Not Your Keys, Not Your Coins——去中心化的自由,以绝对的「私钥安全」为代价。
Chainalysis 2025年7月报告显示,17%-23%的比特币因为私钥遗忘或设备损毁而永久沉睡。因为私钥就是资产所有权,一旦丢失,就无法重置,也没有客服可以帮忙找回,一旦被他人知晓,资金被盗也几乎无法追回。链上的世界给了我们自由,同时也把责任完全交回到我们手里。随着链上生态繁荣起来,我们遇到的各种资产被盗事件屡有发生,但大家往往后知后觉,而且很难搞清楚是哪个环节出了问题——私钥泄露了?点了钓鱼链接?下载了木马程序?还是其他操作失误?
OKX Web3 安全团队希望通过这次科普,加强大家的私钥安全意识,同时再次梳理那些最容易忽视的安全盲点。
一、私钥或者助记词为什么会泄漏?
首先纠正一个常见误区,很多用户认为私钥或助记词泄漏(以下简称“私钥泄漏”)通常发生在使用钱包的过程中。其实,如果你通过正规渠道下载、使用大品牌官方版本的钱包,在正常使用过程中,私钥一般不会被泄漏。私钥泄漏大多是因为保存不当,被他人获取。一旦有人掌握了你的私钥,就可以在任何钱包中导入并控制该账户的资产。
实际上,私钥泄漏的原因有很多,具体源头往往很难完全排查。不过,通过对大量行业案例的分析和协助排查,我们也总结出了一些典型的场景和线索。(见下文)
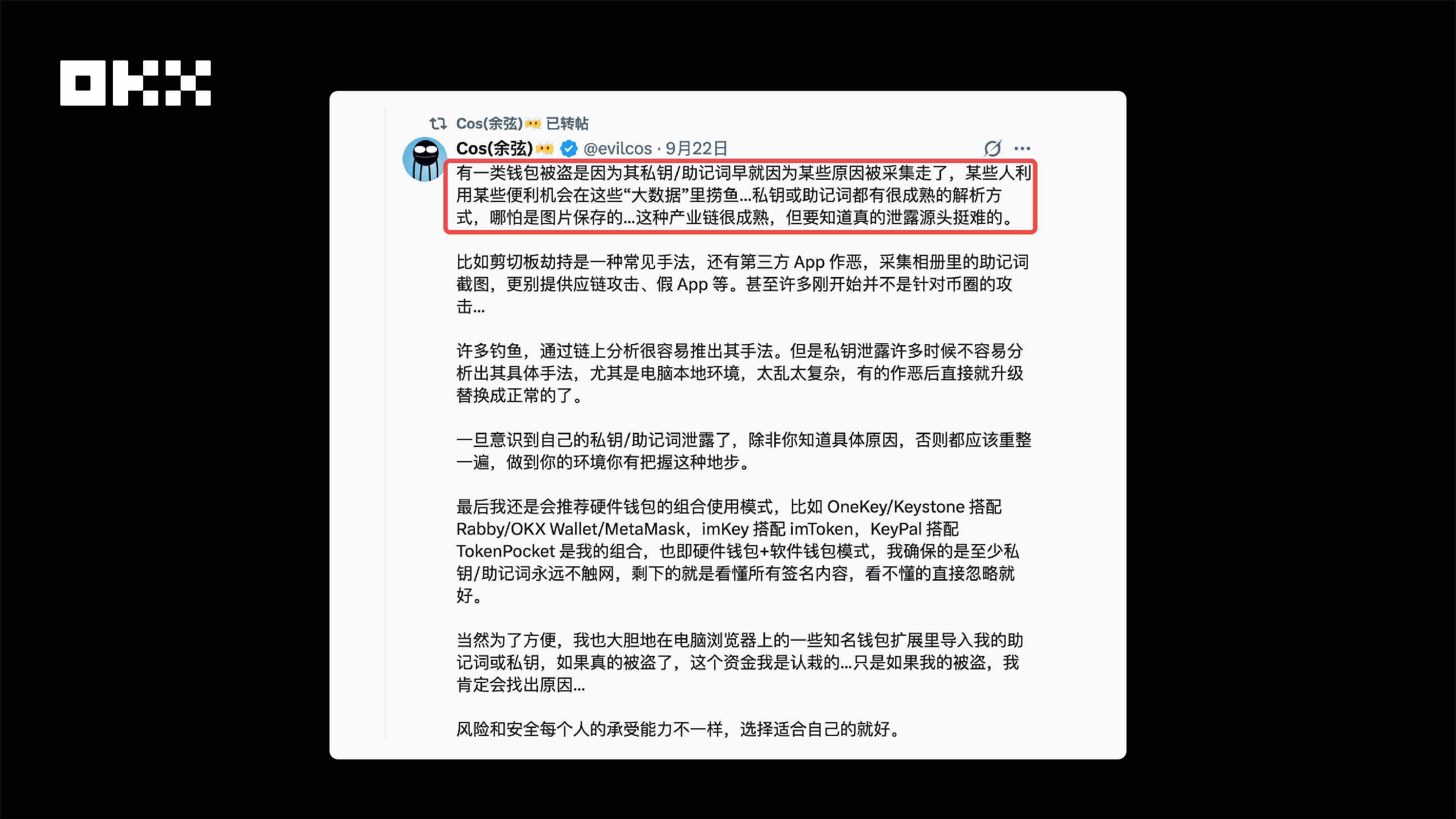
图片:慢雾余弦老师分享的私钥被盗原因分析的难点
