Original source: Max He@Safeheron Lab
Recently, the cryptocurrency community has been widely discussing a significant piece of news: U.S. law enforcement agencies are suspected to have obtained the private keys for approximately 120,000 bitcoins from a mysterious transfer in 2020, valued at up to $15 billion. According to a report by Elliptic [1], these assets were initially associated with the mining pool Lubian.com and were later officially seized by the U.S. Department of Justice. There is widespread speculation that law enforcement may have exploited a random number flaw during wallet generation to reconstruct or take over the private keys, while some believe this is a technical hacking operation led by the U.S. government.
Following the announcement, the entire cryptocurrency industry experienced a strong shock, quickly becoming a focal topic within the sector. This not only sparked extensive discussions on technical and security levels but also raised new concerns among investors regarding the reliability and risk prevention of crypto assets. This article will systematically analyze the event and its underlying security roots from both technical and factual perspectives, delving into key technical details, comprehensively reviewing the evolution of the event, and exploring its potential far-reaching impacts.
Random Numbers and Private Key Security: The Lifeline of the Blockchain World
In the world of blockchain, random numbers are the cornerstone of cryptographic security. Each bitcoin or Ethereum wallet's private key is generated by random numbers—once the random number lacks sufficient "randomness," hackers may predict the private key and directly steal digital assets. To effectively mitigate this risk, wallets must use cryptographically secure random number generators (CSPRNG) to ensure that the generated random numbers are truly unpredictable and non-reproducible.
Wallets that rely on insecure random algorithms may appear to operate normally on the surface, but they actually harbor hidden dangers: once the randomness is successfully predicted, asset loss becomes irreversible.
History Repeats: Lessons from Multiple Major Security Incidents
Between 2022 and 2023, several major security incidents triggered by the same random number vulnerability were disclosed, fully exposing the severity and prevalence of this issue.
