If the cryptocurrency world is never short of dramatic stories, this time, the protagonist has changed to Monero.
This is not a sudden attack, but a power struggle that was announced a month in advance—a prepared confrontation. The attackers even declared that they would "challenge the Monero network from August 2 to August 31." Their goal is aimed at a rare achievement in the blockchain world: to control 51% of the hash power of a privacy coin network with a market value exceeding $5 billion.
And today, the attackers claim they have achieved this goal.
A Premeditated Attack
We all know that in a blockchain network, all transactions must be verified by miners, a process known as "mining." The computational power of miners is referred to as hash power; the higher the hash power, the greater the chance of mining new blocks and receiving rewards.
Monero is no different.
However, compared to other cryptocurrencies, Monero has a design to prevent large mining pools from acting maliciously—it does not support dedicated mining machines (ASICs) and can only be mined using ordinary computer CPUs or GPUs. The original intention of this rule is to prevent miners from gathering in a single large mining pool, allowing anyone to participate in mining with their own computer, making the network fairer and more decentralized.
But this mechanism also has an idealized attack method, which is to rent or mobilize a large number of ordinary servers (such as cloud computing resources, idle PCs, miner computers) in a short period. This is precisely how the attackers executed their plan.
Now, let's look at the premeditated attacker, called Qubic.
The initiator of this action is Qubic, an independent blockchain project not originally created to attack Monero. It is led by Sergey Ivancheglo (nicknamed Come-From-Beyond), a co-founder of IOTA and a seasoned crypto developer, using a "Useful Proof of Work" (UPoW) mechanism that allows miners' hash power to be used not only to solve mathematical problems but also to train its artificial intelligence system "Aigarth," achieving two goals at once.
So why did it associate with Monero and launch a "war" of hash power against it?
In fact, this is an "economic demonstration" of Qubic's UPoW model capabilities. Starting from May 2025, it successfully attracted a large number of miners to join by using its network hash power for CPU mining of Monero, allowing miners to earn both Monero and $QUBIC tokens simultaneously. The Monero mined would be sold for stablecoins, which would then be used to repurchase and destroy Qubic coins, forming a self-reinforcing economic cycle.
After Qubic announced it would "challenge" the Monero network from August 2 to August 31, some members of the Monero community began to monitor the chain around the clock. Someone on Reddit stated that they would keep an eye on every block, especially noting the appearance of "orphan blocks." Initially, everything seemed normal, but one early morning, they noticed a chain reorganization. Normally, chain reorganizations are not uncommon in the Monero network; for example, when two miners mine blocks simultaneously, the system will choose one and discard the other. However, the timing of this was suspicious, seemingly related to Qubic's testing of inserting alternative blocks and forking the blockchain. Although that alternative block was ultimately rejected, it indicated that Qubic was attempting to take action.
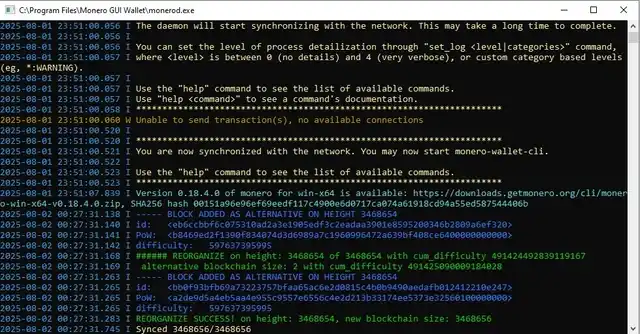
Block status of Monero
The monitor also found that Monero should produce a block every two minutes, but the block generation speed had recently accelerated significantly, suggesting that the network had detected signs of potential attack pressure. This convinced them that Qubic was indeed conducting some form of interference. Another participant pointed out that the only orphan block appeared 12 hours before Qubic publicly claimed it would launch an attack.
In terms of hash power data, the community also observed that Qubic stopped reporting its hash power to public mining pool statistics websites at the beginning of August, making it impossible for outsiders to see their true mining capabilities directly. Some speculated that this might be to hide peak hash power, create opacity, and present more favorable numbers through their own controlled website. Members of the Monero core team analyzed that their hash power was not constant but regularly switched between peaks and troughs, making this "switching" mode more threatening than stable mining.