二、常见的私钥泄漏场景和规避方法
(一)最容易被忽视的场景:钱包创建时已经泄漏
案例一:他人代创建钱包。李先生刚接触 Web3,在一位“热心导师”的帮助下创建了钱包。导师帮他完成了钱包创建、设置交易密码,并指导充值和交易。虽然钱包设置了交易密码,但在创建过程中,导师已经掌握了他的私钥。几天后,李先生充值的 5 ETH 在短时间内被转走。他才意识到,交易密码只是本地验证,掌握私钥的人可以在任何钱包中导入并直接转走他的资产。
安全建议:钱包要自己独立创建,不要让任何人“帮忙”或“代办”。如果怀疑私钥可能已泄露,应尽快将资产转移到新的钱包。
案例二:视频会议投屏创建。张女士在远程“老师”的指导下,通过视频会议投屏创建钱包。老师一步步演示:下载钱包、生成助记词、充值 Gas、购买代币。整个过程看起来非常“贴心”,最后还提醒她:“私钥一定不要泄漏给任何人。”但她并不知道,在投屏的那一刻,助记词可能已经被记录。两周后,她账户中价值约 $12,000 的 USDT 被转走。
安全建议:创建钱包时,关闭屏幕共享、录屏或投屏等功能。如果怀疑私钥可能被泄露,应尽快将资产转移到新的钱包。此外,OKX Wallet在显示私钥和助记词的页面中,不允许截屏、录屏或投屏,有效提升安全性。
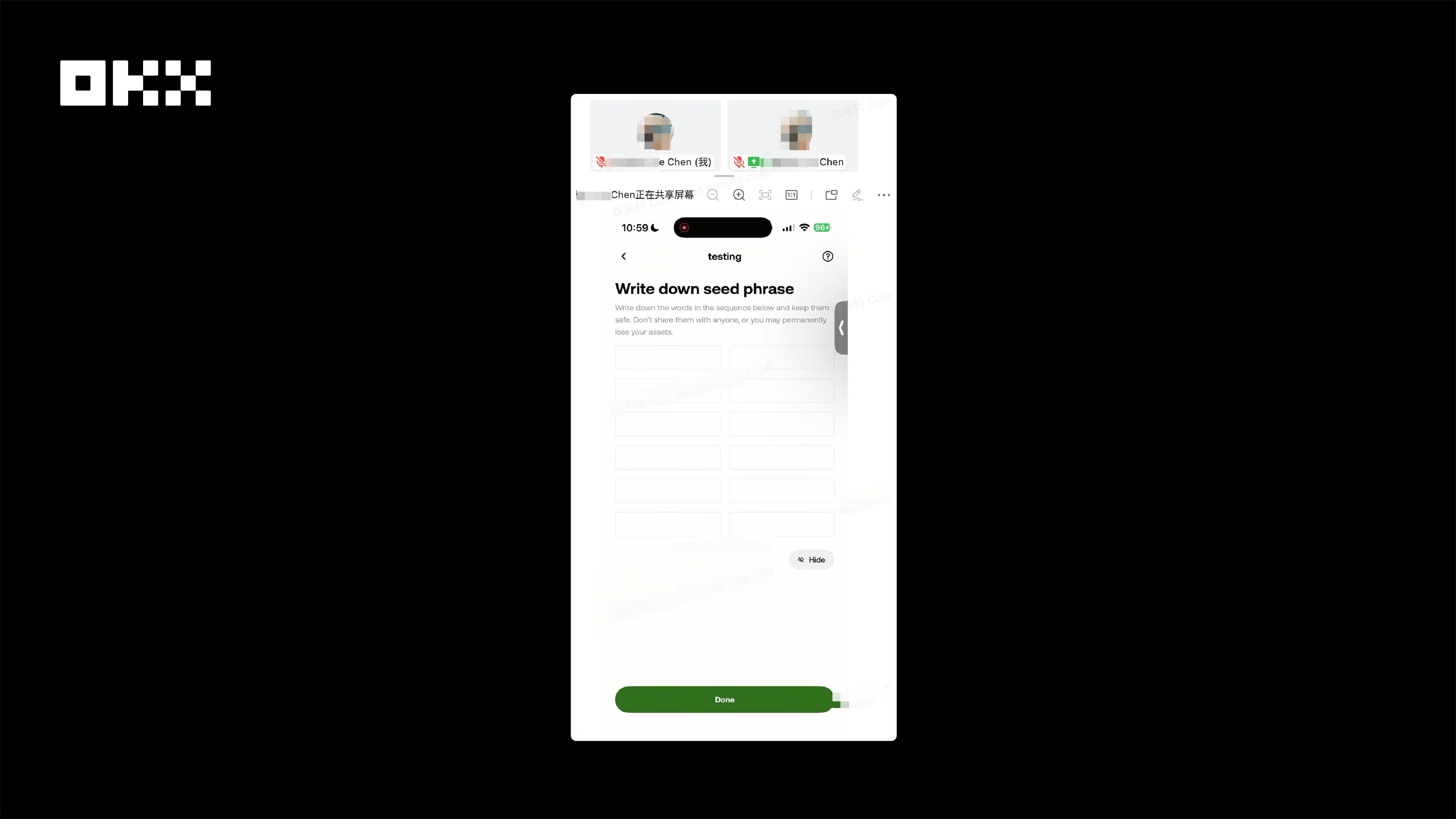
图片:检测到在投屏,OKX Wallet会自动隐去助记词和私钥,他人无法看到文本
(二)最普遍的场景:私钥保存不当导致泄漏
