Author: enze & Lisa
Editor: 77
Background
On January 8, 2026, the decentralized off-chain computing protocol Truebit Protocol was attacked, with the attacker exploiting a contract vulnerability to profit approximately 8,535 ETH (about 26.44 million USD). Below is a detailed analysis of this attack by the SlowMist security team.
Root Cause
The Purchase contract of Truebit Protocol lacked overflow protection in its integer addition operation when calculating the amount of ETH required to mint TRU tokens, resulting in an abnormal price calculation that returned zero. This allowed the attacker to mint a large number of tokens at nearly zero cost and extract the contract's reserves.
Prerequisite Knowledge
Truebit Protocol is a decentralized off-chain computing market designed to transfer complex computing tasks from the blockchain mainnet to off-chain execution, while ensuring the correctness of computation results through economic incentive mechanisms. The protocol introduces a native token, TRU, which employs an algorithmic elastic supply mechanism. The real-time price of TRU is dynamically determined by the ratio function of the ETH reserve in the contract to the circulating supply of TRU, with its minting and burning fully managed by on-chain smart contracts:
- Minting: Users deposit ETH into the Purchase contract to mint TRU at an algorithmic price.
- Burning: Users burn their held TRU to withdraw ETH from the contract at an algorithmic price.
Attack Analysis
Attacker address: 0x6C8EC8f14bE7C01672d31CFa5f2CEfeAB2562b50
Attack contract: 0x764C64b2A09b09Acb100B80d8c505Aa6a0302EF2
Related attack transaction: 0xcd4755645595094a8ab984d0db7e3b4aabde72a5c87c4f176a030629c47fb014
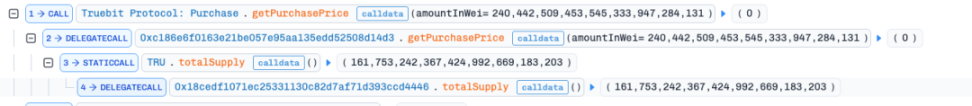
- The attacker called the getPurchasePrice function of the Purchase contract to query the amount of ETH required to mint 240,442,509,453,545,333,947,284,131 TRU tokens. Due to the carefully constructed value, an integer overflow occurred during the price calculation process, resulting in the function returning 0.
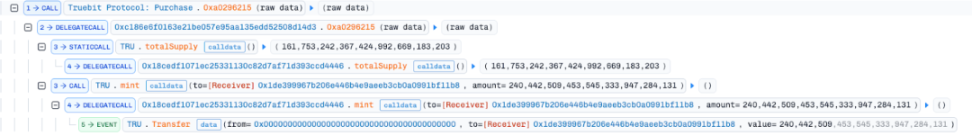
- The attacker called the 0xa0296215 function (minting function) of the Purchase contract, passing in the aforementioned token amount. Since the required ETH price was calculated as 0, the attacker did not need to pay any ETH and successfully minted 240,442,509,453,545,333,947,284,131 TRU tokens.
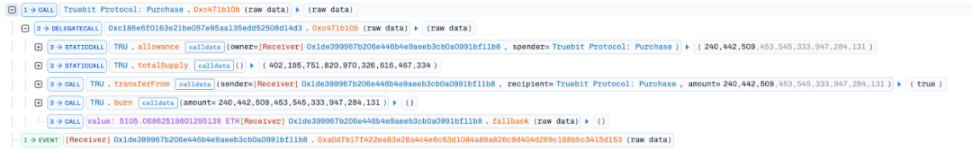
- The attacker immediately called the 0xc471b10b function (burning function) of the Purchase contract to burn all the newly minted TRU tokens, exchanging them for 5,105.069 ETH from the contract reserves.
- The attacker repeated the above "minting → burning" process. As the supply of TRU tokens (S) increased, subsequent minting required a small amount of ETH, but the value of the minted tokens still far exceeded the payment cost, leaving considerable arbitrage space. The attacker continued operations until the contract's ETH reserves were exhausted.