The premeditated attack by Qubic to "show muscle" resulted in Qubic occupying nearly 40% of the Monero network's hash power during the period from May to July. By August, Qubic claimed to have reached 52.72%, directly crossing the 51% "control threshold"—this means it technically had the ability to reorganize the chain, conduct double-spending attacks, or censor transactions. Qubic claimed this was to simulate potential attacks the Monero network might face and to discover security weaknesses early.
Is Qubic Just Blustering?
So, did Qubic really succeed in executing a 51% attack? Many remain skeptical, believing this was merely a deliberately deceptive marketing ploy.
@VictorMoneroXMR raised doubts with the following screenshot. When the total hash power of other Monero mining pools showed 4.41 GH/s and the total network hash power showed 5.35 GH/s, Qubic's dashboard displayed 2.45 GH/s under the same total network hash power, which clearly does not add up and may indicate that Qubic's dashboard did not include its own hash power in the total network hash power. If we adjust based on this assumption, Qubic's hash power actually accounts for only about 30% of the total.
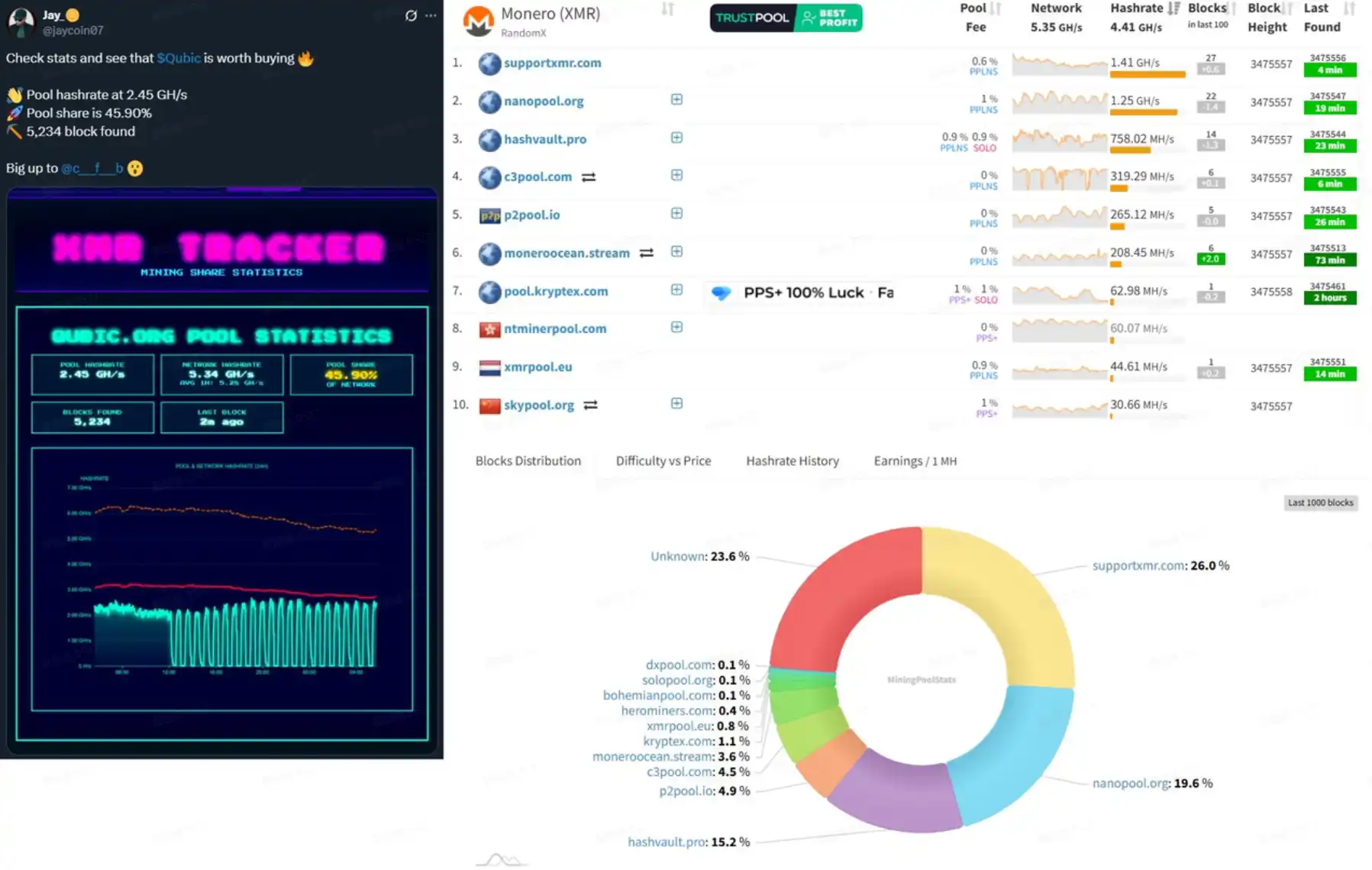
In addition to the data doubts, the most direct on-chain evidence is that Monero experienced a continuous chain reorganization of 6 blocks, but this does not definitively prove that Qubic had the capability to launch a 51% attack.