案例三:假冒APP,安卓用户的噩梦。王先生是一位谨慎的用户,他创建钱包后将助记词截图保存到本地相册,从未上传到云端,自认为这样比较安全。然而,他在某个论坛下载了一个所谓的“增强版 Telegram”,这款 APP 的图标和界面几乎与官方版本一致。实际上,它在后台持续扫描手机相册,通过 OCR(光学字符识别)技术识别出助记词,并自动上传到黑客服务器。三个月后,王先生账户中的资产被清空,损失超过 $50,000。技术分析显示,他的手机中还有假的 imToken、MetaMask、Google Authenticator 等多个恶意 APP。

案例四:BOM 恶意应用导致助记词泄漏。2025 年 2 月 14 日,有多位用户集中出现钱包资产被盗情况。经链上数据分析,这些被盗案例均显示典型的助记词/私钥泄漏特征。进一步回访受害用户发现,他们大多曾安装并使用过一款名为 BOM 的应用。深入调查显示,该应用实际上是精心伪装的诈骗软件。不法分子通过诱导用户授权,非法获取助记词/私钥权限,从而进行系统性资产转移并试图隐匿行为。
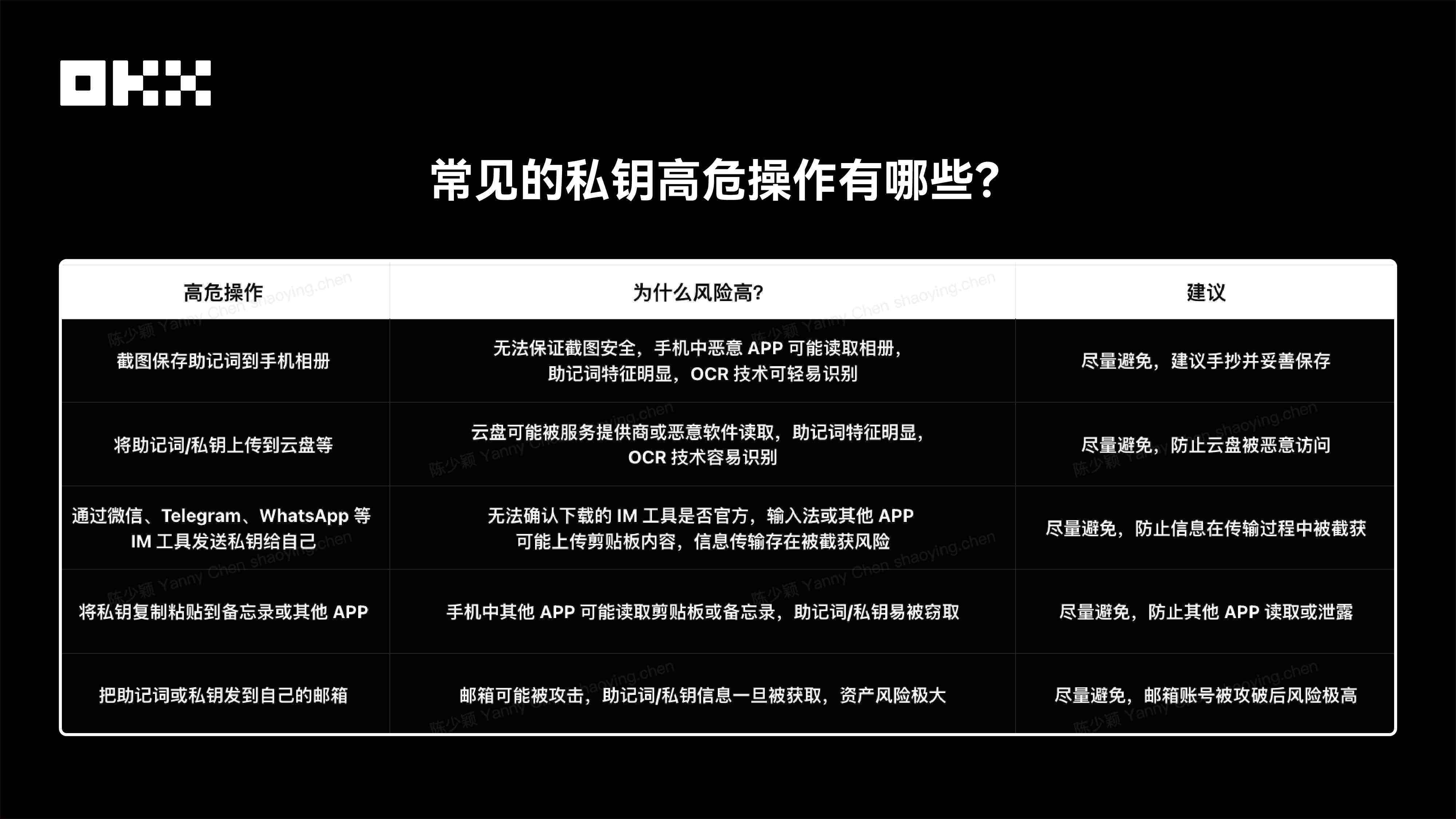
安全建议:很多用户出于“图方便”而养成的习惯,恰恰是最危险的。所以建议大家:1)不要截图助记词! 建议用纸质手抄的方式保存,放在安全地方。2)下载 APP 一定认准官方渠道,不要轻易尝试来路不明的“增强版”或第三方改版。3)发现设备异常或曾截图保存私钥,不要抱侥幸心理,应立即将资产转移到新的钱包。4)OKX 做了什么?为了防止用户在私钥和助记词备份页面截图,我们在这些敏感页面禁用了截屏功能。