Security Incident 1: The Painful Lesson of Wintermute's $160 Million Loss
On September 20, 2022, the well-known market maker Wintermute suffered a major security incident, with approximately $160 million in digital assets stolen [2]. The attackers cleverly exploited a vulnerability in the address generation tool Profanity—this tool relied on Mersenne Twister (MT19937) as a pseudo-random number source in some of its usages to generate "vanity addresses."
Due to the predictability of MT19937's output in the absence of sufficient entropy injection, the attackers were able to reproduce part of the address/private key generation process, successfully calculating the corresponding private keys and transferring funds. This case became the first instance in crypto history where an institutional wallet was breached due to the misuse of random numbers, marking the evolution of randomness issues from mere developer oversight to systemic security risks.
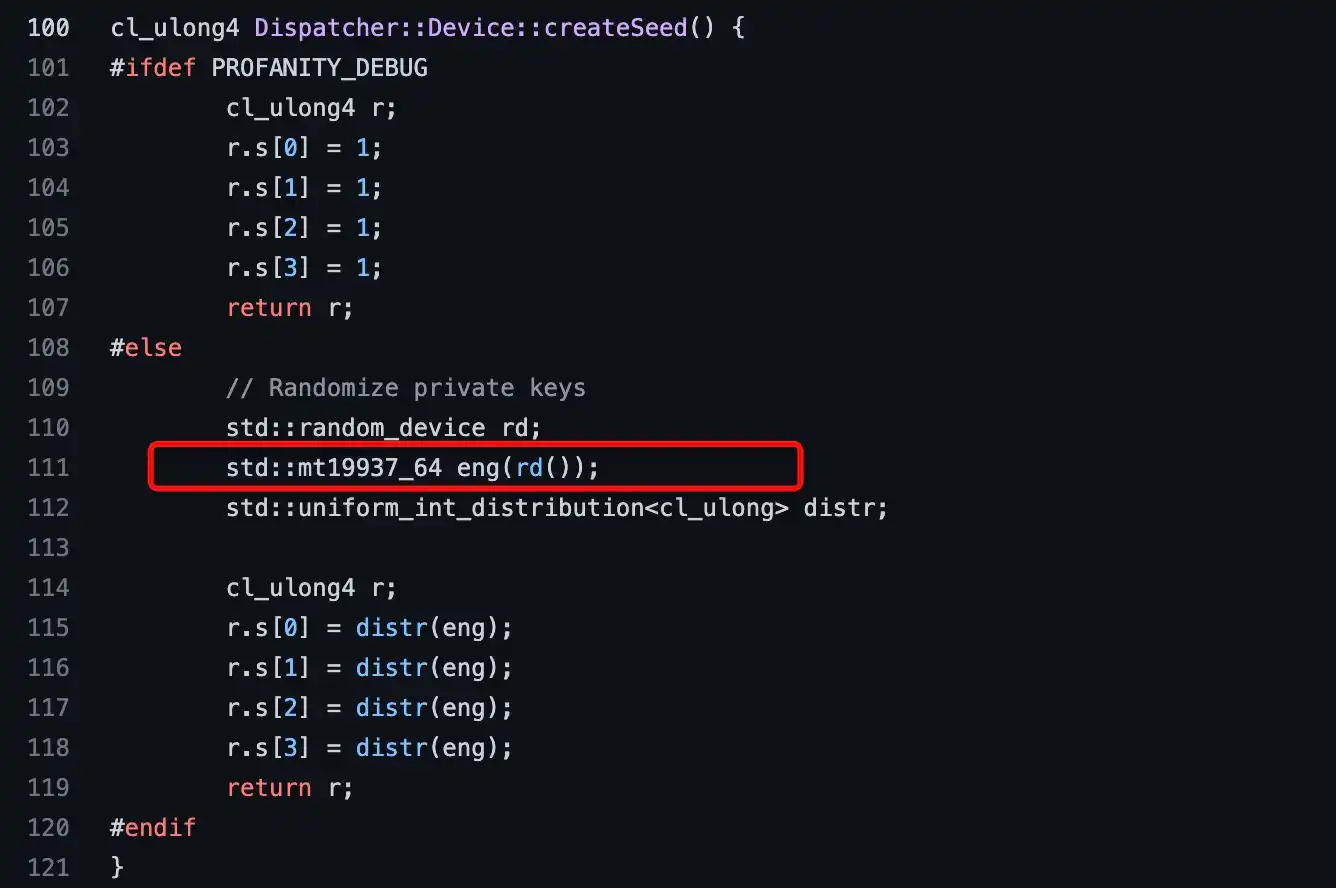
Regarding this attack, Safeheron published an analysis detailing the attack's technical specifics and reproduced the attack process.[3]
Security Incident 2: Trust Wallet's Random Number Vulnerability Triggers a Crisis of Trust
In April 2023, security researchers discovered that the Trust Wallet browser extension (versions 0.0.172–0.0.182) used a non-cryptographically secure random function [4] when generating wallet mnemonic phrases, which also relied on the Mersenne Twister (MT19937) pseudo-random number algorithm (as shown in the figure below), with a random space of only about 2^32 possibilities, far from sufficient to withstand brute-force attacks.
Attackers could enumerate all possible mnemonic combinations within a limited time, thereby reconstructing private keys and stealing user assets. Trust Wallet's official announcement later confirmed the existence of the vulnerability and urgently reminded affected users to migrate their assets in a timely manner. According to an official statement from the project community forum, this vulnerability has led to approximately $170,000 in potential losses, as attackers may have successfully exploited this vulnerability to carry out targeted attacks.
