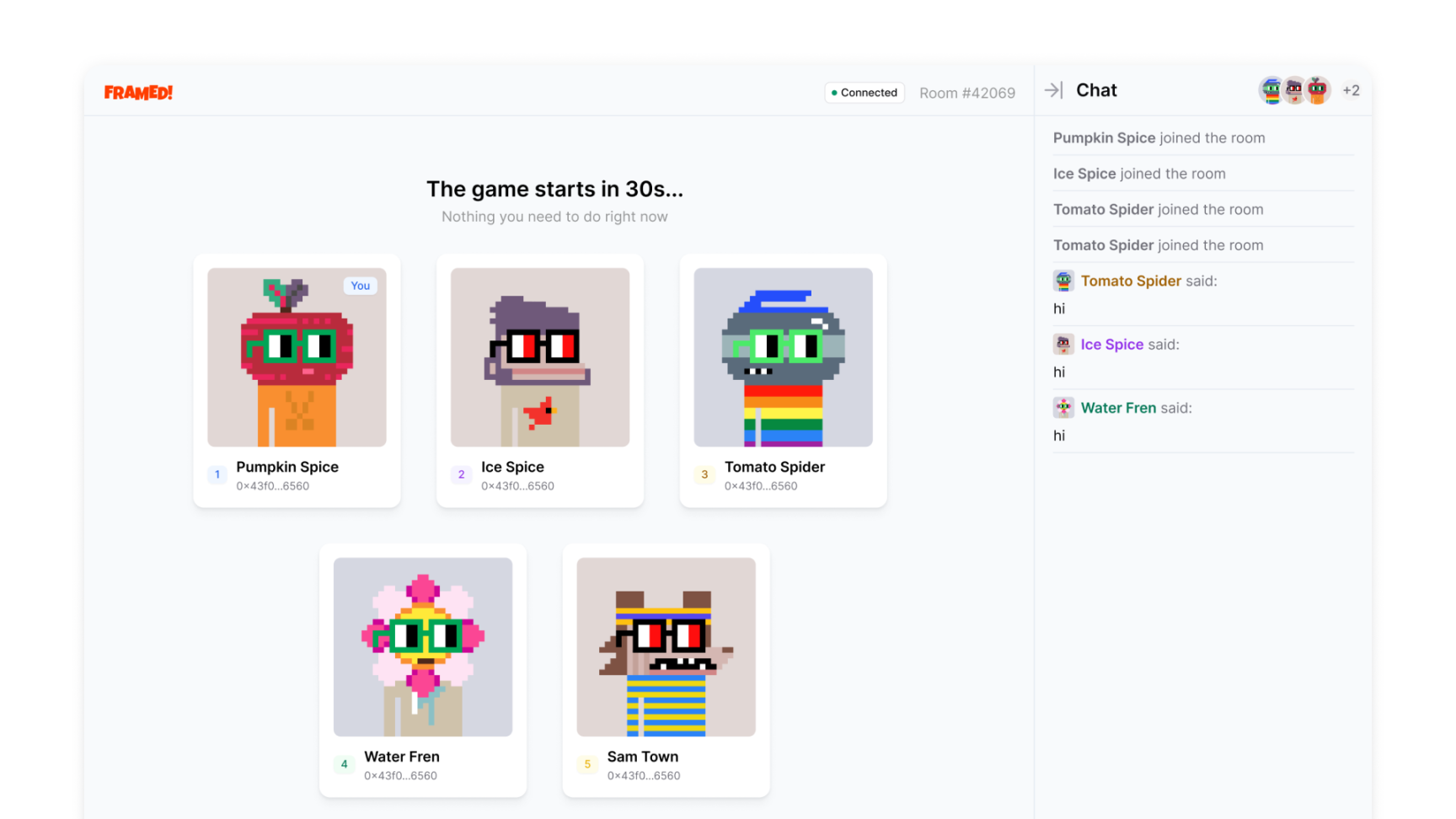
FRAMED! 是一个基于 fhEVM 构建的完全上链和无需信任的隐藏信息游戏(Mafia),其中艺术品窃贼从博物馆偷走了一幅画,玩家被随机分配角色,如公民、小偷、警察或侦探。游戏的目标是让小偷消灭公民,而市民则要共同努力识别并投票淘汰隐藏的小偷,玩家之间需要进行讨论和社交推理,并且必须合作和欺骗对方。
这款游戏的与众不同之处在于它能够直接在链上存储加密状态,全同态加密(FHE)智能合约允许在无需解密的情况下对加密数据进行计算。这种创新解决了隐私限制和保证问题。
F.A.S.T.