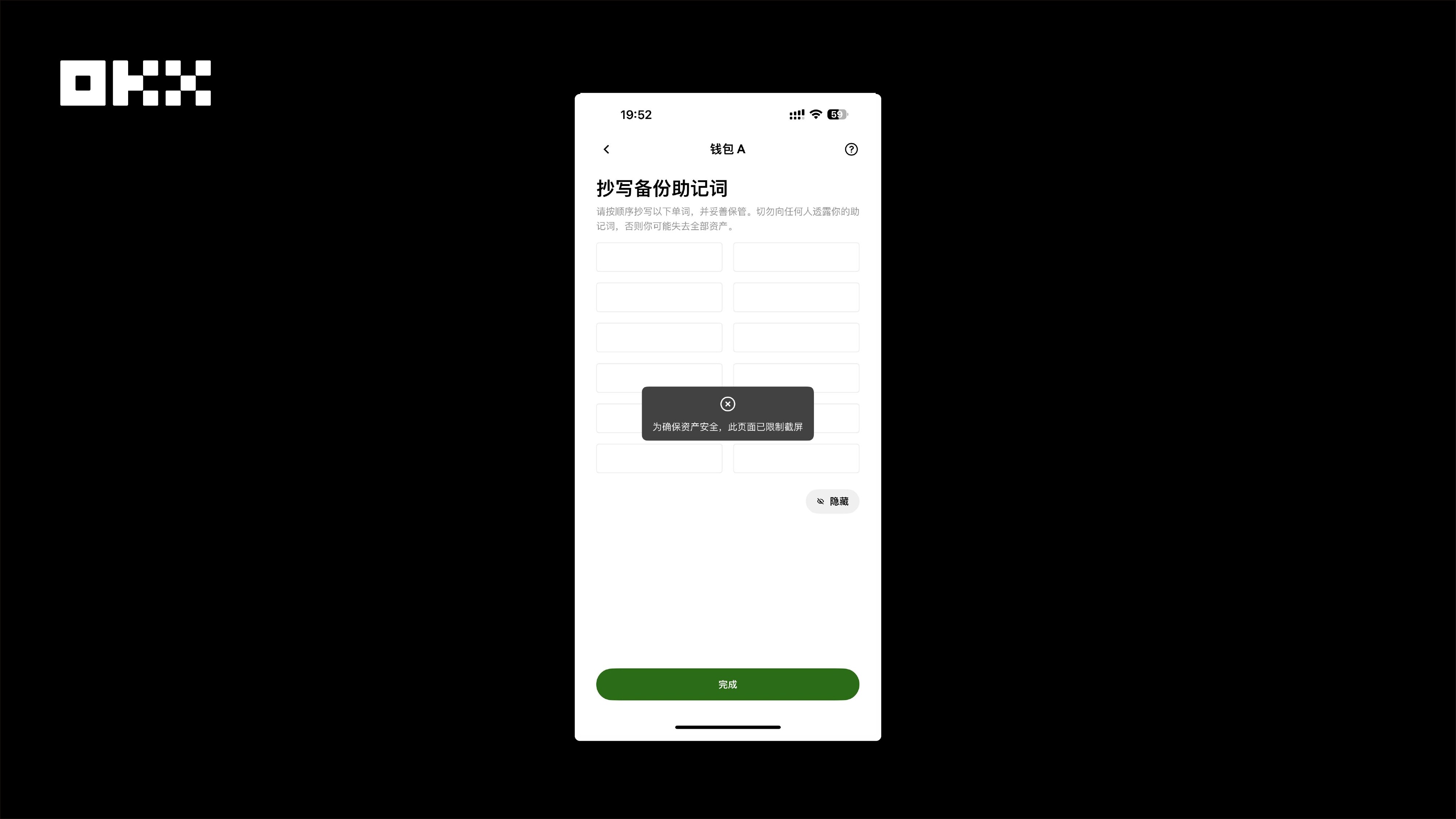
图片:OKX Wallet禁止在私钥和助记词页面截屏
同时,为了降低用户安装到假 APP 的风险,安卓端还提供了恶意应用扫描功能。
图片:OKX Wallet 安卓端提供了恶意应用扫描功能
(三)最常见且最容易上当的场景:私钥被他人钓鱼
案例五:假空投钓鱼。某知名 NFT 项目在 Twitter 宣布向持有者空投新代币。消息发布后仅 10 分钟,多个钓鱼网站便出现在 Google 搜索结果前列(通过付费广告推广)。这些钓鱼网站的域名仅有一个字母差异(如 opensae.io 而非 opensea.io),页面设计几乎与官网一致。当用户连接钱包时,页面显示提示:“网络拥堵,连接失败,请手动输入助记词领取空投。”当天就有超过 50 名用户上当,累计损失超过 $200,000。最快的受害者从输入助记词到资产被转走,仅用了 3.7 秒。
案例六:社会工程攻击。赵女士在某项目的 Discord 群里遇到操作问题,一个头像和昵称都很“官方”的管理员主动私聊她,自称客服要帮她处理,并发来一个“验证页面”的链接。赵女士信以为真,点进去按提示输入了助记词,页面看起来和官网一模一样。几分钟后,她的钱包突然被持续转出多笔资产,她这才意识到所谓的管理员其实是骗子,而任何让用户在网页输入助记词或私钥的“客服”,必然是诈骗。值得注意的是,除了冒充官方管理员,骗子还可能冒充好友、项目方员工或其他可信身份。