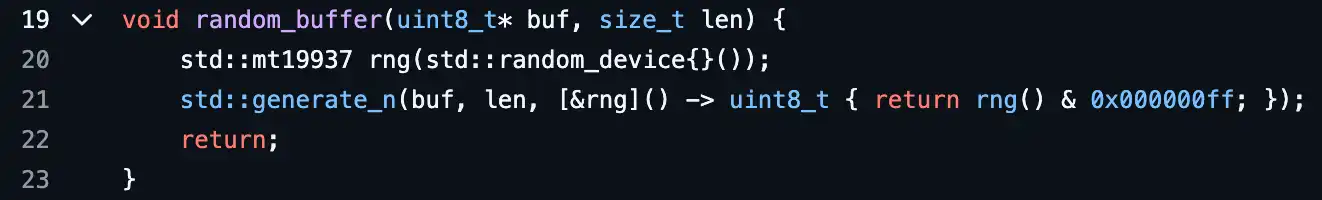
This incident became the first case of a random number vulnerability affecting mainstream wallet end users, bringing the issue of "random number security" to large-scale public attention for the first time.
Security Incident 3: Libbitcoin Explorer (bx seed) Weak Random Number Event
In August 2023, the security research team Distrust announced the discovery of a serious random number vulnerability in the command-line tool Libbitcoin Explorer (bx) version 3.x [5]. This tool also used the Mersenne Twister (MT19937) pseudo-random number generator when executing the bx seed command to generate wallet seeds, relying solely on system time as the seed source, resulting in very low randomness and predictable output. Attackers could enumerate all seed values within a limited time, thereby reconstructing wallet private keys and directly stealing assets.
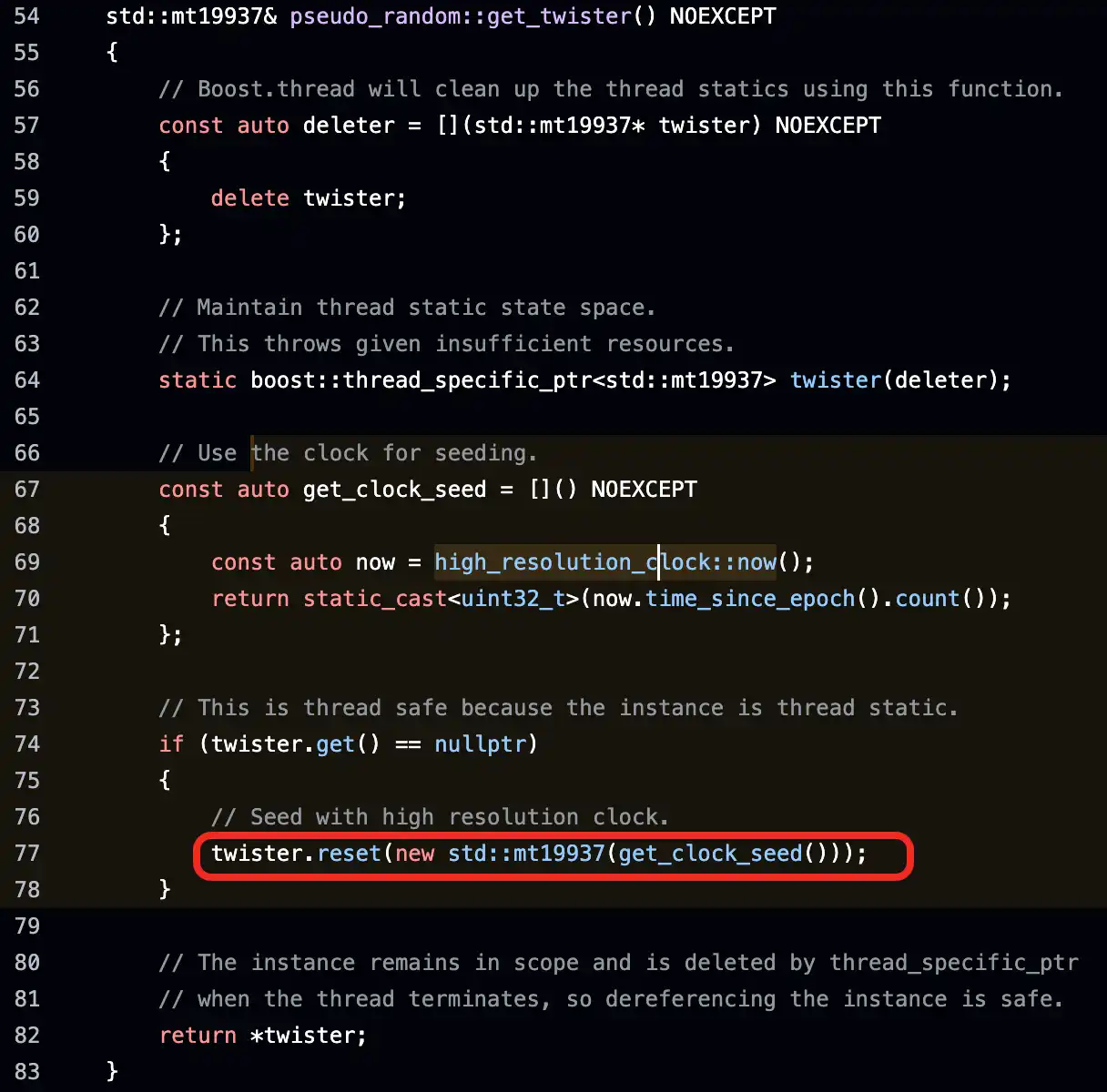
This vulnerability affected all users who generated wallets using Libbitcoin Explorer 3.x, as well as related applications relying on the libbitcoin-system 3.6 library. As of August 2023, over $900,000 in cryptocurrency assets had been stolen due to this vulnerability [6]. The vulnerability was officially registered as CVE-2023-39910 after its disclosure.
Although Libbitcoin-explorer has promptly applied the correct security patch, the matter did not end there.
The Huge Iceberg Emerges
After the disclosure of the Libbitcoin Explorer 3.x security incident, a white hat researcher team led by Distrust established the MilkSad project to continuously track the impact of the vulnerability and promote community response.