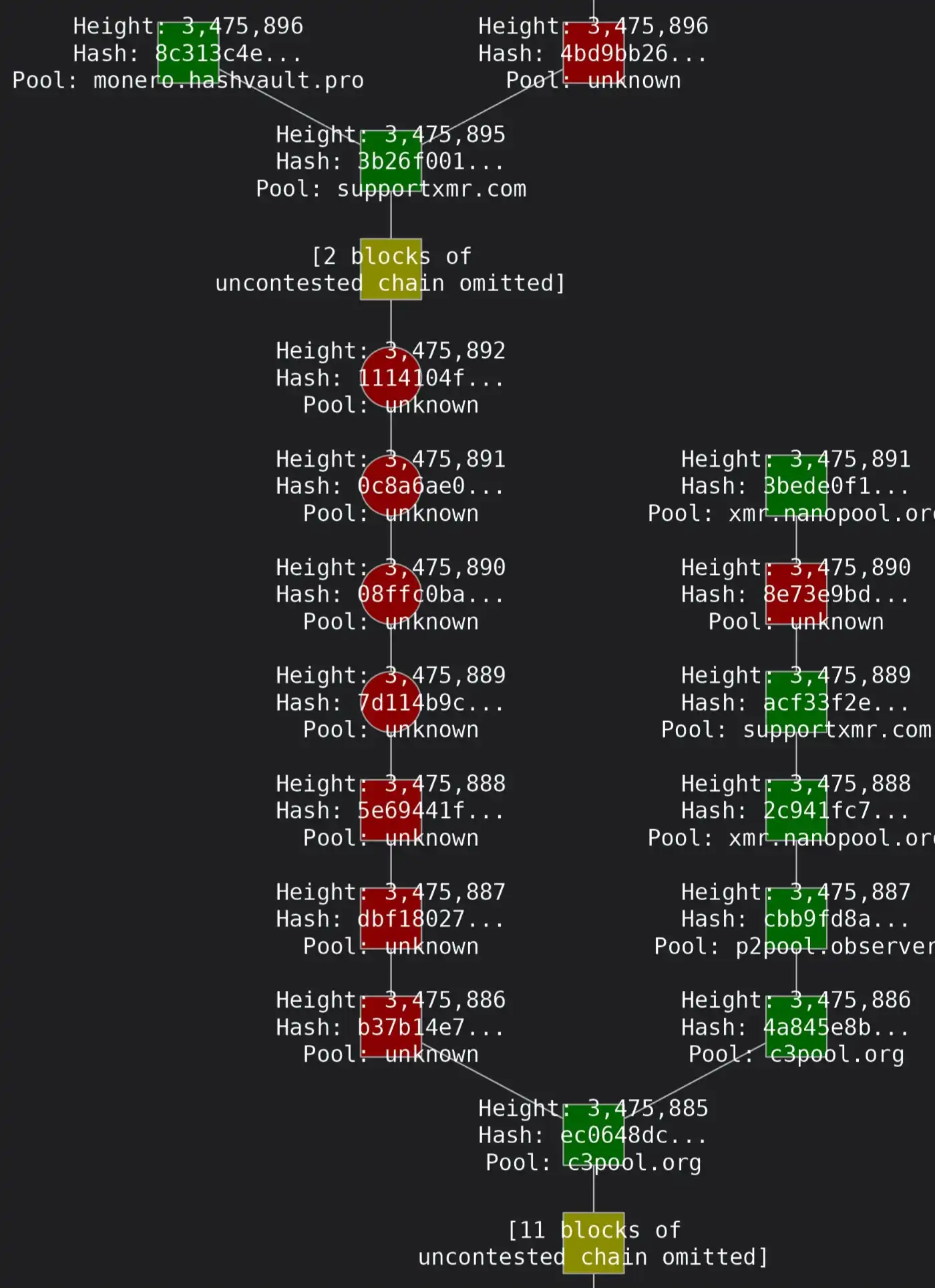
This point was also corroborated in the real-time monitoring post of blocks in the Monero Reddit community.