F.A.S.T. 是一个 Telegram 机器人,使用了图像索引技术,允许用户拍一张自己的照片进行注册,然后可以通过其他人的肖像(合影等形式)来向某人的钱包地址汇款。
ZeroTrustBounty
ZeroTrustBounty 旨在解决传统漏洞赏金平台的挑战——企业必须信任拥有敏感数据的第三方,而白帽黑客无法保证为其服务付款,也就是说白帽黑客向漏洞赏金计划报告了一个漏洞,却没有得到报酬。
而 ZeroTrustBounty 通过使用 TLS 公证和 Lit 协议来解决这个问题,假设有一个 SQL 注入漏洞,ZeroTrustBounty 允许白帽黑客隐藏攻击的 HTTP 请求,但可显示经过密码学验证的 HTTP 响应,以便受影响的企业可以通过密码学方式验证白帽黑客的报告并理解其影响。
付款部分,ZeroTrustBounty 使用 Lit 协议加密 HTTP 请求 / 响应,并且只有在支付给某个地址或持有 NFT 之后才能被企业解密。这样一来,如果企业有意修复该漏洞,则能够确保付款,并消除白帽黑客未获得报酬或第三方服务窃取漏洞技术 / 报告等问题,它还解决了企业向第三方服务披露敏感信息的问题。
Doom Arena
Doom Arena 是一个用于管理和创建游戏竞赛的分布式 DApp,允许开发者主持比赛提供了解决方案,为玩家提供激励,并为开发者产生收益。它引入了一种新颖的方法,以《毁灭战士》(Original Doom Game)为例举办游戏比赛。
这些比赛完全基于区块链和去中心化,为游戏开发者经济创造了一条新途径,游戏开发者和影响力人物可以通过他们的游戏发起比赛,并提供有吸引力的奖金池来激励参与。
其中主持人通过资助 APE 代币作为初始奖金池来启动比赛,玩家将使用他们的 ENS 个人资料登录并支付 APE 购买门票进入比赛。其中 90% 的资金用于增加奖金池,而 10% 归主持人所有,平均而言,在 100 名玩家支付门票参加比赛后,主持人就能收回成本。
总之,该项目创建了一个去中心化平台用于举办游戏竞赛,并为游戏开发者推广其作品、吸引玩家提供了创新方式,并建立起可持续的游戏推广经济模型,任何人都可以发起或参与比赛,为充满活力的游戏生态系统做出贡献。
AirTracker
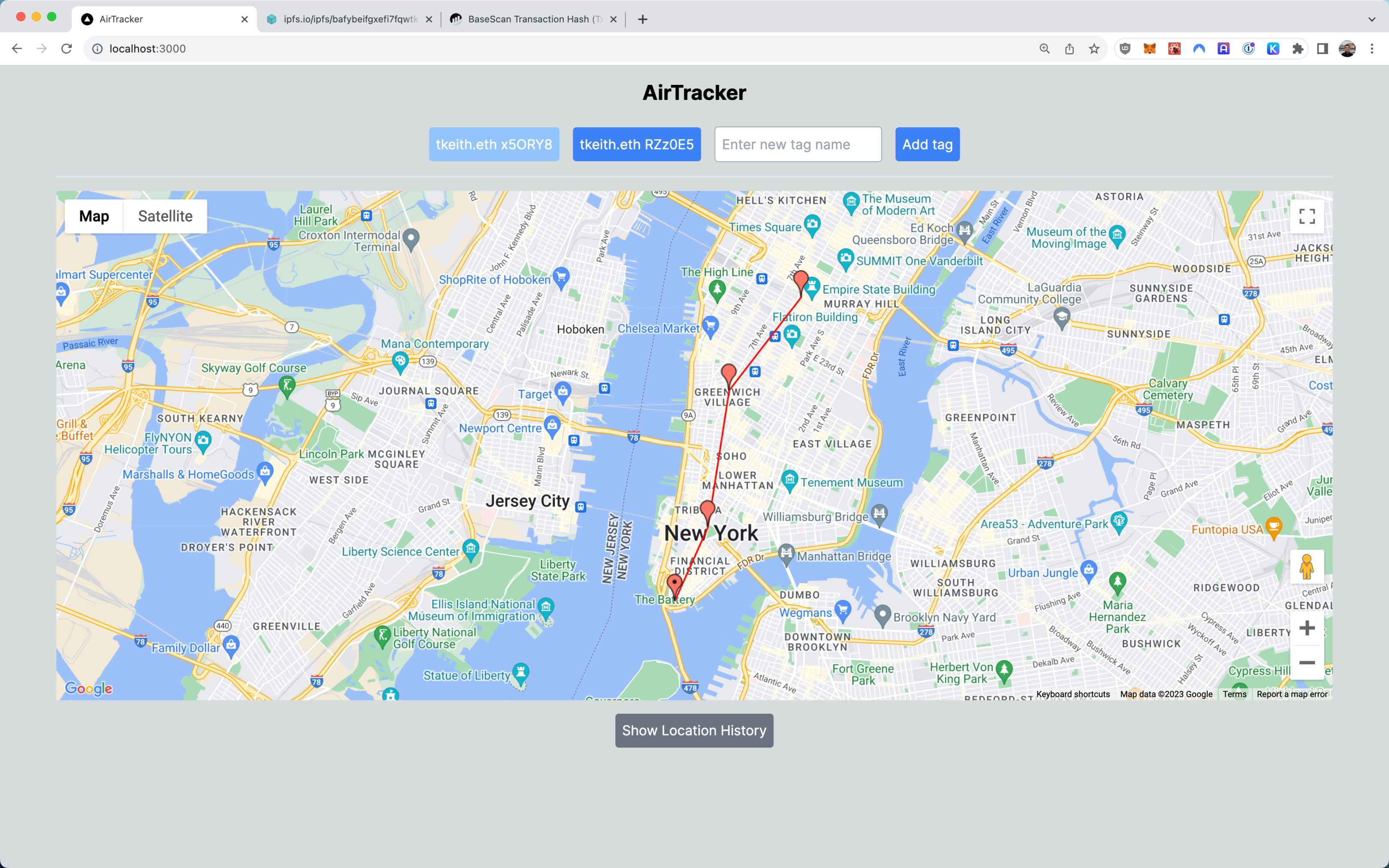