By 2024, researchers systematically sorted out the generation mechanisms of these "weak wallets," wallet types, and configurations of pseudo-random number generators (PRNG) [7], revealing their potential connections with the bitcoin mining pool Lubian.com and the distribution characteristics of related funds.
In 2025, with the help of key clues provided by an anonymous white hat researcher, the long-stalled analysis work made breakthroughs. The MilkSad team discovered that the affected software introduced a new parameter—the PRNG offset—when generating private keys, allowing researchers to re-associate previously scattered wallet groups and reveal a unified random number generation pattern behind them. This discovery became key to understanding the causes of the entire "weak wallet" incident [8].
According to the team's further in-depth analysis, the initially discovered 2,630 problematic wallets in 2023 were just the tip of the iceberg. By searching different segments of the PRNG output, researchers have successfully reconstructed and identified over 227,200 independent wallets (as shown in the figure below), all of which have valid usage records on the mainnet, constituting the largest cluster of "weak random wallets" to date.
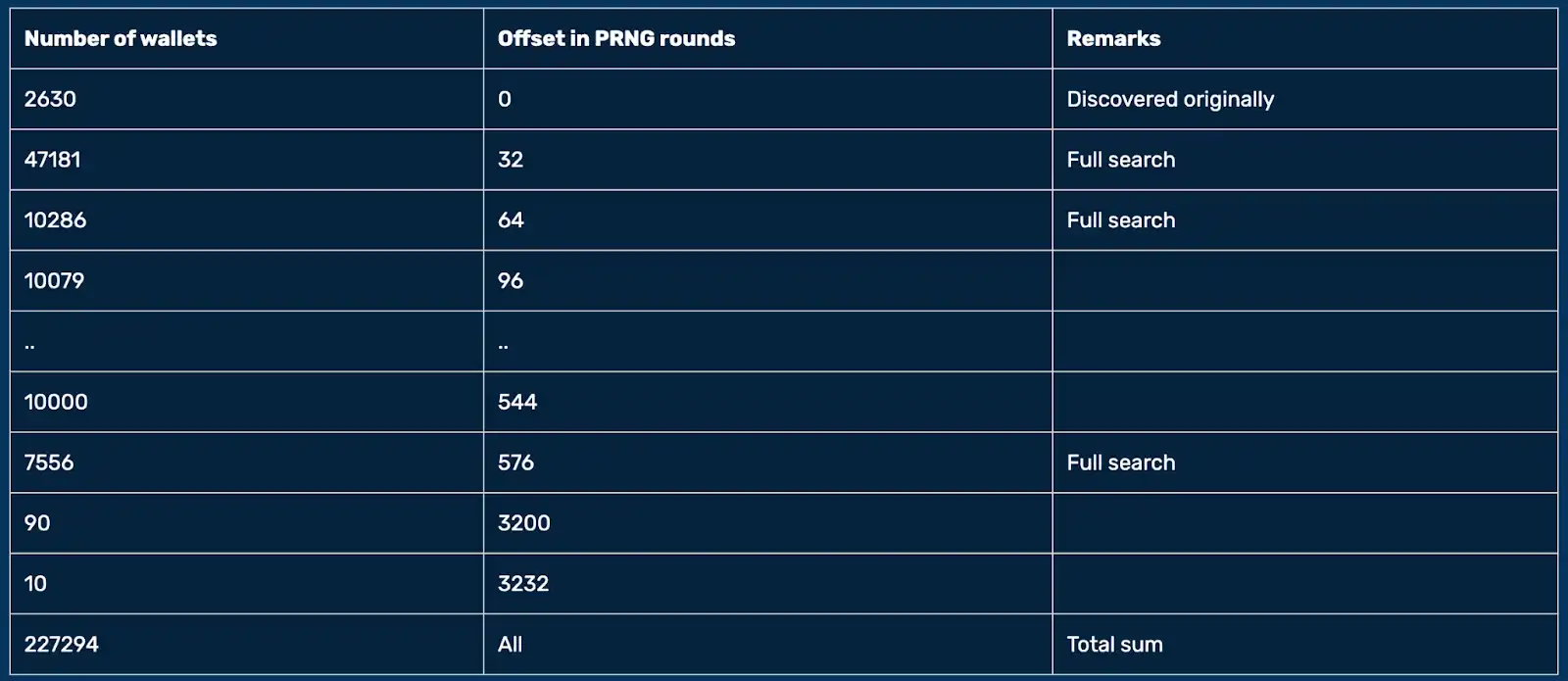
On-chain data shows that these wallets, generated by random number flaws, collectively hold approximately 137,000 bitcoins (BTC). Within just two hours on December 28, 2020, these wallets were emptied, with balances plummeting from 137,000 to less than 200, of which about 9,500 BTC flowed to the payment address of the Lubian mining