Attack Principle Analysis
1. Price Calculation Formula
By reverse engineering the Purchase contract, we identified the core price calculation function:
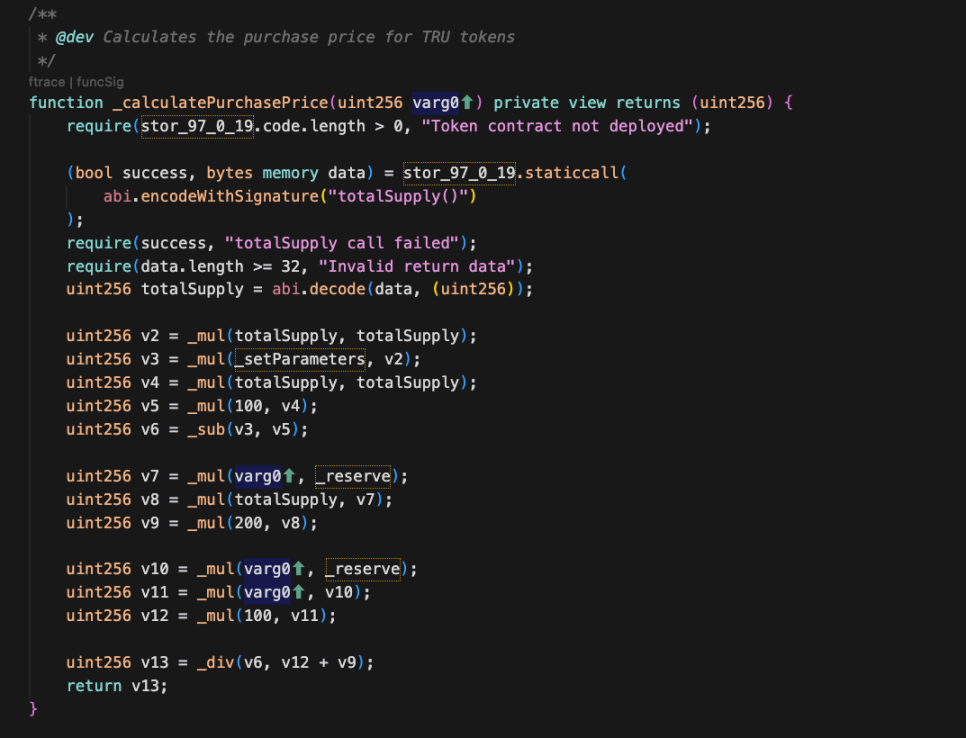
This function is used to calculate the amount of ETH required to mint a specified number of tokens, with the calculation formula as follows:
Price = (100 * A² * R + 200 * A * R * S) / ((100 - T) * S²)
Where:
- A (AmountIn): The number of tokens the user requests to mint
- R (Reserve): The current ETH reserve in the contract
- S (Supply): The current total supply of tokens
- T (THETA): A contract parameter, fixed at 75
2. Vulnerability Reason
The contract was compiled using Solidity version ^0.6.10. In versions prior to Solidity 0.8.0, arithmetic operators (+, -, *) do not include built-in overflow checks. When the result of an operation exceeds the maximum value of uint256 (2²⁵⁶ - 1), a silent overflow occurs, and the result wraps around to a small value near 0.
In the critical code for price calculation:
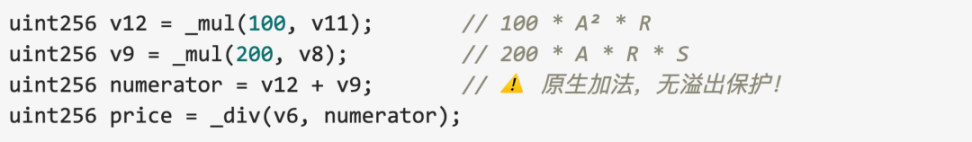
While multiplication operations used the SafeMath library for overflow checks, the addition operation v12 + v9 directly used the native + operator without overflow protection. This constituted the core vulnerability of this attack.
3. Attack Value Analysis
Taking the attacker's first minting transaction as an example:
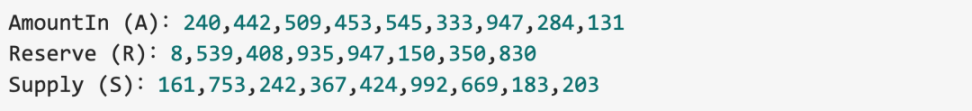
Calculation process:
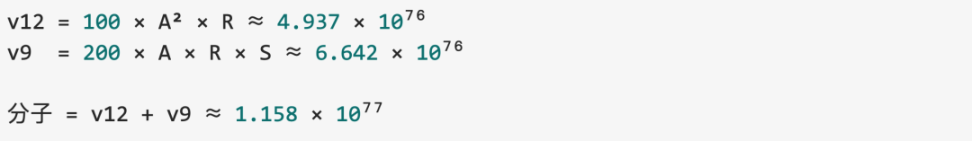
Overflow determination:
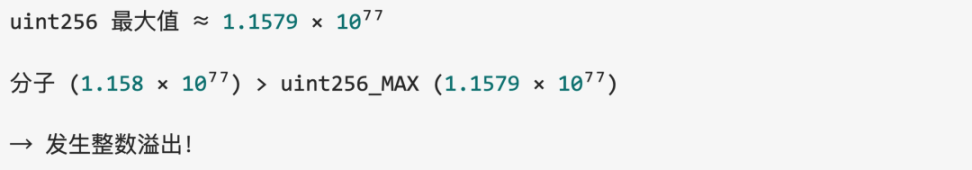
Since the result of v12 + v9 exceeded the maximum value of uint256, an overflow occurred, wrapping the numerator to a very small number. After integer division, the final calculated Price = 0.