Throughout the Qubic challenge, the community did not observe a sustained, significant increase in orphan blocks or chain reorganizations, only one suspected reorg, and the alternative block was rejected. Core developers and community members noted that Qubic had approached or even slightly exceeded 50% hash power at certain times (Qubic claimed to have reached 52.72%); even if it briefly exceeded 51%, if only for a few minutes or a few blocks, it might not be able to execute an effective attack.
In other words, there is currently no evidence showing they maintained a stable hash power above 51% long enough to launch a successful attack.
The consensus in the Monero community is that Qubic may have briefly exceeded 51%, but did not execute an effective attack; it was more like a display of hash power and psychological warfare. The attackers may have displayed exaggerated percentage screenshots on their website to create the impression that they had taken control of the network.
A Losing Deal of Spending $75 Million to Earn $100,000?
Qubic's attack costs have also sparked extensive discussion on social media.
Analysis within the Monero community generally believes that maintaining the current hash power controlled by Qubic is extremely costly. Based on the current network difficulty, the daily block rewards for the entire Monero network are valued at approximately $150,000. If the attackers want to maintain over 50% of the total network hash power, it means they need to produce blocks equivalent to half or more of the total network every day, which incurs staggering hardware, electricity, and operational costs.
According to calculations by Cosine, the founder of security company SlowMist, the cost of such a large-scale attack could reach up to $75 million per day, a figure that is nearly impossible to recoup through mere speculative mining.
Given that this figure is exorbitant, let's analyze it from other angles. First, look at Crypto51, a website specifically designed to estimate the cost of 51% attacks on different PoW cryptocurrencies. It provides hourly rental cost references for some mainstream or mid-cap cryptocurrencies; for example: Ethereum Classic (market cap of several hundred million dollars): about $11,563 per hour; Litecoin: about $131,413 per hour.
Although Crypto51 does not have specific data for Monero, it can be seen that even for mid-sized PoW networks, the attack costs are usually far below the tens of millions of dollars per day level.
Based on discussions on Reddit, a community member attempted to estimate the attack cost for CPU PoW (like Monero) as follows: assuming the use of an AMD Threadripper 3990X (performance of about 64 KH/s), to reach 51% of the total network would require about 44,302 such CPU machines. The equipment purchase cost alone would be approximately $220 million (44,302 × $5,000). If other hardware costs, venue rentals, and electricity expenses are included, an additional tens of millions of dollars would be needed. Electricity costs are estimated at about $100,000 per day.
So, with an attack cost of $75 million per day, how much profit could Qubic make from it?
According to Monero's current tail emission rules, the block time is about 2 minutes, and the reward for each block is fixed at 0.6 XMR. If Qubic controls over 51% of the hash power, it means they have the ability to mine all Monero blocks produced in a day, which is about 432 XMR.
At the time of writing this article, the price of Monero is about $246. Based on the current price of Monero, if Qubic monopolized all Monero production in one day, it could only profit about $106,000.
According to Qubic's official "Epoch 172 Report," Qubic distributes the Monero it mines in a 50%-50% ratio, with half used for repurchasing and destroying $QUBIC and the other half for miner incentives. However, miner rewards are still paid in $QUBIC.
In other words, with a market cap of less than $300 million, $QUBIC has the ability to monopolize the output of Monero, which has a market cap of nearly $4.6 billion. Theoretically, they could go all out and destroy $53,000 worth of $QUBIC in a day, destroying $1.509 million worth of $QUBIC in a month, which is truly insane.