pool, while the remaining approximately 120,000 BTC is presumed to have been transferred to wallets controlled by the attackers. All suspicious transactions used the same transaction fee, exhibiting obvious characteristics of automated batch transfers.
Subsequently, new important clues emerged, further confirming the existence of this large-scale theft incident [9]. Researchers found that some victim wallets on the Bitcoin mainnet had abnormal transaction activities on July 3, 2022, and July 25, 2024. These transactions embedded identical information through the OP_RETURN mechanism:
"MSG from LB. To the whitehat who is saving our asset, you can contact us through 1228btc@gmail.com to discuss the return of asset and your reward."
Researchers speculate that "LB" may represent Lubian.com, and "saving our asset" could refer to the large-scale fund transfer incident on December 28, 2020. These messages were broadcast multiple times to different addresses, seemingly an attempt by Lubian to establish contact with the "white hat" in possession of the assets to discuss asset return and rewards.
However, since the private keys of these wallets had long been compromised, theoretically anyone could initiate transactions or write messages from these addresses, making it impossible to definitively confirm whether this information genuinely originated from the Lubian team or was a misleading or prank operation.
At this point, the main body of the iceberg finally emerged—this systemic vulnerability triggered by random number flaws has developed into one of the largest and most far-reaching security incidents in Bitcoin history.