AirTracker 使用 AirTags 和区块链来存储和传递消息,以进行去中心化的实物物理资产跟踪。它先通过苹果设备抓取每个 AirTag 资产的位置数据,并将其存储在链上和 IPFS 上,位置更新也通过 XMTP 发送,并使用 AirStack 进行 ENS 查找。
用户可以登录 Web UI 以查看地图上每个资产的历史位置,以及特定的时间和位置更新。此外用户还可以通过简单地共享随机生成的标签名称(也称为位置加密密钥)与任何人或任何应用程序共享资产位置。
SafeCreate2
SafeCreate2 使用单链 Safe 保护多链智能合约部署,允许单个链上的 Safe 将智能合约部署到所有链上的相同地址,而无需桥接 ETH。它还允许单链 Safe 在任何多链合约上执行管理功能。
其中它使用 Axelar 发送和接收跨链消息,以确保没有地址冲突,并且每个链上的每个 Safe 都会收到一个唯一的部署命名空间。它还实现了一个 CrossChainOwnable 合约,使用该工具的应用程序可以继承该合约,从而允许在单个链上由 Safe 安全地管理多链合约。
ConsciousNFT
ConsciousNFT 是一个用于 NFT 项目的 AI 工具,可唤醒 NFT 中的意识身份,它为 NFT 项目创始人和所有者提供 AI 引擎工具集,用于共同构建丰富的内部世界,为 NFT 艺术品赋予独特的个性、背景故事、对话能力和叙事深度,成为有意识的角色。
其中包括创建挑战和任务,让 NFT 参与竞争并获得生成式 NFT 奖励;编写交互式叙事,在有意识的 NFT 中建立关系、进行战斗或寻找冒险。
通过 ConsciousNFT,用户可以将经过训练的 LLM 模型铸造到区块链上,以保留关于 NFT 的交互式人物形象,赋予每个 PFP 一种具有对话能力的个性、授权 PFP 培养粉丝群体、将静态 NFT 艺术转化为有感知能力的数字角色等等。
Space Guardians
Space Guardians 旨在为社交私钥恢复方案 MetaMask Snaps + Cryptosat Satellites 开发安全解决方案,以解决通知和审计跟踪的管理问题,从而减少监护人(Guardians)串通的可能性。
它使用了 MetaMask Snaps 框架,并将其与 Cryptosat Satellites 数字孪生(实验室 / 测试环境)的后端 API 集成,用于存储和事件审计,存储库包括前端 Web 产品和后端 API。
A.S.R.