安全建议:一个正规的 DApp 绝不会要求你提供私钥,一个可靠的人也不会向你索要私钥。记住:私钥就是你的资产钥匙,务必妥善保管,不要轻易透露。
三、为什么一旦私钥泄漏,钱包厂商能做的很少?
有用户在发现私钥疑似泄漏、资产被转走后,会第一时间联系钱包团队,希望我们能提供更多帮助。但实际情况是,在私钥已经暴露的前提下,钱包厂商能介入的空间非常有限。
这里可以简单说一下我们在收到“资产被盗”反馈时的基本处理流程,也顺带解释为什么很多时候我们无法直接“追回”链上资产:
首先,我们会协助用户排查资金流向,分析链上资金是否可能与已知黑客团伙或地址集群相关。同时,会建议用户尽快转移尚未被盗的资产,以降低进一步损失的风险。对于被盗金额较大的情况,我们会建议用户及时联系当地警方,通过司法途径寻求帮助。内部团队也会对事件进行深入分析,总结黑客的作案手法,为后续用户防护提供参考。
作为工具提供方,钱包本身无法也没有权限冻结或回滚链上资产。一旦私钥被黑客获取,对方通常会通过自动化脚本在几秒内完成资金转移,速度极快,难以干预。只有当被盗资金最终流入中心化交易所时,才可能通过司法途径申请临时冻结。
当资金链路与我们已掌握的黑客集群存在关联时,我们会从其常见的作案手法出发,协助用户回想近期是否进行过某些高风险操作,进而判断私钥可能是在什么环节暴露的。