Technical Details: The Complete Process of Brutally Cracking 220,000 BTC Wallets
So, how were these 220,000 BTC weak random wallets generated? Let’s detail the specific technical search process [8].
Step 1: Choose the same pseudo-random number generator (PRNG) MT19937 to generate random numbers. It is reiterated that this PRNG is completely lacking in cryptographic security.
Step 2: Use a very low-entropy seed (0 to 2^32-1) to initialize MT19937. The ability to quickly predict these BTC wallet private keys is primarily due to the low-entropy seed.
Step 3: MT19937 outputs a 32-bit integer in each round, but not all of it is used; only the highest 8 bits are selected. This means that each round of MT19937 will yield one byte.
Step 4: Introduce the OFFSET feature to expand the range of private keys. It should be noted that the private key seed in BTC is 32 bytes (equivalent to 24 mnemonic words, i.e., 256 bits). These 32 bytes are obtained from the (32 * OFFSET)th round to the (32 * OFFSET + 31)th round, thus generating the BTC private key seed. Specifically, the BTC private key seed is 32 bytes, as follows:
(1) Rounds 0 to 31 output a 32-byte private key.
(2) Rounds 32 to 63 output a 32-byte private key.
(3) Rounds 32 * 2 to 95 output a 32-byte private key.
(4) And so on, OFFSET can take a maximum value of 3232.
Step 5: Based on the private key seed, use the public BIP32 wallet derivation algorithm, adopting the derivation path m/49'/0'/0'/0/0 to derive child public-private key pairs.
Step 6: Based on the child public key, generate a wallet address of type P2WPKH-nested-in-P2SH with a prefix of 3.
Step 7: If the generated address has indeed been used on-chain, it indicates that a weak random number wallet has been successfully found, and its wallet address and corresponding private key should be recorded.
The entire search process described above is deterministic, with the only variable being the choice of low-entropy seeds, which has 2^32 possibilities, far less than the BTC standard private key space of 2^256. Therefore, all 220,000 weak random wallets and their corresponding private keys can be obtained through brute-force searching.
The Complete Story of the Incident
Let’s summarize the development of the entire event.
As early as several years ago (dating back to 2018), some digital asset projects mistakenly introduced non-cryptographically secure pseudo-random number generators (PRNG) during development and applied them to the extremely sensitive process of wallet private key generation. Due to the developers' lack of understanding of cryptographic security at the time, this error went unnoticed, laying the groundwork for subsequent large-scale vulnerabilities.
Unfortunately, over time, this issue was gradually discovered and maliciously exploited by hackers. Different attack groups launched several well-known attacks based on the same principle— including the Wintermute theft, the Trust Wallet random number vulnerability incident, and the Libbitcoin weak wallet incident. These attacks collectively resulted in hundreds of millions of dollars in asset losses and brought the previously overlooked technical detail of "random number security" to the forefront of the industry.
When researchers analyzed the commonalities among these incidents, they found that all victim wallets exhibited similar randomness defects, which could be traced back to the earlier Lubian mining pool theft incident. Through in-depth research, they confirmed that the wallets used by Lubian also relied on an insecure random number generation mechanism and were part of this "weak wallet" group. Subsequent systematic analysis revealed even more astonishing facts: there are approximately 220,000 weak random wallets across the network, involving a total amount of 120,000 BTC, constituting the largest and most far-reaching random number security incident to date.
As for the circulating claim that "the U.S. Department of Justice led the Lubian.com theft incident," it primarily stems from a subtle fact: during the Department of Justice's formal intervention in handling related assets, the previously dormant Lubian-associated Bitcoin addresses suddenly experienced a large-scale asset transfer. The coincidence of this timing with the direct association of on-chain addresses led many observers to suspect that the government may have employed brute-force methods to recover the relevant private keys. There is also another possibility— the U.S. government did not directly brute-force the private keys but instead controlled the individuals or entities holding the private keys, thereby facilitating the fund transfer.