Monero's Counterattack: An Ongoing Struggle
As a result, the outside world generally believes that Qubic's motivation is not just to directly mine Monero for profit, but to support a "hash power + token" economic model: Qubic does not pay miners directly in fiat currency but uses its own token $QUBIC as a reward, artificially maintaining the secondary market price of the token—once the price stabilizes or even rises, they can exchange a relatively low token issuance cost for substantial real hash power support. The core of this approach is that the rewards miners earn from mining Monero in the Qubic pool will be exchanged for Qubic tokens. If the token price remains high, the nominal earnings for miners will be considerable, naturally attracting them.
In terms of profit model, Qubic itself does not necessarily rely on Monero's block rewards to make money; rather, it leverages this event to generate buzz for its token, increasing trading volume and price, thereby attracting more speculative buying.
As long as the market value and liquidity of Qubic tokens are maintained at a level sufficient to pay miners, this large-scale hash power occupation can continue. However, this model is built on a highly fragile foundation of confidence: if miners feel that the price of Qubic tokens is difficult to maintain, they will collectively sell off to exchange for more stable assets, triggering a price crash and causing a "first to run" stampede.
This is a blatant siphoning of hash power, which naturally provoked strong dissatisfaction and counterattacks from the Monero community.
Interestingly, during Qubic's attack on Monero, it also suffered anonymous attacks.
According to Qubic founder Sergey Ivancheglo (nicknamed Come-From-Beyond), their mining pool experienced a DDoS attack (Distributed Denial of Service attack) during this phase. Qubic reported that its mining pool's hash power dropped from about 2.6 GH/s to 0.8 GH/s, a decline of over 70%. Therefore, he believes that someone intentionally interfered with their hash power operations through a network attack.
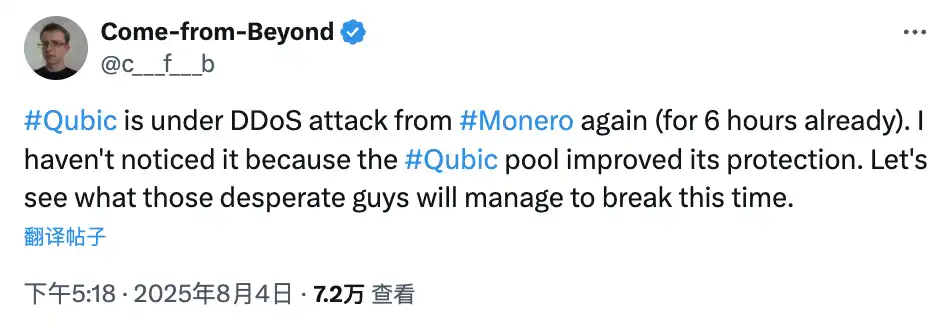
Attacker Qubic founder Sergey Ivancheglo claims he was also attacked
In the process of making accusations, Ivancheglo even specifically suspected Sergei Chernykh (nickname sech1), the main developer of Monero mining software XMRig, as the mastermind behind the attacks. However, sech1 promptly responded, clearly denying any involvement in illegal attacks: "I am not the only one in the Monero community who is dissatisfied with Qubic's actions. But I would never resort to illegal means like DDoS. Others might."
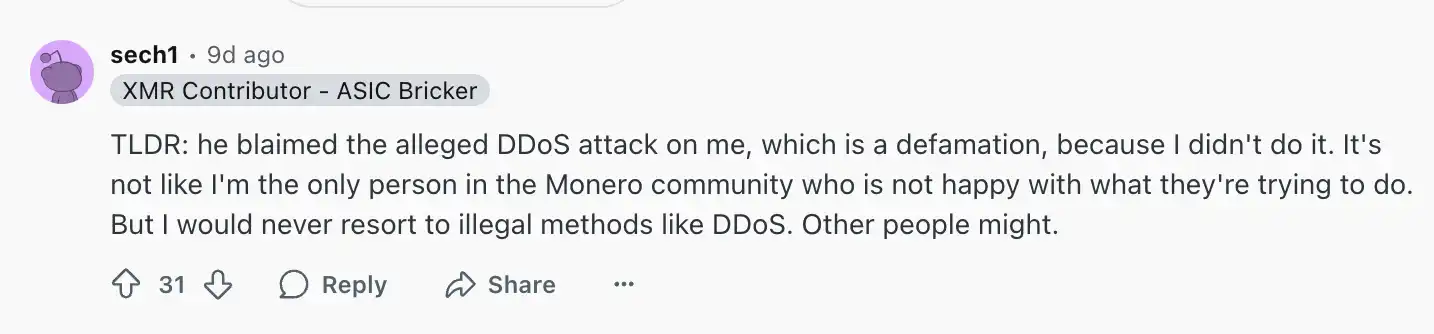
The main developer of Monero mining software XMRig states, "I am not the only one in the Monero community who is dissatisfied with Qubic's actions."