4. Attack Impact
The attacker carefully constructed the AmountIn parameter so that:
- Multiplication operations passed the SafeMath check (not triggering revert)
- Addition operations caused an overflow, wrapping the numerator to a small value
- The integer division result was 0
Ultimately, the attacker was able to mint a large number of tokens without paying any ETH.
MistTrack Analysis
According to on-chain tracking and anti-money laundering tool MistTrack, the attacker profited approximately 8,535 ETH (about 26.44 million USD) from this incident.
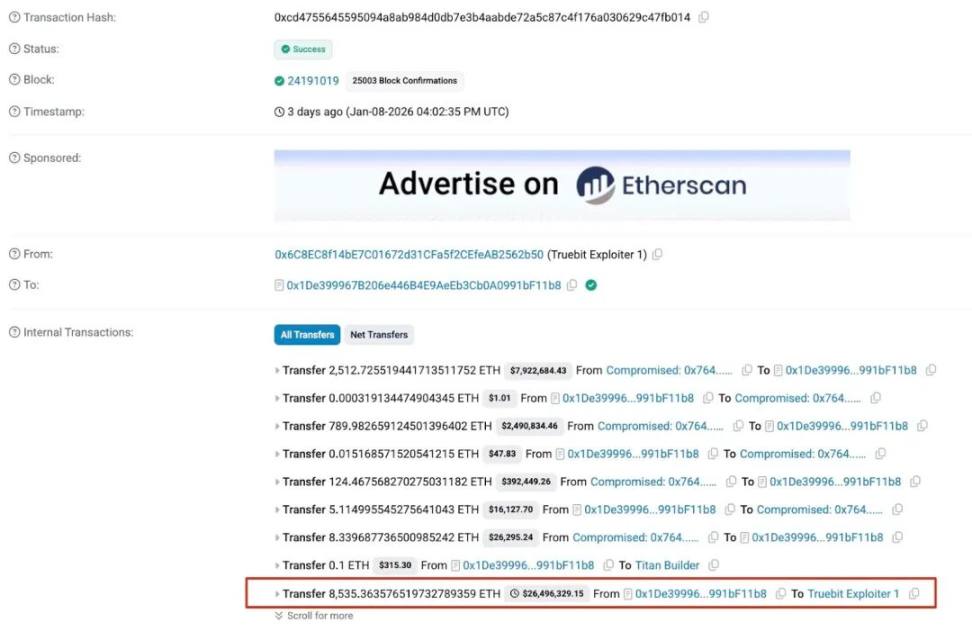
The stolen 8,535 ETH was first transferred to three new addresses, which ultimately all transferred to Tornado Cash.
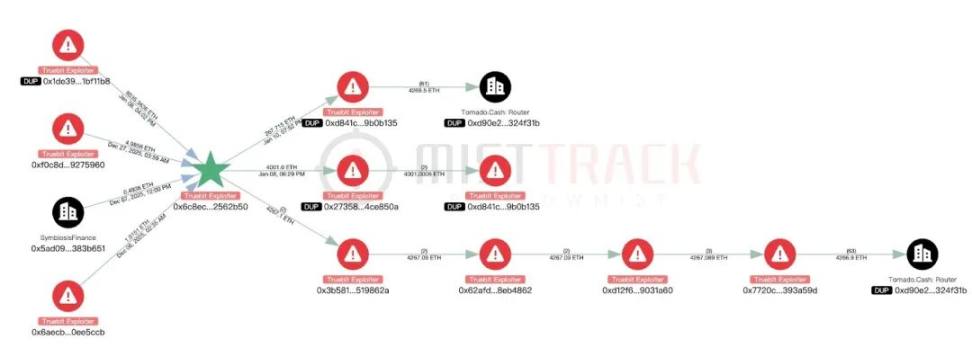
On-chain records show that the attacker’s address had transaction records on November 20, 2025, December 6, 2025, and December 27, 2025, with the following main activities:
- November 20, 2025: Acquired funds through Drain on Avalanche and cross-chained to BNB Chain via Rhino.fi.