Although these wallets belong to weak random wallets that can be breached, and their private keys can theoretically be reproduced through technical means, as of now, there is still no publicly available and verifiable evidence indicating that the U.S. government led a "brute-force" operation against the corresponding private keys. Unless relevant agencies formally acknowledge the fact of technical intervention, the true process of the entire incident will remain shrouded in mystery.
How to Obtain Cryptographically Secure Random Numbers?
Now that we recognize the importance of secure random numbers, how should we correctly obtain them in actual development and application? The following principles should be followed:
(1) Prefer to use secure interfaces provided by the operating system to generate random numbers based on the system entropy pool.
(2) Use secure hardware entropy sources when conditions permit, such as hardware random number instructions from Intel SGX CPUs.
(3) In MPC scenarios, multiple entropy sources can be combined to enhance overall security, for example, by using the Linux system entropy pool in conjunction with Intel SGX CPU hardware random numbers, thereby avoiding the risks of a single entropy source failing or being predicted.
(4) Use secure random number generation interfaces from widely validated cryptographic libraries, such as libsodium, BoringSSL, OpenSSL, etc.
(5) Ensure that the seed entropy is no less than 128–256 bits, and prohibit the use of low-entropy sources such as timestamps and process IDs as seeds.
(6) Strictly prohibit the use of non-cryptographically secure pseudo-random number generators (non-CSPRNG), such as Mersenne Twister (MT19937), Math.random(), rand().
The Advantages of Multi-Source Entropy Fusion in MPC
Compared to single-party systems, MPC has a natural advantage in entropy fusion: each participant can independently provide a random entropy source, and the final random result is generated collectively by all parties. As long as any one party remains honest, the randomness of the entire system cannot be predicted or manipulated. This multi-source random structure significantly enhances the overall security and tamper-resistance of the system, making it one of the core advantages of MPC protocols in terms of security.
Safeheron has built a digital asset security custody protocol based on MPC and TEE technology. In this solution, the participants of the MPC protocol use various independent secure entropy sources, including the Linux system entropy pool and TEE hardware entropy sources (such as Intel SGX hardware random number instructions). This multi-source entropy fusion mechanism not only strengthens the security boundary of the system but also lays a higher security baseline for constructing a trusted execution environment (TEE) and a distributed signature system.
Conclusion
This seemingly mysterious "120,000 bitcoins theft" incident reveals not a certain algorithm being breached, but rather that early developers misused non-cryptographically secure random number algorithms during the private key generation process, fundamentally undermining the security of the entire system.
The security of crypto assets ultimately depends on the rigor of cryptographic implementations; any slight engineering oversight can be successfully exploited by hackers and ultimately determine the ownership of digital assets. Only by ensuring random number security from the source, using trusted entropy sources and validated cryptographic libraries, can we allow "randomness" to return to its original meaning—unpredictable and unalterable.
About Safeheron Lab
Safeheron Lab was founded by Max He, Chief Scientist of Safeheron, and the team gathers international experts in cryptography and security, focusing on fundamental research in cutting-edge areas such as blockchain security and trusted computing. Safeheron Lab collaborates with partners like the Turing Artificial Intelligence Research Institute to promote the transformation of research results and industrial applications, providing innovative solutions for digital asset security.
References
[1] $15 billion seized by US originates from Iran/China bitcoin miner "theft"
[2] How Crypto Trading Firm Wintermute Was Hacked For $160 Million
[3] A Deep Dive of HOW Profanity Caused Wintermute to Lose $160M
[4] Trust Wallet: CVE-2023-31290 Detail
[5] Libbitcoin Explorer: CVE-2023-39910 Detail
[6] CZ: Trust Wallet and Binance Wallet do not use Libbitcoin Explorer to generate mnemonics
[7] Update #7 - Billion Dollar Wallet Range, Now Empty
[8] Update #13 - Discovering Over 224k New Wallets
[9] Update #14 - More Information on Suspected Lubian.com Hack
This article is from a submission and does not represent the views of BlockBeats.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