At the same time, it seems that the Monero community is also discussing how all Monero supporters should organize and completely eliminate Qubic:
"We need a movement #ShortQubic. They want to provoke us, we can only counterattack. After all, the Monero community is larger." "Where can we short Qubic? Why don't we collectively short Qubic Coin, or even leverage? That would completely kill miners' enthusiasm."
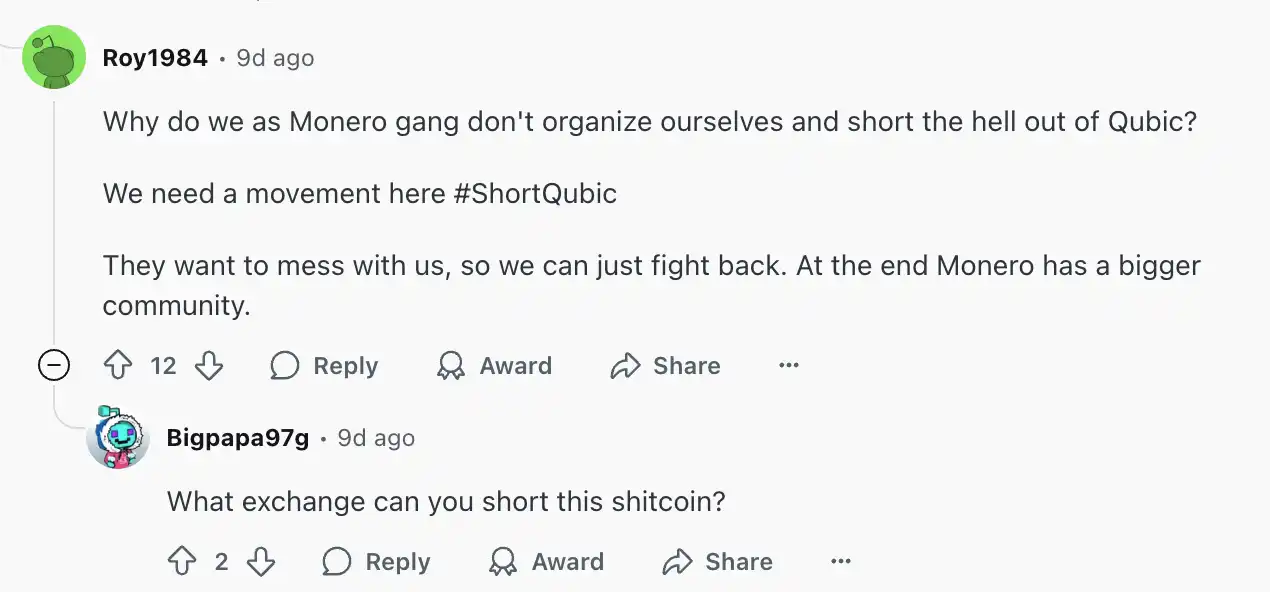
Monero community discusses how to counterattack
Interestingly, some members of the Monero community pointed out that there might also be ideological reasons behind Qubic's attack on Monero.
The Qubic official website shows that the team has many members, but most use pseudonyms, with only two using real names: one is the aforementioned Qubic founder Sergey Ivancheglo, and the other is Qubic scientist David Vivancos, who has been advocating for human-machine integration. David Vivancos is described as a "technocrat," believing in a model of social management driven by technical experts and data. This ideology has been criticized as being contrary to Monero's pursuit of decentralization, privacy, and community autonomy, and even carries a dystopian flavor.
This back-and-forth is far from over, and the smoke of psychological warfare still lingers. Will the Monero community respond to Qubic through technology, finance, or public opinion? And how long can Qubic's "hash power siphoning" last? Rhythm BlockBeats will continue to monitor the situation.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