A.S.R.(Anti Social Recovery)是一种设计模式,允许用户在丢失签名私钥后恢复其智能合约的所有权。
它允许用户部署智能合约,其所有权与其独特的人格证明(例如 World ID)相关联,使用 World ID 验证后,用户可以部署合约,然后从不同的 EOA 接管所有权。
此设计模式可以扩展到许多不同的用例,适用于任何智能合约角色(Minter、Pauser、Burner 等)。此外 World ID 可以与不同的人格证明提供者交换,还考虑了如何将其应用于 ERC20 代币,允许用户从新地址索取余额。
当前支持的操作包括:
- 使用钱包登录;
- 使用 World ID 验证人格;
- 以所有者身份部署智能合约;
- 导入现有智能合约;
- 将智能合约所有权转让给 World ID 持有人拥有的新 EOA 地址;
MEVictim Rebate
MEVictim Rebate 通过使用历史链上数据识别 MEV 受害者,并向受害者空投一个 ERC-721 代币以访问 Scroll 上的代币门控 Uniswap v4 池,从而设计更好的市场激励措施。
具体来讲,该项目将识别 ETH Goerli 上的 MEV 受害者,并授予这些受害者一个 ERC-721 代币,当持有者向 Scroll 上的 Uniswap v4 池提供流动性时,持有者有资格获得回扣。最终该项目根据用户在 ETH Goerli 上的历史链数据,激励更好的 Scroll 交互行为。
其中 ETH Goerli 交易的子图用于识别 MEV 受害者(被抢先交易、三明治攻击等的个人)。然后,交易哈希和日志 ID 作为 Axiom 电路的输入提供。
Axiom 电路使用交易哈希来证明钱包地址是否确实是 MEV 攻击的受害者,如果符合条件,对应的钱包地址将收到一个 ERC-721 代币,然后可以桥接 ERC-721 代币至 Scroll。
RealReturn
RealReturn 是经过验证的真实投资回报的开放排行榜,可以使任何人公开证明他们的投资回报,而无需与任何人或任何地方共享他们的凭据。
它采用了诸如第三方 TLS、MPC 等密码学技术,来处理用户与应用程序服务器之间的 TLS 会话,因此即使会话的内容仍然仅对用户和应用程序服务器可见,公证人也可以在侧面生成一些东西来证明记录未被篡改。
Abstract Wallet
Abstract Wallet 使用 Solidity FCL 来实现 WebAuthn 驱动的 Userop,用户只需拥有智能手机,即可使用带有密钥的帐户抽象功能,实现用户的即时点击登录。
其中用户只需单击一下,即可生成密钥凭证、智能账户、铸造 NFT,且当用户单击创建帐户时,它会使用智能手机的生物识别功能生成一个 FIDO 密钥。
该 FIDO 密钥存储在智能手机的保险库中,提供了对私钥(不像浏览器那样存储在不安全的内存区域)的防护,从密钥凭证派生出来的公钥被推送到链上的主合约,后续交易将使用此密钥进行身份验证。
XSafe
XSafe 优化了 Gnosis Safe 的多重签名流程以供跨链使用,核心目标是减少在多个区块链网络上执行相同管理功能所涉及的时间和复杂性。
用户只需签名一次,签名就会自动传播到所有链接的区块链网络,以跨多个网络执行单个交易。工作流程包括:
- 初始化:用户通过 Gnosis Safe UI(一次性设置)将 X-Safe 集成为自定义模块;
- 创建交易:用户或管理员创建需要跨多个区块链网络执行的交易;
- 签名生成:用户通过 X-Safe 界面使用其私钥对交易进行签名;
- 签名传播:X-Safe 将生成的签名传播到所有已集成区块链上的相应 Gnosis Safe 合约;
- 交易执行:一旦收集到所需数量的签名,X-Safe 就会根据用户设置同时或顺序触发所有链上的交易执行;
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