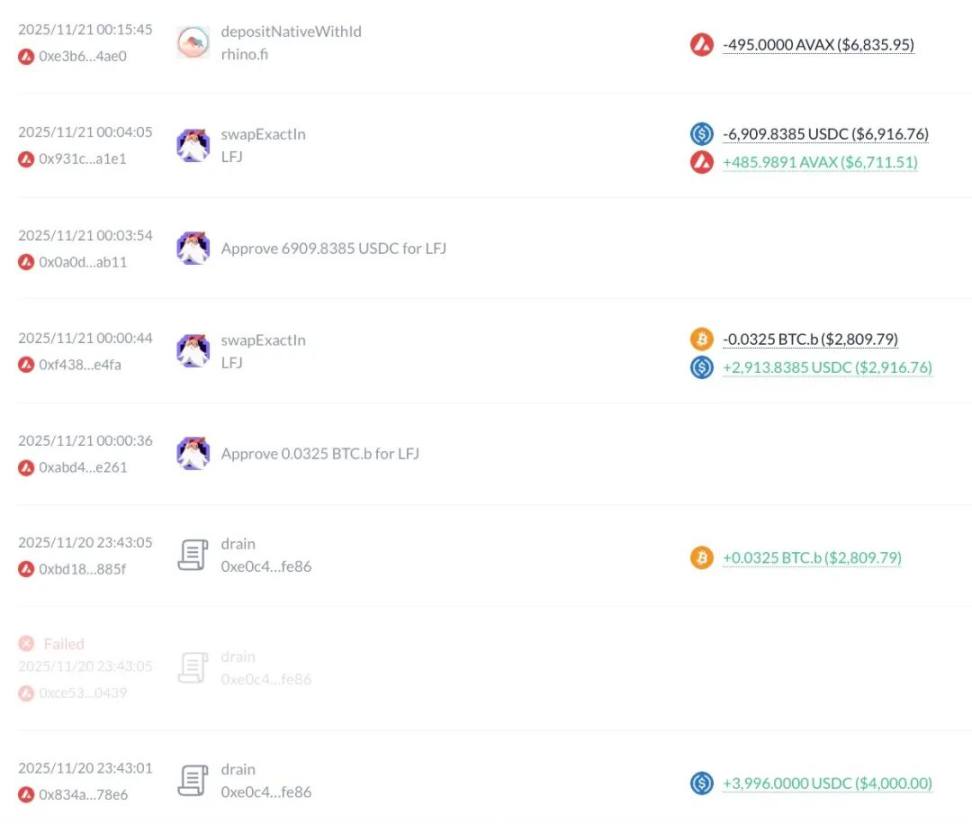
- December 6, 2025: Transferred the received funds from BNB Chain to Ethereum via Rhino.fi.

- December 27, 2025: Acquired 4.98 ETH on Ethereum through RUN, suspected to be from another attack initiated by the attacker, with a total of 5 ETH transferred to Tornado Cash.
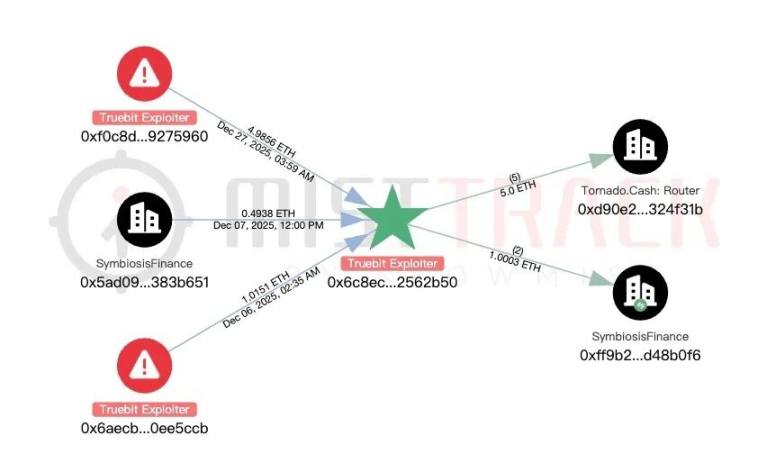
Currently, MistTrack has marked the relevant addresses.
Conclusion
The fundamental reason for this attack was that the Purchase contract did not use the SafeMath library for overflow protection in the addition operation of the numerator when calculating the minting price. Since the contract was compiled using Solidity version 0.6.10, the native + operator lacked overflow checks. The attacker constructed a specific minting quantity that caused the addition result to exceed the maximum value of uint256 and wrap around, leading to a price calculation result of 0, thus achieving nearly zero-cost token minting and arbitrage.
The SlowMist security team recommends that developers ensure all arithmetic operations use the SafeMath library for protection in contracts using Solidity versions below 0.8.0 to avoid logical vulnerabilities caused by integer overflow.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