OKX 一直将用户资金安全放在首位,多年来投入大量资源建立风控体系并设计多重验证机制。虽然这些流程看起来较为繁琐,但都是为了更好地保护用户资产安全。可以说,我们也是业内在安全方面投入最为充足的团队之一。

图片:OKX Wallet安全评分位列第一
正如前面提到的,如果用户安全意识不足或使用习惯不当,依然可能因为钓鱼、私钥泄露等原因遭受损失,这并不取决于使用哪款钱包。因此,妥善保管私钥始终是最关键的安全基础。除了不断提升产品自身的安全能力,我们也持续加强案例分析和安全贴士的分享,帮助用户更好地识别潜风险场景。
四、总结一下,私钥安全Tips

免责声明:
本文仅供参考。本文无意提供 (i) 投资建议或投资推荐,(ii) 购买、出售或持有数字资产的要约、招揽或诱导,或 (iii) 财务、会计、法律或税务建议。数字资产(包括稳定币和 NFT)受市场波动影响, 涉及高风险,并且可能会贬值。关于交易或持有数字资产是否适合您的相关问题,请咨询您的法律/税务/投资专业人士。OKX Web3 钱包仅为一种自托管钱包软件服务,让您可以发现并与第三方平台交互,OKX Web3 钱包无法控制此类第三方平台的服务,也不对其承担任何责任。并非所有产品均在所有地区提供。请您自行负责了解和遵守当地的有关适用法律和法规。OKX Web3 钱包及其相关服务不是由 OKX 交易所提供的,并受 OKX Web3 生态系统服务条款的约束。
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



